Chef DevOps is a specialized discipline within the DevOps realm, concentrating on harnessing the capabilities of Chef, a potent configuration management tool, for automating and overseeing infrastructure as code. Professionals in this field utilize Chef’s resources, recipes, and cookbooks to establish and uphold the desired infrastructure state, ensuring uniformity, scalability, and dependability across various environments.
1. What is a Source?
Ans:
Managing resources well is critical to increasing output and succeeding in various pursuits. Any asset or tool that may be used to accomplish a certain task or meet a need is considered a resource. It can be material, like water, minerals, or forests, or immaterial, like knowledge, abilities, or technology. Infrastructure, financial capital, and human capital are further examples of resources.
2. How is a core plugin’s custom build made and distributed?
Ans:
By packing the altered plugin code into a.hpi or. Jpg file and swapping it out for the matching file in the Jenkins installation directory, a custom build of a core plugin may be made available. The altered code is first packaged as a plugin archive after being compiled into bytecode. After that, the archive is added to the Jenkins installation’s “plugins” directory, taking the place of the original plugin file. In order to implement the modifications and enable the custom build of the core plugin, Jenkins is finally restarted.
3. Define an action for a resource.
Ans:
- Clearly define the intended action, including its goal and parameters.
- List all of the resources that are needed, including staff, tools, and systems.
- Establish the procedures and workflow needed to carry out the task successfully.
- Keep a record of the action plan, including deadlines, roles, and duties.
- Inform pertinent parties about the designated resource activity so that it can be executed and aligned.
4. List the three security measures that Jenkins employs for user authentication.
Ans:
For user authentication, Jenkins uses three security mechanisms: OAuth (Open Authorization), LDAP (Lightweight Directory Access Protocol), and matrix-style protection. Thanks to LDAP, Jenkins can perform user authentication against an external directory service. Through OAuth, users can sign in with login credentials from outside sources such as GitHub or Google. Administrators can manage who has access to Jenkins resources by assigning user roles and permissions within the Jenkins environment through matrix-based security.
5. Describe Chef-apply From Chef-client?
Ans:
In the chef ecosystem, there are distinct functions for Chef-apply and Chef-client. Chef-client is an agent that runs on nodes to apply configurations provided by Chef recipes. In contrast, Chef-apply is a command-line tool intended for testing and debugging Chef scripts locally on a workstation. Chef-apply is mainly utilized in the stages of development and testing, whereas Chef-client is employed in production settings to guarantee automated and consistent configuration management.
6. Describe the run-list.
Ans:
A run-list is a set of operations or actions that must be carried out in a particular order in the fields of systems administration and software development. Chef and other configuration management systems frequently use it. The run list specifies which roles or recipes should be applied to a node. It guarantees that every node in a system has the desired configuration applied consistently. Keeping an accurate and current run list is essential to reliable and effective infrastructure management.
7. How Should a Chef Server Be Configured?
Ans:
The Chef Server is set in two ways:
- Using the Open Source Chef Server option, you can have complete control and customization, as well as download and install the Chef Server software on your Infrastructure.
- We hosted Chef Server. This cloud-based solution, provided as a service by Chef Software, lowers user maintenance overhead by having Chef Software host and operate the Chef Server.
8. What Function Does the Starter Kit Serve?
Ans:
Starter kits typically include basic equipment, samples, and instructions to assist customers in getting started with a specific activity or product. Their function is to ease customers through the first learning curve and make it easier for them to start using the product or participating in the activity.
9. What is a Node?
Ans:
A router or computer is an example of a node in a network. A node in a data structure, such as a tree or graph, indicates a single element connected to other nodes. A node in a distributed system is an entity that processes or stores data, whether physical or virtual. Nodes serve as crucial building blocks for intricate processes within these systems by facilitating processing, organizing, and communication.
10. What are the main distinctions between Agile and DevOps?
Ans:
| Aspect | Agile | DevOps |
|---|---|---|
| Focus | Iterative development | Collaboration between development and operations |
| Goals | Deliver functional software in small, frequent increments | Enhance efficiency, speed, and quality of software delivery |
| Scope | Development phase | Entire software lifecycle (development to operations) |
| Application | Manage tasks, sprints, feedback loops within development | Integrate and automate processes for continuous delivery |
11. What Takes Place Throughout The Bootstrap Procedure?
Ans:
A computer loads its operating system into memory and initializes hardware components during the bootstrap process, which enables it to begin running code and function completely. The BIOS/UEFI must be initialized, the bootloader must be loaded, and the power-on self-test (POST) must be completed before the operating system kernel can be executed.
