
If you are preparing for FortiManager Interview, then you are at the right place. Today, we will cover some mostly asked FortiManager Interview Questions, which will boost your confidence. FortiManager provides automation-driven centralized management of your Fortinet devices from a single console. Therefore, FortiManager professionals need to encounter interview questions on FortiManager for different enterprise FortiManager job roles. The following discussion offers an overview of different categories of interview questions related to FortiManager to help aspiring enterprise FortiManager Professionals.
1. What is FortiManager, and how does it fit into Fortinet’s security ecosystem?
Ans:
FortiManager is Fortinet’s centralized security management solution, serving as the nerve center for configuring and overseeing Fortinet devices. It plays a crucial role in unifying the management of security policies, providing administrators with a consolidated platform for orchestrating and automating security across the network. By acting as a central hub, FortiManager enhances the efficiency of security operations, ensuring a cohesive and responsive security infrastructure within the broader Fortinet ecosystem.
2. How does FortiManager streamline security policy management for distributed networks?
Ans:
FortiManager excels in simplifying security policy management for distributed networks. Its centralized approach allows administrators to create, modify, and deploy security policies seamlessly across multiple Fortinet devices. This not only ensures consistency in policy enforcement but also significantly reduces the complexity of managing security configurations in distributed environments. FortiManager’s ability to streamline policy management enhances operational efficiency, making it an indispensable tool for organizations with expansive and geographically dispersed networks.
3. How does FortiManager support the management of intrusion prevention systems (IPS)?
Ans:
- Centralized IPS policy management
- Uniform IPS settings across devices
- Efficient IPS policy updates
- Enhanced threat detection and prevention
- Streamlined IPS configuration changes
- Real-time monitoring of IPS activities
4. In what ways does FortiManager address scalability for large enterprise environments?
Ans:
FortiManager is engineered with scalability in mind, making it a robust solution for large enterprise environments. Its architecture is designed to handle a high volume of Fortinet devices, providing a scalable platform for organizations with extensive and complex network infrastructures. As an organization grows, FortiManager seamlessly adapts to accommodate an increasing number of devices, ensuring that it remains a reliable and effective security management solution for enterprises of varying sizes.
5. How does FortiManager contribute to the automation of security workflows and tasks?
Ans:
FortiManager plays a pivotal role in automating security workflows and tasks and streamlining operational processes for administrators. It offers automation features that range from policy deployment to routine updates, reducing manual effort and minimizing the risk of human errors. This automation not only accelerates response times to security events but also allows administrators to focus on more strategic aspects of security management, leading to increased efficiency and responsiveness in handling security tasks.
6. What role does FortiManager play in ensuring compliance with security policies and regulations?
Ans:
FortiManager is a cornerstone in ensuring compliance with security policies and regulations. By providing centralized control over security configurations, it facilitates the creation and enforcement of policies that align with industry regulations and internal security standards. Its comprehensive auditing and reporting capabilities allow organizations to demonstrate adherence to compliance requirements during audits. FortiManager thus becomes an indispensable tool for organizations navigating complex regulatory landscapes, ensuring that their security practices remain in line with established standards.
7. What features does FortiManager offer for analyzing and optimizing firewall rule sets?
Ans:
- The rule set analysis tools
- Identification of redundant rules
- Streamlined rule configurations
- Enhanced firewall performance
- Minimized rule conflicts
- Improved overall network security
8. How does FortiManager simplify device lifecycle management for Fortinet devices?
Ans:
FortiManager simplifies device lifecycle management by serving as a centralized platform for provisioning, monitoring, and updating Fortinet devices. It streamlines the onboarding process for new devices, ensuring consistent configurations. Throughout the device lifecycle, FortiManager facilitates monitoring, allowing administrators to track device performance and health. Additionally, it plays a crucial role in ensuring that firmware updates and security patches are applied promptly, contributing to the longevity and reliability of Fortinet devices.
9. Explain the core functionalities of FortiManager in managing FortiGate firewalls.
Ans:
FortiManager is indispensable in managing FortiGate firewalls, providing a centralized platform for configuring, monitoring, and orchestrating firewall policies. Administrators can efficiently create and modify firewall rules, ensuring consistent policy enforcement across FortiGate devices. Its role extends to policy versioning, simplifying rollback procedures, and allowing administrators to track changes over time. FortiManager’s capabilities in managing FortiGate firewalls contribute to maintaining a secure and well-coordinated firewall infrastructure.
