An AWS Architect is a skilled professional responsible for designing and implementing robust cloud solutions on the Amazon Web Services (AWS) platform. These architects play a pivotal role in crafting scalable and secure architectures that align with organizational objectives. Their key responsibilities encompass solution design, utilizing Infrastructure as Code (IaC) tools like AWS CloudFormation for automated deployment, and implementing stringent security measures.
1. How are terminating and stopping instances different processes?
Ans:
Terminating and stopping instances refer to distinct processes in the context of computing resources. “Terminating” an instance typically involves permanently shutting it down, deallocating resources, and ending its existence. In contrast, “stopping” an instance is a temporary suspension, where the instance retains its allocated resources but enters a halted state, allowing for later resumption without data loss.
2. When there is a need to acquire costs with an EIP?
Ans:
EIP stands for an Elastic Internet Protocol address. Costs are acquired with EIP when the same is associated and allocated with the stopped instance. In case only one Elastic IP is there with instances running, and will not be charged for it. However, in case the IP is attached to a stopped instance, you need to pay for it.
3. What are states available in Processor State Control?
Ans:
It contains a two states and they are:
P-state: It has different levels starting from P0 to P15. P0 represents highest frequency and P15 represents lowest frequency.
C-State: Its levels are from the C0 to C6 where C6 is the strongest state for a processor.
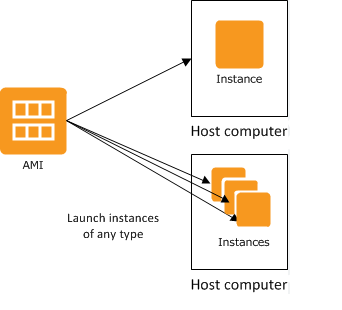
4. What is AMI?
Ans:
AMI is generally considered a template for virtual machines. While starting an instance, it is possible to select a pre-baked AMI’s that AMI commonly has in them. However, not all the AMIs are available to use free of cost. It is also possible to have the customized AMI and the most common reason to use the same is nothing but saving a space on Amazon Web Service. This is done in case a group of software is not required and AMI can simply be customized in this situation.
5. What is a private and public address?
Ans:
Private address is directly correlated with Instance and is sent back to EC2 only in case it is terminated or stopped. On the other hand, the public address is correlated in the similar manner with Instance until it is terminated or stopped. It is possible to replace public addresses with Elastic IP. This is done when a user wants it to stay with an Instance as per need.
6. What are the main components of AWS?
Ans:
- Elastic Block Store (EBS)
- Elastic Compute Cloud (EC2)
- Elastic Load Balancing (ELB)
- CloudWatch
- Identity and Access Management (IAM)
- Route 53
- Simple Email Service (SES)
7. Is it possible to use S3 with EC2 instances?
Ans:
Yes, it’s possible if instances are having root devices and are supported by instance storage. Amazon uses one of very reliable, scalable, fast, as well as inexpensive networks for hosting all websites. With the help of S3, it is possible for developers to get access to the same network. There are tools available in the AMI’s that users can consider when it comes to executing systems in EC2. The files can simply be moved between the EC2 and S3.
8. What method will you use for moving data over a very long distance?
Ans:
Amazon Transfer Acceleration is a good option. There are other options are Snowball but the same doesn’t support a data transfer over a very long distance such as among continents.
Amazon Transfer Acceleration is the best option because it simply throttles data with the help of network channels that are optimized and assure fast data transfer speed.
9. What will happen if I launch instances in Amazon VPC?
Ans:
- This is a common approach that is considered when it comes to launching EC2 instances.
- Each instance will have a default IP address if instances are launched in Amazon VPC.
- This approach is also considered when needing to connect cloud resources with the data centers.
10. Is it possible to speed up data transfer in Snowball?
Ans:
Yes, it’s possible. There are certain methods for this. First is simply copying from the different hosts to the same Snowball. Another method is creating a group of the smaller files. This is helpful as it cuts down encryption issues. Data transfer can also be enhanced by simply copying operations again and again at the same time provided the workstation is capable of bearing load.
11. Why are subnets required to be created?
Ans:
They are needed to utilize the network with the large number of hosts in a reliable manner. By dividing the network into the smaller subnets, it can be made simpler and chances of errors or data loss can be eliminated up to excellent extent.
12. Is it possible to attach multiple subnets to the routing table?
Ans:
Yes, it’s possible. They are generally considered when it comes to routing network packets. Actually, when a subnet has several route tables, it can create confusion about the destination of these packets.
