
IBM BigFix is a powerful endpoint management solution designed to simplify and secure IT operations across large-scale enterprises. It provides comprehensive capabilities for patch management, software distribution, remote control, and compliance monitoring. By centrally managing endpoints such as desktops, laptops, servers, and mobile devices, BigFix helps organizations reduce complexity, improve security posture, and ensure regulatory compliance efficiently.
1. What Is Bigfix Exactly?
Ans:
IB Collaboration between IT architecture and security specialists is made possible by BigFix, an endpoint control and security platform. BigFix gathers software and hardware information to help IT inventory networked devices. To identify and fix security flaws, it is critical to comprehend what is connected to the UCSF network. BigFix is used at UCSF to register PCs and laptops connecting to the network.
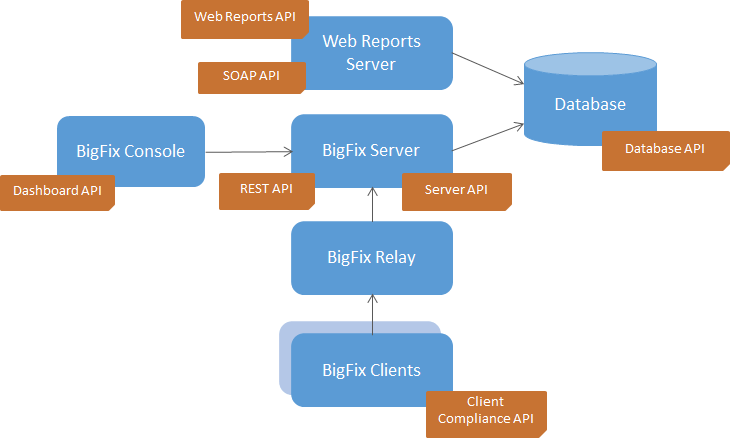
2. What locking configuration profile does BigFix use? Who is in charge of locking or unlocking a system?
Ans:
A locked system cannot execute any commands, including installing or repairing software. Only data-gathering actions are allowed, aside from changing client-side settings (such as updating the BigFix client). By default, the client and the Linux/Unix workspace servers are secured. At the moment, only a select group of IT experts known as the BigFix admins have the authority to freeze and unlock systems.
3. What risks does IBM BigFix pose, and does it affect existing programs?
Ans:
- The BigFix software won’t delete any apps or cause any computer damage.
- There is a small chance that BigFix is causing software conflicts, which could lead to a small issue.
- Remove the computers from the service from the database. Enter the BigFix console login.
- Use the instructions for “Removing Computers from the Database” to manually remove the machines.
4. What defines security patches? Will the computer restart after applying a patch?
Ans:
- Security patches, often known as regular software upgrades, are necessary to maintain the protection of the operating system and applications.
- BigFix can remotely apply updates that are necessary to keep your system secure.
- Clients may be asked to restart their computers to apply the fix.
- Restarting the machine without user consent will only happen in extreme circumstances (e.g., a significant security issue needing urgent response).
5. Why Is Bigfix Installation Needed On All Networked Desktops And Laptops At UCSF?
Ans:
Ensuring the security of UCSF’s data and computational resources requires insight into all linked devices. UCSF IT will receive a precise inventory of linked devices along with information on who owns them and how they are patched. To safeguard UCSF computer resources and data, insight into every device connected to the network is essential. BigFix gives UCSF IT a precise list of all the devices connected to the network, together with information about their owners and patch status.
6. What Can Be Expected Following BigFix Installation?
Ans:
While running in the background, the BigFix Application will communicate information about your computer’s initial state to the BigFix Server. If the system needs to be patched, you will be asked to authorize the process. Demands it. With minimal CPU usage, BigFix will run in the background while routinely interacting with the server to offer real-time system status information and to search for fresh jobs.
7. How can the Uncontended Asset Importer compare recent scans with previous ones?
Ans:
- They match if their Mac addresses are the same.
- They correspond if their hostnames are the same.
- If their IP addresses match, they match even if neither has a hostname or a Mac address.
- Lastly, the newly scanned object will be considered a new asset if it does not meet any of the previously listed requirements.
