
Zoho is a leading software company offering a wide range of cloud-based applications and services for businesses. With a comprehensive suite of tools covering everything from CRM and project management to finance and HR, Zoho empowers organizations of all sizes to streamline their operations and enhance productivity. Known for its user-friendly interfaces and customizable solutions, Zoho continues to innovate, providing cutting-edge technology that meets the evolving needs of modern businesses worldwide.
1. What is the Difference between Static and Dynamic memory allocations?
Ans:
Stationary memory allocation is when the memory size demanded for a program’s variables is determined at collect time, and the allocation can not be changed at runtime. This generally involves fixed-size data structures like arrays. On the other hand, dynamic memory allocation occurs when the Memory is allocated during runtime using pointers, and the size can be acclimated as demanded. Dynamic allocation allows for further flexible memory operation but requires careful running to avoid memory leaks and fragmentation. In languages like C, dynamic Memory is managed using functions like malloc() and free(), whereas languages like Java automate this with scrap collection.
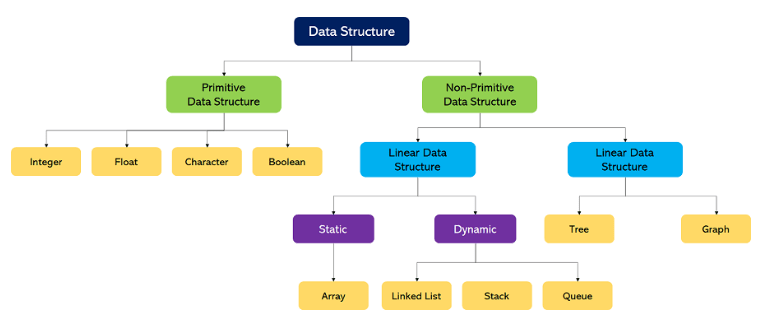
2. What’s a Data Structure?
Ans:
A data structure is a particular way of organizing data in the computer so that it can be used efficiently. Different data structures are suited to other types of operations, and some are primarily technical to specific tasks. Data structures provide large quantities for efficient use management, simple to large databases, and indexing services like hunt machines. Introductory data structures include arrays, linked lists, heaps, and ranges. More complex structures include double trees, stacks, and graphs.
3. What’s the difference between ArrayList and LinkedList?
Ans:
- In Java, ArrayList and LinkedList are both executions of the List interface but differ in their underpinning infrastructures and performance counteraccusations.
- ArrayList is backed by a dynamic array, meaning access to rudiments is quick and effective for listed operations.
- Still, resizing the ArrayList can be expensive if the array needs extended. LinkedList, on the other hand, is enforced using a twice-linked list.
- It offers brisk insertion and omission at any point in the list, especially helpful for operations at the head and tail.
4. What’s a Bubble-kind Algorithm?
Ans:
Bubble kind is a simple sorting algorithm that constantly steps through the list to be sorted, compares each brace of conterminous particulars and barters them if they’re in the wrong order. The pass through the list is repeated until no swaps are demanded, which means the list is sorted. Although simple to understand and apply, the Bubble kind is hamstrung for large datasets as its average and worst-case complexity are O( n ²), where n is the number of sorted particulars. Despite this, it has notable uses in scripts where the data is nearly sorted, or the dataset is small.
5. What are the OOPs generalities?
Ans:
- Object-acquainted Programming( OOP) is a programming paradigm grounded on the conception of” objects”, which can contain data in the form of fields( frequently known as attributes or parcels) and law in the form of procedures.
- The four primary OOP generalities are Encapsulation, which keeps the data safe from outside hindrance and abuse; heritage, which helps in creating new classes from being bones; Polymorphism, which allows styles to do different effects grounded on the object it’s acting upon; and Abstraction, which hides complex realities while exposing only the necessary corridor of objects.
6. What’s the difference between an abstract class and an interface in Java?
Ans:
| Feature | Abstract Class | Interface |
|---|---|---|
| Definition | An abstract class can have abstract methods along with concrete methods. | An interface can only have abstract methods and constants. |
| Variables | It can have instance variables. | It cannot have instance variables. |
| Constructors | Can have constructors. | Cannot have constructors. |
| Instantiation | Cannot be instantiated directly. | Cannot be instantiated directly. |
| Subclassing | Subclasses extend one abstract class. | Classes can implement multiple interfaces. |
7. What’s the difference between TCP and UDP?
Ans:
- TCP( Transmission Control Protocol) and UDP( stoner Datagram Protocol) are the two core protocols of the IP suite.
- TCP is connection-acquainted, meaning a connection is established and maintained until the operation programs at each end have finished swapping dispatches.
- It provides dependable, ordered, and error-checked delivery of a sluice of bytes.
- UDP is connectionless, meaning it doesn’t guarantee communication delivery, order, or error checking.
- This makes UDP brisk and more effective for operations that can tolerate some data loss, such as streaming audio and videotape.
8. What’s a mincing function?
Ans:
A mincing function is an algorithm that takes an input( or’ communication’) and returns a fixed-size string of bytes, generally a condensation unique to each unique input. The affair called the hash value, should immaculately not be reversible, meaning it should be computationally infeasible to reconstruct the original input given only the hash affair. Hash functions are generally used in data structures like hash tables for effective data reclamation, cryptography for ensuring data integrity, and various operations where unique identifiers are necessary.
