
If you’re looking for FortiAnalyzer Interview Questions & Answers for Experienced or Freshers, you are in right place. There are a lot of opportunities from many reputed companies in the world. According to research, FortiAnalyzer has a market share. So, You still have the opportunity to move ahead in your career in FortiAnalyzer Engineering. ACTE offers Advanced FortiAnalyzer Interview Questions that help you in cracking your interview & acquire a dream career as FortiAnalyzer Engineer.
1. What square measures FortiAnalyzer’s fundamentals?
Ans:
The FortiAnalyzer platform may provide enhanced information on security events across your network by combining network work, analysis, and coverage into a single system. The FortiAnalyzer product line reduces the effort required to review and uphold policies and also identifies attack patterns to help America adjust its policy framework. FortiAnalyzer offers coverage, analysis, and centralized work on a virtual platform.
2. Which square best represents the features of the virtual appliances FortiAnalyzer?
Ans:
- The possibilities and benefits offered by FortiAnalyzer virtual appliances are as follows:
- FortiAnalyzer virtual appliances provide more than 550 reports and modifiable charts that support the monitoring and upkeep of acceptable use guidelines, attack trends, and policy compliance.
- The network capability and utilization knowledge coverage of FortiAnalyzer allow for cost-effective network management. • FortiAnalyzer’s descendible design enables the devices to operate in collector or analyzer modes for optimal log processing.
- FortiAnalyzer’s advanced built-in features, Including event correlation, rhetorical analysis, and vulnerability evaluation, provide crucial tools for comprehensive network security.
- Network-wide compliance is ensured by secure knowledge aggregation from several FortiGate and FortiMail appliances.
3. In what ways does FortiAnalyzer improve visibility within its platforms?
Ans:
FortiAnalyzer offers its services, including data processing, content archiving, reporting, security event analysis, rhetorical analysis, malicious file quarantining, and vulnerability management, to businesses of all sizes from a single, central place. It provides a streamlined, consolidated view of an organization’s threat exposure by its ability to aggregate a variety of data and correlate and analyze different written account information with geographical security knowledge from Fortinet appliances and third-party devices.
4. How is the information related to Security Events managed by FortiAnalyzer?
Ans:
- The FortiAnalyzer platform may be integrated into the current security architecture to read safety events, archival content, and vulnerability assessments, allowing us to turn back time.
- The FortiAnalyzer platforms retrieve all available data from Fortinet solutions, including email, traffic, event, virus, and attack filtering. Once activity rhetorical analysis and network auditing are completed, it eliminates the need for human log file searching.
- The file quarantine, vulnerability assessment, and centralized knowledge archiving features of the FortiAnalyzer platform reduce the amount of time needed to handle the vary.
5. What problem arises while deciding between virtual and hardware appliances?
Ans:
The majority of organizations today utilize virtual or hardware IT infrastructure due to various financial limitations. This makes every piece of hardware and virtual appliance included in a security plan necessary. Depending on the environment, which combines virtual and physical IT infrastructure, FortiAnalyzer will be installed as a hardware or virtual appliance. FortiAnalyzer can log events from hardware appliances running FortiOS, virtual appliances, or a combination of both.
6. How much of a benefit does Network Event Correlation offer?
Ans:
An important part of integrated management is the event correlation component. Across the organization’s network, Network Event Correlation enables computer users to identify and respond to network security concerns promptly.
7. Explain the distinctions between FortiAnalyzer’s stateful and stateless firewalls.
Ans:
| Stateful Firewall | Stateless Firewall |
|---|---|
| Maintains a state table to track connections | Does not keep track of the state of connections |
| Considers the state of the connection | Evaluates each packet individually |
| May introduce more processing overhead | Typically has lower processing overhead |
8. How can we take advantage of the Versatile Management Solutions offered by FortiAnalyzer?
Ans:
The following are important components of FortiAnalyzer’s managerial skill:
- Diversity of sorts of elements.
- Flexibility in architecture.
- Extremely adaptable.
- Easy licensing.