It is because of no other reason than there should be only one route table in the subnet. The route table can have unlimited records and therefore it is possible to attach the multiple subnets to the routing table.
13. What does AMI contain within AWS?
Ans:
- A template for instance’s root volume.
- A block device mapping to decide which volumes should be attached to an instance when it is launched.
- Launch permissions to determine which AWS accounts are permitted to use AMI to launch instances.
14. What happens if AWS Direct Connect fails to perform its function?
Ans:
It is recommended to backup Direct Connect as in case of power failure you can lose everything. Enabling BFD i.e. Bi-directional Forwarding Detection can avoid the issues. In case no backup is there, VPC traffic would be dropped and need to start everything from an initial point again.
15. Compare RDS, Redshift, and DynamoDB.
Ans:
RDS is basically the DBM service that is considered for relational databases. It is useful for upgrading and patching data automatically. However, it works for structured data only.
On the other hand, Redshift is used in Data analysis. It is basically data warehouse service.
When it comes to the DynamoDB, it is considered when there is a need to deal with unstructured data. RDS is quick as compared to both Redshift and DynamoDB.
16. Is it possible to run multiple DBs for Amazon RDS free of cost?
Ans:
Yes, it’s possible. However, there is a strict upper limit of 750 hours of usage post which everything will be billed as per the RDS prices. In case you exceed the limit, and will be charged only for an extra hour beyond 750.
17. What is the difference between On-demand Instance and Spot Instance?
Ans:
| Feature | On-Demand Instances | Spot Instances | |
| Pricing Model |
Fixed pricing |
Variable pricing based on supply and demand | |
| Cost Predictability | High predictability | Costs can fluctuate based on market conditions | |
| Availability | Always available | Availability subject to spot market conditions | |
| Ideal Use Case |
Stable, continuous workloads |
Short-term, fault-tolerant, or flexible workloads |
18. What exactly are key pairs in AWS?
Ans:
- Key pairs are the credentials that are used to access the Amazon EC2 Instances securely.
- Key pairs include the public and private keys when connecting to the Amazon EC2 instance.
19. What is the significance of Connection Draining?
Ans:
There are certain stages when traffic needs to be re-verified for bugs and unwanted files that raise security concerns. Connection draining helps in the re-routing traffic that comes from the Instances and which is in queue to be updated.
20. What if content is absent in CloudFront and a request is made?
Ans:
CloudFront sent content from the primary server directly to cache memory of edge location. As it’s a content delivery system, it tries to cut down latency and that is why it will happen. If operation is performed for a second time, the data would directly be served from a cache location.
21. What are the benefits of auto-scaling?
Ans:
- Enhanced a fault tolerance
- Sustain the performance automatically
- Higher availability
- Optimal cost management
- Make a reasonable scaling decisions
22. Define AWS CloudTrail.
Ans:
AWS CloudTrail is the service that provides logs of AWS API calls and associated events for auditing and compliance purposes. It enables the customers to track changes to AWS resources and understand who made those changes, what actions were taken, and when they were taken.
23. When is EIP necessary to obtain costs?
Ans:
EIP stands for the elastic Internet Protocol address. When an EIP is used to procure the expenses related to and allotted to the halted case, the expenses are related to and allotted to the halted case. However, you must pay for an IP address if it is associated with the suspended case or is not associated with any event.
24. What factors are considered while choosing an availability zone?
Ans:
- Cost
- Latency
- Compliance
- Availability of services and features
25. Describe SQS in terms of AWS.
Ans:
Amazon Simple Queue Service (SQS) allows to send, store, and receive the messages between the multiple software components at any amount without losing the original messages.
26. What are key features of Amazon CloudSearch?
Ans:
Amazon CloudSearch is the fully managed cloud solution for websites or applications.
- Range search
- Boolean search
- Prefix search
- Highlighting
- Complete text search
27. Which can be used for collecting and processing e-commerce data?
Ans:
Amazon Redshift and Amazon DynamoDB are the best options. Generally, data from e-commerce websites are unstructured. As both of them are useful for the unstructured data, and can use them.
28. Which services are used to deploy applications in AWS?
Ans:
- AWS Elastic Beanstalk
- AWS EC2
- AWS Lambda
- AWS Fargate
- AWS Lightsail
- AWS CloudFormation
29. Which AWS instance is suitable for transporting a four-hub Hadoop cluster?
Ans:
This can be accomplished by running an instance of i2.large or c4.8x large. Regardless, c.4bx requires a more sophisticated PC setup. At certain points, can simply instruct EMR to carry out worker’s programmed design on behalf. S3 can be used to store data that can then be retrieved by the EMR. It will then re-stack data in S3 .