9. How do you design a program using Java?
Ans:
- Designing a program in Java generally involves several crucial ways: defining the problem, creating a suitable class structure, and enforcing classes. First, quickly outline what the program is supposed to do.
- Also, identify the objects you need to model in the program and design classes and interfaces that synopsize these objects’ parcels and actions.
- Java programs are generally structured around classes and objects, using heritage and interfaces to enhance reusability and maintainability.
10. What’s normalization in the design of a database?
Ans:
Normalization is a systematic approach used in relational database design to reduce redundancy and facilitate data integrity. It involves organizing the fields and tables of a database to minimize redundancy and reliance. Normalization is achieved through a series of ways called standard forms; each standard form addresses a particular type of anomaly and has rules that must be followed to achieve that form. The thing is to make the database more effective and reduce the liability of data anomalies during data operations like insertion, update, or omission.
11. What’s the difference between mound and line data structures?
Ans:
- Heaps and ranges are abecedarian data structures used to store collections of rudiments, but they operate in different ways.
- A mound follows the Last First Eschewal ( LIFO) system, where the last element added to the mound is the first to be removed.
- Everyday mound operations include pushing( adding) an item to the top, popping( removing) the top item, and skimming at the top item without removing it.
- A line follows the First In First Out( FIFO) principle, where the first element added is the first one to be removed.
12. How is a mound enforced?
Ans:
A mound can be enforced using various data structures, but arrays and linked lists are the most common. An array-grounded perpetration uses a fixed-size array and an indicator (representing the top of the mound). Rudiments are added or removed from the end of the array as the mound grows or shrinks. In linked list perpetration, the mound is dynamic and can grow as demanded; each new element is added to the head of the list (drive operation), and junking (pop operation) also occurs at the head. Both executions give the necessary LIFO geste of the mound.
13. What are the advantages of interpretation control systems similar to Git?
Ans:
Interpretation control systems( VCS) similar to Git offer multitudinous benefits for software development. They enable multiple inventors to work on the same design contemporaneously without noticing each other’s changes. Git provides a robust system for tracking changes, allowing inventors to return to former performances of law, review history, and manage different performances( branches) of systems efficiently. This is pivotal for error correction and understanding design elaboration. Also, Git supports distributed development, enabling inventors to work offline and attend with others later.
14. What kinds of joins are there in SQL?
Ans:
SQL supports several types of joins, combining rows from two or more tables grounded on affiliated columns. The primary joins are:
- INNER JOIN (returns rows when there’s a match in both tables),
- LEFT JOIN (returns all the rows from the left table and matched rows from the right table;
- If there is no match, return NULL on the right side), RIGHT JOIN (opposite of LEFT JOIN), and
- FULL OUTER JOIN (returns rows when there’s a match in one of the tables).
There are also variations like CROSS JOIN, which produces a Cartesian product of all rows in the tables involved, and tone JOIN, which is a regular join but involves the same table.
15. What’s the difference between JRE, JDK, and JVM?
Ans:
- JRE( Java Runtime Environment), JDK (Java Development Kit), and JVM (Java Virtual Machine) are all core factors of Java programming, but each serves a different purpose.
- The JVM is an abstract computing machine that enables the computer to run a Java program.
- The JRE is Java’s on-stringer part that creates the JVM. It includes the JVM, core libraries, and factors demanded for Java operations.
- The JDK includes the JRE and adds the compilers and tools( like JavaDoc and Java Debugger) demanded to develop Java operations.
16. When is serialization used?
Ans:
Serialization is used when data structured as objects need to be saved, transmitted, or participated in a format that can be fluently reconstructed latterly in the same or a different computing terrain.
Typical uses of serialization include:
- Storing object countries in databases.
- Transferring objects over a network between servers or guests.
- Caching objects in lines.
Serialization is pivotal for distributed operations where cases of objects need to cut network bumps. It helps convert complex objects into a byte sluice that can be transported fluently and reconstructed into the original object structure.
17. Find the longest subsequence, adding subsequence in the given array. e,( 3, 4,-1, 0, 6, 2, 3).
Ans:
We need a system to track the possible sequences efficiently to find the longest adding subsequence in the array( 3, 4,-1, 0, 6, 2, 3). The longest adding subsequence in this array is(- 1, 0, 2, 3). This sequence is constructed by relating the incremental growth of values, disregarding any former lower values that can not extend to a longer sequence. Dynamic programming methods are generally used for this purpose in more complex scripts, as they give a way to break the problem down into simpler subproblems and use the results of formerly answered subproblems.
18. In a database, are NULL values analogous to those of zero or space?
Ans:
In databases, NULL values represent the absence of a value rather than zero or a space. NULL is used as a placeholder for unknown or irrelevant values. It’s different from zero, which is a number and can be used in computations, and it’s also different from an empty string, which is considered a type of data( a string with a zero-length). NULL values can be tricky in SQL operations because any computation or logical operation involving a NULL value generally results in NULL, reflecting the unknown nature of the value.