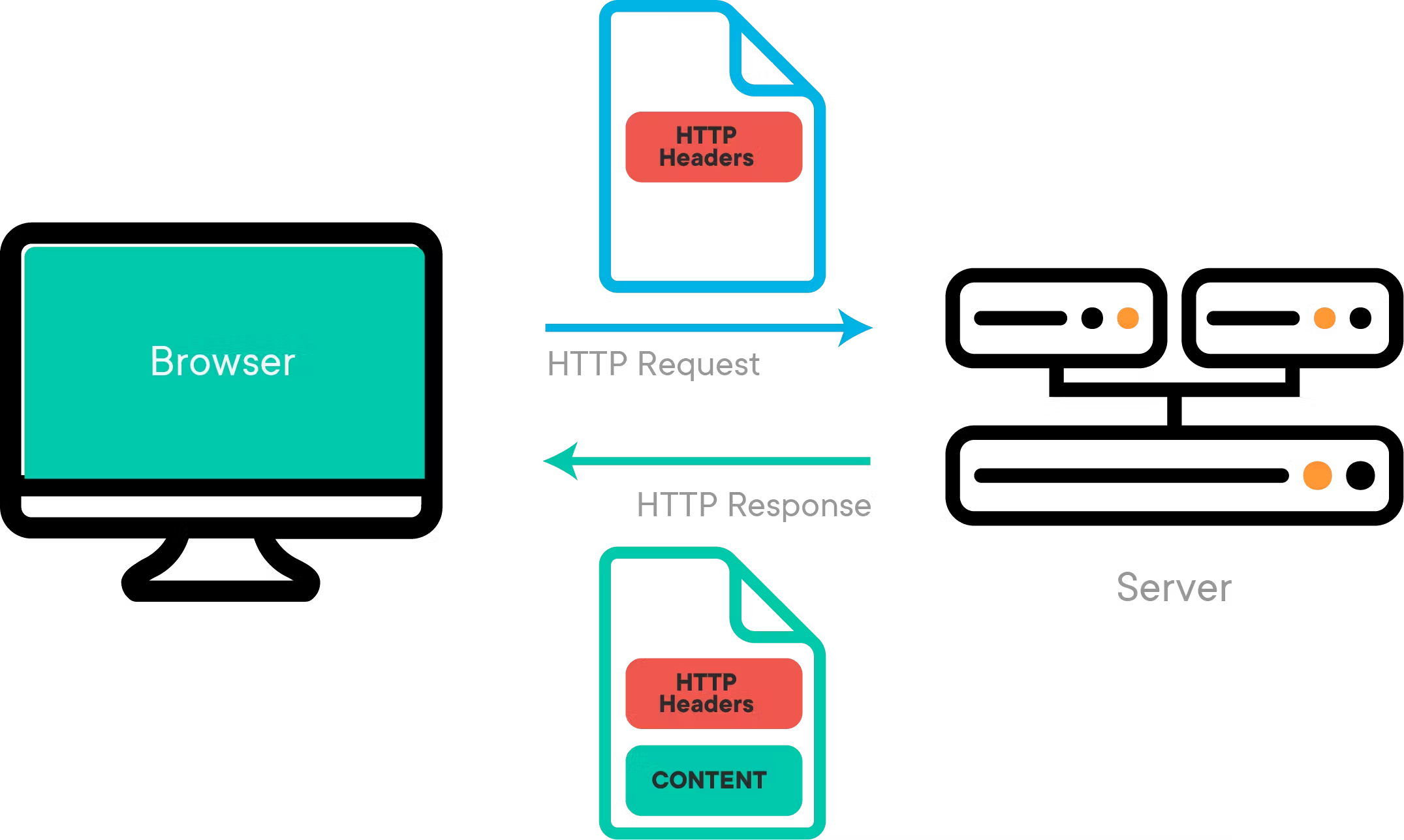
12. How does the HTTP protocol function?
Ans:
HTTP (Hypertext Transfer Protocol) enables communication between clients (such as web browsers) and servers. When a client requests a resource (like a web page or image), it sends an HTTP request to the server. After processing the request, the server provides the requested data and a status code indicating the result of the request (e.g., success or error). This exchange is stateless, meaning each request is treated independently without memory of prior interactions. HTTP is fundamental for retrieving and displaying web content, facilitating seamless browsing.
13. Verify Which node bootstrapped successfully.
Ans:
- During bootstrapping, look for any error notices in the system logs or terminal output.
- Search for particular success messages that signify a successful bootstrapping effort.
- Keep an eye on network traffic to determine whether the node is actively corresponding with other nodes.
- Use a command-line tool or management interface to view the node’s status.
- Confirm that the node is operating as planned inside the network and that it is fulfilling its intended role.
