
Preparing for a Fortinet interview involves understanding critical aspects of network security, firewall technologies, and Fortinet’s solutions. Candidates should be well-versed in threat intelligence, intrusion prevention, VPN technologies, and security policies. Typical questions might delve into scenarios involving network design, troubleshooting, and implementing security measures. For more advanced roles, familiarity with Fortinet’s Security Fabric architecture and experience managing large-scale security deployments may be assessed. Additionally, questions on threat detection and response strategies using Fortinet’s solutions might be explored. Practical experience, problem-solving skills, and a comprehensive understanding of Fortinet’s security ecosystem will be crucial to interview success.
1. What do you know about Fortinet?
Ans:
Fortinet is a multinational cybersecurity company headquartered in Sunnyvale, California. It is known for providing a wide range of security products and services to help businesses and organizations protect their networks, systems, and data from cyber threats.
2. Describe the key features of Fortinet.
Ans:
Fortinet offers a comprehensive suite of cybersecurity solutions focusing on network security. The key features of Fortinet products, particularly its FortiGate firewalls, include:
- Firewall Protection
- Antivirus and Antimalware
- Advanced Threat Protection
- Secure SD-WAN
- Multi-Cloud Security
- Security Fabric Integration
3. Explain the function of FortiWeb in the Fortinet ecosystem.
Ans:
FortiWeb is a critical component of Fortinet’s cybersecurity ecosystem, designed to provide advanced web application firewall (WAF) capabilities. Its primary function is to protect web applications from various cyber threats, including web application attacks, data breaches, and other vulnerabilities that may arise in web-based environments. Function of FortiWeb in the Fortinet ecosystem.
- Web Application Security
- Deep Packet Inspection
- Security Policy Enforcement
- Protection Against OWASP Top Ten Threats
- Bot Mitigation
- SSL Offloading and Inspection
4. What are the benefits of the Scalable feature in Fortinet Fabric?
Ans:
Fortinet’s Fabric is designed to provide a comprehensive and integrated approach to cybersecurity. The Scalable feature in Fortinet Fabric refers to the ability of Fortinet solutions to scale and adapt to an organization’s changing needs and growth.
- Flexibility
- Performance Optimization
- Resource Efficiency
- Adaptability to Distributed Environments
- Consistent Security Policies
- Ease of Management
5. What does the security feature of Fortinet Security Fabric benefit us?
Ans:
Fortinet Security Fabric is a comprehensive and integrated security framework designed to provide organizations with a cohesive approach to cybersecurity. The security features offered by Fortinet Security Fabric bring several benefits to businesses.
6. What is Fortinet, and what are its core products?
Ans:
Fortinet is a cybersecurity company that provides various security solutions, including firewalls, antivirus, intrusion prevention, and endpoint security. Their core products include the FortiGate firewall, FortiManager for centralized management, FortiAnalyzer for logging and reporting, and FortiClient for endpoint protection.
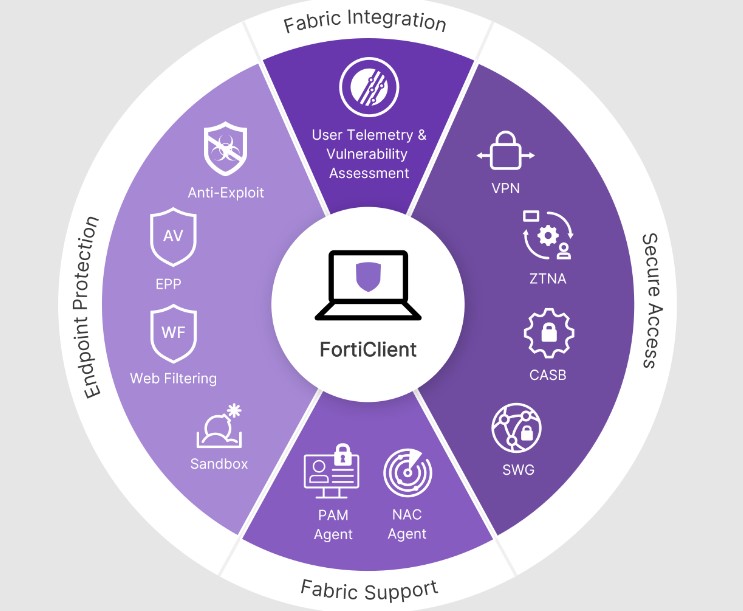
7. What is SSL VPN, and how does FortiGate support it?
Ans:
SSL VPN (Secure Socket Layer Virtual Private Network) allows secure remote access to the corporate network. FortiGate supports SSL VPN through its SSL-VPN web portal and SSL-VPN tunnel mode, providing fast access for remote users without needing a client installation.
