- Introduction to Splunk in Security
- Importance of Security Response in Modern IT
- Splunk Approach to Security Monitoring
- Real-Time Threat Detection with Splunk
- Using Analytics for Proactive Security
- Splunk’s Role in Threat Intelligence
- Why specifically use machine learning?
- Conclusion
Introduction to Splunk in Security
In today’s digital world, cyber threats are not just a possibility; they are certain. Attackers are using more advanced tools than ever, making traditional security methods feel like trying to catch rain in a thimble. Simply waiting for an alarm to sound is no longer a good strategy. The new era in cybersecurity focuses on staying ahead of the threat. It’s about creating a proactive security response that can predict, identify, and stop attacks before they cause serious damage. This is where the power of data, combined with Machine Learning in Splunk, becomes crucial. To build the skills needed for such intelligent threat detection, explore Machine Learning Training a hands-on program that equips professionals to develop predictive models, automate responses, and strengthen cybersecurity infrastructure. By using platforms like Splunk, organizations can shift their security stance from defensive to offensive, turning large amounts of data into their biggest defensive asset.
Importance of Security Response in Modern IT
A quick and effective security response is not just an IT issue; it is an important business function. How fast an organization can spot and handle a threat directly affects its profits and reputation. A slow or poor response can lead to serious problems. To enhance detection speed and automate threat response at scale, explore Overview of ML on AWS a strategic guide that explains how Amazon Web Services empowers security teams with machine learning tools for real-time analysis, anomaly detection, and intelligent decision-making.
- Minimizing Financial Damage: The longer an attacker is in your network, the more harm they can cause. A swift response can stop data theft, system damage, and ransomware attacks, saving millions in recovery costs and possible fines.
- Protecting Brand Reputation: Customers trust you with their data. A data breach breaks that trust, often for good. A fast and clear response shows you know what you’re doing and can help reduce long-term damage to your reputation.
- Ensuring Regulatory Compliance: Laws like GDPR, HIPAA, and CCPA have strict rules for data protection and breach notification. A clear security response plan is crucial for meeting these legal requirements and avoiding heavy penalties.
- Maintaining Business Continuity: A significant security incident can stop business operations completely. A strong response plan ensures that key systems can be restored quickly, reducing downtime and loss of income.
Ready to Get Certified in Machine Learning? Explore the Program Now Machine Learning Online Training Offered By ACTE Right Now!
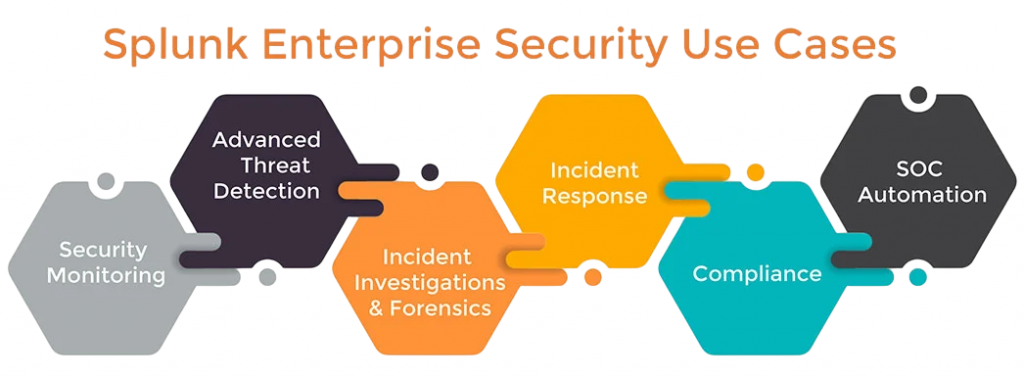
Splunk Approach to Security Monitoring
Splunk changes the game in security monitoring by breaking down data silos and giving a complete view of an organization’s security stance. Its approach is based on a few key principles that help security teams work more efficiently: centralized visibility, real-time analytics, and scalable automation. To implement intelligent models that support these principles, explore Keras vs TensorFlow a side-by-side comparison that explains how each framework handles model building, deployment, and integration with enterprise-grade tools.
- Unified Data Aggregation: Splunk gathers and standardizes data from all your different security tools and IT systems. This provides a single source of truth, eliminating the need to switch between numerous consoles to investigate an alert.
- Centralized Visibility and Dashboards: With all your data in one spot, you can build custom dashboards that display important security metrics and trends. This helps analysts quickly identify suspicious patterns and monitor the health of their security environment in real time.
- Powerful Search and Correlation: Splunk’s Search Processing Language (SPL) drives its analytics. It lets analysts run complex queries across large datasets in seconds, connecting seemingly unrelated events to reveal the full story of an attack.
- Automated Alerting and Workflows: Instead of manually sorting through logs, teams can set up Splunk to automatically create alerts for specific actions or thresholds. This cuts down on manual work and allows analysts to concentrate on valuable investigations and threat hunting.
- Detecting Unknown Threats: Traditional security tools rely on predefined rules and signatures to find known threats. Machine Learning excels at identifying the “unknown unknowns” by detecting subtle anomalies and deviations from normal behavior that rule-based systems would overlook.
- Reducing Alert Fatigue: Security analysts often feel overwhelmed by a constant flood of low-level alerts. Machine Learning algorithms can analyze and score these alerts, automatically filtering out false positives and prioritizing genuine threats. This allows analysts to focus their time and energy where it matters most.