14. How to Upload A Cookbook To The Chef Server Using This Command?
Ans:
Use the (knife cookbook upload) command and the cookbook name to upload a cookbook to the Chef Server. The Cookbook will be uploaded from your desktop computer to the Chef server locally. Make sure you are in the directory where the Cookbook that you want to upload is located. Depending on how your Chef Server is configured, you might also need to authenticate using the proper credentials.
15. How to Update Your Node’s Cookbook?
Ans:
Using the “chef-client” command on the node, you can apply an updated cookbook to your node. This command retrieves the most recent version of the Cookbook from the Chef Server and applies it to the node’s configuration. As an alternative, you can use automation tools like cron or a task schedule to schedule a Chef client to run regularly or manually activate it.
16. How to Adjust the Cookbook’s Version When It’s Prepared for Production Use?
Ans:
- Select a versioning strategy, such as Semantic Versioning (SemVer), for example.
- Taking into account the modifications performed, raise the version number accordingly.
- Modify the version number found in the configuration files or metadata of the Cookbook.
- Ascertain that everyone involved knows about the updated version.
- For production use, publish or distribute the revised Cookbook together with the new version number.
17. How to Make A Second Node And Use The Cookbook For Amazing Customers On It?
Ans:
Use a configuration management tool like Chef or Ansible to set up the node and apply the Cookbook before creating a second node and applying the “Awesome Customers” cookbook. The complexity of the recipe, the speed of the network, and the target’s performance are some of the variables that affect how long a node takes. However, it usually takes a few to tens of minutes.
18. How Does Using Test Kitchens Help Local Development?
Ans:
To minimize errors and guarantee consistency, local development employs Test Kitchen, which enables developers to test cookbooks and configurations in a controlled environment that closely mimics production. Additionally, it offers quick feedback on modifications, facilitating quicker development cycles and better infrastructure code quality overall.
19. What duties do system administrators have inside an organization?
Ans:
System administrators are in charge of monitoring and maintaining IT Infrastructure, which includes servers, networks, and security measures, to guarantee dependable and secure operation. To maximize efficiency and reduce downtime, they also apply system updates and patches, debug problems, and offer technical assistance.
20. what does IT Infrastructure mean?
Ans:
The framework of networks, hardware, software, and services that support an organization’s computing needs is referred to as its IT infrastructure. It includes operating systems, databases, servers, storage, networking hardware, and applications. The basis for securely and efficiently delivering and managing IT resources is provided by IT infrastructure. It consists of both virtual and physical elements, such as cloud computing platforms and data centres. Businesses may innovate, run efficiently, and adjust to the ever-evolving technology landscape with the help of an efficient IT infrastructure.
21. Describe Chef Desktop.
Ans:
Administrators can use it to specify and automate desktop environment setup, configuration, and upkeep. By enforcing uniform setups across several PCs, users can ensure compliance and minimize manual intervention using Chef Desktop. Utilizing the Infrastructure as a code model allows users to effectively manage desktop setups through version control systems and treat them like code. Chef Desktop also provides comprehensive auditing and reporting tools to monitor modifications and guarantee system integrity.
22. What characteristics does Chef Compliance offer?
Ans:
Chef Compliance offers functionalities to evaluate, address, and guarantee adherence to security guidelines and legal obligations. It also has reporting features, automated assessments, and customized compliance profiles to maintain a secure environment.
23. How does the DevOps team use Chef Infra for infrastructure management?
Ans:
Infrastructure as code principles are enforced, and configuration management duties are automated by DevOps teams using Chef Infra. By describing configurations in code, they can guarantee scalability, consistency, and quick deployment of changes throughout the Infrastructure.
24. Describe the characteristics of Chef Habitat.
Ans:
Chef Habitat’s packaging, deployment, and management features make application lifecycle management easier. These features enable applications to run in a variety of environments and be portable, automated, and scalable. Recipes are combined to create cookbooks, which enable modular and reusable setups in Chef infrastructure.
25. Describe the significance of Chef Inspec in relation to automation.
Ans:
Enabling teams to describe compliance requirements as code, perform automated compliance checks, and guarantee ongoing compliance across the infrastructure lifecycle, Chef InSpec plays a critical role in compliance automation. It offers insight into the state of compliance and facilitates proactive correction, lowering the possibility of security lapses and non-compliance.
26. Describe how the Chef uses recipes.
Ans:
Recipes in Chef are used to specify the actions required to set up and maintain system resources. They are made up of Ruby code that indicates the system’s intended state. Recipes allow infrastructure tasks to be automated by specifying what resources should be in what state. They are necessary to build scalable and repeatable setups that allow for uniform deployment in various contexts.
27. In Chef, what does a Node represent?
Ans:
A node in Chef represents a server or other computer under Chef’s control. It includes details regarding the node’s configuration, such as The Chef server’s use of characteristics, run-lists, and environment parameters to enforce desired states and apply customizations.