10. What features are offered for managing web application firewall (WAF) policies?
Ans:
- Centralized WAF policy management
- Unified security policies for web applications
- Efficient WAF policy deployment
- Granular control over WAF configurations
- Simplified WAF rule management
- Real-time monitoring of web application security
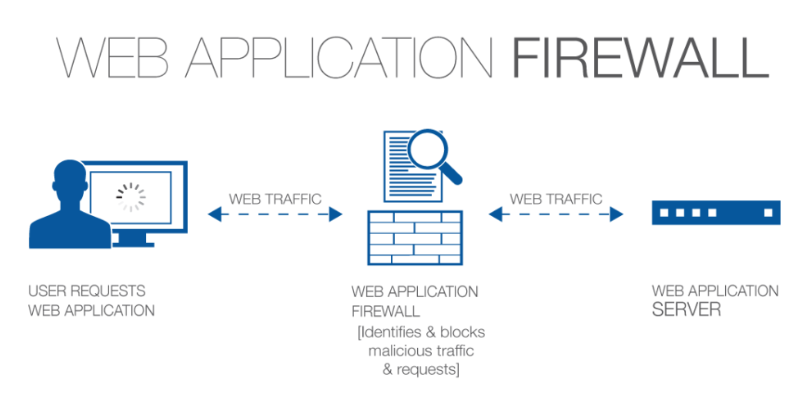
11. How does FortiManager enhance network visibility and monitoring capabilities?
Ans:
FortiManager enhances network visibility by consolidating data from Fortinet devices and presenting it through a centralized interface. Administrators gain comprehensive insights into network activities, security events, and device performance in real time. FortiManager’s reporting and analytics capabilities provide detailed reports, allowing administrators to make informed decisions based on the analysis of historical and real-time data.
12. What automation features does FortiManager provide for deploying security policies?
Ans:
FortiManager offers a suite of features for automating the deployment of security policies across Fortinet devices. Through its intuitive interface, administrators can create and modify security policies, and FortiManager ensures seamless deployment to multiple devices simultaneously. Policy changes are orchestrated efficiently, reducing the time and effort required for manual configuration.
13. How does FortiManager manage FortiSwitch devices efficiently?
Ans:
FortiManager contributes to the efficient management of FortiSwitch devices by providing centralized control over configuration and monitoring. Administrators can seamlessly manage switch configurations, ensuring optimal performance and adherence to security policies. FortiManager’s role extends to the orchestration of switch settings, allowing for consistent policies and efficient management of FortiSwitch devices across the network.
14. What role does FortiManager play in VPN provisioning and management?
Ans:
FortiManager plays a key role in VPN provisioning and management by centralizing the configuration and monitoring of VPN connections. It simplifies the deployment of VPN policies, ensuring consistent settings across devices. FortiManager provides a unified view of VPN activities, facilitating effective monitoring and troubleshooting. Its role in VPN management contributes to secure and reliable remote access capabilities within the network.
15. How does FortiManager aid in updating firmware and enhancing security?
Ans:
FortiManager enhances network security by centralizing the management of firmware and security updates for Fortinet devices. It ensures that devices are promptly updated with the latest patches and security definitions, reducing vulnerabilities and enhancing the overall resilience of the network against emerging threats. FortiManager’s role in facilitating timely updates contributes to maintaining a robust security posture.
16. How does FortiManager support role-based access control for administrators?
Ans:
FortiManager supports role-based access control (RBAC) by allowing administrators to be assigned specific roles with predefined permissions. This granular access control ensures that individuals have access only to the functionalities necessary for their responsibilities. By implementing RBAC, FortiManager enhances security, minimizes the risk of unauthorized changes, and provides a structured approach to administrative access.
17. In what ways do they contribute to network segmentation and policy enforcement?
Ans:
- Efficient network segmentation tools
- Centralized policy enforcement
- Streamlined policy updates
- Minimized lateral movement risks
- Enhanced overall network security
- Consistent policy application across segments
18. How does FortiManager track security configuration changes?
Ans:
FortiManager aids organizations in maintaining audit trails by logging all configuration changes made to Fortinet devices. This comprehensive logging ensures transparency and accountability, allowing organizations to track modifications, conduct audits, and identify potential security risks. FortiManager’s role in generating detailed audit trails contributes to a robust and compliant security management process.
19. What role does FortiManager play in orchestrating and automating responses to security threats?
Ans:
- Centralized threat intelligence integration
- Automated threat response workflows
- Coordinated defense mechanisms
- Rapid quarantine actions
- Policy adjustments in real-time
- Proactive defense against emerging threats
20. How does FortiManager aid zero-touch provisioning for Fortinet devices?
Ans:
FortiManager supports zero-touch provisioning by automating the initial configuration of Fortinet devices. This capability enables devices to be deployed with minimal manual intervention, reducing deployment time and minimizing the likelihood of configuration errors. FortiManager’s support for zero-touch provisioning streamlines large-scale network deployments, ensuring a consistent and error-free configuration process.