- Automating Behavioral Baselines: Manually defining “normal” behavior for thousands of users and systems is nearly impossible. Machine Learning automates this process, continuously learning and updating these baselines as your environment changes.
- Accelerating Incident Investigation: By grouping related events and identifying causal relationships, Machine Learning helps analysts grasp the full scope of an attack in minutes instead of hours. This dramatically speeds up the investigation and response process.
To Explore Machine Learning in Depth, Check Out Our Comprehensive Machine Learning Online Training To Gain Insights From Our Experts!
Real-Time Threat Detection with Splunk
In cybersecurity, timing is crucial. The period between the first breach and its detection is where attackers succeed. Splunk closes this gap by allowing real-time threat detection. It doesn’t wait to analyze data in batches; it constantly monitors data streams as they come into the system. To build intelligent systems that support this kind of proactive defense, explore Machine Learning Training a hands-on program that teaches professionals how to develop predictive models, automate monitoring, and enhance cybersecurity using real-time data.
For example, if a user account that usually operates from the United States suddenly logs in from Eastern Europe, Splunk can instantly flag this unusual travel scenario. This quick awareness lets security teams take action before the intruder can gain more control or navigate laterally across the network. Additionally, Splunk uses correlation searches to link multiple data points into a single, accurate alert. This provides the context needed to grasp the entire scale of a potential attack.
Using Analytics for Proactive Security
A proactive security response means moving from just reacting to alerts to actively searching for threats. This is where cybersecurity analytics comes in. Splunk helps teams go beyond known threats and seek out signs of the unknown. By examining historical data, security teams can identify what “normal” activity looks like for each user, server, and application in their environment. Once this baseline is set, any deviation, even a small one, can be flagged for further investigation. To support this kind of intelligent monitoring, explore Best Machine Learning Tools a curated guide to top platforms that help automate anomaly detection, streamline data analysis, and enhance cybersecurity operations. For instance, if a server suddenly starts communicating on an unusual port or a user begins accessing files they have never interacted with before, this could signal a compromise. This data-driven security approach turns your data into an active defense tool.
Looking to Master Machine Learning? Discover the Machine Learning Expert Masters Program Training Course Available at ACTE Now!
Splunk’s Role in Threat Intelligence
No organization operates in isolation. To effectively defend against modern threats, you need to understand the global threat landscape. This is where threat intelligence comes in. Splunk excels at making threat intelligence useful by connecting with many external feeds that offer current information on harmful IP addresses, recognized malware signatures, and attacker command-and-control servers.
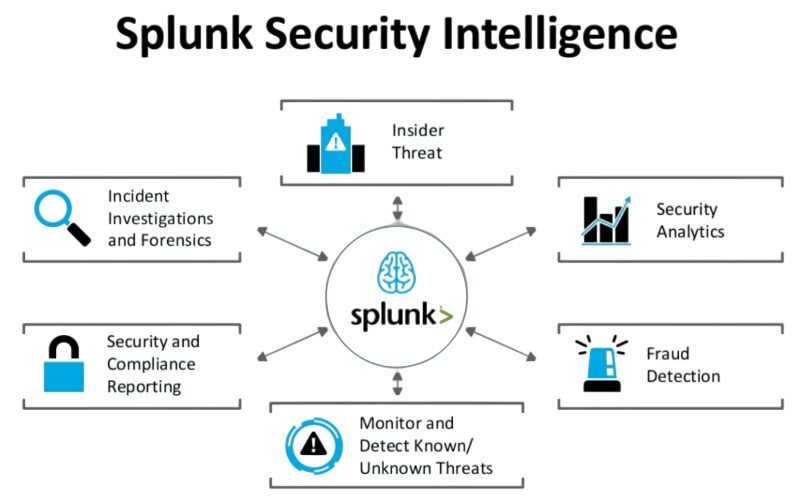
To explore how deep learning enhances these capabilities through pattern recognition and anomaly detection, check out Deep Learning Books a curated collection of expert resources that cover neural networks, cybersecurity applications, and advanced threat modeling techniques. Splunk automatically links this external intelligence with your internal machine data. If one of your systems tries to connect with a known malicious domain, Splunk will create an immediate, high-priority alert. This adds external context to your internal security data, helping you quickly identify and prioritize the biggest threats to your organization.
Why specifically use machine learning?
While analytics and threat intelligence are powerful, Machine Learning takes proactive security to the next level. It automates and scales the process of finding hidden threats in ways that human analysts alone cannot achieve. Its benefits are transformative for any security operations center. To understand the models driving this transformation, explore Machine Learning Algorithms a strategic guide that explains how classifiers, anomaly detectors, and ensemble methods are reshaping cybersecurity with speed and precision.
Preparing for Machine Learning Job Interviews? Have a Look at Our Blog on Machine Learning Interview Questions and Answers To Ace Your Interview!
Conclusion
In response to constantly changing cyber threats, waiting to react is not a good strategy. The key to effective defense is a proactive, data-based approach. By using Splunk for Security along with the predictive capabilities of Machine Learning in Splunk, organizations can transform their protection methods. To build the expertise needed for such intelligent security solutions, explore Machine Learning Training a hands-on program that teaches professionals how to develop predictive models, automate threat detection, and enhance cybersecurity using real-time data. This combination allows for real-time threat detection and the chance to anticipate and stop attacks before they cause damage. Adopting Machine Learning in Splunk as part of a long-term strategy is essential for any organization that wants to create a strong and flexible security system ready for future challenges.