
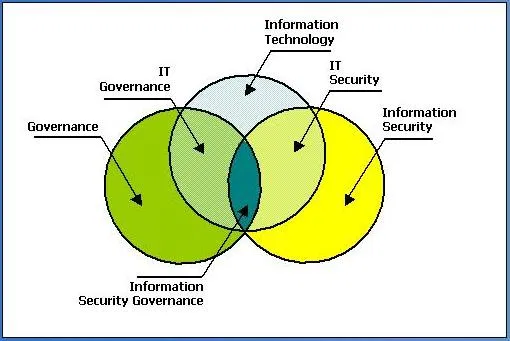
The process of establishing and maintaining a framework and supporting management structure and processes to provide assurance that information security strategies are aligned with and support business objectives, are consistent with applicable laws and regulations through adherence to policies and internal controls, and provide assignment of responsibility, all in an effort to manage risk.
- ITU-T X.1054, Governance of Information Security, defines information security governance as “the system by which an organization’s information security-related activities are directed and controlled.”
- More generally, the term security governance encompasses governance concerns for cyber security, information security, and network security.
Governance

Establishment of policies and continuous monitoring of their proper implementation by the members of the governing body of an organization. Governance includes the mechanisms required to balance the powers of the members (with the associated accountability) and their primary duty of enhancing the prosperity and viability of the organization.
Information Security Mission
The mission of Information Security is to design, implement and maintain an information security program that protects the Medical School’s systems, services and data against unauthorized use, disclosure, modification, damage and loss. The Information Security Department is committed to engaging the Medical School community to establish an appropriate information security governance structure that enables collaboration and support for new information security initiatives.
Information Security Approach
- Foster a culture of empowerment, accountability and continuous improvement
- Demonstrate a consistent Information Security and Compliance message through effective communication and partnerships
- Prioritize information assets and processes
- Strive to influence positive and meaningful change within IT and UMMS as a whole
- Identify and prioritize risks
- Implement foundational security controls across key assets
- Build a targeted security capability model
- Develop the security improvement road map
- Ensure governance and organization engagement
Information Security Scope
- Protect the assets of the Medical School through secure design, operations and management governance
- Align work and work products within UMMS-relevant laws, regulations and requirements
- Apply a risk-based approach to our security design, guidance and decisions
- Continuously safeguard against current and potential threats
Information Security Importance
The importance of a proactive Information Security team is to provide the framework for keeping sensitive data confidential and available for authorized use while building effective relationships with our business and IT partners.
Information Security Principles and Goals
- Protecting the confidentiality of data
- Preserving the integrity of data
- Promote the availability of data for authorized use
- Proactively identify risks and propose viable mitigation steps
- Cultivate a proactive risk management culture
- Implement “best practice” threat management strategies and processes to reduce threats
The Controls Framework
- Policy Development
- Security Awareness
- Internal Risk Assessments
- Third-party Risk Assessments
- Risk Remediation Support
- Secure SDLC
- Record retention schedule management
- SOC 2 Facilitation
- Threat protection & monitoring
- Malware detection (ePO)
- Threat correlation & reporting
- Incident response
- Computer forensics
- Vulnerability management
- Application scanning
- Penetration testing
- Campus & industry threat collaboration
- Security training administration
Characteristics of effective security governance
The eleven characteristics of effective security governance are critical for an effective enterprise information security information program. They are:
- It is an institution-wide issue
- Leaders are accountable
- It is viewed as an institutional requirement (cost of doing business)
- It is risk-based Roles,
- responsibilities and segregation of duties are defined
- It is addressed and enforced in policy
- Adequate resources are committed
- Staff are aware and trained
- A development life cycle is required
- It is planned, managed, measurable and measured
- It is reviewed and audited
Organizational Structure
Unplanned and uncoordinated localization of authority poses great challenges for institution-wide compliance with security, copyright, privacy, identity and other regulation. It makes it awkward for CIOs to account well for the breadth and depth of overall IT activity, and it can be inefficient. Localization of authority in some areas is critical. The question is not “to centralize or not to decentralize” but where to centralize (or not) and how to harmonize institutional efforts and investments in IT.