8. Explain the Unified Threat Management (UTM) concept and how Fortinet implements it.
Ans:
UTM integrates various security functions into a single platform. Fortinet’s FortiGate firewall is an example of UTM, combining firewall, antivirus, intrusion prevention, VPN, and other security features in one device. This approach simplifies management and ensures a comprehensive security posture.
9. How does FortiGate provide high availability and redundancy?
Ans:
FortiGate offers high availability through features like clustering and failover. Multiple FortiGate devices can be configured in a cluster to provide redundancy. If one device fails, another takes over seamlessly, ensuring continuous network protection.
10. Can you explain the critical features of FortiGate?
Ans:
FortiGate is Fortinet’s flagship firewall product. It offers features such as
- Firewall
- VPN
- Antivirus
- Intrusion prevention
- Application control
- Web filtering
11. Explain what Fortinet Security Fabric is.
Ans:
Fortinet’s Security Fabric is a comprehensive security architecture that integrates various security solutions to provide seamless protection across the entire network. It allows different Fortinet products to share threat intelligence and coordinate responses in real-time.
12. What is FortiManager, and what role does it play in network security?
Ans:
FortiManager is a centralized management solution for Fortinet devices. It allows administrators to configure and monitor multiple FortiGate devices from a single interface, streamlining management tasks and ensuring consistent policies across the network.
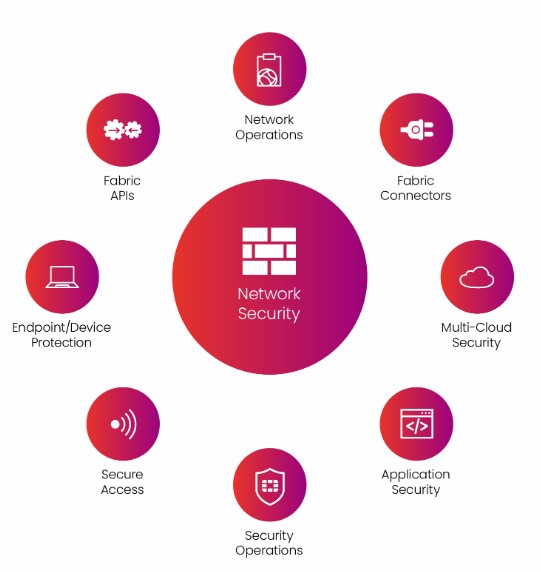
13. Explain the concept of Threat Intelligence in Fortinet’s security solutions.
Ans:
Threat Intelligence in Fortinet’s security solutions involves collecting, analyzing, and sharing information about current and potential cybersecurity threats. This information helps Fortinet devices make real-time informed decisions to protect against emerging threats.
14. How does Fortinet address the challenge of securing remote access?
Ans:
Fortinet provides solutions like FortiClient and FortiGate VPN capabilities to block remote access. These technologies use encryption and authentication protocols to ensure remote users can securely connect to the corporate network.
15. What is the purpose of FortiAnalyzer in a Fortinet deployment?
Ans:
FortiAnalyzer is a centralized logging and reporting tool. It collects and analyzes log data from Fortinet devices, providing insights into network activity and security events and helping organizations meet compliance requirements.
16. How does Fortinet contribute to cloud security?
Ans:
Fortinet offers solutions for securing cloud environments, such as FortiGate VMs for virtualized environments and FortiWeb for web application security. FortiCASB provides cloud access security broker capabilities, ensuring secure cloud adoption.
17. How does Fortinet’s Fortigate differ from other firewall solutions?
Ans:
Fortinet’s FortiGate is known for integrating various security features into a single appliance. It provides a comprehensive security solution with features like firewall, VPN, antivirus, intrusion prevention, and more, all managed through a unified interface.
18. What is FortiGate’s role in a Zero Trust Security model?
Ans:
FortiGate plays a crucial role in a Zero Trust Security model by enforcing strict access controls and verifying the identity of users and devices before granting access to resources. It helps organizations move away from the traditional approach of trusting everything inside the network and adopting a more granular and secure access approach.
19. How do you troubleshoot network connectivity issues using FortiGate?
Ans:
Troubleshooting network connectivity issues with FortiGate involves:
- Checking firewall policies.
- Examining logs.
- Verifying routing configurations.
- Using diagnostic tools provided by Fortinet, such as packet capture and logging utilities.
20. Explain what Fortinet Security Fabric is.
Ans:
Fortinet Security Fabric is an integrated and collaborative security framework that enables various Fortinet solutions to work together, share threat intelligence, and respond to security incidents in real-time.