8. How do the client and scanner differ from each other in BigFix?
Ans:
| Feature | BigFix Client | BigFix Scanner |
|---|---|---|
| Purpose | Manages and executes endpoint tasks | Performs specific scanning tasks |
| Functionality | Applies patches, enforces policies, deploys software | Scans endpoints for inventory and security assessments |
| Installation | Installed on all endpoints to be managed | Typically installed on endpoints needing specific scans |
| Communication | Communicates regularly with the BigFix server | Sends scan results to the BigFix server |
9. How do tools and standards for protecting student data differ from those for faculty and staff?
Ans:
No, because the technologies are the same, they monitor UCSF’s security and risk status equally and effectively. Students, staff, and instructors are all subject to the same policies and procedures. When personal information is disclosed, confidentiality is affected. Pupils have faith in their teachers to share their data sensibly and with confidentiality. Instructors are in charge of maintaining the privacy of each student’s data and only disclosing it to those who need to know, like administrators, other teachers, and parents.
10. How Does System Performance Get Affected When BigFix Is Used On The Client’s Server?
Ans:
The CPU usage parameters have been adjusted by default to mitigate excessive consumption of the server’s CPU resources. Customers can expect BigFix software to utilize only 2% of the CPU when operating on a single processor. For systems with multiple processors, the total CPU usage percentage of the BigFix agent is proportionally reduced. This adjustment ensures the software remains efficient while minimizing its impact on overall system performance.
11. How often should hard drive encryption be checked, and how should it be monitored?
Ans:
- As a best practice, reporting frequency should be increased from fortnightly to monthly to ensure that encryption standards are met.
- Thanks to BigFix Data Security and Encryption monitoring, the disk is safeguarded, which is crucial if it is compromised.
- The size and performance of your computer’s hard drive will determine how long it takes. The process lasted from twenty minutes to three hours during our testing.
12. How well does BigFix integrate with standard server procedures and activities?
Ans:
- BigFix is a popular system management tool that has a track record of not interfering with other service operations.
- Over the past few years, UCSF has needed help running BigFix on hundreds of thousands of machines. Before being distributed, BigFix tests every Fixlet message in its lab.
- Frequently, problems found during this testing procedure are fixed by adding additional “notes” to the Fixlet message.
13. Why Is The User’s Order of LMT Required?
Ans:
Defining an IBM authorization record for licensing, software membership, and technical support is advised, even if LMT is a free offering. A limit order is an order to purchase or sell stocks that has a restriction on the lowest price that can be received (sell limit) or the maximum price that can be paid (buy limit). Should the order be filled, it will only be at the limit price mentioned or a lower amount. But there’s no guarantee of execution.
14. When is it necessary to run the LMT/BFI server?
Ans:
The LMT/BFI servers must be operational at all times for consistent reporting and real-time data processing from terminals. For a sub-capacity license, IBM pricing mandates that a capacity can be run on every terminal once every 30 minutes. Going back five years, the BigFix server’s capacity is retained. Days. As a result, the system should be turned off for at most five days.
15. What rules prevent illegal use of BigFix by internal and external users?
Ans:
- Administrator rights are only granted to qualified IT staff members who follow industry best practices, which include only gaining access to the information required to perform their jobs.
- The BigFix system is constantly observed and is physically housed in the data center. Patches are often applied to keep the system secure.
16. What Will IT Do With The BigFix Server Owned by the Client?
Ans:
- BigFix is going to gather data regarding the user’s system configuration, which includes the RAM, CPU, and operating system.
- BigFix only collects personal data after speaking to the owner of the system.
- IT won’t ever upgrade software or modify files. IT, however, has the power to remove servers from the networks or apply updates if the systems analyst does not respond promptly.
17. What Is the Maintenance Service? Why Do “In Progress” Notifications Appear?
Ans:
The Enterprise Manager system’s maintenance service needs to be set up to support file uploads. The server’s file status is instantly updated whenever a server function is configured. The user might have to restart the Console to see the modifications. We improve the infrastructure in our data centers to support your instance when we do a Salesforce Instance Refresh or Migration. Your instance will relocate to a new data center and have a new name after this maintenance.
18. How Can a Creation be Created? Will the File Be Imported?
Ans:
From the Media Library dashboard, accessible via the Manage section in the navigation tree under the Images link, users can manually input details such as the disc size, architectural design, and operating system. The disc size specified should reflect the uncompressed size of the WIM file. Typically, this uncompressed size is nearly double the size of the original WIM file. This ensures that the media library accurately represents the storage requirements for deploying the WIM file.
19. How should a user choose the best configuration management type for their environment?
Ans:
For guidance on designing their installation, they can refer to the IBM Terminal Controller’s Wireless Remote Installation Instructions. Microsoft Intune’s Microsoft Configuration Manager
- Infrastructure Management of Progress Chef.
- Puppet Company.
- Red Hat Automation Platform for Ansible.
- Database for ServiceNow Configuration Management.
- HashiCorp’s Terraform.
- Aria Automation for VMware.