IT governance-related committees include :
- Top-level IT steering committee for oversight of major IT policies and initiatives
- IT advisory committees for administration and teaching and learning
- IT initiative specific committees for items like enterprise resource planning, security or business continuity
Governance structures depend on desired outcomes
CERT GES [3] describes structure based on desired outcomes.
- Top revenue growth – decentralized to promote customer responsiveness and innovation
- Profit – centralized to promote sharing, reuse and efficient asset utilization
- Multiple performance goals – blended centralized and decentralized
Information Security Governance Structures
The NIST Security Handbook [5] states that governance is highly dependent on the overall organization structure.
- Centralized maintain budget control and ensure implementation and monitoring of information security controls.
- Decentralized have policy and oversight responsibilities and budget responsibilities for their departmental security program not the operating unit information security program. Reporting structures are different as well.
- Governance structures can be hybrid, with a combination of characteristics from both centralized and decentralized.
Political Archetypes
Weill and Ross use political archetypes in IT Governance [3] to describe people or groups who have decision rights.
- Business monarchy: Senior business executives make IT decisions
- IT monarchy: IT executives make IT decisions
- Feudal: Business unit leaders make IT decisions to optimize local needs, but do not facilitate enterprise decision-making.
- Federal: Coordinated IT decision-making between the center and the business units.
- IT duopoly: IT executives and one other group (such as senior executives or business units) make IT decisions.
- Anarchy: Individual users or small groups make IT decisions Anarchy is expensive, difficult to support and rare, but sometimes used when very rapid customer responsiveness is needed.
Roles and Responsibilities
The ISO or CISO is an emerging profession with highly-motivated individuals seeking their own professional development through membership in organizations, participation in training where they can find it and constant sharing of ideas and advice with others both internally and externally to their organization. There does not seem to be a clearly defined path for this new subfield within IT. The vast majority of those in an ISO/CISO position held previous positions in IT and came from higher education backgrounds. Institutions appear to be recruiting security officers from IT managerial ranks. Often these folks started with very strong technical experience and have now developed skills in business process analysis, thus moving away from hands-on activities .
- In addition to certifications, ISOs find the following “soft skills” beneficial .
- Reputation building
- Campus-wide coordination and communication
- Collaboration
- Campus-wide profiles
- These soft skills are critical for effective engagement with diverse campus audiences.
- Senior leader of the institution
- Deans, Department Chairs and Directors
- IT managers
- Auditors
- Attorneys
- Human Resources
- Faculty
- Staff
- Students
- Primary ISO responsibilities
- Development and enforcement of security policies and procedures
- Risk management
- Security awareness program
- Incident management and forensics
- Business continuity
- Disaster recovery
- Supportive functions of an ISO
- Application and system security
- Network security
- Access control
- Authentication and authorization
- Identity management
Decision-Making Structures
Weill and Ross [3] describe organizational units and roles responsible for making IT decisions, such as committees, executive teams, and business/IT relationship managers.
- Executive or senior management committees
- IT leadership committee
- Process teams with IT members
- Business/IT relationship managers
- IT council of IT and business executives
- Architecture committee
- Capital improvement committee
Security Governance and Security Management
To better understand the role of security governance, it is useful to distinguish between information security governance (previously defined), information security management, and information security implementation/operations. ISO 27000 defines information security management as follows:
- The supervision and making of decisions necessary to achieve business objectives through the protection of the organization’s information assets. Management of information security is expressed through the formulation and use of information security policies, procedures and guidelines, which are then applied throughout the organization by all individuals associated with the organization.
And information security implementation/operations can be defined in this fashion:
- The implementation, deployment and ongoing operation of security controls defined within a cyber security framework.
security program
- The management, operational, and technical aspects of protecting information and information systems. A security program encompasses policies, procedures, and management structure and mechanism for coordinating security activity.