30. List the types of load balancers in AWS services.
Ans:
- Application Load Balancers
- Network Load Balancers
- Classic Load Balancers
- Gateway Load Balancers
31. What happens if AWS Direct Connect is not fully utilised?
Ans:
It is recommended to reinforce Direct Connect, as risk losing everything if there is force failure. Empowering BFD with Bi-directional Forwarding, such as Detection, can assist in avoiding problems. Without reinforcement, VPC traffic will be lost, and everything will have to be restarted from scratch.
32. What are different Amazon S3 storage classes available?
Ans:
- S3 Standard
- S3 Standard-Infrequent Access (S3 Standard-IA)
- S3 Intelligent-Tiering
- S3 a One Zone-Infrequent Access
- S3 Glacier Instant Retrieval
- S3 Glacier Flexible Retrieval
- S3 Glacier Deep Archive
33. What happens if CloudFront’s substance is unavailable ?
Ans:
CloudFront routed data directly from essential workers to the store memory of the edge area. Because it is the framework for substance conveyance, it will attempt to minimize inertness, which is why it will occur. If activity is repeated, the information is served directly from the store area.
34. What are various cycles conclusive and halting?
Ans:
When an instance is halted, it terminates normally. Following that, it conducts a transaction. Due to the fact that the entire EBS volume remains accessible, the occurrence can be restarted at any time. The best part is that when an event is paused, clients are not charged for the time period during which event was paused.
The occurrence concludes with the standard closure. After that, Amazon EBS volumes began to vanish. To prevent them from erasing, simply set Erase on Termination to bogus. Given that occurrence has been deleted, it is illogical to anticipate that it will be run again in future.
35. When should AWS consider Provisional IOPS over Standard RDS stockpiling?
Ans:
If clump-based has, an equivalent is required. This is because temporary IOPs have shown to provide faster IO rates. In any case, they are somewhat more expensive than alternative options. Hosts who prepare their own bouquets are not required to enlist guests’ assistance. Temporary IOPs have gained popularity as a result of this rationale.
36. What does Amazon EC2 administration entail?
Ans:
Amazon describes the Elastic Compute Cloud (Amazon EC2) as web administration that provides cloud users with resizable register limits. Its purpose is to simplify web-scale distributed computing for designers. The straightforward web administration interface of the Amazon EC2 enables engineers to acquire and manage limits with the minimal grating.
37. What role cushion plays in Amazon’s web administrations?
Ans:
Buffer is accustomed to fortifying a framework against traffic or load eruptions by synchronizing various components. The segments consistently receive and evaluate the solicitations unevenly. Support maintains the harmony between the various components and forces them to operate at similar speed in order to provide a faster type of assistance.
38. What exactly is a Serverless application?
Ans:
The serverless application can be defined easily with the AWS Serverless Application Model (AWS SAM), which is an extension of AWS CloudFormation, by specifying Amazon API Gateway APIs, AWS Lambda functions, and Amazon DynamoDB tables that are needed.
39. What are AWS’s Shared Responsibility Model?
Ans:
- Due to the fact that they are building frameworks on top of AWS platform, security responsibilities will be shared.
- While AWS is responsible for cloud security, the client is responsible for cloud security.
- Clients retain control over security they choose to implement to protect their own content, stage, applications, frameworks, and organizations, no differently than would with on-premises datacenter applications.
40. What does CloudFront’s geo-targeting entail?
Ans:
Using the geo-targeting concept, businesses may show audience tailored content based on a geographic location without changing the URL. This makes it simpler to produce content that is especially suited to the local audience’s needs.
41. Why is it not possible to change the private IP address of an EC2 instance?
Ans:
This is because a private IP remains with the instance permanently or through a life cycle. Thus it cannot be changed or modified. However, it is possible to change a secondary private address.
42. What does CloudFront’s geo-targeting entail?
Ans:
Using the geo-targeting concept, businesses may show audience tailored content based on a geographic location without changing the URL. This makes it simpler to produce content that is especially suited to the local audience’s needs.
43. How do Availability Zone and Region relate to one another?
Ans:
AWS regions, like US-West 1 (North California) and Asia South, are distinct geographic regions (Mumbai). Availability zones, on other hand, are the locations that are present inside regions. These are often isolated zones that have the ability to duplicate themselves as needed.