28. How does OHAI function within Chef?
Ans:
Chef uses OHAI, a system profiling tool, to collect data about a node’s environment and configuration. It gathers information on the hardware, network setup, operating system, and other characteristics used by Chef recipes and resources to determine configuration choices.
29. Describe how a chef uses a knife.
Ans:
Chef’s Knife is a command-line tool for managing environments, nodes, cookbooks, configuration data, and communication with the Chef server. It offers commands for managing node setups, remotely executing chef-client commands, uploading cookbooks, and carrying out various administration duties.
30. Describe the dpkg package resource.
Ans:
On Ubuntu and Debian-based systems, the dpkg_package resource in Chef manages the installation of Debian packages. To ensure consistent package management across nodes, it enables Chef recipes to specify the package name and version to install, along with any dependencies and installation settings.
31. List the various Chef handler types.
Ans:
In Chef, handlers specify what should happen when certain events—like success, failure, or convergence occur during a client run. There are three different categories of handlers: exception handlers, report handlers, and start handlers. They offer a means of ensuring that the conditions are met before the Chef run continues.
32. Describe to the Chef what an exception handler is.
Ans:
- When a Chef client encounters an error or exception, custom actions can be initiated via the Exception handler in Chef.
- It offers a way to handle mistakes politely and respond appropriately by logging them, notifying users, or undoing modifications.
33. Describe the Chef report handler.
Ans:
The creation and transmission of reports regarding the Chef client run to outside systems or services falls under the purview of the Chef report handler. It gathers data on the run’s status that is, its successes, failures, and system modifications—and transmits it to specified endpoints for examination or observation.
34. Describe the Chef’s Start handler.
Ans:
A Start handler in Chef is a mechanism that initiates actions upon the start of a Chef client run. It enables the completion of particular tasks or configuration setup before the start of the main Chef operation. Start handlers are frequently used for pre-run checks, environment setup, and logging initiation.
35. Describe Chef’s Handler DSL.
Ans:
Chef has a domain-specific language called Handler DSL that is used to define handler actions and indicate when they should be invoked. The ability to define handlers in independent handler files or within Chef recipes gives users the flexibility to handle events during Chef client runs by defining conditions, priority, and other characteristics.
36. Describe the Chef run-list.
Ans:
A run-list is a collection of roles and recipes in Chef that specify the configuration and the sequence in which Chef configures nodes. During a Chef Client run, it outlines which resources need to be maintained and in what order. Roles and recipes can both be included in the run list, enabling structured and modular configuration management. Through the definition of a run-list, administrators can guarantee uniform, dependable, and uniform configurations throughout their Infrastructure.
37. What information is needed in Chef to bootstrap a node?
Ans:
- To bootstrap a node in Chef, details like the node’s hostname or IP address, the SSH username, password, or SSH key, and the URL or IP address of the Chef server are required.
- By doing this, the node is able to establish a connection with the Chef server and register for configuration management.
38. Describe how to apply to a node in Chef, an updated Cookbook.
Ans:
A node in Chef can have an updated Cookbook applied to it by uploading the new version to the Chef server and then adding the revised Cookbook version to the node’s run list. Alternatively, the Chef client on the node can be set to run automatically or manually. When the client runs, the most recent version of the Cookbook is downloaded from the server.
39. Describe Test Kitchen.
Ans:
The Test Kitchen is a testing tool that Chef uses to automate code and cookbook reviews. To ensure that their Chef code is proper in a controlled environment, developers can create test scenarios, set up virtual machines or containers, make configuration changes, and run tests.
40. How crucial is it that Chef’s SSL certificates be installed?
Ans:
For secure communication between chef components, including the chef server, chef clients, and other services, it is important to install SSL certificates in Chef. SSL certificates encrypt data being sent over the network, shielding private data from unauthorized parties’ interceptions or manipulation. Additionally, it aids in proving the legitimacy and dependability of Chef clients and servers, guaranteeing safe and dependable communication throughout the Chef ecosystem.
41. What does Chef’s SSL_CERT_FILE mean?
Ans:
The location of the SSL certificate file in Chef can be specified using the environment variable SSL_CERT_FILE. The certificates in this file are used to create secure connections during HTTPS communication. By setting SSL_CERT_FILE, the Chef can find out where to look for the certificates required to authenticate connections to external services or resources. This guarantees a safe connection between other external endpoints and Chef clients and servers.
42. What is the Chef command for a knife’s SSL check?
Ans:
To confirm that a Chef server is SSL configured, run the “knife sSSLcheck” command in Chef. This command guarantees that the SSL certificates are set up for Chef clients’ interactions with the commands. It’s crucial for preserving integrity and security in environments under Chef management. The resource file serves as a guide, allowing the Chef to carry out configuration actions on target nodes and encouraging scalability and efficiency in infrastructure management.