21. How does Fortinet address zero-day threats?
Ans:
Fortinet uses a combination of signature-based detection, behaviour analysis, and threat intelligence to address zero-day threats. Advanced features like sandboxing and real-time updates contribute to proactive threat mitigation. Fortinet uses a combination of signature-based detection, behavioural analysis, and threat intelligence from FortiGuard to identify and mitigate zero-day threats in real-time.
22. What is SD-WAN, and how does Fortinet incorporate it into its solutions?
Ans:
SD-WAN (Software-Defined Wide Area Network) is a technology that enhances the performance and security of traditional WANs. Fortinet integrates SD-WAN capabilities into its FortiGate devices to optimize and secure wide-area network traffic.
23. Explain the purpose of a firewall. How does FortiGate provide firewall protection?
Ans:
- A firewall is a security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- FortiGate is Fortinet’s firewall product, providing features such as stateful inspection, intrusion prevention, VPN support, and application control to protect networks from unauthorized access and cyber threats.
24. What is Unified Threat Management (UTM), and how does Fortinet incorporate it into its products?
Ans:
UTM combines multiple security features into a single device, streamlining management and improving overall security. Fortinet integrates UTM features into FortiGate, offering a consolidated approach to security that includes firewall, antivirus, intrusion prevention, VPN, and more in a single platform.
25. Explain the concept of SD-WAN and how Fortinet support it.
Ans:
SD-WAN (Software-Defined Wide Area Networking) optimizes and manages network traffic distribution across multiple WAN connections. Fortinet’s SD-WAN solutions, often integrated into FortiGate devices, provide efficient and secure connectivity by dynamically selecting the best path for traffic based on policies, application requirements, and real-time network conditions.
26. How does Fortinet address the challenges of securing cloud environments?
Ans:
- Fortinet provides solutions like FortiGate-VM and FortiWeb-VM, designed for virtualized and cloud environments.
- Fortinet offers a range of solutions for securing cloud environments, including FortiGate-VM for virtualized environments, FortiWeb for web application security, and FortiCASB for Cloud Access Security Brokerage.
- These solutions help organizations extend their security policies to the cloud and protect against threats in virtualized and cloud-based infrastructures.
27. Explain the concept of Security Fabric in Fortinet.
Ans:
Fortinet’s Security Fabric is an integrated architecture providing a unified cybersecurity approach. It enables various Fortinet products to share threat intelligence and coordinate responses in real-time, creating a cohesive and adaptive defence mechanism.
28. How does Fortinet address zero-day and advanced persistent threats (APTs)?
Ans:
Fortinet employs advanced threat intelligence and analysis through FortiGuard Labs. Additionally, features like sandboxing in FortiSandbox help detect and mitigate zero-day threats by analyzing suspicious files in a secure environment before they can harm the network.
29. Explain the role of FortiManager in a Fortinet deployment.
Ans:
FortiManager is a centralized management solution that allows administrators to control and monitor multiple Fortinet devices from a single console. It streamlines policy management, firmware updates, and device configuration, improving overall network security management.
30. What is Fortinet, and what products/services do they offer?
Ans:
Fortinet is a cybersecurity company that provides various products and services to secure networks and endpoints. Their offerings include firewalls, antivirus, intrusion prevention, VPN, and other security solutions.
31. Can you explain the critical features of FortiGate, Fortinet’s flagship firewall product?
Ans:
FortiGate is a high-performance firewall that integrates multiple security technologies. Key features include stateful firewall, VPN support, intrusion prevention, antivirus, web filtering, and application control.
32. How does Fortinet’s Security Fabric work, and what benefits does it provide?
Ans:
Fortinet’s Security Fabric is a comprehensive security architecture that integrates various security solutions to provide real-time threat intelligence, visibility, and control across the entire network infrastructure. It enhances coordination and communication between security components, providing a more effective defence against cyber threats.
33. Explain the purpose of Fortinet’s FortiGuard services.
Ans:
FortiGuard services are Fortinet’s threat intelligence and research platform. It provides real-time updates on the latest threats, including antivirus signatures, intrusion prevention rules, and other security intelligence. This helps Fortinet devices stay up-to-date and effectively protect against emerging threats.