19. What’s the difference between a pointer and a reference?
Ans:
In C, pointers and references serve analogous purposes but are unnaturally different. A pointer is a variable that holds the memory address of another variable and can be reassigned to another address or set to nullptr. Unequivocal dereferencing is required to pierce the target variable’s value. On the other hand, a reference is an alias for another variable and must be initialized when declared; it can not be later changed to reference another variable. References give more straightforward syntax and further safety in specific scripts because they guarantee the actuality of a beginning object( they can not be null).
20. What’s the difference between call by reference and value?
Ans:
- The difference between call by reference and call by value lies in how arguments are passed to functions.
- In call by value, a copy of the factual parameter is passed to the function, and variations to the parameter within the function don’t affect the original variable.
- In call by reference, a function receives a reference to the factual parameter, and any changes made in the function affect the original variable.
- Call by reference can lead to more effective law( avoiding clones of large structures), but it requires careful running to prevent unintended side goods.
21. What’s a virtual function in C?
Ans:
A virtual function in C is a member function in a base class that you anticipate to stamp in deduced classes. When you use a virtual function, it enables a point known as polymorphism within C. This allows for the magic of deduced class styles through base class pointers or references. This geste is eased by the C runtime using a medium called the vtable, an array of pointers to virtual functions. However, C ensures that the most deduced function is called for that object if a function is declared virtual in a base class.
22. What’s the meaning of” Sockets in OS”?
Ans:
- Sockets are endpoints for transferring and entering data across a network.
- They’re an abecedarian technology in operating systems for network communication, enforced via zilches-handed APIs.
- Sockets allow communication between processes on the same or different machines through defined protocols like TCP( Transmission Control Protocol) and UDP(Stoner Datagram Protocol).
- A socket is associated with a specific protocol, harborage, and IP address, creating a complete system for ensuring data can be routed and entered correctly across the network.
23. What’s a software bug?
Ans:
A software bug refers to an error, swelling, or fault in a software program that causes it to produce incorrect or unanticipated results or to bear in unintended ways. Bugs can stem from miscalculations and crimes made during software development, including crimes in law, design, or sense. They can affect stoner experience, software functionality, and system performance and, in severe cases, lead to system failures or security vulnerabilities. Relating and fixing bugs is a pivotal part of development, generally addressed through testing and debugging processes.
24. What’s the difference between a mound overflow and a mound overflow?
Ans:
A mound overflow and a mound overflow are critical programming crimes involving improper memory use, but they do so in different areas. A mound overflow happens when too important Memory is used on the call mound, generally due to deep or horizonless recursion or by allocating too important space for original variables. A mound overflow occurs when dynamic memory allocation on the mound exceeds the allocated Memory, frequently due to improper running of buffers or incorrect computations of the size demanded. Both can lead to crashes or exploitable vulnerabilities.
25. What’s an impasse in operating systems?
Ans:
An impasse in operating systems occurs when two or more processes stay for the other to release coffers or, more generally, wait for an event that can only be touched off by one of the waiting processes, leading to a deadlock. The four conditions necessary for an impasse are collective rejection (only one process can use a resource at a time), hold and stay (processes holding coffers while waiting for others), no appropriation (coffers can not be forcefully removed from a process), and indirect delay (the presence of an indirect chain of processes). Managing gridlocks involves precluding, avoiding, or detecting and recovering from them.
26. What’s the difference between a switch statement and an if-ended statement in programming?
Ans:
- A switch statement and an- if-additional statement are control inflow structures in programming that direct the inflow grounded on conditions.
- The switch statement is generally used when comparing a single variable against a series of constants, furnishing a cleaner and more effective volition when handling multiple conditions grounded on the same variable.
- In discrepancy, if-ended statements are more flexible and can handle varied conditions that may not relate directly to a single variable’s value.
27. What measures can be taken to guarantee data security in a web operation?
Ans:
Ensuring the security of data in web operations involves multiple layers of protection.
Crucial measures include:
- Using HTTPS to cypher data in conveyance.
- Enforcing strong authentication and authorization practices.
- Securing databases from SQL injection attacks by using set statements.
- Sanitizing stoner inputs to help cross-site scripting( XSS).
Regularly streamlining and doctoring software to close vulnerabilities and conducting security checkups and penetration testing are pivotal.
28. separate between the “throws” and “throw” keywords in Java?
Ans:
In Java,” throw” and” throws” are keywords used for handling exceptions, but they serve different purposes. The” gamble” keyword is used within a system to throw an exception, allowing the System to break average inflow and shoot an error or custom communication to the calling function. On the other hand,” throws” is used in a system’s protestation to indicate that this System might throw certain exceptions, thereby passing the responsibility to handle these exceptions to the calling system.
29. Explain compactly about Python decorators.
Ans:
Python decorators are a design pattern that allows a stoner to add new functionality to a living object without modifying its structure. Decorators are generally called before describing a function you want to embellish. In Python, decorators are enforced as functions (or classes) that take a function as an argument and return a function that enhances or changes the geste of the original function. This point is handy for adding functionalities like logging, access control.
30. Define design patterns and give some exemplifications of patterns you’ve used.
Ans:
A design pattern is a general, applicable result to the general problem within a given environment in software design. Design patterns are templates for breaking issues that can be used in numerous situations. Exemplifications of design patterns include the Singleton, which ensures a class only has one case and provides:
- The global point of access to it.