8. In what ways might FortiAnalyzer’s performance be used to enhance its upmarket capacity?
Ans:
The FortiAnalyzer family of models may dynamically grow storage to meet retention and compliance requirements, and they handle thousands of FortiGate and FortiClient agents.
9. How does FortiAnalyzer’s centralized work of many record types measure up?
Ans:
This record, together with information about electronic messaging activities and knowledge, viruses, attacks, system events, traffic activity, and internet filtering. From one location, system directors will examine the entire network.
10. How does the seamless integration of FortiAnalyzer with Fortinet products provide advantages?
Ans:
The closed connection with Fortinet products optimizes its functionality and enables FortiAnalyzer resources to be managed economically via FortiGate or other FortiManager user interfaces.
11. What benefits result from selecting the Collector and Standalone modes for FortiAnalyzer?
Ans:
- In response, FortiAnalyzer will be installed as a standalone unit or tailored for particular tasks.
- It is contingent upon the circumstances and required utility. Not every business requires every feature and benefit offered by FortiAnalyzer.
13. How does FortiAnalyzer differ from antiquated techniques?
Ans:
- The answer is that threats within networks are always changing due to factors including organizational expansion, new laws, and operational requirements. Traditional approaches focus on identifying and cataloging network hazards via labor, examination, and coverage over an extended period.
- FortiAnalyzer provides enterprise-class solutions not only to identify these risks but also to provide you with the flexibility to change with the dynamic network. FortiAnalyzer will aggregate logs in a highly class-conscious, layer work architecture and produce incredibly customized reports for structure requirements.
14. What does knowledge mining and content work entail?
Ans:
- Log aggregation and archiving are now crucial in identifying security concerns and controlling network usage. FortiAnalyzer not only offers a comprehensive analysis, coverage, and period work, but it also makes complex content work of user activity and network traffic possible.
- Activities will be monitored throughout time, recorded, and then examined again if needed. User, protocol, source, destination, and other tracking of activities will be partially implemented.
- Additionally, the content that has been modified during a session can be accessed. Not only is content creation vital to comply with laws such as HIPAA and SOX, but it is also very critical to enforce acceptable usage regulations and safeguard firm assets and holdings.
15. What Does an Exposure Analysis Tool Do?
Ans:
The built-in vulnerability scanner in FortiAnalyzer finds flaws in a variety of servers, such as mail servers, file transfer protocol servers, other operating systems, or Windows hosts. It then generates vulnerability reports that illustrate the possible openings for attacks on a particular device.
16. What level of detail can we obtain with FortiAnalyzer’s help?
Ans:
- The FortiAnalyzer software (UI) enables system directors to delve deeply into security log information and provide the granular level of reporting required to understand what’s going on throughout the whole network.
- Due to network traffic, network directors are able to examine log and content information based on historical or temporal knowledge.
17. What is the Log Browser?
Ans:
The Log Browser makes it easier for Americans to view log files or communications from devices that are registered. We can locate certain information by simply filtering the log files and messages.
18. What square measures the supporting devices of the FortiAnalyzer?
Ans:
These include the following: FortiClient PC Endpoint Security, FortiGate Multi-Threat Security Systems, FortiMail Email Security Systems, and FortiClient Mobile Endpoint Security.
19. How will the scientific address of FortiAnalyzer be edited?
Ans:
In order to make changes to the FortiAnalyzer VM science address, we would like to do the following actions:
- To access the read product page, select Plus > Manage/View product from the toolbar.
- Choose the serial range for the FortiAnalyzer VM, and the Product Details page opens.
- To change the specific FortiAnalyzer VM’s outline, partner details, and science address, select Edit.
20. What does “Thick Provision Lazy Zeroed” mean?
Ans:
The process of dividing up storage space among virtual machine (VM) disks that create virtual disks in default thick format is known as thick provision lazy zeroed. The dense
21. What is Eager Zeroed Thick Provisioning?
Ans:
The VMware provisioning technique known as “thick provisioning eager zeroed” creates a virtual machine (VM) disk in the default thick format. A feature of VMware vSphere called VMware Fault Tolerance, which provides high availability (HA) for enterprise computer code applications, is supported by a thick provision eager to be zeroed.