43. What is the file called Chef Resources?
Ans:
Essential to Chef infrastructure automation is a file called `recipes. Rb}, which is the Chef resources file by default. It includes Ruby code that describes the ideal state of the system and indicates which resources need to be configured and in what way. Each of these file’s resource declarations stands for a distinct configuration item, including the installation of packages, the handling of files, or the launch of services. Chef ensures consistency and reproducibility across environments by using these declarations to converge the system to the intended state.
44. Define Data Bags?
Ans:
Chef, a configuration management tool, has a feature called Data Bags that allows you to store sensitive data in JSON format together with global variables. During the configuration process, they provide centralized management of data accessible to Chef nodes. In Chef infrastructure, Data Bags are very helpful for storing passwords, configuration settings, and other information that needs to be shared among several nodes. Chef server ACLs (Access Control Lists) can be used to restrict access to Data Bags.
45. What is the resource chef_acl?
Ans:
To handle Access Control Lists (ACLs) on nodes and data bags in Chef, use the chef_acl resource. ACLs specify a person who is authorized to carry out particular tasks on resources in the Chef ecosystem. You can give or take permissions for individuals or groups to access, write, create, or remove resources using the chef_acl resource. Using this tool, you can limit access to sensitive information or vital infrastructure parts in your Chef environment and implement security regulations. It’s an essential part of maintaining appropriate governance and controlling access in chef deployments.
46. What details are required to bootstrap in Chef?
Ans:
In order to bootstrap a node in Chef, the following details are required:
- The hostname or IP address of the node you wish to bootstrap.
- SSH access to the node using the right login information.
- The IP address or URL of the Chef server.
- The confirmation is important and connected to the Chef company.
- The Chef organization’s name.
47. How do you upload a cookbook to the Chef server using a command?
Ans:
- Usually, the `knife cookbook upload` command is used to upload cookbooks to the Chef server.
- To begin with, confirm that you have access to the Chef server and the required permissions.
- Open the directory where the Cookbook that you wish to upload is located.
- Enter the Cookbook’s name and then use the command `knife cookbook upload}. As an illustration, use {knife cookbook upload my_cookbook}.
48. What does Chef’s run-list entail?
Ans:
The run list in Chef is a set of roles and recipes that specify what needs to be done on a node. It establishes the node’s setup and configuration. While roles are collections of recipes and other properties, recipes are sets of instructions for customizing particular components. The run list determines the sequence in which roles are allocated, and recipes are applied during a Chef client run. It’s an essential component of using Chef to manage Infrastructure as code, guaranteeing reproducibility and consistency across environments.
49. How can an updated Cookbook be added to the Chef node?
Ans:
First, use the `knife` to publish the modified Cookbook to the Chef server before applying it to the node in Chef—cookbook upload` command. Next, you can wait for the node’s scheduled Chef client interval to complete, or you can manually start a Chef client run on the node. In order to ensure that the node’s configuration corresponds to the most recent version specified in the Cookbook, the node will search the Chef server for any updated Cookbooks and apply them appropriately. This process occurs during the Chef client run.
50. Compose a service. Is there a Chef resource that disables the HTTP service at startup and stops it?
Ans:
- Use the following resource in Chef to halt and turn off the HTTP service:
- {{{ruby ‘httpd’ service do action [:stop, :disable] end {{{
- This code will turn off the HTTP service’s automatic startup upon system boot after stopping it first.
51. What are the purposes of Chef Resources?
Ans:
Declarative phrases called “Chef Resources” specify the ideal state of a system setup. They outline what ought to be present and how it ought to be set up. Among the tasks are managing files, users, packages, services, and commands. Chef Resources accomplishes this by automating configuration management processes, ensuring consistency across environments.
52. Describe a Chef Node and explain its significance.
Ans:
A server or virtual machine under the control of the Chef automation platform is called a Chef Node. Administrators can specify and enforce desired states on the node by using it as a target for Chef recipes and configurations. The Chef Node’s importance resides in its function within the Infrastructure, allowing scalability, automation, and consistent configuration management in a dispersed context. Organizations can increase system dependability, maintain compliance, and expedite deployment by using Chef to manage nodes.
53. In Chef, what distinguishes a Cookbook from a Chef Recipe?
Ans:
A Cookbook in Chef is an assembly of attributes, files, templates, and recipes arranged according to a predetermined format. It offers a method for configuring and managing resources among different nodes. Conversely, a Chef Recipe is an essential part of a Cookbook; it guides how to set up and maintain particular resources on a node. Basically, a Cookbook is a collection of recipes, whereas a Recipe is specific to one setup or administration step.