- The Observer is used to notify multiple objects about any changes without making them dependent on each other.
- Plant pattern provides a way to produce objects without specifying the exact class of objects that will be created.
31. What’s a law review, and what are some stylish practices for conducting a law review?
Ans:
A law review is a methodical examination of computer source law intended to find miscalculations overlooked in the original development phase, perfecting both the quality of software and the inventors’ chops. Stylish practices for conducting a law review include keeping reviews small and focused, using rosters to ensure thickness, furnishing formative and compassionate feedback, clarifying and communicating rendering norms, and incorporating automated tools to catch trivial issues.
32. What’s a database indicator, and how does it facilitate performance?
Ans:
- A database indicator is a data structure that improves the speed of data reclamation operations on a database table at the cost of fresh writes and storehouse space to maintain the indicator data structure.
- Indicators are used to detect data quickly without having to search each row in a database table every time it is penetrated.
- They do this by creating pointers to the rows in a table, which allows the database machine to jump directly to the row with the asked data.
33. What is a thread pool, and how does it work?
Ans:
A thread pool is a collection of pre-instantiated, idle vestments ready to be given work. These are used to manage the thread operation in a program. When a task is introduced, a thread from the pool is awakened, runs the task, and returns to the pool formerly done. This minimizes the outflow associated with thread creation. Thread pools are beneficial in scripts where producing many short-lived vestments is expensive. The system’s effectiveness is bettered by reusing formerly lived vestments, making thread pools ideal for garçon operations and concurrent processing.
34. What do you mean by communication line?
Ans:
A communication line is an asynchronous service-to-service communication used in serverless and microservices infrastructures. Communication ranges provide a dependable, protocol-agnostic system for storing dispatches to be reused later, divorcing the product of information from its consumption. They enable operations to communicate and reuse operations at different rates, perfecting fault forbearance, scalability, and the overall robustness of the operation running.
35. What’s a cargo balancer, and how does it work?
Ans:
- A cargo balancer is a device that acts as a rear deputy and distributes network or operation business across several servers.
- Cargo balancers are used to improve the capacity and trustability of operations.
- They facilitate the distribution of workloads across multiple computing coffers, similar to computers, computer clusters, network links, central processing units, or fragment drives.
- Balancing request loads across numerous coffers helps any single garçon from getting a tailback.
36. What’s a constructor in C?
Ans:
In C, a constructor is a particular type of member function of a class that initializes objects of a class. A constructor has the same name as the class and no return type; it’s automatically invoked when an object is created. Constructors can be overfilled to accept different figures of parameters and can be defined with varying access specifiers. Particular types of constructors include dereliction, copy, and move constructors, each serving different initialization purposes, easing inflexibility and effectiveness in resource operation.
37. What’s the difference between a function and a system in OOP?
Ans:
- In object-acquainted programming( OOP), the terms” function” and” system” are frequently used interchangeably but have distinct meanings.
- A function is a law called by name and independent of any object. On the other hand, a system is a function that’s associated with an object and defined within a class.
- Styles can manipulate the data contained within the class case or object, acting on the data within its class and controlling the geste of an object.
38. What do you mean by recursion?
Ans:
- Recursion is a programming technique in which a function calls itself to solve a problem. It’s used when a problem can be divided into more manageable sub-problems of the same type.
- Recursive results are frequently cleaner and easier to understand than iterative bones for problems like covering a complex data structure, sorting, or calculating factorials.
- Still, recursion requires proper running to avoid horizonless recursion and mound overflow crimes. Base cases are pivotal to stopping the recursion, and each recursive call should bring the result closer to this base case.
39. How is a stack typically implemented?
Ans:
A stack is typically implemented using either an array or a linked list. Array-based stacks use a fixed-size variety with operations (push and pop) occurring at the top, constrained by the array’s capacity. Linked list-based stacks use nodes where each node points to the next, allowing for dynamic growth. Both types follow the Last In, First Out (LIFO) principle.
40. When can super keywords be used?
Ans:
The super keyword in Java refers to the immediate parent class of a class. It can be used to pierce superclass styles and constructors hidden or walked by the styles in a class. Using super can be particularly useful in system booting, where a class system requires the functionality of the parent class’s System plus some fresh or modified geste. It’s also used in constructor chaining to bring the parent class’s constructor, ensuring proper initialization of all fields in the heritage scale.
41. Can you explain the concept of a message queue?
Ans:
Software systems employ message queues as a communication tool to let messages flow back and forth between various threads or processes. A message queue serves as a buffer, holding communications until the receiving entity for a short while. Asynchronous communication is made possible by message queues, suggesting that sender and recipient actions need not co-occur. They are frequently used to increase the scalability, dependability, and decoupling of system components in distributed systems and applications.
42. What testing methodologies do you follow to ensure law quality?
Ans:
- Various testing methodologies ensure law quality, each acclimatising to specific software development aspects.
- Unit testing is abecedarian, fastening on individual factors to ensure they serve rightly in insulation.
- Tools like JUnit for Java or PyTest for Python are generally used. Integration testing follows, where multiple units are combined and tested as a group to identify interface blights.