20. How Can a User Recover a Deleted Software Fragment?
Ans:
Users may see that items have been removed when they visit the Audit Log in Catalog Tools on the Product Catalogue tab main window. The function “Display Deleted” is accessible at every tier of the Catalog hierarchy. Click that button to view lost items and then retrieve them. Utilise ReclaiMe or other generic file recovery software. Keep in mind that TRIM may make it difficult to retrieve erased data from an SSD, but that’s another topic! When it comes to recovering fragmented files, other file systems like Linux EXT3/4 or FAT file systems are less lenient.
21. Does the user have to import the software again every time it is modified?
Ans:
Click “Start Now” after selecting Import Options under Data file in the Settings menu. Users must reset Import Segments to adjust catalogs, which can be done through the Import Options tab of the Control Panel. During import, the module name is checked in ‘sys.modules’. If found, the import completes; otherwise, a ‘ModuleNotFoundError’ occurs, and Python will continue searching if the module name is absent.
22. What are some ways that IBM BigFix can be integrated with other IT tools and systems?
Ans:
- With the help of pre-built connectors, web services, and APIs, IBM BigFix provides comprehensive integration capabilities for smooth interaction with ticketing systems, SIEM systems, and other systems.
- These linkages improve overall efficiency and effectiveness by facilitating centralized administration, orchestrating IT activities, and fostering better cooperation between IT teams.
23. How Do ITAM and SAM Differ From One Another?
Ans:
Information Technology Asset Management, or ITAM for short, is the process of keeping track of all resources related to information technology, such as digital goods, hardware, software, network infrastructure, and communication. SAM, on the other hand, stands for Software Asset Management, an approach that primarily focuses on the IT Asset Management category of “software” assets.
24. What Kinds of User Accounts Are Appropriate To Create Before Deployment?
Ans:
- Every user should ideally have a single domain user profile with the necessary permissions.
- Permission to install the software on the SUA server.
- Permission to use the database server and create databases there.
- Permission to communicate with the IBM Terminal Manager server and retrieve its instructions.
25. Can Two Management Connectors Be Installed On A Single Relay?
Ans:
The user may have two different management connectors on the same channel. However, they shouldn’t be identical. For example, a relay can support two iOS connectors but not two Lotus Traveler connectors. An electrically powered switch is called a relay. It consists of a set of working contact terminals and a set of input terminals for one or more control signals. The switch may have any number of contacts in any combination of make, break, and other contact forms.
26. Why might an installed app’s name appear as unintelligible letters on an Android device?
Ans:
The Android Client’s code page for the TEM Deployment will remain empty even after enrollment. English is the IANA client configuration by default for Android phones unless it is changed. The ability to turn icon labels on or off varies based on the kind of Home launcher. If you can’t find it, try long pressing on a blank area of the home screen. If that doesn’t work, see if you have Launcher settings choices.
27. How Does the TEM Console Differentiate Between Regular and Proxy Servers?
Ans:
- A full TEM agent, including all common inspections and replies, is installed on standard computers.
- Proxy servers employ APIs to retrieve hardware information and feed it into the terminal as a computer instead of executing a full TEM application.
- The user receives a response straight from the web server that contains the website’s data.
- The role of a proxy server is to mediate between the user and the web server. To hide the user’s true address from web servers, proxy servers employ a new IP address on their behalf.
28. What is preventing the user from applying any ESXi patches?
Ans:
- Audit-only material is included in ESXi patches. Customers can use the VMware Update Client or download and install updates straight from the VMware website to fix issues with ESXI.
- Open the home view of vSphere Lifecycle Manager. Select Menu > Lifecycle Manager in the vSphere Client.
- Select the Updates tab. An overview of all updates is displayed to you in the vSphere Lifecycle Manager depot.
29. Which Kind Of Device Is Fit For The Management Extension?
Ans:
The CPU will definitely be the main limiting factor for medium—and large-sized installations. If the machine has four cores, it should be able to perform all management extension tasks. Like any other service mentioned in the Services app (services. msc), the Microsoft Intune Management Extension is a device service. Following a device reset, this service may restart and search for any assigned PowerShell scripts with the Intune service.
30. Why Do Some Fields In Reports From The TEM Agent Differ From Reports From Proxied VMs?
Ans:
Data from the VMware Interfaces is extracted and converted to TEM properties via the vCenter plug-in. However, since many of these factors are set up, they occasionally deviate from what is supplied by the TEM Agent due to changes made by the user. For inline editing to be available, the field needs to be added to the layout allocated to the record type that is filtered in the list view. To enable inline editing, the user must check the Marketing User box on the User detail page.
