
- Introduction to Composite Key
- Why Use a Composite Key in SQL?
- How Composite Keys Differ from Primary Keys
- Characteristics of Composite Keys
- Real-Life Scenarios Where Composite Keys Are Used
- Advantages of Using Composite Keys
- Limitations and Challenges with Composite Keys
- Conclusion
Introduction to Composite Key
In relational database design, ensuring that each record is uniquely identifiable is essential for maintaining data accuracy and enabling efficient data retrieval. Typically, this is achieved by assigning a primary key to a table, often consisting of a single column. However, many real-world scenarios do not have a single column capable of uniquely identifying a record. In such cases, a composite key becomes a critical solution. A composite key is formed by combining two or more columns in a table, where the combination of these columns together guarantees uniqueness for each row. While the individual columns may contain duplicate values, their combined values will always be unique, ensuring the correct identification of each record. Composite keys are commonly employed in many-to-many relationships, transactional databases, link tables, and normalized database designs in Database Training. They help enforce business rules that require multiple attributes to define uniqueness. For example, consider a university database system that tracks student enrollments in courses. An Enrollments table might include Student_ID and Course_ID columns. Neither column alone can uniquely identify a record, since a student may enroll in multiple courses, and a course may have many students enrolled. However, the combination of Student_ID and Course_ID forms a composite key that uniquely identifies each enrollment record. This approach prevents duplicate entries and preserves data integrity. Using composite keys not only strengthens data integrity but also helps align the database structure with real-world business rules. This alignment makes the database schema cleaner and more logical, improving maintainability and efficiency over time. By carefully designing composite keys, database designers can create robust systems that accurately represent complex relationships in data.
To Explore Database in Depth, Check Out Our Comprehensive Database Online Training To Gain Insights From Our Experts!
Why Use a Composite Key in SQL?
In many real-world database tables, especially those that represent relationships, a single column is often insufficient to uniquely identify each row. This is where composite keys become essential. Composite keys combine two or more columns to form a unique identifier, allowing for accurate distinction between records when a single attribute is not enough in How To Start a Career in Database Administration. One of the most common uses of composite keys is in modeling many-to-many relationships, which require an intermediary table that includes combined foreign keys from the related tables. By doing so, composite keys maintain data integrity by ensuring that no two rows share the exact same combination of key column values, thereby enforcing critical business logic constraints. Using composite keys also supports the principles of database normalization by eliminating data redundancy and improving consistency across the system.
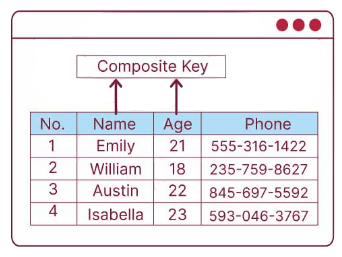
They enable more efficient and meaningful referential designs, particularly in transaction-based or relational datasets, where the connections between entities are best represented through multiple attributes. Moreover, composite keys help avoid the use of synthetic or surrogate keys, such as auto-incrementing numbers, which may have no real-world significance. Instead, composite keys rely on natural identifiers that are directly relevant to the business context, making the data model clearer and more intuitive. Additionally, composite keys maintain referential integrity when used as foreign keys in related child tables, ensuring consistency between related records. This makes the overall database schema more robust and aligned with real-world entities. By reflecting the true nature of relationships and constraints within the data, composite keys contribute to a more accurate and maintainable database design that effectively supports business operations and data analysis.
How Composite Keys Differ from Primary Keys
- Definition and Purpose: A primary key is the cornerstone of relational databases, ensuring each record is uniquely identifiable within a table.
- Simple Primary Key: A simple primary key consists of a single column, often an auto-incremented number or UUID, making it straightforward to implement and use.
- Advantages of Simple Keys: Simple keys simplify query writing, joins, indexing, and foreign key references, contributing to better performance and easier database management in Schema in SQL Server.
- Composite Primary Key: Composite keys include two or more columns combined to create a unique identifier, necessary when uniqueness depends on multiple attributes in complex data models.
- Challenges with Composite Keys: Using composite keys complicates query writing and foreign key relationships since all key columns must be referenced, potentially increasing query complexity and slowing performance.
- Real-World Use Cases: Composite keys better reflect real-world scenarios, such as identifying a book in a specific library branch (Book_ID + Branch_ID) or tracking employee shifts (Employee_ID + Shift_Date).
- Choosing Between Simple and Composite Keys: While both types serve the purpose of uniqueness, selecting a simple or composite primary key depends on the application’s data nature and business logic, balancing simplicity against data model fidelity.
- Composed of Two or More Columns: A composite key uses multiple columns together to guarantee uniqueness in a table, ensuring no duplicate records for the combined fields.
- No NULL Values Allowed: Each column in a composite key must be defined as NOT NULL in Database Training, just like simple primary keys, to maintain data integrity.
- Uniqueness Through Combination: None of the individual columns in the composite key need to be unique alone, but their combined values must uniquely identify each record.
- Defines Table Relationships: Composite keys often serve as junction keys in many-to-many relationships, linking two entities through an intermediary table.
- Used in Foreign Key Constraints: Child tables can reference composite keys by creating foreign keys that include all columns of the composite key, maintaining referential integrity.
- Impact on Indexing and Query Optimization: Composite keys create composite indexes automatically, affecting how the database engine optimizes queries; the order of columns in the key is crucial for index efficiency.
- Usage in Queries and Joins: Composite keys are used in JOIN and WHERE clauses to match related records, but require careful construction of queries since all key columns must be specified.
- Reflect Real-World Data Models: Composite keys naturally mirror actual business scenarios by linking multiple entities in a meaningful way.