34. Can you explain the differences between FortiGate and FortiWiFi?
Ans:
| Aspect | |||
| Primary Purpose | Multi-threat security appliance for network protection. | Wireless UTM (Unified Threat Management) device with built-in Wi-Fi capabilities. | |
| Built-in Wireless | Wireless Optional, some models support additional wireless modules. | Inherent wireless functionality with integrated Wi-Fi access points. | |
| Flexibility | Offers flexibility in choosing wireless modules or using separate wireless solutions. | Integrates wireless capabilities directly into the device, simplifying deployment. | |
| Scalability | Scalable for different network sizes and can handle diverse security requirements. | Well-suited for smaller to mid-sized environments, with less emphasis on scalability than FortiGate. | |
| Target Audience | Suitable for a wide range of enterprises and service providers with diverse security needs. | Geared towards small to medium-sized businesses seeking integrated security and wireless functionality. |
35. How does Fortinet’s Security Fabric work?
Ans:
Fortinet’s Security Fabric is an integrated and collaborative approach to security that connects different security solutions across the network. It enables seamless communication and sharing of threat intelligence to enhance overall security. Fortinet’s Security Fabric is a framework that integrates and orchestrates various security products and solutions to provide a unified and cohesive security architecture.
36. Can you explain the role of FortiAnalyzer in Fortinet’s ecosystem?
Ans:
FortiAnalyzer is Fortinet’s centralized logging and reporting solution. It collects and analyzes log data generated throughout the Fortinet Security Fabric, providing visibility into network activity, security events, and potential threats. This information is crucial for monitoring, analysis, and compliance reporting.
37. Explain the purpose of FortiManager in a Fortinet deployment.
Ans:
- FortiManager is a centralized management platform for Fortinet devices.
- It streamlines configuration management, policy enforcement, and firmware updates across multiple FortiGate devices, ensuring consistency and efficiency.
- Its primary purpose is simplifying the configuration, monitoring, and updating of various Fortinet devices, particularly FortiGate firewalls.
- FortiManager enhances the efficiency and effectiveness of managing security policies across distributed networks.
38. How does Fortinet approach threat intelligence and stay updated on emerging threats?
Ans:
Fortinet employs FortiGuard Labs to gather threat intelligence. FortiGuard Labs continuously monitors global threat landscapes, analyzes threats, and provides real-time updates to Fortinet’s security solutions.
40. What is SSL/TLS inspection, and how does Fortinet handle it for encrypted traffic?
Ans:
- SSL/TLS inspection involves decrypting and inspecting encrypted traffic to detect and prevent threats.
- Fortinet devices, like FortiGate, can perform SSL/TLS inspection, allowing them to analyze encrypted content for potential threats.
- SSL/TLS inspection, also known as SSL/TLS decryption or SSL/TLS interception, decrypts and inspects encrypted traffic that flows through a network.
- This is crucial for security appliances like firewalls to analyze the content of encrypted connections, as many threats can be hidden within encrypted communications.
41. What is Fortinet’s approach to threat intelligence?
Ans:
Fortinet employs a global threat intelligence network called FortiGuard. It continuously collects and analyzes threat data from various sources worldwide. This intelligence is then used to enhance the effectiveness of Fortinet’s security solutions by providing up-to-date threat detection and prevention capabilities. Fortinet takes a comprehensive and proactive approach to threat intelligence as a critical component of its cybersecurity strategy.
42. How does Fortinet’s firewall technology work?
Ans:
A firewall is a network security device that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. Fortinet’s firewall technology provides a comprehensive security solution by combining stateful inspection, intrusion prevention, VPN, and application control to protect networks from various threats.
43. What do you know about Fortinet and its products?
Ans:
Fortinet is a global leader in cybersecurity solutions. It provides various products and services, including firewalls, antivirus, intrusion prevention, and secure SD-WAN. Their FortiGate firewall series is widely used for network security. Fortinet is a global cybersecurity company that provides various security solutions for businesses, enterprises, and service providers.
44. Can you explain the concept of sandboxing in Fortinet’s security solutions?
Ans:
Sandboxing involves running suspicious files in a virtual environment to analyze their behaviour. Fortinet’s sandboxing technology, integrated into FortiSandbox, helps identify and block advanced threats before they can harm the network. The concept is to create a virtual environment, often called a “sandbox,” where suspicious files or objects can be executed and observed without posing a risk to the production network.
45. What are the critical components of Fortinet’s Security Fabric?
Ans:
Fortinet’s Security Fabric comprises interconnected security technologies that share threat intelligence. Key components include:
- FortiGate firewalls
- FortiManager
- FortiAnalyzer
- FortiClient
- FortiSIEM
46. Explain the purpose of Fortinet’s FortiManager.
Ans:
FortiManager is a centralized management and monitoring solution provided by Fortinet, a leading cybersecurity company. The primary purpose of FortiManager is to streamline and enhance the management of Fortinet’s security infrastructure, particularly FortiGate firewalls. It is a central point for configuring, monitoring, and updating multiple Fortinet devices, enabling organizations to manage their network security infrastructure efficiently.