31. What is the purpose of IBM BigFix?
Ans:
- IBM BigFix product suite, enterprises can view and manage both physical and virtual endpoints using a single infrastructure, a single console, and a single kind of agent.
- This offers a quick and simple solution for compliance, endpoint, and security management.BigFix is the outcome of IBM acquiring BigFix, Inc., which allowed them to provide more security and compliance services.
- The software lets businesses see and control both physical and virtual endpoints and offers endpoint and security management in a single package.
32. Describe the BigFix console.
Ans:
- BigFix is a useful tool that helps defend against specific cyberattacks and safeguards endpoints in advance of an assault.
- It boosts defenses against cyberattacks and automates the process. It preserves software audit readiness, reduces the chance of non-compliance, and maximizes software expenditure.
- With only a few mouse clicks, authorized staff may utilize the BigFix console’s revolutionary Fixlet technology to discover compromised or abnormal machines on your network and then fix them across any subset of the network.
33. How does IBM BigFix vary from conventional endpoint management solutions?
Ans:
An endpoint management platform called IBM BigFix offers automation, control, and real-time visibility for managing endpoints. BigFix is different from typical solutions in that it stresses real-time response and automation for security, compliance, and patching. It also provides scalability, enabling the control of hundreds of thousands of endpoints from a single console.
34. How is the BigFix client operated?
Ans:
The BigFix agent examines the registry, system language, and other key elements to determine whether patches are installed correctly or are corrupt. Console Operators can address issues by inserting Notes® into Fixlet® descriptions, providing detailed information and context. Additionally, a variety of tools such as wizards, reports, and dashboards are available for managing Fixlets, offering comprehensive support for maintaining system integrity and security.
35. How does IBM BigFix handle network bandwidth optimization during patch deployments?
Ans:
- During patching, IBM BigFix uses various techniques to maximize network traffic.
- During patch deployments, IBM BigFix uses a variety of techniques, including peer-to-peer distribution, bandwidth throttling, and download caching, to maximize network capacity.
- These systems guarantee effective patch delivery during extensive deployments while reducing the strain on network resources.
36. What are the advantages of IBM BigFix for endpoint management over other solutions?
Ans:
- For endpoint management, IBM BigFix provides unmatched scalability, automation, real-time visibility, and extensive security capabilities.
- Its capacity to manage various endpoint environments, guarantee regulatory compliance, and offer practical insights for efficient security operations set it apart.
37. How can BigFix be used to deliver a patch?
Ans:
- Select “All Fixlets and Tasks” in the navigation tree under “All Patch Management.”
- Refine the results by choosing the relevant site, such as “Windows Patches (English).”
- Browse the list panel for available Fixlet messages.
- Click on a Fixlet message to select it from the displayed options.
- Proceed with the deployment as needed based on the selected Fixlet.
38. What benefits does IBM BigFix provide in this regard, and how does it manage software distribution?
Ans:
IBM BigFix makes it easier to distribute software by Software distribution is made easier by IBM BigFix, which packages apps into Fixlets that are efficiently and automatically deployed to endpoints. Its benefits include support for a variety of settings and applications, dependable and consistent software deployment, and real-time visibility into deployment status and compliance.
39. What is a Fixlet in BigFix?
Ans:
The BigFix platform revolves around fixlets and tasks, the core elements for managing and automating IT operations. Fixlets are predefined actions or scripts designed to address specific issues or perform updates, while tasks are broader activities that can include multiple actions. The License Metric Tool, a component of BigFix, utilizes these fixlets and tasks to execute necessary operations on designated computers.
40. How can IBM BigFix help with threat mitigation and incident response?
Ans:
- IBM BigFix is essential to incident response because it offers real-time visibility into endpoint security posture and automates threat remediation steps.
- It lessens the effect of attacks and minimizes downtime by facilitating the quick identification, containment, and remediation of security problems.
41. How does IBM BigFix handle diverse endpoint environments with different operating systems?
Ans:
- From a single management console, IBM BigFix supports diverse endpoint environments, such as Windows, macOS, Linux, and Unix.
- It ensures uniformity in security policies, patch management, and configuration enforcement by providing consistent management capabilities across a range of operating systems.
42. What factors need to be taken into account by enterprises while preparing to implement IBM BigFix?
Ans:
- Organizations should consider infrastructure considerations, scalability requirements, network bandwidth, endpoint variety, and interaction with current systems.
- In order to achieve organizational goals, efficient planning guarantees a seamless deployment process, peak performance, and successful application of IBM BigFix capabilities.