- System testing examines the complete intertwined System to corroborate that it meets the specified conditions.
43. How do you find duplicates in an array?
Ans:
- One can use several styles to find duplicates in an array, such as mincing, sorting the array first, or using a set data structure.
- Using a set can be the most effective way, where you reiterate the variety of rudiments and add each to the set.
- However, if an element is formerly in the set, it’s a duplicate. Another approach is Sorting the array and surveying it for successive equal rudiments.
- These styles vary in time and space complexity, and the choice depends on specific conditions like the array’s size and the range of implicit values.
44. Explain ‘Exceptions’ in Java. What are its types?
Ans:
In Java, an exception is an event that disrupts the regular inflow of the program. It’s an object thrown at runtime and describes an error or unanticipated condition that can occur during the prosecution of a program. Java exceptions are distributed into two main types: checked and unbounded exceptions. Checked exceptions must be declared in a system’s throws clause if the System can throw them and aren’t caught within it. Unbounded exceptions don’t need to be declared or seen, including crimes like RuntimeExceptions.
45. How is JDK different from JRE?
Ans:
The Java Development Kit( JDK) and Java Runtime Environment( JRE) are two core factors of the Java platform, but they serve different purposes. The JDK is a complete software development tackle for Java operations, applets, and factors. It includes the JRE, a practitioner/ haul( Java), a compiler( javac), an archiver( jar), an attestation creator( Javadoc) and other tools demanded in development. On the other hand, the JRE provides the libraries, the Java Virtual Machine( JVM), and other factors to run operations written in Java.
46. What’s a storehouse class? What are its various specifications?
Ans:
- A storehouse class in C and C programming languages defines the compass( visibility) and continuance of variables and functions within a program.
- There are four storehouse classes: bus, register, static, and extern. Bus variables have an original compass and are automatically allocated and deallocated.
- Register suggests( however, doesn’t guarantee) that the variable be stored in a register rather than RAM for quicker access.
- Stationary variables save their value after they go out of the compass and are initialized only formerly. An extern is used to declare a global variable or function in another train.
47. How do you declare a horizonless circle in Java?
Ans:
- In Java, a horizonless circle can be declared in several ways, depending on the structure preferred.
- Generally, it’s declared using a while circle or a for circle. For illustration, using the while circle, you can write while( true){// law to repeat}, which will continue to execute indefinitely because the condition true is always true. also, a for circle can be used as for(;;){// law to repeat}.
- Both constructs create an endless circle until a break statement is encountered or the program is terminated.
48. How is Java different from other similar platforms?
Ans:
Java is substantially distinct from other programming platforms due to its platform-independent nature. Java programs are collected into bytecode, which can be run on any device equipped with a Java Virtual Machine( JVM). This” write formerly, run anywhere” ( WORA) capability means inventors can develop Java law on one System and anticipate it running on any other Java-enabled System without any adaptations. Likewise, Java incorporates robust security features.
49. What’s a Detector?
Ans:
In database operation systems, the detector is a procedural law that is automatically executed in response to certain events on a particular table or view in the database. Alarms are used to conserve data integrity by checking or changing data automatically in a database or auditing changes to data. For illustration, a detector can be set to notify a director when a new record is added or to modernize a value in one table when a corresponding record changes in another. Alarms can be defined as fire before or after the data revision.
50. Explain the firewalls.
Ans:
A firewall is a network security device that monitors and controls incoming and gregarious network business grounded on destined security rules. It generally establishes the hedge between the trusted internal network and the untrusted external network, similar to the Internet. Firewalls can be tackled- grounded, software-grounded, or a combination. They work by blocking or permitting data packets grounded on security rules set by the network director. Firewalls are pivotal in preventing unauthorized access to networks and are an abecedarian security structure for securing data and coffers.
51. Name some services handed by the operation subcaste in the Internet model.
Ans:
- The operation subcaste in the Internet model provides a wide array of services that grease end-stoner processes and operations to pierce the network.
- These services include train transfer, dispatch, and train service protocols similar to HTTP (for web browsing), FTP (for train transfers), SMTP (for dispatch), and DNS (for sphere name resolution).
- It also includes further technical protocols like TELNET and SSH for remote session services and protocols like SNMP for network operation.
- The operation subcaste gives stoner interfaces and support for services similar to electronic messaging and network data sharing.
52. What’s IP Spoofing?
Ans:
- IP Burlesquing refers to creating Internet Protocol( IP) packets with a forged source IP address to hide the sender’s identity or impersonate another computing system.
- This method is generally used in denial-of-service attacks and other types of cyber pitfalls, where the trustability of the source is critical.
- It exploits how the Internet works to shoot data packets, making it a potent vulnerability in network security. Mitigation strategies include packet filtering, confirmation checks, and robust authentication styles.
53. What are the Advantages of Fiber Optics?
Ans:
Fiber Optics’ advantages include advanced bandwidth capacities and lesser speed, allowing data to travel briskly and in larger quantities compared to traditional essence dispatch lines. Fibre optics are less susceptible to electromagnetic hindrance, ensuring cleaner and more dependable signals. They also have a lower attenuation rate, meaning the signal can travel longer distances without declination. Also, fibre optical lines are more secure from wiretapping, have a lower periphery, and are lighter in weight, making them easier to install.