22. What is skinny provisioning?
Ans:
- One way to boost the effectiveness of the accessible area in enclosure networks (SAN) is through thin provisioning (TP).
- Thin Provisioning works by distributing disk cabinet space across several users in a flexible way, accommodating each user’s minimum area requirement at any given time.
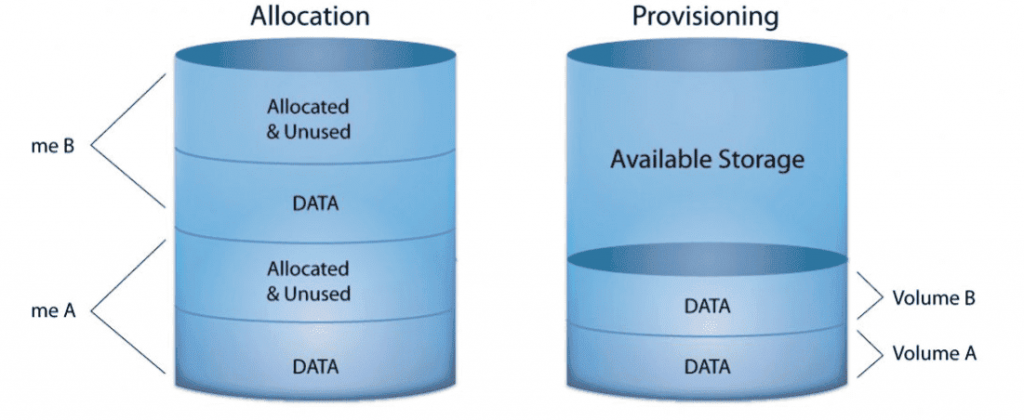
23. What is provisioning for old storage?
Ans:
To maximize an enclosure network’s performance, storage provisioning is a technique for distributing storage, occasionally among different server hard drive sections (SAN). The SAN administrator has traditionally handled this, and it is a laborious process.
24. How does one fetch?
Ans:
- In order to facilitate knowledge analysis on the Log read, FortiView, and Reports tabs, we can retrieve offline reports that contain compressed logs from one FortiAnalyzer unit to a second FortiAnalyzer unit wherever the logs are automatically indexed within the data.
- System directors can examine information from compressed logs using FortiAnalyzer’s retrieve capability, which does not negatively impact the initial FortiAnalyzer unit’s performance due to its appealing logs that are occurring in the background.
25. What square measures the functionality of FortiAnalyzer?
Ans:
The banner, which is the topmost element on the website, features the facilitate button, notifications, admin menu, tile menu, ADOM menu (when enabled), and house button (the Fortnitet logo).
- The menus for the selected pane are located in the tree menu, which is on the left side. Unavailable through Device Managers.
- The Content pane includes widgets, lists, configuration options, or alternative information based on the selected pane, menu, or options. The content pane handles the majority of management activities.
- The content pane contains options for managing content, such as create New and Delete, located just above the toolbar.
26. How will we typically replace worn-out discs?
Ans:
The tough disk of a FortiAnalyzer unit needs to be changed whenever it breaks. Hot-swapping refers to the process of replacing a fixed disk while the FortiAnalyzer unit continues to operate in devices that enable hardware RAID from FortiAnalyzer. Before replacing the fixed disk on FortiAnalyzer units with computer code RAID, the device should be closed.
27. How likely are we to include a static route?
Ans:
The next steps make adding a static route in FortiAnalyzer simple. We have to navigate to System Preferences > Network.
- Next, we should consistently press the generate New button after selecting the Routing Table button to feature an associated IPv4 static route or the IPv6 Routing Table button to feature an associated IPv6 static route. The New Network Route pane for the product is shown.
- In order to create the new static route, we can now put the values together and click OK.
- In order to create the new static route, we can now put the values together and click OK.
28. How does a thick virtual disk differ from an eager zeroed thick virtual disk?
Ans:
The majority of people are aware of the differences between virtual disks that are thickly and thinly provisioned. The blocks of a thick disk are allocated in the virtual machine once the disk is constructed, but not those of a skinny disk. Although there is very little performance difference between a thick disk and an eager zeroed thick disk, some applications still require eager zeroed thick provisioned disks.