21. How does FortiManager aid in network segmentation and policy enforcement?
Ans:
FortiManager plays a crucial role in contributing to effective network segmentation by allowing administrators to define and enforce security policies based on network segments. It ensures that policies are consistently applied, minimizing the risk of lateral movement for threats and enhancing overall network security. FortiManager’s role in policy enforcement contributes to creating a secure and segmented network architecture.
22. What role does FortiManager play in ensuring secure and efficient NAC policies?
Ans:
- Centralized NAC policy management
- Unified security policies for network access
- Streamlined NAC policy updates
- Granular control over access configurations
- Enhanced overall network security
- Real-time monitoring of NAC activities
23. How does FortiManager orchestrate security responses to threats?
Ans:
FortiManager plays a pivotal role in orchestrating and automating security responses to threats. It centralizes threat intelligence and enables automated responses, such as quarantine actions and policy adjustments. This orchestration ensures a rapid and coordinated defense against emerging security threats, enhancing the network’s ability to adapt and respond effectively to evolving risks.
24. How does FortiManager contribute to the management of SSL/TLS certificates within a network?
Ans:
FortiManager simplifies SSL/TLS certificate management by providing a centralized platform for configuring, monitoring, and updating certificates. It ensures that certificates are consistently managed, reducing the risk of expired or misconfigured certificates that could impact network security. FortiManager’s role in certificate management contributes to maintaining a secure and well-managed cryptographic infrastructure.
25. What features are offered for backup and recovery of security configurations?
Ans:
FortiManager provides robust features for the backup and recovery of security configurations. Administrators can regularly backup device configurations, ensuring quick recovery in case of failures or unforeseen issues. This proactive approach minimizes the impact on network operations, ensuring continuity and resilience in the face of unexpected events.
26. What role does FortiManager play in managing SSL VPN configurations?
Ans:
- Centralized SSL VPN policy management
- Uniform SSL VPN settings across devices
- Simplified SSL certificate management
- Granular control over VPN configurations
- Streamlined SSL VPN deployment
- Real-time monitoring of SSL VPN activities
27. How does FortiManager support integration with third-party security solutions within a network?
Ans:
FortiManager supports integration with third-party security solutions through open APIs and standardized protocols. This flexibility allows organizations to create an ecosystem of security tools, enhancing interoperability and ensuring a comprehensive and cohesive security posture across the network. FortiManager’s support for integration contributes to a more holistic approach to security management.
28. In what ways do you assist in maintaining network performance through resource optimization?
Ans:
FortiManager assists in maintaining network performance by optimizing resources through efficient policy management. It ensures that security policies are well-tailored, avoiding unnecessary resource consumption and bottlenecks. By optimizing policies, FortiManager contributes to balanced and optimized network performance, ensuring that security measures do not compromise overall network efficiency.
29. How does FortiManager contribute to the management of wireless network security policies?
Ans:
- Centralized FortiAP configuration management
- Unified security policies for wireless networks
- Efficient management of multiple FortiAPs
- Consistent security settings
- Simplified wireless network deployment
- Real-time monitoring of wireless security
30. What role does FortiManager play in ensuring high availability and reliability?
Ans:
FortiManager plays a critical role in ensuring high availability and reliability by centralizing the management of security configurations. It provides mechanisms for redundant deployments, automatic failover, and synchronization, minimizing downtime and ensuring continuous network security. FortiManager’s emphasis on high availability contributes to maintaining a robust and resilient security infrastructure.
31. How does FortiManager contribute to the visibility and management of wireless network security?
Ans:
FortiManager enhances the visibility and management of wireless network security policies by centralizing the configuration and monitoring of FortiAP devices. It ensures consistent security settings, facilitates policy updates, and provides comprehensive insights into wireless network security. FortiManager’s role in managing wireless security policies contributes to a secure and well-managed wireless network environment.
32. What security analytics and reporting capabilities does FortiManager offer?
Ans:
FortiManager provides robust security analytics and reporting capabilities for network administrators. It offers detailed reports on security events, policy compliance, and network performance. This wealth of information empowers administrators with actionable insights for decision-making, troubleshooting, and strategic planning. FortiManager’s analytics and reporting capabilities contribute to a data-driven and informed approach to network security.
33. What mechanisms does FortiManager provide for device backup and recovery?
Ans:
- Scheduled configuration backups
- Versioned configuration history
- Rapid recovery in case of failures
- Redundant backup storage options
- Enhanced data integrity checks
- Seamless restoration of configurations
34. How does FortiManager contribute to the simplification of network troubleshooting and diagnostics?
Ans:
FortiManager contributes to the simplification of network troubleshooting by providing centralized visibility into device configurations and activities. It offers diagnostic tools and logs, facilitating quick identification of issues and streamlining the resolution process for network administrators. FortiManager’s role in simplifying troubleshooting enhances the efficiency of incident response and network maintenance.