54. What’s the difference between Bluetooth and wifi?
Ans:
- Bluetooth is primarily a wireless technology standard for swapping data over short distances using short-wavelength radio swells, which is ideal for creating networks in particular areas with high security.
- On the other hand, wifi provides high-speed internet and network connections over lesser distances, using radio swells generally in an original area network( LAN).
- While Bluetooth consumes lower power, making it suitable for mobile bias, wifi provides lesser data output, making it suited for broadband internet connections and supporting multiple biases.
55. What’s Thrashing?.
Ans:
Thrashing occurs when a computer’s virtual memory coffers become inadequate, causing constant paging and inordinate lading or data switching between RAM and the hard fragment. This condition significantly degrades system performance as the System spends more time switching runners than executing deals. Thrashing can be eased by adding physical Memory, optimizing operations and processes, or using more effective memory operation methods.
56. What’s virtual Memory?
Ans:
Virtual Memory is a memory operation capability of an operating system(no) that uses tackle and software to allow a computer to compensate for physical memory dearths, temporarily transferring data from arbitrary access memory( RAM) to fragment storehouse. This process increases the available Memory through the use of fragment space. By using virtual Memory, a system can run more extensive operations with lower real RAM, with the OS automatically handling the process of switching data in and out of RAM as demanded.
57. What’s the time-sharing System?
Ans:
A time-participating System is a computing terrain in which multiple users partake in the system’s coffers contemporaneously. The operating system uses scheduling to allocate time places to each stoner and operation, effectively managing the prosecution of various tasks similar to users interacting with the system as if they’ve exclusive use of the coffers. This optimizes CPU operation, enhances system effectiveness, and enables more interactive stoner sessions.
58. What’s multitasking?
Ans:
- Multitasking refers to an operating system’s capability to handle multiple tasks simultaneously.
- In multitasking zilch, CPU time is divided among multiple processes through process scheduling, which can be preemptive or collaborative.
- This allows a stoner to run multiple operations contemporaneously, making systems more effective and productive.
- The zilch manages the tasks’ conditions for processor time, Memory, and I/ O, ensuring that system coffers are allocated meetly and switching between functions so snappily that it gives the print of community.
59. What’s caching?
Ans:
Caching is a technology grounded on the storehouse of data in a temporary storehouse area known as a cache. This process allows for the rapid-fire reclamation of data by storing clones of lines or data results where they can be penetrated more snappily than reacquiring them from the primary data source every time they’re demanded. Common exemplifications include cybersurfer caches that store web runners, images, and other web content locally to speed up cargo times and CPU caches, which store instructions and data near the processor to reduce the detention in costing data from main Memory.
60. What’s the difference between the Operating system and kernel?
Ans:
- The operating system is comprehensive software that manages and tackles coffers and provides services for computer programs.
- It encompasses several factors, including the kernel, stoner interface, and system serviceability. The kernel, on the other hand, is the core element of the no; it manages the CPU, Memory, and supplemental bias.
- The kernel is the minor position of the OS, handling communication between tackle and software factors.
- At the same time, the full zilches include operations and interfaces erected on top of the kernel.
61. Explain different languages present in DBMS
Ans:
- Data Definition Language( DDL) includes commands like CREATE, ALTER, and DROP, which define and modify the database schema.
- Data Manipulation Language( DML) is similar to SELECT, INSERT, UPDATE, and cancel; these commands manage and manipulate data.
- Data Control Language( DCL) Commands like GRANT and drop control access to data.
- Transaction Control Language( TCL) Includes commands like COMMIT and ROLLBACK, which are used to manage deals within the database.
62. Are NULL values in a database the same as that of blank space or zero?
Ans:
In a database, NULL values represent a lack of data or an unknown value, different from a blank space or zero. A blank space( or empty string) is a valid string value that happens to contain no characters, and zero is a numeric value. NULL, conversely, signifies that the data doesn’t live or isn’t applicable and doesn’t equate to any value, including zero or space. Handling NULL values rightly is pivotal for accurate querying and data integrity.
63. What’s a process? What are the different countries involved in the process?
Ans:
A process is a case of a program in prosecution, including its current values of the program counter, registers, and variables. The typical countries of a process in an operating system include
- New The process is being created.
- Ready: The process is prepared to run and stay for CPU time.
- Running Instructions are being executed.
- The waiting process is staying for some events.
- Terminated The process has finished prosecution. These countries are part of the process life cycle managed by the zilch through process scheduling and resource allocation.
64. What are starvation and ageing in the operating System?
Ans:
Starvation occurs when a process gets sufficient coffers for prosecution because other processes continuously consume them. It generally affects low- precedence processes in a system where precedence-grounded scheduling algorithms are used. Ageing is a fashion used to help starvation; it increases the precedence of staying processes, ensuring they have enough precedence over getting the necessary coffers and executing.
65. What’s DBMS, and what’s its mileage? Explain RDBMS with exemplifications.
Ans:
- A Database Management System( DBMS) is software designed to store, recoup, define, and manage data in a database.