44. What actions comprise a CloudFormation Solution?
Ans:
- Using JSON or YAML format, create the CloudFormation template or use an existing one.
- Code should be saved in the S3 bucket, which acts as code repository.
- To call a bucket and build the stack using a template, use AWS CloudFormation.
- The services are provisioned one at a time by CloudFormation after reading files and comprehending the services that are called, their order, and connections between services.
45. What alternative tools are available to log into the cloud environment?
Ans:
- AWS CLI for Linux
- AWS CLI for Windows
- AWS CLI for Windows CMD
- AWS SDK
- Eclipse
46. What exactly is DDoS assault?
Ans:
A DDoS attack involves accessing a website and setting up several sessions in order to prevent the other authorized users from using the service. The following are native tools that can aid in shutting off DDoS attacks against AWS services:
- AWS Shield
- AWS WAF
- Amazon Route53
- Amazon CloudFront
47. Describe Amazon EC2.
Ans:
Elastic Compute Cloud, also known as the EC2, offers scalable computing power. Utilizing the Amazon EC2 frees up funds for hardware purchases, allowing for quicker application development and deployment. And can launch as many or as few virtual servers as you need, set up networking and security settings, and control storage using the Amazon EC2. It eliminates the need to forecast traffic because it may be scaled up or down to suit changes in requirements.
48. Give some non region-specific AWS services.
Ans:
- IAM
- Web Application Firewall
- Cloudfront
- Route 53
49. Describe Elastic Transcoder.
Ans:
The Elastic Transcoder, an AWS Service utility that allows for media transcoding in a cloud and precisely enables us to carry out necessary tasks, makes it simple to accomplish this. It is affordable, practical, and incredibly scalable for the companies and developers.
50. What are typical AMI design types?
Ans:
- Fully baked AMI
- Just enough baked AMI (JeOS AMI)
- Hybrid AMI
51. Define Amazon S3.
Ans:
The most widely used storage platform is Amazon S3, often known as a S3. S3 stands for Simple Storage Service. Any quantity of data may be stored and retrieved from anywhere with S3, an object storage system. Despite versatility, it is practically limitless and inexpensive because it is storage that is accessible when needed. It also provides the previously unheard-of levels of availability and durability in addition to advantages. Data management for cost reduction, access restriction, and compliance is aided by the Amazon S3.
52. How do I log in or recover from a lost key on an EC2 instance?
Ans:
- Check to see if EC2Config service is active.
- Remove instance’s root volume.
- The volume should be connected to the temporary instance.
- Make configuration file changes.
- Relaunch initial instance.
53. What is the use of Amazon Virtual Private Cloud (VPC)?
Ans:
The ideal way to connect from a local data center to the cloud resources is through a VPC. Each instance is given a private IP address that may be accessible from a data center after the data center is connected to VPC where it is located. In this manner, you can use the resources on the public cloud as if they were on a personal network.
54. How do you give users access to a particular bucket?
Ans:
To grant access, must take four procedures listed below. As follows:
- Sort the cases into categories
- Specify who has access to manage which servers
- Secure the tags
- Policies must be affixed to the IAM users
55. What security features and products are offered by VPC?
Ans:
Security groups: This controls inbound and outgoing traffic at instance level for the EC2 instances, acting as a firewall.
Network access control lists: They serve as subnet-level firewalls, regulating the inbound and outbound traffic.
Flow Logs: The inbound and outbound traffic from a network interface in the VPC is recorded in flow logs.
56. What Advantages Does AWS’ Disaster Recovery Offer?
Ans:
Businesses employ cloud computing in part to facilitate quicker IT system recovery after disaster without incurring additional costs for a second physical location. The AWS cloud provides a wide range of well-liked disaster recovery architectures, from the settings that permit rapid failover at scale to environments that handle the minor client workload data center outages.
57. What things are needed before moving to Amazon Web Services?
Ans:
Costs associated with the operations include price of infrastructure, capacity to balance supply and demand, transparency, and the other factors.
- Employment Productivity
- Cost reduction
- Operational toughness
- Business nimbleness
58. In AWS, what do RTO and RPO mean?
Ans:
The Recovery Time Objective, or RTO, is the longest period of time a company or organization is willing to wait for the recovery to be finished following an outage. RPO, or Recovery Point Objective, on other hand, is the highest amount of data loss that business is ready to take as measured in time.
59. What exactly are T2 instances?
Ans:
- The T2 Instances are designed to give CPU a moderate baseline performance as well as potential to burst to greater performance when needed by the workload.