2.1 Information Security Management System Element
Information Security Governance Objectives
- Part of the objectives of ISG is to ensure that there is an accurate security framework that meets the objectives of the organization.
- Candidates are tested on the broad requirements for effective ISG and what is required to develop a framework with an accompanying plan of action for implementing it.
- Candidates will be required to understand the contents of the framework, which will generally consist of:
- A comprehensive security strategy that is intrinsically linked with business objectives
- Governing security policies that address each aspect of strategy, controls and regulation
- A complete set of standards for each policy to ensure that procedures and guidelines comply with policy
- An effective security organizational structure void of conflicts of interest and with sufficient authority and adequate resources
- Institutionalized metrics and monitoring processes to ensure compliance, provide feedback on effectiveness, and provide the basis for appropriate management decisions.
- The implementation and management of security programs is discussed in detail in the CISM review manual under the topic “Information Security Program Development and Management”, where the different frameworks are discussed. One such framework that candidates will need to focus on highly is the SABSA framework for security management.
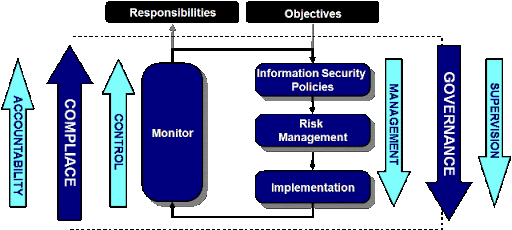
Importance of Information Security Governance
As dependence on information grows, the criticality of ISG increases as well. Organizations are beginning to appreciate information and the knowledge based on it, without which conducting business would not be possible. Candidates are therefore tested on the series of benefits that are experienced under effective ISG. These include:
- Providing assurance of policy compliance. Candidates will be required to show an understanding of how assurance can be made to ensure policy compliance.
- The ability to address the increasing potential for civil or legal liability inuring the organization.
- The ability to improve trust in customer relationships
- The methods that can be taken to protect the organization’s reputation
- The methods of effective management of information security resources
Outcomes of Information Security Governance
- Information security governance contains a structured set of elements that are required to provide senior management with assurance that its major objectives are captured in the organization’s security posture. After the elements have been put in place, management can rest assured that adequate and effective information security will protect the organization’s most critical and important assets.
- ISG is mainly involved in the development, implementation and management of a security program that achieves six outcomes that candidates will be tested on. These include:
- Strategic alignment: Emphasis here is placed on aligning information security with the respective business strategy in order to support the objectives of the organization
- Risk management: Candidates are tested on the risks facing the organization and how they can be mitigated with the negative impacts on business reduced to an acceptable level.
- Value delivery: The exam lays emphasis on security investments intended to support business. Candidates are tested on measures that ensure security investments are continuously improved by meeting various objectives.
- Resource management: Candidates will need to understand various points here, for example, it is necessary that knowledge which is captured is made available across the organization, proper practices are followed for document security, long lasting security architectures are designed that define and utilize resources.
- Performance measurement: Candidates will be tested on the various reporting metrics and how effective reporting is done on information security processes to meet the desired objectives, and how independent assurance from external audits and assessments can be achieved.
- Integration: ISG ensures that the relevant assurance factors are integrated to make sure that processes operate as intended from end to end. Candidates are tested on the integration and coordination of the various assurance functions so as to ensure complete security, formal relationships between assurance functions, and the roles and responsibilities between assurance functions.
conclusion
Finally, candidates should know that ISG is the responsibility of the board of directors and executive management and should be a transparent and integral part of enterprise governance, complementing or encompassing the IT governance framework. This is supported by the developers of the Business Model for Information Security (BMIS), who state that “It is no longer enough to communicate to the world of stakeholders why the organization exists and what constitutes success, we must also communicate how we are going to protect our existence.”