- It helps in maintaining data integrity, security, and thickness. A Relational Database operation System( RDBMS) is a type of DBMS grounded on the relational model proposed by Edgar. Codd.
- In RDBMS, data is structured in tables( relations) connected through foreign keys. Common exemplifications include MySQL, PostgreSQL, and Oracle.
66. What do you mean by transparent DBMS?
Ans:
A transparent DBMS simplifies and objects database operations for users and operations, making the complexity of certain database operations unnoticeable to them. This can include aspects like data distribution transparency, which hides the physical position of data, and sale transparency, which ensures that operations are either entirely complete or fail, maintaining database thickness without users’ intervention.
67. Define a Relation Schema and a Relation.
Ans:
In a relational database environment, a relation schema refers to the logical structure of a table that’s defined by a name and a list of attributes, specifying fields and data types. A relation is a case of the schema; it’s a table comprising rows( tuples) and columns( attributes) that conform to the schema. The schema describes the structure, while the relation is the factual data stored per that structure.
68. What’s data abstraction in DBMS?
Ans:
Data abstraction in a DBMS refers to hiding the details of how data is stored and maintained while furnishing a clean model for end users to use. This abstraction allows users to interact with the System without having to understand complex details of how data is stored, penetrated, and reused. It helps simplify relations with the database and enhances the effectiveness of data operation.
69. What are the three situations of data abstraction?
Ans:
- Physical position: The minor position describes how data is stored in the database, including complex data structures and train storehouse details.
- Logical position: The middle position defines what data is stored in the database and what relationship exists among those data. This includes tables, views, and indicators.
- View Level: The loftiest position involves how the users view the data. This can involve different database views for different users, generally through a graphical user interface or specific query responses.
70. How important does Memory enthral a class?
Ans:
In object-acquainted programming languages like C or Java, the Memory enthralled by a class depends not on the class description but on the class’s cases (objects). A class as a design only consumes Memory once objects are expressed. Each object’s memory consumption is determined by the sum of its data members’ sizes, banning static members, which are stored independently. Also, there may be more due to alignment and virtual functions (like a pointer to a virtual table).
71. What defines a deadlock in operating systems?
Ans:
In operating systems, a deadlock happens when two or more processes are stuck waiting for resources that the others are holding, preventing them from moving forward. Resources cannot be shared; hold and wait allows processes to have some resources while requesting more; no preemption prohibits resources from being taken by force; and circular wait refers to a chain of processes waiting on resources held by each other in a circle. These are the four conditions that apply to this situation.
72. Explain how public key cryptography works.
Ans:
- Public Crucial cryptography, also known as asymmetric cryptography, involves using two different but mathematically linked keys: public and private keys.
- The public key is shared openly, allowing others to crack dispatches that only the holder of the corresponding private key can decipher.
- Again, the private key, which is kept secret by the proprietor, can be used to subscribe dispatches, furnishing a way to corroborate the proprietor’s identity through the public key.
73. What’s SMP (Symmetric Multiprocessing)?
Ans:
Symmetric Multiprocessing (SMP) is a type of multiprocessing in which two or more identical processors are connected to a single, shared main memory and controlled by a single operating system case. These processors perform computing tasks inversely and can access Memory coincidentally. SMP systems are adequate for operations where tasks can be divided into multiple processes or vestments that run singly and contemporaneously.
74. How is an array enforced?
Ans:
In programming, an array is a collection of rudiments, all of the same type, stored in conterminous memory locales. This allows for adequate access to rudiments via indexing, where the memory address of any element can be calculated by adding the indicator multiplied by the size of each component to the base address of the array. Arrays are enforced in static and dynamic forms, which dictates whether their size can change during runtime.
75. Find the array’s longest growing subsequence.
Ans:
An array’s longest adding subsequence (LIS) is a rigorously added subsequence with the maximum possible length. This problem can be answered using dynamic programming where each cell dp(i) in a DP array represents the length of the LIS ending at indicator i. Reiterate through former rudiments for each element to find a sequence that the current element can extend. The complexity of this System is (2)O( n2).
76. Why are iterative cascade models superior to traditional bones?
Ans:
- The iterative cascade model improves upon the traditional one by introducing replication across the stages.
- While the conventional cascade model completes each phase entirely before moving to the coming, the iterative cascade model allows reconsidering and enriching former stages grounded on literacy and feedback from after stages.
- This inflexibility helps better manage pitfalls, conform to changes, and refine system conditions and design before final deployment.
77. What exactly doesre-entrancy mean?
Ans:
- Re-entrancy refers to a function’s capability to be broken in the middle of prosecution and safely called again(“re-entered”) before its former prosecutions are complete.
- This is critical in concurrent programming when multiple prosecution vestments use participated coffers.
- Multiple vestments can safely execute are-entrant functions contemporaneously. They don’t hold static or global non-constant data, don’t modify their law, and only call other-entrant functions or System calls.
78. What do SVM’s support vectors do?
Ans:
In Support Vector Machines( SVMs), support vectors are the data points closest to the decision face( or hyperplane). These points are critical in defining the hyperplane because they’re the most delicate to classify and, therefore, have the topmost eventuality to affect the position and exposure of the hyperplane. The support vectors help to maximize the periphery between the classes in the point space, contributing directly to the robustness and delicacy of the bracket model.