43. What is the function of action scripts and Fixlets in BigFix?
Ans:
IBM BigFix Fixlets are actionable notifications that specify what has to be done on endpoints in terms of tasks or instructions, including applying patches or running commands. Fixlets are accompanied by action scripts that instruct users on how to perform the defined actions on target endpoints. This allows for automation and uniform policy enforcement.
44. How do the various IBM BigFix deployment choices differ from one another?
Ans:
IBM BigFix offers on-premises and cloud-based deployment options for various organizational needs. Cloud installations provide scalability, flexibility, and reduced administrative overhead, making it easier to adapt to changing requirements and scale resources as needed. On the other hand, on-premises deployments offer complete control over infrastructure and data, which can be crucial for organizations with stringent security or compliance requirements.
45. What factors ought to be taken into account while organizing a BigFix deployment?
Ans:
- Three components must be installed for BigFix Inventory to be fully deployed on Windows: an MS SQL database, the BigFix platform, and the BigFix Inventory server.
- Additionally, any computer from which you wish to gather software inventory data needs to have a BigFix client installed.
- It is also essential to ensure that network connectivity between these components is properly configured.
46. What is an architect for BigFix?
Ans:
- BigFix is a family of technologies that enables enterprises to view and manage both physical and virtual endpoints using a single infrastructure, a single console, and a single kind of agent.
- It offers a quick and simple solution for compliance, endpoint, and security management—a bugfix system.
- Additionally, BigFix provides real-time visibility and control over endpoints, ensuring rapid response to emerging threats and compliance issues.
47. What components make up BigFix?
Ans:
BigFix is a useful tool that helps defend against specific cyberattacks and safeguards endpoints in advance of an assault. Boost defenses against cyberattacks and automate the process. Preserve software audit readiness, reduce the chance of non-compliance, and maximize software expenditure. You need to install BigFix’s three main components. The server, Console, and clients. A database that houses all of the information obtained from the clients is also necessary for the application.
48. What are the benefits of endpoint management using Fixlets in IBM BigFix?
Ans:
- Fixlets in IBM BigFix offer instructions and actionable intelligence for managing endpoints, including patch deployment, configuration, and script execution.
- They facilitate real-time responses to security risks and compliance needs while enabling automation, consistency, and scalability in endpoint management operations.
49. How do the BigFix client and scanner differ from one another?
Ans:
All IBM applications created on top of the BigFix infrastructure use the BigFix client to perform various operations on terminals. In contrast, LMT/BFI uses the scanner as a stand-alone component. It collects information about the hardware and software that are installed on the computers that make up your infrastructure. The data can be imported into the LMT/BFI server after being transferred to the BigFix server.
50. Which aspects of IBM BigFix’s vulnerability management capabilities are most important?
Ans:
IBM BigFix excels in vulnerability management by focusing on real-time vulnerability scanning, automated patch deployment, and detailed reporting on vulnerabilities and their remediation. It offers insights into the security status of each endpoint and integrates threat intelligence for current vulnerability data. The platform also prioritizes vulnerabilities based on risk and impact, ensuring that remediation efforts are effectively directed.
51. How are licensing compliance and software asset management handled by IBM BigFix?
Ans:
- IBM BigFix offers visibility into software installs, usage, and license entitlements across endpoints, which helps with software asset management.
- It contributes to license compliance by identifying unauthorized software installations, maximizing software utilization, and assisting with licensing reconciliation and compliance reporting.
52. What Kinds of User Accounts Are Appropriate to Create for Deployment?
Ans:
- Every user should ideally have a single domain user profile with the necessary permissions.
- Permission to install the software on the SUA server.
- Permission to use the database server and create databases there.
- Permission to communicate with the IBM Terminal Manager server and retrieve its instructions.
53. What makes BigFix necessary?
Ans:
Every company must be protected against security risks. Improving the security of endpoints, portholes, and vulnerability points—any of which, if left unchecked, may result in a major network catastrophe—is one of the finest methods to safeguard a commercial firm. IBM BigFix is the best approach for managing vital company assets and securing endpoints.
54. How does IBM BigFix help businesses make sure they comply with regulations?
Ans:
- By constantly checking endpoints for compliance with corporate policies and regulatory standards, IBM BigFix helps ensure regulatory compliance.
- In order to expedite compliance efforts, it offers comprehensive reporting for audit purposes, automated enforcement of compliance rules, and integration with compliance frameworks.