29. How can one comprehend the FortiGate from Fortinet?
Ans:
It has features including net filtering, SSL scrutiny, automatic threat prevention, and intrusion hindrance system (IPS). Computer science (AI) is another feature of FortiGate that aids in proactive threat identification.
30. How will bodily access be changed?
Ans:
To change body access, we should always 1st head to System Settings > Network.
- By default, port1 settings are going to be displayed. We are able to assemble body access for a special interface.
- We should Click All Interfaces and choose the interface from the list.
- We should set the sciencev4 IP Address/Netmask or the IPv6 Address.
- After that, we should always choose one or a lot of Body Access varieties for the interface and set the default entrance and name System (DNS) servers followed by clicking on Apply.
31. Which technique may be used on a FortiMail unit to prevent email messages from being unintegrated for units that do not exist?
Ans:
Recipient Address Verification ought to be adopted to stop Email messages from being unintegrated for non-existent accounts.
32. 98. Define UTM?
Ans:
- A complete security solution that provides multiple protection against a range of cyber threats is called Unified Threat Management (UTM).
- It combines several networking and security features into a single platform, including features like content filtering, antivirus, and defense against spyware and unauthorized internet access.
- In complex IT settings, UTM solutions are very helpful for streamlining security administration.
33. How can one understand Fortinet as a partner company?
Ans:
Fortinet is a conglomerate of multinational corporations based in Sunnyvale, California, employing more than 7,000 people. Network security solutions from Fortinet include firewalls, antispam, end security, spyware, and antivirus software. In order to educate more developers about cybersecurity, Fortinet also announced the launch of the Network Security Expert (NSE) technical certification program.
35. Explain what a Next-Generation Firewall.
Ans:
The Next-Generation Firewall (NGFW) serves as a firewall with thorough packet analysis. It has every feature found in a typical firewall. In addition, it offers Shell (SSH) management, Secure Sockets Layer (SSL) examination, application awareness, and an Integrated Intrusion Protection System (IPS).
36. What distinguishes a normal firewall from a next-generation firewall?
Ans:
The most common differences between a regular firewall and a next-generation firewall are listed below:
- An NGFW can identify a user, but a regular firewall is unable to do so.
- Only traffic supported by levels two through four will be monitored by a typical firewall.
- A conventional firewall only shows up at the incoming packets’ header, footer, source, and destination. The NGFW will examine the information in the incoming packet.
37. What is the UTM?
Ans:
IT departments can use it to address security issues as it offers a variety of security measures on a single platform. It has features including spyware, content filtering, antivirus software, and unapproved website access.
38. Could you elaborate on integrated threat management?
Ans:
Integrated threat management is a complementary strategy used to combat malware such as spam and advanced threats. It offers protection against infiltration at both end and entry points. It protects each element in a highly heterogeneous and integrated context from all threats, enabling simplified administration.
39. Describe Security Fabric.
Ans:
- It offers smooth security by broadening the attack surface, enriching endpoints in various situations, etc. Connecting disparate technologies via a single console will speed up operations and close security holes.
- FortiGate uses the symmetric-key algorithms AES and DES to encrypt and decode data. The following algorithms are supported by FortiGate: aes128-md5; aes128-sha1; des-md5; des-sha1; des-sha256; des-sha384; des-sha512
40. Name the various coding mechanisms offered in Fortigate.
Ans:
FirewallFortiGate encrypts and decrypts data using the symmetric key techniques DES and AES. Among the algorithms that FortiGate supports are
- aes128-md5
- aes128-sha1
- des-md5
- des-sha1
- des-sha256
- des-sha384
- des-sha512
41. In the context of the Fortinet Security fabric, what does “Aware” mean?
Ans:
Security materials allow for ongoing improvement and give managers situational awareness. It will spread awareness across the network, indicating a comprehension of potential dangers. Its main goal is to comprehend the information flow or flow throughout the network. It regulates where and to whom the packet is delivered.