35. How does FortiManager contribute to securing virtualized and cloud environments?
Ans:
FortiManager plays a pivotal role in managing and securing virtualized environments and cloud deployments by extending its centralized management capabilities to virtual instances. It ensures consistent security policies, visibility, and compliance across diverse deployment environments. FortiManager’s adaptability to virtualized and cloud settings contributes to a cohesive and secure hybrid infrastructure.
36. How does FortiManager support the integration of third-party security solutions?
Ans:
- Open APIs for integration
- Standardized protocols support
- Interoperability with diverse security tools
- Comprehensive security ecosystem
- Enhanced threat intelligence sharing
- Strengthened overall security posture
37. How does FortiManager handle multi-tenancy and diverse security requirements?
Ans:
FortiManager addresses multi-tenancy challenges by providing granular control over security policies. Administrators can define and enforce policies based on tenant requirements, ensuring that each tenant’s security needs are met while maintaining overall network integrity. FortiManager’s support for multi-tenancy contributes to a flexible and secure network architecture that accommodates diverse security requirements.
38. Explain FortiManager’s role in threat intelligence integration and its impact on proactive security.
Ans:
FortiManager integrates threat intelligence by centralizing the collection and dissemination of threat information. This integration enhances proactive security by enabling automated responses to emerging threats. FortiManager plays a critical role in orchestrating timely responses, ensuring a swift and coordinated defense against evolving security risks. Its integration with threat intelligence contributes to a robust and adaptive security posture.
39. How does FortiManager facilitate role-based access control (RBAC) for administrators?
Ans:
- Centralized RBAC management
- Customizable roles and permissions
- Granular access control
- Assignable responsibilities
- Enhanced security through the least privilege
- Audit trails for role-based activities
40. How does FortiManager manage intrusion prevention systems (IPS) in a network?
Ans:
FortiManager facilitates the management of intrusion prevention systems (IPS) by providing a centralized platform for configuring and monitoring IPS policies. It ensures that IPS policies are consistently applied, enhancing the network’s ability to detect and prevent malicious activities. FortiManager’s role in managing IPS contributes to a proactive and effective defense against a wide range of cyber threats.
41. Explain FortiManager’s role in orchestrating and managing secure SD-WAN deployments.
Ans:
FortiManager plays a crucial role in orchestrating and managing secure SD-WAN deployments by centralizing the configuration and monitoring of SD-WAN policies. It ensures that SD-WAN settings align with security policies, providing a seamless and secure SD-WAN experience. FortiManager’s role in managing SD-WAN contributes to optimizing network performance, ensuring secure connectivity, and facilitating efficient traffic management.
42. How does FortiManager contribute to the management of email security policies and configurations?
Ans:
FortiManager contributes to the management of email security policies by centralizing the configuration and monitoring of FortiMail devices. It ensures that email security settings are consistently applied, helping organizations protect against email-borne threats. FortiManager’s role in managing email security policies contributes to a resilient and well-managed email security infrastructure.
43. How does FortiManager contribute to the management of IAM policies within a network?
Ans:
- Centralized FortiAuthenticator configuration management
- Unified IAM policies for user access
- Streamlined IAM policy updates
- Granular control over user authentication
- Real-time monitoring of IAM activities
- Enhanced overall access management
44. How does FortiManager contribute to the efficient management of VPN configurations?
Ans:
FortiManager significantly enhances the efficient management of VPN configurations by providing a centralized platform for administrators to configure and monitor VPN connections. It streamlines the deployment of VPN policies across Fortinet devices, ensuring consistency in settings. The centralized nature of FortiManager allows for real-time monitoring, enabling administrators to track VPN activities, identify potential issues promptly, and optimize the performance of VPN connections. This centralized approach simplifies the complex task of managing VPN configurations, contributing to a more secure and smoothly operating network.
45. What role does FortiManager play in enhancing network segmentation for improved security?
Ans:
FortiManager plays a pivotal role in enhancing network segmentation, thereby improving overall security. It provides efficient tools for policy enforcement, enabling administrators to define and enforce security policies based on network segments. This granular approach minimizes the risk of lateral movement for potential threats, containing and isolating security incidents. FortiManager’s capabilities in enforcing policies contribute to a more robust network architecture, where each segment is fortified against unauthorized access or potential breaches, leading to heightened overall security.