47. How does Fortinet’s FortiGuard service contribute to cybersecurity?
Ans:
FortiGuard provides real-time threat intelligence, updating Fortinet devices about the latest threats. It includes antivirus, web filtering, intrusion prevention, and other security services.
48. Can you explain a Fortinet firewall and its key features?
Ans:
Fortinet’s firewall solutions are designed to provide comprehensive network protection by inspecting and controlling incoming and outgoing network traffic based on predetermined security rules. The Fortinet firewall is a crucial component in Fortinet’s integrated security platform, offering features that go beyond traditional packet filtering.
- Unified Threat Management (UTM)
- Next-Generation Firewall (NGFW)
- Intrusion Prevention System (IPS)
- Virtual Private Network (VPN) Support
- Web Filtering
- Application Control
- Identity-Based Policies
- Security Fabric Integration
- Advanced Threat Protection
- Logging and Reporting
49. How does VPN work, and what types of VPN does Fortinet support?
Ans:
VPN (Virtual Private Network) allows secure communication over an untrusted network. Fortinet supports various VPN types, including IPsec VPN, SSL VPN, and others, providing encrypted connections for remote access or site-to-site connectivity.
50. How does FortiGuard contribute to Fortinet’s security solutions?
Ans:
FortiGuard is Fortinet’s threat intelligence and research service. It provides real-time updates on the latest threats, helping Fortinet products stay current and protect against emerging cybersecurity threats. It plays a crucial role in fortifying Fortinet’s security offerings by providing a range of services, including threat intelligence, antivirus protection, intrusion prevention, web filtering, and more.
51. How does Fortinet support cloud security?
Ans:
Fortinet offers cloud security solutions, including FortiGate VMs for virtualized environments, FortiWeb for web application security, and FortiCASB for cloud access security broker capabilities, ensuring comprehensive security in cloud deployments. Their approach involves integrating security into various aspects of cloud infrastructure to provide a robust and scalable security posture.
52. What is SD-WAN, and how does Fortinet play a role?
Ans:
SD-WAN, or Software-Defined Wide Area Networking, is a technology that enables organizations to simplify the management and operation of their wide area networks (WANs) by using software-based controls and automation. It allows for the dynamic and intelligent routing of traffic across different WAN links, often including broadband internet connections, to optimize performance, enhance security, and reduce costs.
53. How does Fortinet address the challenges of securing IoT devices within a network?
Ans:
Fortinet provides specialized security solutions for IoT devices, including FortiNAC, which helps discover, classify, and secure IoT devices on the network. FortiGate’s security features extend to IoT devices, ensuring comprehensive protection.
54. Discuss Fortinet’s role in securing multi-cloud environments.
Ans:
Fortinet offers solutions like FortiGate VMs, FortiWeb, and FortiCASB to secure multi-cloud environments. FortiGate provides consistent security policies across different cloud platforms, FortiWeb protects web applications, and FortiCASB offers visibility and control over cloud applications.
55. How does Fortinet help organizations achieve Zero Trust Network Security?
Ans:
Fortinet supports Zero Trust Network Security by implementing least privilege access, continuous monitoring, and dynamic trust verification. Technologies such as Zero Trust Network Access (ZTNA) and Network Access Control (NAC) contribute to building a Zero Trust architecture.
56. How does FortiToken contribute to multi-factor authentication in Fortinet’s security ecosystem?
Ans:
FortiToken is a multi-factor authentication solution from Fortinet. It enhances security by requiring users to provide a second authentication factor (typically a one-time password) and their regular credentials, adding an extra layer of protection against unauthorized access.
57. Discuss Fortinet’s approach to securing remote access and the role of VPN solutions.
Ans:
Fortinet’s FortiGate devices provide secure remote access through VPN solutions. Whether using SSL VPN or IPsec VPN, FortiGate ensures encrypted and authenticated connectivity for remote users, maintaining data security in transit.
58. What is Fortinet’s approach to Zero Trust Security?
Ans:
Fortinet embraces the Zero Trust Security model by assuming that no entity—inside or outside the network—should be trusted by default. Fortinet’s products, such as FortiGate, FortiSandbox, and FortiAuthenticator, work together to enforce rigorous authentication, access controls, and continuous monitoring, aligning with the principles of Zero Trust.