42. What is the meaning of ‘Actionable’ in Fortinet Security material?
Ans:
It is a standard collection of centralized orchestration and threat intelligence. As a result, it provides unfair threat intelligence to every security device in your network by comparing global threat intelligence with native network knowledge.
43. Describe the Fortinet Fabric’s “Scalable” functionality.
Ans:
- End-to-end security should be offered with a high degree of monitoring.
- The package from Security Fabric scales not just inside the environment but also smoothly with the data it receives from IoT devices and endpoints.
- From the Internet of Things to the cloud, it safeguards packet knowledge across dispersed networks.
44. What’s the FortiGate firewall
Ans:
The most widely used network firewall in the world, FortiGate NGFW offers unmatched threat intelligence and security performance powered by AI, complete visibility, and networking and security convergence.
45. In the Fortinet Security Fabric, which is the open genus Apis?
Ans:
An organization can require several security devices with distinct purposes. To integrate Fortinet security solutions, security materials offer open genus Apis that must be accustomed to embodying these devices from technology.
46. In what ways does Fortinet’s Fabric-Ready Partner program differ from the other partner initiatives?
Ans:
The Fortinet Fabric-Ready partner program increases transparency by facilitating integration via open-source APIs and distributing scripts that make use of DevOps technologies. Integration with Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform, VMware NSX, and other platforms is made possible using material connectors. Workflows, security rules, and application deployments may all be automated with its help.
47. What Is a Firewall from Fortinet?
Ans:
- Fortet firewalls are nothing, but they’re mostly designed with security processors in mind to change the greatest threat to security and performance available in the industry for SSL-encrypted communications within a company.
- The main uses for this Fortinet firewall are granular application visibility, user knowledge protection, and secure Internet of Things devices. Appliance firewalls of this type are made to trace issues reasonably.
48. What is FortiGate at SPU?
Ans:
The Security Process Unit (SPU) Content Processors (CPs) included in the majority of FortiGate models speed up a number of frequently occurring, resource-intensive security-related procedures. The most central processing unit determines which duties are assigned to Hertz, who operates at the system level. More recent FortiGate devices support CP9 processor
49. What are the considerations that should be made when installing a Fortinet firewall in the rack?
Ans:
The region underneath is small print that provides support for a method of assembling Fortinet firewalls:
- First, adjust the room’s temperature. This can be done within the close temperature range specified by the system management of the instrument’s original manufacturer (OEM).
- Making use of a system such as dependable power attachment.
- Firewalls are sufficient system flow is utilized to ensure secure operations.
- Firewalls Sufficient system safeguards are employed to manage overcurrent and supply wiring.
50. Why is it possible to use a FortiMail device in clear mode?
Ans:
The administrator need not monitor DNS records for protected domain names if the FortiMail unit is operating in clear mode.
51. What is the purpose of a FortiAnalyzer dataset question?
Ans:
The FortiAnalyzer datasets are collections of log messages derived from devices under observation. The datasets were supplemented by charts developed in the FortiAnalyzer area unit. Use the supplied datasets to create a chart; if not, create your unique datasets by running an SQL info query on the log messages stored on the FortiAnalyzer unit.
52. Which profiles are frequently used as a defense against denial-of-service assaults?
Ans:
- The acronym for FortiGate Agglomeration Protocol is FGCP. This is one of the usual high-handiness options and proprietary solutions that the Fortinet firewall offers.
- The two firewalls that make up the FortiGate High Handiness Answer are mostly used to configure the high-handiness operation.
53. What is a cluster of FGCP?
Ans:
The acronym for FortiGate Agglomeration is the FGCP procedure. This is one of the usual high-handiness options and proprietary solutions that the Fortinet firewall offers. The two firewalls that make up the FortiGate High Handiness Answer are mostly used to configure the high-handiness operation.
54. What are the various actions that a user should perform prior to updating the Fortinet security firewall’s computer code?
Ans:
- Store the prior configuration after making a backup.
- Make a copy backup before deleting the old one.
- The Fortinet computer code frequently fails. This can be among the worst circumstances.