46. How does FortiManager support high availability and failover configurations?
Ans:
- Redundant FortiManager deployments
- Automatic failover mechanisms
- Continuous synchronization of configurations
- Minimized downtime during failovers
- Enhanced reliability and availability
- Seamless transition in case of primary failure
47. How does FortiManager contribute to network performance optimization through resource allocation?
Ans:
FortiManager significantly contributes to network performance optimization by ensuring judicious resource allocation through efficient policy management. It allows administrators to configure security policies that are well-tailored to the network’s needs, avoiding unnecessary resource consumption. By preventing bottlenecks and optimizing resourceusage, FortiManager plays a crucial role in achieving a balanced and efficient network performance. This results in reduced latency enhanced overall user experience, and a network that operates seamlessly even under varying traffic loads.
48. How does FortiManager support integration with Security Information and Event Management (SIEM) systems?
Ans:
- Seamless integration through standardized protocols
- Event logging and correlation capabilities
- Enhanced incident response coordination
- Strengthened SIEM capabilities
- Centralized event data collection
- Streamlined security information management
49. What features does FortiManager offer for the management of SSL/TLS certificates?
Ans:
FortiManager simplifies SSL/TLS certificate management by providing a centralized platform for configuration and monitoring. It ensures that SSL/TLS certificates are consistently managed across devices, reducing the risk of misconfigured or expired certificates. Administrators can efficiently handle certificate-related tasks, including issuance, renewal, and revocation, ensuring the robust security of encrypted communication. By centralizing certificate management, FortiManager contributes to a more secure network environment where encrypted communications are properly configured and maintained.
50. How does FortiManager support virtual private networks (VPNs) for secure remote access?
Ans:
- Centralized VPN configuration management
- Uniform VPN policies across devices
- Simplified VPN deployment
- Granular control over VPN settings
- Real-time monitoring of VPN activities
- Enhanced security for remote access
51. How does FortiManager contribute to the orchestration of secure SD-WAN deployments?
Ans:
FortiManager plays a crucial role in orchestrating secure SD-WAN deployments by centralizing the configuration and monitoring of SD-WAN policies. It ensures that SD-WAN settings align with security policies, providing a seamless and secure SD-WAN experience. Administrators can efficiently manage SD-WAN configurations, ensuring optimal performance and security. Real-time monitoring capabilities enable administrators to proactively address issues and optimize SD-WAN performance, contributing to a reliable and secure network infrastructure.
52. What role does FortiManager play in optimizing firewall rule sets for better performance?
Ans:
- The rule set optimization tools
- Analysis of rule performance impact
- Enhanced overall firewall performance
- Minimized rule conflicts and overlaps
- Improved network throughput
- Streamlined firewall policy management
53. What mechanisms does FortiManager employ for disaster recovery planning and network resilience?
Ans:
FortiManager is instrumental in disaster recovery planning, offering mechanisms for backup and recovery of security configurations. It allows administrators to schedule and perform regular backups of device configurations, ensuring that critical security settings are preserved. In the event of failures or unforeseen issues, FortiManager facilitates rapid recovery by seamlessly restoring configurations. This minimizes downtime, ensures continuous network operations, and contributes to overall network resilience and robust disaster recovery strategies.
54. How is FortiManager maintaining compliance with regulatory requirements and industry standards?
Ans:
FortiManager plays a crucial role in assisting organizations in maintaining compliance with regulatory requirements and industry standards. It provides tools for creating, enforcing, and auditing security policies, ensuring that the network adheres to specific compliance standards. The centralized visibility into security configurations simplifies the compliance auditing process, allowing organizations to demonstrate adherence to regulations such as GDPR, HIPAA, or PCI DSS. FortiManager’s capabilities contribute to the creation of a secure and compliant network environment, addressing the complex landscape of regulatory compliance.
55. What role does FortiManager play in the orchestration and management of cloud security policies?
Ans:
- Extension of centralized management to cloud environments
- Uniform security policies across on-premises and cloud deployments
- Streamlined cloud security policy updates
- Granular control over cloud security settings
- Real-time monitoring of cloud security activities
- Enhanced overall security posture for hybrid and multi-cloud architectures
56. What role does FortiManager play in threat intelligence integration for proactive security?
Ans:
FortiManager is a key component in threat intelligence integration, centralizing the collection and dissemination of threat information. By integrating threat intelligence feeds, FortiManager enables automated responses to emerging threats. This proactive security approach ensures a swift and coordinated defense against evolving security risks. Administrators can leverage real-time threat intelligence to adjust security policies and fortify the network against potential threats. FortiManager’s integration with threat intelligence contributes to a proactive and dynamic security posture.