59. How does Fortinet assist organizations in achieving compliance?
Ans:
Fortinet products help organizations meet regulatory compliance by providing features like logging, reporting, and access controls. The security appliances assist in enforcing policies that align with specific compliance standards, such as PCI DSS, HIPAA, or GDPR.
60. How does Fortinet address the challenges of securing IoT devices in a network?
Ans:
Fortinet provides security solutions, such as FortiNAC, that are designed to discover, profile, and control IoT devices on a network. By implementing network access controls, Fortinet helps organizations secure and manage increasing numbers of IoT devices with diverse security requirements.
61. Explain Fortinet’s role in the NIST Cybersecurity Framework.
Ans:
Fortinet provides solutions aligning with the NIST Cybersecurity Framework by offering capabilities for identifying, protecting, detecting, responding to, and recovering cybersecurity incidents. This framework helps organizations manage and improve their cybersecurity posture.
62. How does Fortinet address the challenge of securing IoT devices in a network?
Ans:
Fortinet provides solutions like FortiNAC (Network Access Control) to secure IoT devices. FortiNAC identifies, controls, and monitors IoT devices on the network, ensuring that they meet security policies and are not a source of vulnerabilities.
63. How does Fortinet support secure access for remote users?
Ans:
Fortinet provides solutions like FortiClient and FortiGate VPN to secure remote access. FortiClient offers endpoint security, while FortiGate VPN ensures secure connectivity for remote users, allowing organizations to support and protect their remote workforce effectively.
64. How does FortiSandbox contribute to Fortinet’s security ecosystem?
Ans:
FortiSandbox is Fortinet’s advanced threat detection and analysis solution. It uses sandboxing technology to execute suspicious files in an isolated environment, allowing it to identify and mitigate advanced threats before they impact the network. It plays a crucial role in Fortinet’s security ecosystem by providing an isolated environment for analyzing potentially malicious files and activities.
65. How does FortiGate ensure high availability and reliability in a network?
Ans:
- FortiGate devices support features such as High Availability (HA) clustering, where multiple devices work together to ensure continuous availability.
- This includes failover mechanisms and load balancing to distribute traffic efficiently.
- FortiGate provides high availability and reliability in a network through various features and configurations designed to minimize downtime and maintain continuous operation.
66. Explain the concept of Threat Intelligence in the context of Fortinet.
Ans:
Threat Intelligence refers to the information gathered about cyber threats, including tactics, techniques, and procedures used by attackers. Fortinet leverages Threat Intelligence through services like FortiGuard to enhance its security solutions’ detection and prevention capabilities.
67. How does Fortinet support secure access for remote users?
Ans:
Fortinet supports secure remote access through VPN solutions, and FortiClient is the endpoint security application. FortiClient provides VPN connectivity, antivirus protection, web filtering, and other security features to ensure the security of remote users connecting to the corporate network.
68. Explain the role of FortiManager in a Fortinet infrastructure.
Ans:
FortiManager is the central management tool for Fortinet devices. It provides a centralized platform for configuring, monitoring and managing Fortinet devices across the network. FortiManager streamlines administrative tasks, ensuring consistent security policies and configurations.
69. How does Fortinet contribute to network segmentation and security zoning?
Ans:
Fortinet supports network segmentation and security zoning through features like virtual domains (VDOMs) on FortiGate devices. VDOMs allow administrators to create multiple security domains within a single physical device, enabling effective segmentation and control over network traffic.
70. Discuss Fortinet’s approach to threat intelligence and sharing.
Ans:
Fortinet emphasizes threat intelligence through FortiGuard, its comprehensive threat intelligence service. FortiGuard provides real-time updates on the latest threats, and Fortinet encourages sharing threat intelligence across its user community to enhance collective cybersecurity defences.
71. Explain what NAT is and how it is used in Fortinet devices.
Ans:
Network Address Translation (NAT) is a method used to map private IP addresses to a public IP address. Fortinet devices use NAT to allow multiple devices on a private network to share a single public IP address for internet access.
72. How does Fortinet ensure the high availability of its products?
Ans:
Fortinet achieves high availability through features like device clustering and redundant hardware configurations. Clustering allows multiple devices to work together as a single logical unit, ensuring continuous operation even if one fails.
73. What is the role of FortiGuard in Fortinet’s security ecosystem?
Ans:
FortiGuard is Fortinet’s threat intelligence and research arm. It provides real-time updates on security threats, vulnerability signatures, and other security-related information to Fortinet devices, ensuring they are equipped to defend against the latest threats.
74. Explain the purpose of Fortinet’s FortiManager.
Ans:
FortiManager is a centralized management solution allowing administrators to configure, monitor, and report multiple Fortinet devices from a single console. It streamlines management tasks, enhances visibility, and ensures consistent policies across the network.