54. How are Chef repositories operated?
Ans:
The Chef repository usually adheres to a particular directory structure. Cookbooks include instructions and additional resources needed for system configuration and management. Roles specify the functions and recipes that the server should execute. Environments specify groups of systems’ configurations. Users can work with others and manage modifications to the Chef Repository using version control systems like Git.
55. What does it mean to have a signed header?
Ans:
It has a cryptographic signature created with a private key that can be validated with the matching public key. This guarantees that the data comes from a reliable source and hasn’t been altered during transmission. In security protocols like HTTPS, signed headers are frequently used to guarantee data integrity and authenticity and protect against different kinds of attacks, such as data tampering and man-in-the-middle attacks.
56. Explain Chef’s run-list?
Ans:
The Chef run list lists the roles and recipes that specify what should be applied to a node during the Chef-client run. This list denotes the sequence in which the node is configured using roles and recipes. Either straight recipes or roles that contain several recipes can be referenced in the run list. Chef guarantees consistency and repeatability in the node setup by specifying the required configuration in the run list.
57. How significant is a Chef beginning kit?
Ans:
Authentication keys, configuration files, and required dependencies are usually included. By streamlining the setup procedure, this tool guarantees consistency between Chef deployments. It also aids in the learning of Chef’s best practices and framework for newcomers. It also improves teamwork by giving everyone on the team a common starting point.
58. How does one go about changing a Chef Cookbook?
Ans:
Observing version control procedures is essential for monitoring and effectively making adjustments. After the modifications are done, thoroughly test the revised Cookbook to ensure there are no regressions and that it operates as intended. Following testing, raise the Cookbook’s version number in accordance with semantic versioning guidelines.
59. What are the steps involved in bootstrapping in Chef, and what data is required?
Ans:
In the context of Chef, bootstrapping is the process of configuring a new node under Chef’s supervision. The node’s IP address or hostname, its login credentials (such as its SSH key or username/password), and the run list—which lists the roles or recipes that must be applied to the node—are all required for bootstrapping.
60. Elaborate on how you interpret Chef’s Test Kitchen.
Ans:
Chef has a tool called Test Kitchen that automates the testing of infrastructure code. In a local development environment, it enables developers to write and execute tests against their Chef cookbooks. Test Kitchen applies cookbook recipes, sets up virtual machines or containers, and performs tests to ensure the infrastructure functions as it should. Supporting many testing frameworks like Serverspec, InSpec, and ChefSpec enables developers to confirm that their infrastructure code is correct before putting it into production.
61. What stages does DevOps consist of?
Ans:
There are normally five stages in DevOps:
- Continuous Development: this involves regular code writing and commits by developers.
- Continuous Integration: this process involves automatically testing and integrating code updates into a shared repository.
- Continuous Testing: automated tests that guarantee the functioning and quality of the code.
- Continuous Deployment: under this approach, code modifications are automatically pushed to live environments upon successful test completion.
- Continuous Monitoring: In order to find problems and enhance the system, performance and user metrics are regularly tracked.
62. What distinguishes continuous deployment from continuous delivery?
Ans:
The deployment procedure is the primary distinction between continuous deployment and continuous delivery. When tests pass, code updates are automatically sent to a staging or pre-production environment as part of continuous delivery, enabling them before being deployed to production for manual review. Conversely, continuous deployment eliminates the need for manual intervention by automatically deploying code changes to production environments when tests pass.
63. How does configuration management fit into the DevOps process?
Ans:
Throughout the software development, testing, and deployment lifecycle, configuration management in DevOps refers to the monitoring and regulation of modifications to the Infrastructure, software, and other components. It does this by automating resource provisioning, configuration, and maintenance, ensuring consistency, stability, and scalability. Version control, environment synchronization, and compliance tracking are made easier by configuration management solutions, which let teams effectively manage complex systems and react to changes quickly.
64. How can ongoing monitoring aid in the upkeep of the system’s complete architecture?
Ans:
DevOps continuous monitoring aids in maintaining the system’s complete architecture by giving current information about its stability, security, and performance. It entails keeping an eye on a number of metrics for all environments and components, including CPU and memory utilization, reaction times, and error rates. Constant monitoring keeps the system robust, effective, and compatible with predetermined standards and objectives by facilitating early issue discovery, proactive troubleshooting, and improvement opportunities.
65. How does AWS fit into DevOps?
Ans:
DevOps teams may use AWS to take advantage of Infrastructure as code, automate resource provisioning, scaling, and management, make monitoring and logging easier, and guarantee high availability and fault tolerance for apps. Additionally, AWS provides services, including AWS CodeBuild, AWS CodeDeploy, and AWS CodePipeline, which facilitate cooperation and agility in DevOps workflows by streamlining the development and deployment processes.