- The user must now explore the NOTE command, which the manufacturer provides for free. This could provide useful information on firewall processes related to debugging fixes and examine them during the show, etc.
- Complete the system upgrade.
55. What occurs if the FortiGate unit’s disk work is turned off?
Ans:
The logs are written to nonvolatile storage as a unit if disc work is disabled. Frequent rewrites can reduce the lifespan and capacity of flash drives.
56. How can I use the internet to turn off actions related to body access management?
Ans:
The executive activity access from the skin world via the user interface (user interface) AND the user interface via the CLI will be disabled.
- Configure the user interface.
- Revise.
- End; unset permission to access.
57. Write the essential command for the user interface to turn off the car’s USB installation.
Ans:
The essential user interface code element to deactivate or turn off USB installation is as follows:
- Configuration system
- Configure the auto-install system.
- Deactivate auto-install-config.
- Turn off auto-install-image.
- Conclude.
58. In FortiGate, what is Ipsengine?
Ans:
The software system that uses application management and IPS scanning methods on content going through FortiOS is called the Fortigate IPS engine. Updates to the IPS engine include bug fixes, performance improvements, and detection.
59. How can Fortinet offer assistance in the event that a network administrator is dishonest about a problem?
Ans:
The following are the essential options available to address any problem:
- System of knowledge base.
- Document library management with Fortinet.
- Communities that offer certification and training.
- Using the Fortinet Video collection.
- Upkeep of discussion forums.
- Convenient technical contact support.
60. Under what conditions is an email message received by the FortiGate unit subject to the bounce verification? Take new ans
Ans:
The front MAIL After creating and activating a bounce verification secret, the FROM field has a null reverse path.
61. Describe NP6Lite.
Ans:
The majority of IPv4 and IPv6 traffic, IPsec VPN cryptography, CAPWAP communication, and multicast traffic can all be offloaded using NP6. Similar to the NP6, but with a smaller output and a few helpful constraints (such as not offloading CAPWAP data), the NP6Lite may be a component of the Fortinet SOC3.
63. How do bodily domains work?
Ans:
- The admin administrator is modified by administrative domains (ADOMs) in order to limit the access rights of various FortiAnalyzer unit directors to a specific group of devices in the device list. ADOMs will prevent access to information from a single VDOM that has been chosen for a tool on Fortinet devices that have virtual domains (VDOMs).
- Activating ADOMs modifies the interface and interface, as well as their functions. Because of the admin administrator, access to the functions is contingent upon your log-in status. You will have access to every ADOM if the admin administrator has logged you in.
- The settings in your administrator account control access to ADOMs if you’re not logged in as the admin administrator.
64. How can I add more gadgets to trick the wizard?
Ans:
To add gadgets that the wizard is exploiting. Verify that you are in the appropriate ADOM before victimizing someone else. Click on Add Device in Device Manager. Set up the following parameters:
- IP Address: this is the device’s information science address.
- SN: This is the device’s serial range.
- Device Name: name of the blood type on the gadget.
- Device Model: Select the device’s model.
- Firmware Version: Select the device’s code version.
- Description: (Optional) Type a description of the gadget.
- Select Next After being delivered to the ADOM, the device is ready to begin sending causality logs to the FortiAnalyzer unit, provided it is productive.
- To finish adding the device and close the wizard, click end.
65. What is the material view?
Ans:
The Fabric Read module allows you to view the list of endpoints and form material connectors. In version vi.0 ADOMs and later, the content read tab is available.
66. How Can Historical Average Log Rates Be Displayed?
Ans:
To display the average log rates historically:
- Verify that you are in the appropriate ADOM when victimizing other ADOMs.
- Select the Devices Total tab from the fast-standing bar by going to Device Manager.
- To view the graph, select the desired quantity in the Average Log Rate (Logs/Sec) column.
- To view more details, move the cursor over the graph.
67. Material Connectors: What Are They?
Ans:
Yes, you can create the following types of material connectors using FortiAnalyzer:
- Storage on page thirty-three;
- ITSM.