79. What exactly is cross-confirmation?
Ans:
Cross-validation is a statistical system used to estimate the skill of machine literacy models. It covers against overfitting in a prophetic model, mainly when the data is limited. Incross-validation, the dataset is resolved into k lower sets or crowds. The model is trained on k- 1 of these crowds, with the remaining part used as test data to estimate model performance. This process is repeated multiple times, with each of the k crowds used exactly formerly as the test set, allowing the model’s effectiveness to be reliably estimated
80. Why is Java’s central System static?
Ans:
Java’s central System is stationary because it allows the Java Runtime Environment( JRE) to bring this System without having to express a case of the class. This is practical since the central System is the entry point of any standalone Java operation and must be accessible to start the operation. Being static, it can be directly called with the class, simplifying the launching process by Java’s command-line tools or any other surroundings that run Java operations.
81. How does Java reissue an object?
Ans:
- Java serializes an object by converting its state to a byte sluice so that it can be regressed into a copy of the object.
- This process involves writing the class of the object, the class hand, and the values of all its fields, including private and public bones, to an affair sluice.
- When the object is later deserialized, Java uses the class name and class hand to recreate it in Memory and restore its fields from the values in the byte sluice.
82. What are the different forms of Java script crimes?
Ans:
In JavaScript, crimes can occur in various forms, similar to Syntax crimes when there’s an error in the law syntax, Type crimes when an operation is applied to the wrong data type, Reference crimes when there’s an attempt to source a missing variable, Range crimes when an object is given an invalid length, and Eval offences related to the eval() function. Custom crimes can also be defined and thrown using the Error object to handle specific error cases more effectively.
83. What do you believe are the essential rudiments of good content?
Ans:
- The essential rudiments of good content include its applicability to followership, furnishing value through information, entertainment, or solutions to problems, and thickness in quality and voice.
- Good content should be well-delved, factually accurate, and engaging to keep followers interested. It should also be well-structured with clear calls to action when applicable and optimized for hunt machines to increase visibility.
84. How will you develop a content strategy for a customer/ brand?
Ans:
Developing a content strategy for a customer or brand involves:
- There are several crucial ways of understanding the brand’s pretensions.
- Probing the target followership to identify their requirements and content consumption habits.
- Assaying challengers’ content for gaps and openings.
- Setting apparent content objects.
- Defining crucial performance pointers( KPIs).
The strategy should include a content timetable for thickness, deciding on the blend of content types and distribution channels, and figuring out content creation, publication, and creation procedures.
85. How do you assess the quality of content?
Ans:
Assessing the quality of content involves several criteria: delicacy of information, clarity and unity in donation, applicability to the intended followership, engagement position, and alignment with SEO stylish practices if applicable. The content should be well-structured with a logical inflow, free of grammatical and spelling crimes, and effectively communicate its intended communication. Also, user feedback and analytics, similar to runner views, time spent on the runner, and conversion rates, can give perceptivity to the content’s performance and quality.
86. What’s your proofreading process?
Ans:
- The proofreading process generally involves several ways to ensure content is free of crimes and quickly communicates its communication.
- It begins with a thorough read-through to check for grammatical, punctuation, and spelling miscalculations.
- This is followed by checking syntax and consonance, ensuring the textbook flows logically and efficiently.
- Proofreaders may use tools like Grammarly or Hemingway to help identify unresistant voices, readability issues, or complex judgment structures.
87. What are the difference between collect-time and runtime crimes.
Ans:
Collect-time compiler detects time crimes as it tries to restate the source law into machine law and generincludesclude includes type-checking, type-checking or missing lines that are substantiated in the law. Runtime crimes occur while the program runs after successfully collecting and executing. These crimes can be caused by illegal operations similar to dividing by zero, penetrating out-of-bounds rudiments in an array, or trying to use null object references.
88. Explain the refactoring?
Ans:
- Refactoring is the process of restructuring computer law without changing its external geste.
- It aims to facilitate the functional attributes of the software, similar to readability, low complexity, maintainability, and extensibility.
- Refactoring helps to clean up the codebase, making it easier to understand and less precious to modify.
89. Explain the purpose and impact of the Global practitioner Cinch in CPython?
Ans:
The Global Practitioner Cinch( GIL) is a mutex that protects access to Python objects, precluding multiple native vestments from executing Python bytecodes at formerly. This cinch is necessary because CPython’s memory operation isn’t thread-safe. The GIL can be a significant tailback in CPU-bound and multi-threaded law since it allows only one thread to execute in Python space at a time. Although it simplifies the perpetration of CPython by avoiding the need for unequivocal cinch operation, it can hamper performance by precluding true multi-core concurrency.
90. What do you understand by ‘serverless armature’?
Ans:
Serverless armature refers to a design pattern where pall providers handle servers and structures entirely. This model allows inventors to concentrate purely on operation law rather than garçon operations, scaling, and conservation. Operations are erected in serverless terrain run in stateless cypher holders that are event-touched off and entirely managed by the pall provider. The armature is cost-effective as it generally operates on a pay-per-use model and can automatically gauge the operation’s demands.