66. List the top three DevOps KPIs.
Ans:
- Deployment Frequency: This metric tracks the frequency of code modifications that are put into production. It shows the effectiveness of the deployment process and the regularity of end-user updates.
- Mean Time to Recover (MTTR): Measuring the average time needed to recover from an incident and restore service, indicating how well incident response and recovery procedures worked.
- Lead Time for Changes: Assessing how quickly new features or fixes are delivered by tracking the length of time it takes for a code change to go from development to testing and deployment to production. These KPIs assist teams in evaluating the efficacy and efficiency of their DevOps procedures and directing ongoing development initiatives.
67. Explain what configuration management has to do with “Infrastructure as Code.”
Ans:
The term “Infrastructure as Code” (IaC) describes the approach of maintaining and delivering computing infrastructure without the need for manual operations by using machine-readable specification files. To ensure consistency and repeatability, infrastructure automation (IaC) automates the setup, deployment, and administration of infrastructure components such as servers, networks, and databases.
68. How is AWS implemented?
Ans:
AWS CDK (Cloud Development Kit), Terraform, and AWS CloudFormation are some of the services used to develop Infrastructure as a Cloud (IaC). Using templates or programming languages, users can describe infrastructure components in code that are then executed to provide and manage resources in AWS environments automatically.
69. What Data Is Needed for Bootstrapping?
Ans:
Access to financial data, such as anticipated spending, revenue projections, and possible funding sources, is vital. A thorough comprehension of your product or service, how it addresses client pain points, and its distinctive value proposition is essential. Ultimately, a well-considered business plan that outlines strategy, objectives, and a plan of execution is required.
70. What are the DevOps antipatterns?
Ans:
DevOps antipatterns include rigid processes, isolated teams, a lack of automation, a disregard for feedback loops, an excessive reliance on tools, a clash in culture, a disregard for security, and a treatment of DevOps more like a job title than a cultural shift.
71. What advantages does version control offer?
Ans:
Version control has many advantages, such as facilitating team collaboration, tracking version changes in the code, allowing for error rollbacks, streamlining code review procedures, improving code organization, facilitating branch experimentation, providing audit trails for compliance, enhancing code stability, effectively tracking bugs, and supporting continuous integration and deployment workflows.
72. Describe the DevOps concept of “Shift left to reduce failure.”
Ans:
DevOps’ “shift left to reduce failure” approach strongly emphasizes including security, testing, and other quality assurance methods early in the development process. By addressing issues as early in the software development lifecycle as possible, teams can minimize risks, cut down on errors, and improve overall product quality. This will result in fewer failures and more seamless deployments.
73. What is the deployment pattern for blue and green?
Ans:
A DevOps technique known as the “Blue/Green Deployment Pattern” maintains two identical production environments, dubbed “Blue” and “Green.” While one environment, like Blue, handles live traffic, another, like Green, updates with new code or other modifications. Traffic is moved from the active environment to the upgraded one after testing, enabling smooth deployments with little downtime and the opportunity to roll back if problems occur.
74. What Does Constant Testing Entail?
Ans:
Continuous testing is a DevOps methodology that integrates testing at every stage of the software development lifecycle, from conception to implementation. Ensuring that code updates match quality requirements and do not introduce regressions entails automating testing methods, running tests often, and implementing feedback loops. Delivery is accelerated through continuous testing of high-quality software and the early detection and resolution of problems.
75. Define Automation Testing?
Ans:
Using software tools and scripts to test cases automatically without human interaction is known as automation testing.
Writing scripts are
- run tests,
- compare outcomes, and
- providing reports is part of it.
76. What advantages might automation testing offer?
Ans:
Among the many advantages of automation testing is improved test coverage, which guarantees that more application components are examined in-depth. Tests may be conducted more quickly and often thanks to its great acceleration of test execution. Automation lowers the possibility of human error, increases test accuracy, and yields more dependable results. Another essential benefit of test scripts is their reusability, which saves time and effort by enabling the same scripts to be used for several projects or test cycles. Furthermore, automation makes early defect discovery easier, allowing problems to be found and fixed sooner in the development process.
77. How may testing be automated inside the DevOps lifecycle?
Ans:
Testing may be automated throughout the DevOps lifecycle by including automated test scripts in the CI/CD pipeline. Automated tests can be started during the development, deployment, and post-deployment stages using tools like Jenkins, Bamboo, or GitLab CI. This guarantees ongoing feedback and quick problem detection.
78. Why is DevOps dependent on Continuous Testing?
Ans:
Continuous testing is crucial to DevOps because it guarantees that code changes are adequately tested at every stage of the software delivery pipeline. It aids early problem detection, expedites feedback loops, encourages team participation, decreases risks, and improves overall software quality.