55. Why Does Ucsf Demand That Bigfix Be Installed On Every Desktop And Laptop Connected To The Network?
Ans:
To safeguard UCSF computer resources and data, insight into every device connected to the network is essential. This will give UCSF IT a precise list of all the devices on the network, together with information on who owns them, their patch status, and what they are made of. Every other device on the UCSF network is in danger of unknown or unidentified devices, and they will be susceptible to deletion from the UCSF network.
56. What Comes With Bigfix Installation?
Ans:
The BigFix icon will appear on the Menu Bar (Mac OS X) or System Tray (Windows). The BigFix Client, which operates in the background, will report your system’s initial condition to the BigFix Server. If the System Requires a Patching Task, you will be prompted to accept it. The patching task window will remain in the foreground, and you won’t be able to dismiss it if you postpone the work for an extended period.
57. How is unauthorized access to the BigFix system prevented for both external and internal users?
Ans:
Administrator powers are restricted to qualified IT workers who adhere to industry best practices for system administration, which include granting them access to the minimal amount of data necessary to do their duties, in line with the University of California Electronic Communication Policy. The BigFix system is constantly being monitored and has limited physical access to the data center. System integrity is ensured by applying patches regularly.
58. How Do The Bigfix Client And Scanner Differ From One Another?
Ans:
- All IBM products built on the BigFix platform share the BigFix client, which is used to carry out various functions on the endpoints.
- A client is a tool used to install scanners on computers and manage them via fillets.
- It gives information on a set of computer attributes, such as the hostname or IP address.
- On the other hand, the scanner is a separate part that LMT/BFI uses. It gathers data regarding the software and hardware that are set up on the computers in your network.
59. What Will Bigfix Be Doing on My Server?
Ans:
- BigFix will gather information about the system configuration, including the operating system, CPU, RAM, hard drive capacity, patch status, and the server’s local account list.
- It will not gather personal information, including browser history or user data saved on the server.
- IT must first speak with the system owner to apply fixes or change files.
60. How does IBM BigFix handle scalability, and what needs to be considered for large deployments?
Ans:
- Because of its distributed architecture, IBM BigFix is extremely scalable, allowing it to manage hundreds of thousands of endpoints from a single console.
- Large installations need to consider appropriate infrastructure sizing, optimized server configurations, and the deployment of relay infrastructure for efficient endpoint traffic management.
61. How does IBM BigFix provide data safety, and what are its security features?
Ans:
- Strong security features like role-based access control, encrypted data in transit and at rest, and secure communication protocols are all used by IBM BigFix.
- By following industry standards and best practices, keeping an eye out for security risks and vulnerabilities, and offering audit trails for accountability, it guarantees data protection and integrity.
62. What are the typical BigFix environment’s core components?
Ans:
The BigFix server, BigFix console, and BigFix clients are the key parts of a typical BigFix environment. The BigFix server is in charge of overseeing the BigFix ecosystem and providing clients with material and updates. Administrators use the BigFix console to deliver updates and manage the environment. Installed on the computers that require management, the BigFix clients fetch content and updates from the BigFix server.
63. How do you maintain server compliance in a large, dispersed company setting?
Ans:
In a big distributed company setting, several important techniques ensure that servers maintain compliance. First and foremost, you must establish a compliance policy that is understandable and accepted by all parties. Second, all of the servers in the environment need to be tracked and monitored for compliance. Lastly, you must possess a technique to enforce compliance, including reviewing compliance reports by hand or automating the process.
64. What is the difference between an update and a patch in the context of BigFix?
Ans:
A patch is a specific type of modification applied to a software program’s code to resolve a bug or security flaw. It typically targets fixing issues or vulnerabilities identified after the software’s release. In contrast, an update involves broader modifications to the software’s code aimed at adding new features, improving performance, or enhancing existing functionalities. Updates are generally larger in scope compared to patches and may include changes to user interfaces, additional functionalities, or optimizations to the software’s core operations.
65. Can BigFix be used to build custom reports? If so, how?
Ans:
“Maintenance windows” are a notion used by BigFix that refers to times when servers can be pulled offline for patching or maintenance. BigFix allows for the scheduling of maintenance windows in advance, and it will automatically take servers offline and restart them as necessary. This guarantees that servers are always available when needed and are only taken offline when it is convenient.
66. How does IBM BigFix go above and beyond patch management to support endpoint security?
Ans:
- IBM BigFix provides complete endpoint security through automated security policy enforcement, continuous monitoring, and real-time visibility.
- It goes beyond patch management to efficiently handle security incidents, enforce configuration standards, and identify and fix security flaws.
- In IBM BigFix, relevance language is essential for dynamically assessing endpoint circumstances and identifying necessary actions (like patching or configuration modifications).