- Avoid Surrogate Keys: They eliminate the need for artificial or synthetic IDs when natural attribute combinations can provide uniqueness in How To Become a Data Modeler.
- Better Normalization: Composite keys promote breaking down large tables into smaller, well-structured, and logically connected entities, supporting database normalization.
- Supports Referential Integrity: By enforcing consistent relationships between parent and child tables, composite keys make data modeling more robust and reliable.
- Improved Data Integrity: They prevent duplicate rows by ensuring that no two records share the same combination of key column values.
- Reduces Redundancy: Composite keys help avoid unnecessary data duplication across multiple tables, maintaining cleaner data storage.
- Multi-Column Indexing and OLAP Usage: Automatic indexes on composite keys boost query performance, and these keys play a key role in defining dimensions for OLAP cubes and data warehousing systems.
Do You Want to Learn More About Database? Get Info From Our Database Online Training Today!
Characteristics of Composite Keys
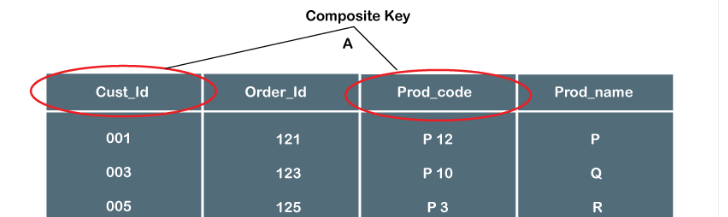
Real-Life Scenarios Where Composite Keys Are Used
In many practical database systems, composite keys are not only useful but often necessary to accurately model real-world data relationships. Various industries rely on composite keys to maintain data integrity and ensure unique identification where single columns fall short. In education systems, for example, an Enrollment table may use a combination of Student_ID and Course_ID to uniquely identify which student is enrolled in which course. Similarly, exam results often track performance using a composite key of Student_ID, Subject_ID, and Term to differentiate results across subjects and academic periods. In retail and e-commerce, composite keys are essential for order management; an Order Items table might use Order_ID combined with Product_ID to guarantee that each product appears only once per order. Inventory management systems also rely on composite keys like Product_ID and Store_ID to track stock levels across different locations in What is a Transaction Processing System. Transportation and airline industries make extensive use of composite keys as well. Flight schedules are uniquely identified by Flight_Number and Date, while seat bookings require a combination of Passenger_ID and Flight_ID to ensure each booking is unique per passenger and flight. Healthcare systems benefit from composite keys in appointment management, combining Doctor_ID, Patient_ID, and Appointment_Time to prevent scheduling conflicts. Medication tracking may use Patient_ID, Medication_ID, and Start_Date to monitor drug administration accurately. Human resources departments employ composite keys to track employee assignments and work schedules. For instance, Employee_ID paired with Project_ID prevents double assignment of employees, and Employee_ID with Shift_Date records shift planning efficiently. These examples demonstrate that composite keys are integral to robust data design and accurately represent complex business logic, highlighting their crucial role across various domains.
Would You Like to Know More About Database? Sign Up For Our Database Online Training Now!
Advantages of Using Composite Keys
Limitations and Challenges with Composite Keys
Composite keys offer significant advantages in relational database design, but they can also introduce complexities that may not always be desirable depending on the context. One of the main challenges is that queries involving composite keys tend to be more complicated. Since composite keys consist of multiple columns, joins and lookups require specifying all key components, which can increase the complexity of SQL statements and impact readability. This complexity extends to database maintenance as well. Any modification to a column that is part of a composite key can have far-reaching consequences, affecting all foreign key relationships that reference it. Such changes carry risks and may require careful planning to avoid data integrity issues in Types of Joins in SQL Server. Additionally, composite keys can reduce the clarity of database schemas. When tables include large keys made up of several columns, visualizing and understanding schema diagrams can become more difficult for developers and database administrators. From a storage perspective, composite keys increase the amount of data stored, especially in large tables with millions of rows, because every key column consumes space in indexes and foreign key references. Another practical issue arises when working with Object-Relational Mapping (ORM) tools like Hibernate or Entity Framework, which often have limited or complicated support for composite keys. This can lead to development challenges and require extra workarounds. Finally, having multiple columns as a key increases the potential for data entry errors. Without strict validation and controls, inconsistencies or mistakes can creep into one of the key fields, potentially compromising data integrity. Despite these challenges, composite keys remain valuable, but it is important to weigh their benefits against these considerations when designing your database schema.
Want to Learn About Database? Explore Our Database Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
Composite keys play a foundational role in relational database design by providing a robust mechanism to enforce multi-column uniqueness and maintain meaningful relationships within complex data models. Although they add a level of complexity to schema design and query operations, the trade-offs are often worthwhile, especially in normalized databases and transactional systems where data integrity is paramount. The decision to use composite keys versus surrogate keys largely depends on the specific business requirements and the nature of the data. Surrogate keys, such as auto-incrementing IDs, simplify identification but may lack real-world meaning, while composite keys reflect natural business rules by combining multiple fields to define uniqueness. For instance, in Database Training scenarios like a student enrolled in a course or a product stocked in a warehouse, a composite key is not just appropriate it is necessary to accurately represent the underlying relationships. Using composite keys helps prevent duplicate records and enforces constraints that align with organizational policies, thereby enhancing data quality. Moreover, understanding when, why, and how to implement composite keys enables developers and database architects to create schemas that are both logical and maintainable. Well-designed composite keys contribute to clearer data models that mirror real-world entities and processes, which is essential for scalability as the organization grows and evolves. Despite the challenges in querying and managing composite keys, their ability to accurately capture complex uniqueness rules makes them an indispensable tool in relational database design. Mastery of composite keys, alongside other database design principles, equips professionals to build systems that are reliable, efficient, and aligned with business goals.