57. Explain the role of managing and securing Internet of Things (IoT) devices.
Ans:
- Centralized FortiNAC configuration management
- Unified security policies for IoT devices
- Efficient IoT policy deployment
- Granular control over IoT device settings
- Real-time monitoring of IoT device security
- Streamlined IoT policy update
58. How does FortiManager contribute to the management of email security policies and configurations?
Ans:
FortiManager significantly contributes to the management of email security policies by centralizing the configuration and monitoring of FortiMail devices. It ensures that email security settings are consistently applied, helping organizations protect against email-borne threats such as phishing or malware. Real-time monitoring capabilities enhance the visibility of email security activities, allowing administrators to respond to potential threats promptly. FortiManager’s role in managing email security policies contributes to a robust defense against email-related vulnerabilities.
59. How does FortiManager contribute to the management of endpoint security configurations?
Ans:
- Centralized FortiClient configuration management
- Unified endpoint security policies
- Efficient endpoint policy deployment
- Granular control over endpoint settings
- Real-time monitoring of endpoint security
- Streamlined endpoint policy updates
60. What features does FortiManager offer for analyzing and optimizing firewall rule sets?
Ans:
FortiManager offers robust features for analyzing and optimizing firewall rule sets. It provides tools for analyzing rule performance impact, identifying redundant rules, and streamlining rule configurations. This results in enhanced overall firewall performance by minimizing conflicts and optimizing rule sets. Administrators can efficiently manage and refine firewall policies, contributing to improved network security and streamlined rule management.
61. How does FortiManager support the management of web application firewall (WAF) policies?
Ans:
FortiManager facilitates the centralized management of web application firewall (WAF) policies. It enables administrators to define, deploy, and monitor WAF policies across multiple devices. This centralized approach ensures effective protection against web-based attacks by allowing granular control over WAF configurations. Real-time monitoring capabilities provide administrators with insights into the effectiveness of WAF policies, contributing to a secure and resilient defense against web application threats.
62. In what ways does FortiManager contribute to the optimization of (IPS)?
Ans:
FortiManager significantly contributes to the optimization of intrusion prevention systems (IPS) by providing a centralized platform for configuring and monitoring IPS policies. It ensures that IPS policies are consistently applied across devices, enhancing the network’s ability to detect and prevent malicious activities. FortiManager’s centralized approach streamlines IPS configuration changes, allowing administrators to optimize IPS policies for improved security efficiently.
63. How does FortiManager streamline the management of (VPNs) for secure remote access?
Ans:
FortiManager streamlines VPN management by centralizing the configuration and monitoring of VPN connections. It ensures consistent VPN policies across devices, facilitating remote access management. Real-time monitoring capabilities provide administrators with visibility into VPN activities, enabling effective security monitoring. FortiManager’s role in streamlining VPN management contributes to enhanced security for remote access scenarios, ensuring a secure and seamless experience for remote users.
64. What features does FortiManager provide for dynamic adjustment of firewall rule sets?
Ans:
- The rule set optimization tools
- Real-time analysis of rule performance
- Identification of redundant rules
- Streamlined rule configurations
- Improved overall network security
65. What mechanisms does FortiManager provide for managing NAC policies?
Ans:
FortiManager provides efficient management of network access control (NAC) policies through centralized configuration and monitoring of FortiNAC devices. It ensures that NAC policies align with overall security strategies, providing granular control over network access configurations. Administrators can efficiently manage and update NAC policies, contributing to enhanced overall network security by preventing unauthorized access and enforcing compliance.
66. How does FortiManager streamline the management of security policies for distributed networks?
Ans:
- Centralized security policy management
- Uniform policy enforcement
- Simplified policy updates
- Efficient handling of distributed policies
- Reduction of policy conflicts
67. How does FortiManager contribute to the management of endpoint security configurations within a network?
Ans:
FortiManager contributes to endpoint security management by centralizing the configuration and monitoring of FortiClient devices. It ensures that endpoint security settings are consistently applied across devices, providing real-time monitoring of endpoint security activities. Administrators can efficiently deploy and update endpoint security policies, contributing to a secure network environment by protecting against potential threats at the endpoint level.
68. What role does FortiManager play in managing and securing Internet of Things (IoT) devices within a network?
Ans:
FortiManager manages and secures IoT devices by centralizing the configuration and monitoring of FortiNAC devices. It ensures that security policies for IoT devices align with overall network security strategies. This centralized approach streamlines the management of diverse IoT deployments, providing a unified and secure framework for IoT devices. FortiManager’s role in managing IoT devices contributes to enhanced security, preventing potential threats arising from IoT vulnerabilities.
69. How does it contribute to the management of (IAM) policies within a network?
Ans:
FortiManager contributes to IAM policy management by centralizing the configuration and monitoring of FortiAuthenticator devices. It ensures that IAM policies align with overall security strategies, providing centralized control over user authentication and access management. Administrators can efficiently manage and update IAM policies, contributing to enhanced overall access security and ensuring that only authorized users have access to the network resources.