75. What is SSL VPN, and how does Fortinet implement it?
Ans:
SSL VPN (Secure Socket Layer Virtual Private Network) allows remote users to access the network securely. Fortinet implements SSL VPN through its FortiGate devices, providing encrypted communication between the hidden user and the corporate network.
76. How does Fortinet address the challenges of advanced threats and zero-day attacks?
Ans:
Fortinet employs a multi-layered security approach, combining signature-based detection, behavioural analysis, and threat intelligence. FortiGuard Labs provides real-time updates to Fortinet devices, enhancing their ability to detect and mitigate emerging threats. Fortinet addresses the challenges of advanced threats and zero-day attacks through a comprehensive, multi-layered security approach.
77. What is the role of Fortinet’s FortiManager and FortiAnalyzer?
Ans:
- FortiManager is a centralized management solution for Fortinet devices, allowing administrators to configure and monitor multiple FortiGate devices.
- FortiAnalyzer is a centralized logging and reporting tool for analyzing security data and generating reports.
- FortiManager and FortiAnalyzer are integral components of Fortinet’s Security Fabric, each serving distinct yet complementary roles in the management, analysis, and optimization of network security.
78. What is Fortinet’s Security Fabric, and how does it enhance network security?
Ans:
Fortinet’s Security Fabric is an integrated cybersecurity architecture that connects different security solutions to work together as a unified system. It enhances network security by enabling seamless communication and threat intelligence sharing between Fortinet devices.
79. Can you discuss the advantages of implementing Fortinet’s SD-WAN solutions?
Ans:
- Fortinet’s SD-WAN solutions offer improved network performance, cost savings, and enhanced security.
- Challenges may include proper configuration and integration with existing network infrastructure.
80. Explain the concept of Unified Threat Management.
Ans:
UTM integrates multiple security features into a single platform to provide comprehensive protection against various threats. Fortinet implements UTM through its FortiGate firewall devices, which combine features such as firewall, antivirus, intrusion prevention, VPN, and web filtering, among others, into a unified solution.
81. What is the purpose of FortiGate in Fortinet’s product portfolio?
Ans:
FortiGate is a critical component of Fortinet’s product lineup. It is a next-generation firewall that integrates various security features such as firewall, VPN, intrusion prevention, antivirus, and web filtering. FortiGate is designed to provide comprehensive threat protection and secure the network infrastructure.
82. How does Fortinet address the challenges of securing modern networks?
Ans:
Fortinet has a holistic approach to cybersecurity, addressing the challenges of modern networks through solutions like FortiCloud and FortiCASB. FortiCloud offers cloud-based security services, and FortiCASB (Cloud Access Security Broker) helps organizations secure their cloud applications and data.
83. How does Fortinet contribute to threat intelligence?
Ans:
Fortinet’s FortiGuard Labs provides real-time threat intelligence by constantly analyzing global threat landscapes. This intelligence is integrated into Fortinet’s security solutions, enabling them to identify and mitigate emerging threats. This proactive approach enhances the effectiveness of Fortinet’s security products.
84. What is the role of Fortinet’s FortiGate in a network security setup?
Ans:
FortiGate is a series of firewalls produced by Fortinet. It provides a wide range of security and networking functions, including firewall, VPN, intrusion prevention, antivirus, and web filtering. Its role is to protect a network from various cyber threats.
85. How does Fortinet’s threat intelligence contribute to cybersecurity?
Ans:
Fortinet’s threat intelligence provides up-to-date information on emerging threats and vulnerabilities. It enables Fortinet’s security solutions to make informed decisions, enhancing the ability to detect and respond to new and evolving cyber threats.
86. How does Fortinet address the evolving threat landscape?
Ans:
Fortinet employs a proactive and adaptive approach to cybersecurity. They continuously update their threat intelligence, leverage artificial intelligence and machine learning, and provide regular firmware updates to ensure their security solutions are equipped to handle the latest and emerging threats.
87. How does Fortinet contribute to SD-WAN solutions?
Ans:
Fortinet offers SD-WAN capabilities through its FortiGate devices. Integrating SD-WAN into FortiGate allows organizations to optimize and secure their wide area network traffic, providing efficient and secure connectivity between different locations.
88. How does Fortinet address the challenges of securing cloud environments?
Ans:
Fortinet offers a range of solutions for securing cloud environments, including FortiGate-VM for virtualized environments, FortiWeb for web application security, and FortiCASB for cloud access security. These solutions help organizations extend their security policies to protect data and applications in the cloud.