67. What are the details of IBM BigFix’s involvement in vulnerability management and repair?
Ans:
- IBM BigFix plays a critical role in vulnerability management by locating, ranking, and fixing security flaws on various endpoints.
- It provides effective vulnerability remediation through patch distribution and configuration modifications, automated vulnerability evaluation, and prioritization depending on risk levels.
- Effective endpoint management is aided by its ability to precisely target endpoints, improve automation capabilities, and facilitate sophisticated decision-making based on real-time data.
68. Describe the procedure engaged in expanding BigFix with new devices.
Ans:
Adding new devices to BigFix involves several key procedures. First, the device must be identified, and its basic data must be collected, including its IP address, operating system, and any relevant hardware specifications. Next, a device record must be created in the BigFix console. This involves logging into the BigFix management interface and manually or automatically adding the new device to the system. Finally, the BigFix agent must be installed on the device.
69. How does BigFix determine computer relevance?
Ans:
BigFix uses a variety of variables to determine the relevance of computers within its network management framework. These variables include the operating system (OS), which helps identify the platform and any specific requirements or configurations needed; the existence of specific software, which allows for the detection of installed applications and their versions to ensure they are up-to-date and meet compliance standards; and the IP address of the computer, which aids in network segmentation and location-based management.
70. How should one go about using BigFix to automate software updates?
Ans:
- There are several methods for automating software upgrades with BigFix; however, the most popular and widely utilized is the BigFix Update Management tool, which is the recommended approach.
- This powerful function allows you to set up a schedule for software updates, ensuring that updates are performed at times that are convenient for your organization.
- Additionally, it offers the flexibility to update programs when specific conditions are met, such as when a device is idle or during off-peak hours.
71. What kinds of operations can be carried out using BigFix’s run script action?
Ans:
The run script action enables the execution of a variety of scripts, including but not limited to PowerShell, VBScript, and JavaScript. This action allows for executing commands that are typically run at a command prompt or within other environments. This capability provides flexibility and versatility, enabling the automation of tasks, system administration, and integration with other applications or processes.
72. When generating a new file in BigFix, which deployment processes should be carried out first?
Ans:
The following is the suggested sequence of deployment procedures for establishing a new fillet in BigFix.
- Make a fillet plan.
- Make the fillet
- Check the file.
- Give the fillet out.
- Keep an eye on the fillet
73. How can the version of the BigFix client installed on a computer be determined?
Ans:
- Using the BigFix client itself is the most effective technique to find out which version of the BigFix client is installed on a machine.
- A built-in command is available to retrieve the running client’s version number.
- Open the BigFix client and select the “Help” option to accomplish this.
- Next, choose the “About BigFix” menu item. This will cause a window to pop up and show the client’s version number.
74. How can a specific query’s viability be determined without running it on a live system?
Ans:
- Queries can be tested using the BigFix console before being executed on an actual system.
- Choose the “Query” tab and type the query you wish to test into the “Query” field to accomplish this.
- Lastly, press the “Test” button. After that, the query’s results will be displayed in the Console without the need to run it on a real machine.
75. How does BigFix manage the availability of servers during patching or maintenance?
Ans:
BigFix refers to “maintenance windows” as intervals of time when servers may be taken offline for patching or maintenance. BigFix allows for the scheduling of maintenance windows in advance, and it will automatically take servers offline and restart them as necessary. This guarantees that servers are always available when needed and are only taken offline when it is convenient. Website. Installing and configuring the BigFix client on the device is required in order to connect it to the BigFix server.
76. How does one go about adding additional devices to BigFix?
Ans:
- Adding new devices to BigFix involves several procedures.
- First, the device must be identified, and you must collect its basic data, including its IP address.
- The device record must then be created in the device’s BigFix console, and the BigFix agent must then be installed on the device.
77. Which analytics and reporting tools are included in IBM BigFix?
Ans:
IBM BigFix offers analytics and reporting tools to enhance visibility into endpoint management and security. Features include customizable dashboards for real-time monitoring, comprehensive patch compliance and vulnerability reports, and historical data analysis. Users can generate pre-built and custom reports based on specific needs and export them in various formats, aiding in performance tracking and decision-making.
78. Which two categories of significance are there?
Ans:
Two Sorts of Relevance and Tie-breaks | Ethical Theory and In more formal terms, let us reintroduce the two forms of relevance: Global Relevance: If a claim, X, is sufficiently strong in comparison to the strongest claim it opposes, then it is considered globally relevant. Local Relevance: If a claim (X) is sufficiently strong in comparison to a claim (Y), then X is Locally Relevant to Y.