70. How does FortiManager contribute to network scalability for large enterprises?
Ans:
- Horizontal scalability
- Efficient management of numerous devices
- Centralized control over extensive infrastructures
- Streamlined policy deployment at scale
- Consistent security policies across large networks
71. What role does FortiManager play in the orchestration?
Ans:
FortiManager orchestrates and manages cloud security policies by extending its centralized management capabilities to cloud deployments. It ensures consistent security policies, visibility, and compliance across on-premises and cloud environments. Administrators can efficiently manage and update cloud security policies, providing a cohesive security posture for hybrid and multi-cloud architectures. FortiManager’s role in cloud security management contributes to a secure and integrated approach to protecting cloud resources.
72. How does FortiManager contribute to the optimization of disaster recovery planning for network resilience?
Ans:
FortiManager contributes to the optimization of disaster recovery planning by offering robust mechanisms for backup and recovery of security configurations. It ensures that configurations are regularly backed up, minimizing downtime in case of failures. In the event of unforeseen issues, FortiManager facilitates rapid recovery by seamlessly restoring configurations. This centralized approach to disaster recovery planning ensures continuous network operations, resilience against potential disruptions, and a proactive strategy for mitigating the impact of network incidents.
73. In what ways does FortiManager enhance network visibility and monitoring capabilities?
Ans:
- Consolidation of data from Fortinet devices
- Comprehensive real-time monitoring
- Insights into network activities
- Visibility into security events
- Performance metrics for device monitoring
74. What centralized features does FortiManager provide for audit readiness and streamlined compliance audits?
Ans:
FortiManager offers centralized features for audit readiness by providing tools for creating, enforcing, and auditing security policies. Its centralized visibility into security configurations simplifies the compliance auditing process, allowing organizations to demonstrate adherence to regulations and industry standards. FortiManager’s features, such as role-based access control, audit trails, and reporting capabilities, streamline the audit process. This contributes to maintaining a secure and compliant network environment, ensuring that organizations are well-prepared for regulatory audits and internal assessments.
75. How does FortiManager ensure high availability and resilience in distributed network environments?
Ans:
With active-active clustering, FortiManager guarantees high availability in dispersed networks, facilitating smooth failover and load balancing across several instances. It also facilitates real-time synchronization and synchronized settings, which increase robustness by preserving consistency amongst network components.
76. What role does FortiManager play in automating security workflows for rapid threat response?
Ans:
- Workflow automation features
- Automated threat response actions
- Coordinated defense mechanisms
- Rapid quarantine capabilities
- Real-time adjustments to security policies
77. What is the key difference between FortiManager and FortiAnalyzer?
Ans:
| Key Difference | FortiManager | FortiAnalyzer | |
| Primary Function | Centralized configuration and management of Fortinet devices, ensuring consistency and efficiency in network operations. | Specialized for log analysis, reporting, and forensic analysis, providing insights into network activities and security events. | |
| Focus Area | Configuration management, policy enforcement, and device monitoring. | Log aggregation, analysis, and reporting for enhanced security visibility and compliance monitoring. | |
| Use Cases | Centralized control of security policies, device configurations, and updates across the network. | Log storage, analysis, and reporting for auditing, compliance, and investigating security incidents. | |
| Data Handling | Configuration data, policies, and monitoring information for Fortinet devices. | Log data from Fortinet devices, providing historical records for analysis and compliance reporting. | |
| Integration with Security Device | Manages Fortinet security devices and enforces policies on them. | Analyzes logs and reports generated by Fortinet devices, aiding in identifying and mitigating security incidents. |
78. How does FortiManager contribute to efficient SSL VPN policy management across devices?
Ans:
By offering a single platform for establishing, monitoring, and updating rules across devices, FortiManager simplifies the administration of SSL VPN policies. Large-scale deployments become simpler with its intuitive UI for building and implementing consistent SSL VPN settings. Moreover, version control and policy templates are supported by FortiManager, guaranteeing effective and coordinated SSL VPN management throughout the network.
79. What role does FortiManager play in optimizing firewall rule sets for better performance?
Ans:
- The rule set analysis tools
- Identification of redundant rules
- Streamlined rule configurations
- Enhanced firewall performance
- Minimized rule conflicts
80. How does FortiManager contribute to the orchestration of secure SD-WAN deployments?
Ans:
By centralizing configuration and administration responsibilities, FortiManager enables safe SD-WAN orchestration while guaranteeing uniformity across dispersed network components. It makes SD-WAN policy changes and dynamic provisioning possible, improving flexibility and response to shifting network circumstances. The extensive monitoring features of FortiManager offer real-time insight into SD-WAN performance, enhancing overall network efficiency and security.