68. In FortiGate, what is IDS?
Ans:
An associate degree application called an intrusion detection system (IDS) keeps an eye on network traffic and looks for known risks as well as questionable or hostile conduct. When the IDS finds threats or security issues, it notifies those security groups and delivers alerts.
69. Next-Generation Firewalls: What Are They?
Ans:
- Third-generation firewall technology includes Next-Generation Firewalls (NGFWs), which combine classic firewalls with additional network device filtering features, including intrusion prevention systems (IPS) and application firewalls employing in-line deep packet inspection systems (DPIs).
- Other methods, including website filtering, QoS/bandwidth management, antivirus inspection, TLS/SSL encrypted traffic analysis, and third-party identity management integration (e.g., LDAP, RADIUS, Active Directory), could also be used.
70. Is it feasible for the FortiMail Administrator to obtain email account information from an LDAP server?
Ans:
The profile is then linked to the regionally structured domain by assembling the LDAP profile sections “User question options” and “Authentication.”
71. When a supplier information scientific address uses a sender name on a FortiMail unit, does it generate spam?
Ans:
- FortiMail briefly fails and delays email communications from that particular information science address.
- Emails sent that provide an information science address are permanently rejected by FortiMail.
- FortiMail quarantines all emails sent from that supply information scientific address.
72. How will we benefit from the safety feature of the Fortinet Security material?
Ans:
To reduce time to shield, global and native risk intelligence and alteration data are shared throughout specific goods. For the many locations and functions within the network, security will not only need to use strong security measures but also true visibility associate degree. The management wants these various components to work together as a cohesive security system.
73. In the context of Fortinet Security Fabric, what do we understand by unjust?
Ans:
In order to set itself apart from other vendors, Fortinet’s design integrates a unified software system, highly optimized hardware and computer code processes with unparalleled zero-day discovery, and a detection method that combines hardware virtualization, machine learning, and activity detection.
74. What will the Fortinet Security Fabric’s Open Arthropod Genus reveal to us?
Ans:
- Leading technology partners can incorporate the material with ease thanks to the material’s well-defined, open arthropod genus. Real security material, of course, enables North American countries to get the most out of our current security technology investment.
- For this reason, Fortinet has created a number of open, clearly defined arthropod genera that allow technology partners to be included in Fortinet Security content. When used together, the Fortinet Security content allows for swift adaptation to both the dynamic threat landscape and the constantly changing specification.
75. Why is a security material strategy so vital to network security in the current environment?
Ans:
In the current period of cultural movements, organizations have had to address an increasing number of issues that put an incredible amount of pressure on their security skills, like virtualization and the Internet of Things.
76. What distinguishes Fortinet’s security fabric strategy from other vendors’ attempts?
Ans:
In order to set itself apart from other vendors, Fortinet’s design integrates a unified software system, highly optimized hardware and computer code processes with unparalleled zero-day discovery, and a detection method that combines hardware virtualization, machine learning, and activity detection.
77. How will the security fabric from Fortinet help its international network of distributors and solution providers?
Ans:
- Security remains one of the channel’s most significant potential due to its complex and significant nature. Partners who can organize, plan, implement, and optimize an integrated security system are in more demand due to their expertise.
- Associates will help their clients gather and respond to a lot of unfair intelligence, coordinate risk responses, and alter the development, dissemination, and coordination of their security management and additional research by fusing conventional security devices with emerging technologies into an integrated security cloth.
78. How does Fortinet’s Fabric-Ready Partner program differ from the partner initiatives that other vendors frequently advertise?
Ans:
Fortinet’s Fabric-Ready Partner Program enlists top-tier technological alliance partners, just like a number of other partner programs. In contrast to other ways, Fortinet’s methodology actually enables the partners to give pre-integrated, end-to-end security services ready for deployment in any company.
79. Under what situations is an email message received by the FortiMail unit subject to an antispam?
Ans:
If any of the following applies to an incoming email, bounce verification may be required: Verification of bounces is enabled. There is a minimum of one bounce address key. The Bypass Bounce Verification option is deactivated in the protected domain that the receiver is a member of (see Configuring protected domains).