79. How can a big distributed company environment ensure that servers maintain compliance?
Ans:
In a big distributed company setting, several important techniques ensure that servers maintain compliance. First and foremost, you must establish a compliance policy that is understandable and accepted by all parties. Second, all of the servers in the environment need to be tracked and monitored for compliance. Last but not least, you need a mechanism to enforce compliance, like automated or human evaluation of compliance reports.
80. Which techniques does IBM BigFix employ to identify and address security threats?
Ans:
- IBM BigFix uses several techniques to identify and mitigate security threats, such as real-time vulnerability scanning, integration with threat intelligence, and automated patch management.
- It continuously monitors endpoints for vulnerabilities and applies threat intelligence to stay updated on new risks.
- Automated responses and remediation are implemented based on predefined policies and threat levels, complemented by detailed reporting and alerts for quick issue resolution.
81. What does IBM BigFix have to offer?
Ans:
- BigFix is a useful tool that helps defend against specific cyberattacks and safeguards endpoints in advance of an assault.
- It boosts defenses against cyberattacks and automates the process. Preserve software audit readiness, reduce the chance of non-compliance, and maximize software expenditure.
- Additionally, BigFix provides real-time visibility and control over endpoints, enhancing overall security management.
82. In the context of BigFix, what distinguishes an update from a patch?
Ans:
A patch is a modification to a software program’s code that addresses a bug or fixes a security flaw. In contrast, an update is a modification to a software program’s code that adds new capabilities or enhances already existing functionality. The primary distinction between a Patch Management tool and Windows Update lies in their respective functions and purposes. Windows Update is a feature of the Windows operating system that automatically updates Windows machines with the most recent security updates and patches straight from Microsoft.
83. Which BigFix troubleshooting tools are frequently used?
Ans:
- The BigFix client log: This log, which is located in the installation directory of the BigFix client, includes details on every action the client has made.
- The BigFix server log: This log, located in the BigFix server’s installation directory, includes details on every action the server has taken.
- The BigFix console is a web-based interface that allows you to run troubleshooting commands and monitor information about the BigFix system’s status.
84. What is the remote control target for IBM BigFix?
Ans:
During a remote control session, the target user has the capability to communicate with the controller user through the interface provided by the IBM® BigFix® Remote Control Target software. This communication interface is conveniently displayed in the target system’s taskbar, allowing the target user to easily access and use it for interaction during the session.
85. What distinguishes BigFix inventory from ILMT inventory?
Ans:
When IBM software contractual obligations necessitate sub-capacity license reporting, ILMT (IBM License Metric Tool) is typically implemented. ILMT is primarily designed for IBM software. In contrast, BigFix Inventory goes beyond ILMT by maintaining up-to-date catalogs that encompass numerous software vendors besides IBM, ensuring comprehensive license compliance across various software products.
86. Which protocol is used by the BigFix client?
Ans:
The BigFix Client utilizes the ICMP protocol, similar to how tracert works, to locate the nearest BigFix Relay. Initially, each BigFix Client sends multiple rounds of ICMP packets to potential BigFix Relays, increasing the TTL (Time-to-Live) with each round until a response is received from a Relay. This iterative process ensures efficient communication establishment between the Client and the nearest operational Relay.
87. Who Can Access The Bigfix System Administrator Controls?
Ans:
BigFix administrator controls are accessible to designated UCSF IT Staff members. Every activity made within BigFix and every access to it is recorded and routinely audited. The patching process will end with a system reboot. Rebooting the system several times could be required if patching the system is far behind schedule. BigFix is going to operate in the background.
88. What qualifies as relevance?
Ans:
- The concept of relevance pertains to the relationship between two topics in a manner that makes it advantageous to consider the second topic when examining the first.
- This principle has been extensively studied across various disciplines, such as cognitive sciences, logic, and library and information science.
- Researchers in these fields examine how relevance affects decision-making, problem-solving, information retrieval, and communication, seeking to understand the cognitive mechanisms for identifying pertinent information in different contexts.
89. Which four categories of significance exist?
Ans:
The various categories of research relevance include:
- Academic significance.
- Social significance.
- Relevance in practice.
- Scientific significance.
90. What advantages does IBM BigFix offer regarding real-time data collection and monitoring?
Ans:
IBM BigFix provides significant real-time data collection and monitoring advantages, including continuous visibility into endpoint status and security. It offers up-to-date information on system configurations, vulnerabilities, and compliance, allowing for swift issue identification and resolution. The platform supports detailed monitoring of software installations, patching activities, and system performance, with real-time alerts and reporting to ensure effective IT management.