89. How does Fortinet contribute to threat intelligence?
Ans:
Fortinet collects threat intelligence from its global network of sensors and FortiGuard Labs. This intelligence is used to update security signatures and enhance the ability of Fortinet’s products to detect and mitigate emerging threats. Fortinet contributes to threat intelligence through its dedicated threat research and intelligence team, FortiGuard Labs.
90. How does Fortinet ensure the scalability of its security solutions in large networks?
Ans:
Fortinet’s security solutions are designed to scale horizontally, allowing organizations to add devices and resources as their network grows. Using purpose-built hardware and optimized software also ensures high performance, even in large and complex network environments.
91. What is the purpose of Fortinet’s FortiAnalyzer?
Ans:
FortiAnalyzer is a centralized logging and reporting appliance that collects and analyzes log data from Fortinet devices. It provides insights into network traffic, security events, and user activity, helping organizations monitor and respond to potential threats.FortiAnalyzer is a centralized logging, analysis, and reporting solution within the Fortinet security ecosystem.
92. How does Fortinet address the challenges of secure remote access?
Ans:
- Fortinet offers solutions like FortiClient for secure remote access. It provides VPN capabilities, endpoint protection, and integration with FortiGate firewalls to ensure a secure connection for remote users.
- Fortinet addresses the challenges of secure remote access through various technologies and solutions designed to provide safe, reliable, and user-friendly remote connectivity.
93. What is FortiGuard, and how does it enhance security offerings?
Ans:
- FortiGuard is Fortinet’s threat intelligence and research division.
- It provides real-time updates on the latest threats and vulnerabilities, enabling Fortinet devices to have up-to-date protection against emerging cyber threats.
- It plays a crucial role in enhancing Fortinet’s security offerings by providing real-time threat intelligence, updates, and services to Fortinet’s cybersecurity solutions.
94. How does Fortinet address SD-WAN in its solutions?
Ans:
Fortinet provides SD-WAN capabilities through its FortiGate appliances. It allows organizations to optimize and secure their wide-area network connections by dynamically routing traffic based on application performance and security policies. Fortinet’s SD-WAN solutions aim to optimize and ensure wide-area networks by leveraging software-defined principles.
95. What is the purpose of FortiGate in the Fortinet product portfolio?
Ans:
FortiGate is Fortinet’s flagship product and is a next-generation firewall that provides comprehensive security features, including firewall, VPN, intrusion prevention, antivirus, and application control. That highlights the purpose of FortiGate:
- Web Filtering
- Unified Threat Management (UTM)
- Firewall Protection
- Intrusion Prevention System (IPS)
- Antivirus and Antimalware
96. What is FortiManager, and how does it contribute to the security ecosystem?
Ans:
FortiManager is a centralized management solution for Fortinet devices. It provides a single control point for configuring and managing multiple FortiGate devices, streamlining security policy management and ensuring consistency across the network.
97. Explain the role of FortiAnalyzer in a Fortinet deployment.
Ans:
FortiAnalyzer is a centralized logging and reporting solution. It collects and analyzes log data from Fortinet devices, providing insights into network traffic security events and facilitating compliance reporting. Role of FortiAnalyzer:
- Log Collection and Storage
- Security Event Analysis
- Reporting and Dashboards
- Alerts and Notifications
- Historical Analysis
98. How does Fortinet address zero-day threats?
Ans:
Fortinet addresses zero-day threats by utilizing advanced threat detection mechanisms, including FortiSandbox. FortiSandbox analyzes suspicious files in a secure environment to detect and mitigate previously unknown threats. Fortinet addresses zero-day threats through a multi-layered security approach, and FortiSandbox plays a crucial role in detecting and mitigating these advanced threats.
99. Discuss the importance of threat intelligence in the security approach.
Ans:
Threat intelligence enhances security by providing up-to-date information about emerging threats. Fortinet incorporates threat intelligence into its solutions to improve the detection and response capabilities against evolving cyber threats. Threat intelligence plays a critical role in Fortinet’s security approach, contributing to the effectiveness and responsiveness of its cybersecurity solutions.
100. How does Fortinet contribute to the Zero Trust Security Model?
Ans:
- Fortinet promotes the Zero Trust Security Model by implementing rigorous authentication, continuous monitoring, and most minor privilege access controls.
- Through features like FortiAuthenticator and FortiNAC, Fortinet helps organizations enforce strict access policies and verify the identity of users and devices.
- The Zero Trust Security Model is based on the idea that organizations should not automatically trust entities inside or outside their network and should verify and authenticate every user, device, and application attempting to connect to the network.