80. Which operational mode permits the FortiMail unit to be controlled as a full-featured email server?
Ans:
SpamTitan Cloud servers can utilize recipient verification to confirm that the recipient’s email address is valid before sending an email to them. If the user does not exist, the email will be stopped before it reaches the mail server (recipient verification is turned off by default).
81. What distinguishes a traditional firewall from a next-generation firewall?
Ans:
NGFWs provide all of the standard features of classic firewalls, including support for virtual private networks (VPNs), packet filtering, stateful monitoring, and network and port address translation (NAT). The goal of next-generation firewalls is to incorporate additional OSI model levels, enhancing.
82. What is Conventional Firewall?
Ans:
- A conventional firewall acts as the cornerstone of network security, controlling and keeping an eye on network traffic entry and exit in accordance with predetermined security rules.
- These firewalls usually use one of two inspection methodologies: stateless or stateful. They are primarily concerned with managing network traffic.
- Of the OSI architecture. Moreover, NGFWs provide a more thorough security solution by carefully examining the packet data in addition to the headers.
83. What is your knowledge of Fortinet as a company?
Ans:
- Fortinet is a major multinational corporation based in Sunnyvale, California, that employs more than 7000 people worldwide.
- The business focuses on security-driven networking solutions, which include antivirus software, state-of-the-art firewalls, antispam services, and endpoint security.
- As evidence of its commitment to developing a workforce skilled in cybersecurity, Fortinet has also launched a technical certification program, the Network Security Expert (NSE)
84. Which back-end servers are typically known to provide recipient verification?
Ans:
SpamTitan Cloud servers can employ recipient verification to confirm that the recipient’s email address is valid before sending an email to them. If the receiver (recipient verification is turned off by default) does not exist, the email will be banned before it reaches the mail server. Servers for LDAP and SMTP.
85.What is your knowledge about FortiGate from Fortinet?
Ans:
The Fortinet product FortiGate is more than a firewall. This all-inclusive cybersecurity solution provides multiple layers of defense against a range of threats. Advanced features include powerful web filtering, SSL inspection, automatic threat defense systems, and an intrusion prevention system (IPS) are included. FortiGate’s proactive threat detection and response capabilities are improved by integrating AI, making
86. What Will The Nonvolatile Storage Include In The Fortimail Unit’s Native Storage Structure?
Ans:
Together with the system configuration and certificates, the nonvolatile storage contains an image of computer code.
87. Which History Log Field Reflects The Fortimail Unit’s Action Regarding a Specific Email?
Ans:
The Fortinet product FortiGate is more than a firewall. This all-inclusive cybersecurity solution provides multiple layers of defense against a range of threats. Advanced features include powerful web filtering, SSL inspection, automatic threat defense systems, and an intrusion prevention system (IPS) are included. FortiGate’s proactive threat detection and response capabilities are improved by integrating AI, making
88. What are Cross-search log messages?
Ans:
- The same SMTP session (with one or more emails sent during the session) or the same email message may be logged in several types of log files since different log file types record different events/activities.
- For instance, the following sorts of log files will record the occurrence if the FortiMail units find a virus in an email message:
- History log: due to the fact that it keeps track of every sent and undeliverable email message metadata.
- Antivirus log: due to the discovery of a virus. The history log contains fewer descriptions of the virus than the antiviral Log.
- Event log: due to the initiation and termination of the antiviral process on the FortiMail system.
89. Tell me about the past of Fortinet.
Ans:
In response, Fortinet, founded in 2000 by Ken and Michael Xie, has achieved notable advancements in the field of cybersecurity. FortiGate, the company’s first main product, was introduced in 2002. During its initial years of operation, Fortinet raised millions of dollars in funding. Over the last ten years, Fortinet has increased the size of its portfolio by making calculated purchases of software firms that deal with security. The launch of Fort AI in February 2020, which demonstrated Fortinet’s dedication to AI-powered security solutions, was a recent significant step.
90. Why Would A Fortimail Unit Be Placed in Clear Mode?
Ans:
In essence, DNS records don’t need to be updated. Set up the “User question options” and “Authentication” parts of the LDAP profile, then link it to the regionally optimized domain.