81. What centralized features does FortiManager provide for audit readiness and streamlined compliance audits?
Ans:
- Role-based access control for audit trails
- Comprehensive reporting capabilities
- Centralized visibility into security configurations
- Simplified compliance auditing process
- Alignment with regulatory requirements
82. How does FortiManager support efficient management of SSL/TLS certificates across the network?
Ans:
By offering centralized control and enabling administrators to install, monitor, and update certificates throughout the network, FortiManager simplifies SSL/TLS certificate administration. It provides certificate lifecycle management procedures that are automated, guaranteeing effective compliance and renewal. Additionally, FortiManager improves overall network security by providing full insight into certificate status and expirations.
83. What role does FortiManager play in threat intelligence integration and proactive security?
Ans:
- Integration with threat intelligence feeds
- Centralized collection of threat information
- Automated responses to emerging threats
- Coordinated defense against evolving risks
- Real-time adjustments based on threat intelligence
84. How does FortiManager contribute to the management of email security policies and configurations?
Ans:
By centralizing policy formulation, setup, and monitoring, FortiManager simplifies email security administration and ensures efficiency and consistency throughout the network. In order to improve overall management and protection against threats, it provides a consistent interface for managing different email security measures.
85. What features does FortiManager offer for analyzing and optimizing (IPS)?
Ans:
For the purpose of assessing and improving Intrusion Prevention System (IPS) rules, FortiManager offers an extensive feature set that includes customized reports and real-time threat intelligence updates. It makes it possible to effectively fine-tune IPS setups to improve network security and threat detection.
86. How does it contribute to the management and security of the Internet of Things (IoT) in a network?
Ans:
- Centralized FortiNAC configuration management
- Unified security policies for IoT devices
- Efficient handling of diverse IoT deployments
- Streamlined management of IoT security
- Enhanced security posture against IoT vulnerabilities
87. How does FortiManager ensure secure and efficient management of (NAC) policies?
Ans:
By centralizing setup, monitoring, and enforcement, FortiManager guarantees safe Network Access Control (NAC) policy management and makes it possible to implement uniform access policies throughout the network. In a variety of network scenarios, it improves security and compliance by providing fine-grained control over user and device access.
88. What role does FortiManager play in the efficient management of endpoint security configurations?
Ans:
By centralizing the administration of security configurations and enabling administrators to deploy and track policies across endpoints, FortiManager plays a critical role in endpoint security. In order to guarantee uniform protection and compliance, it offers a centralized platform for customizing and upgrading endpoint security features. With automation and real-time visibility into endpoint security status, FortiManager improves efficiency.
89. How does FortiManager contribute to the optimization of disaster recovery planning for network resilience?
Ans:
- Robust backup and recovery mechanisms
- Scheduled configuration backups
- Rapid restoration of configurations
- Minimized downtime during recovery
- Continuous network operations in the face of disruptions
90. What features does FortiManager offer for centralized identity and access management (IAM) policy control?
Ans:
With capabilities including user authentication, role-based access control (RBAC), and connectivity with external authentication systems, FortiManager provides centralized Identity and Access Management (IAM) policy management. It improves security and access governance by offering a single platform for creating and implementing IAM policies throughout the network.
91. Explain FortiManager’s mechanisms for efficient cloud security policy orchestration.
Ans:
Through centralized administration, FortiManager guarantees effective cloud security policy orchestration, facilitating uniform setup and monitoring of security policies across multi-cloud environments. In order to improve cloud protection, it facilitates automation and interaction with cloud services, making it easier to implement and execute security measures.
92. How does FortiManager contribute to the prevention of IP address exhaustion and efficient capacity planning?
Ans:
By optimizing IP address allocation through centralized administration and assuring effective planning and use, FortiManager helps to prevent IP address depletion. It gives administrators insight into how IP addresses are being used, allowing them to more efficiently plan and distribute resources for increased network capacity.
93. Explain FortiManager’s role in ensuring low latency and high responsiveness.
Ans:
- Efficient allocation of resources
- Streamlined policy configurations for optimal performance
- Continuous monitoring for performance optimization
- Centralized visibility into network activities
- Enhanced network responsiveness and reduced latency
94. Explain FortiManager’s role in dynamically adjusting network configurations.
Ans:
By centralizing management and using real-time data, FortiManager dynamically modifies network configurations, enabling administrators to react quickly to evolving network circumstances. In response to changing security and performance needs, it ensures agility and flexibility by supporting automated workflows for dynamic policy modifications.
95. Explain FortiManager’s role in securing compliant network environments for organizations.
Ans:
- Tools for creating, enforcing, and auditing security policies
- Centralized visibility into security configurations
- Alignment with regulatory requirements and industry standards
- Simplified compliance audits
- Contribution to a secure and compliant network environment.