79. What are the essential components of tools for continuous testing?
Ans:
Smooth integration with CI/CD pipelines is a crucial component of continuous testing systems, guaranteeing automated Testing throughout the development lifecycle. To offer thorough coverage, these tools must support a variety of testing methodologies, including unit, functional, performance, and security testing. Tracking test results and promptly spotting problems also require strong reporting and monitoring features.
80. What git command downloads any repository from GitHub to your computer?
Ans:
Git clone is the command used to download a repository from GitHub to your local computer. This command generates a local working directory where you can start making changes in addition to copying the complete repository, including all branches and their history. To begin working on an existing project, developers must use the git clone command, which copies the repository to their local workstation and enables Git tracking and management.
81. What distinguishes the typical Git repository initialization procedure from a bare repository?
Ans:
In Git, a bare repository is mostly used as a central repository and does not have a working directory. Compared to normal repositories, it is smaller and operates faster over the network since it does not contain checked-out copies of the files. A typical repository, on the other hand, comes with a working directory where files can be checked out for modification.
82. How can a commit that has already been pushed and made public be undone?
Ans:
Git revert is the command to undo a commit that has been pushed and made public. Without changing the commit history, this step generates a new commit that effectively undoes the changes made by the previous commit. Git revert preserves the repository’s history by providing a new commit that undoes the modifications made in the last commit, leaving the old commit unaltered. This contrasts with other methods, such as git reset, which can rewrite history and cause problems in shared repositories. This method works exceptionally well in group settings when maintaining the commit history is crucial.
83. Describe the distinction between git pull and git fetch.
Ans:
Git fetch refreshes your local branches with the most recent changes from the remote repository without changing your working directory by obtaining the most recent updates from the remote repository and bringing them into your local repository. This enables you to examine the modifications before merging them into your active branch. Git pull, on the other hand, automatically combines the most recent changes into your current branch in addition to fetching them. This is a quick and easy technique to maintain codebase synchronization with the remote repository because it directly updates your working directory with the latest changes.
84. Describe Git stash.
Ans:
Git stash allows you to safely swap branches or work on other projects without losing your ongoing work. It does this by temporarily storing changes that still need to be committed. This is very helpful if you need to go from your current activity to another branch to investigate without committing unfinished changes or to address an urgent issue. Git commands can be used to examine and manage the stored changes kept in a stack. When you’re ready to pick up where you left off, you may use git stash apply to apply the changes stashed back to your working directory, restoring your previous state without interfering with your workflow.
85. Describe the Git branching principle.
Ans:
In Git, branching is the process of separating work on individual features or fixes from the main development line. Because each branch represents a separate development line, numerous developers can work simultaneously without affecting the modifications made by the other developers. To manage the development workflow efficiently, branches can be built, merged, and removed.
86. How do Git Merge and Git Rebase vary from one another?
Ans:
- By creating a new merge commit that integrates the modifications from both branches while preserving the whole history of each branch, Git Merge merges the histories of the two branches.
- This method creates a non-linear history that includes the merge commit while maintaining the context of the modifications performed in both branches.
- Git Rebase, on the other hand, operates by reapplying or transferring commits from one branch to another.
- The requirement for a separate merging commit is essentially eliminated by this method, which rewrites the commit history to provide a linear sequence of commits.
87. Describe Git bisect.
Ans:
- Git bisect is a command-line tool that helps developers quickly determine the root cause of problems. It performs a binary search through the commit history to locate the precise commit that created a fault or defect in the codebase.
- Git bisect is a tool that uses binary search to systematically reduce the range of commits in order to identify the commit that introduced the bug.
88. Describe Jenkinsfile.
Ans:
The Jenkinsfile, a text-based configuration file, defines the Jenkins Pipeline, including all of its stages, phases, and configuration settings. By defining and managing their CI/CD pipelines as code, developers may achieve automation, reusability, and version control.
89. Describe the two kinds of Jenkins pipelines and their syntax.
Ans:
Jenkins’s two categories of Git Merge preserve the commit histories of both branches while integrating changes from one branch into another by generating a new merge commit. Git Rebase creates a linear history with cleaner, better-organized commits by transferring changes from one branch to another. Declarative and scripted pipelines are two types of pipelines. Scripted Pipeline is more flexible and allows users to design custom logic and control flow.
90. Define Scripted Pipelines.
Ans:
Scripted Pipeline is more flexible and allows users to design custom logic and control flow. It employs the Groovy scripting dialect. Its syntax entails writing Groovy code into stages and defining the pipeline’s execution location using the “node” block. Declarative Pipeline, on the other hand, uses predefined directives in a more formal syntax. The “pipeline” block is used in its syntax, and stages, phases, and post-actions are defined declaratively using syntax like YAML