- The T2 instances are cheap and are of General Purpose instance type. They are typically employed in the situations where CPU usage is inconsistent or infrequent for the workloads.
60. What benefits does AWS IAM offer?
Ans:
An administrator can grant the granular access to a number of users and groups using the AWS IAM. The numerous materials that have generated may need to be accessible to the different user groups and users at a different levels. Using the IAM, can establish roles with certain access levels and assign roles to people. Additionally, it provides Federated Access, which enables us to grant the access to resources to users’ applications without having to first construct IAM Roles.
61. What does AWS’s “Power User Access” mean?
Ans:
The owner of AWS resources is the same as an administrator user. The Administrator User has access to create, modify, delete, and inspect resources in addition to granting the other AWS users access.
A Power User is given Administrator Access, but not authority to manage users and permissions. Although they are not able to grant the access to other users, users with Power User Access can change, delete, view, and create resources.
62. How can speed up data transfer in Snowball?
Ans:
Yes, some specific methods for the speeding up Snowball are:
- By simply copying from a different host to the same Snowball.
- By creating a group of smaller files. This is helpful as it cuts down encryption issues.
63. What is Hypervisor?
Ans:
A Hypervisor is the type of software used to create and run virtual machines. It integrates the physical hardware resources into the platform which are distributed virtually to the each user.
64. How do you handle data archiving in AWS?
Ans:
One way to handle the data archiving in AWS is to use the Amazon S3 Glacier, which is a secure, durable, and extremely low-cost Amazon S3 storage class for data archiving and a long-term backup. With S3 Glacier, can store data at a cost that is as little as 1/10th of the one cent per gigabyte per month.
65. What is Amazon CloudFront?
Ans:
Amazon CloudFront is the content delivery network (CDN) that securely delivers data, videos, applications, and APIs to the customers globally. It integrates with the other Amazon Web Services products to give developers and businesses an easy way to distribute content to end users with the low latency, high data transfer speeds, and no minimum of usage commitment.
66. What is Amazon ECS Fargate?
Ans:
- Amazon ECS Fargate is a serverless compute engine for containers, eliminating the need to manage the underlying infrastructure.
- The EC2 launch type requires managing EC2 instances for container deployments.
67. How can you optimize costs in AWS?
Ans:
Optimizing costs in AWS involves a multi-faceted approach. Utilize services like AWS Cost Explorer to visualize and understand usage patterns, AWS Budgets for setting cost and usage alerts, and Trusted Advisor for personalized cost optimization recommendations. Employing Reserved Instances for predictable workloads and implementing resource tagging for better cost allocation are additional strategies.
68. What is AWS CloudFront’s role in enhancing content delivery and security?
Ans:
- AWS CloudFront is a content delivery network (CDN) that accelerates the delivery of web content and APIs.
- It also provides security features like DDoS protection and encryption.
69. Explain the concept of Amazon RDS Multi-AZ deployments.
Ans:
Amazon RDS Multi-AZ (Availability Zone) deployments enhance the high availability of relational database instances by automatically replicating the primary database to a standby instance in a different Availability Zone.
In the event of a planned or unplanned outage affecting the primary database, Amazon RDS will automatically promote the standby instance to the primary role, minimizing downtime and ensuring continuous database availability.
70. How does AWS WAF enhance the security of web applications?
Ans:
AWS WAF is a web application firewall service designed to protect web applications from common online threats. It allows users to create customizable web security rules that filter and monitor HTTP traffic.
By defining rules to block or allow traffic based on specific conditions, such as IP addresses or patterns in the request, AWS WAF mitigates risks associated with various web exploits, including SQL injection and cross-site scripting.
71. What is Amazon Elastic Container Registry (ECR)?
Ans:
Amazon Elastic Container Registry (ECR) is a fully managed Docker container registry that allows users to store, manage, and deploy Docker container images. ECR seamlessly integrates with container orchestration services like Amazon ECS (Elastic Container Service) and Kubernetes.
72. How can you design an architecture for disaster recovery in AWS?
Ans:
Designing an architecture for disaster recovery in AWS involves several key considerations. Implement multi-region deployments to ensure redundancy and availability. Regularly back up critical data and configurations, utilizing services like AWS Backup. Establish clear recovery point objectives (RPOs) and recovery time objectives (RTOs) for different components.
73. What is AWS Cloud9, and how does it facilitate collaborative development?
Ans:
AWS Cloud9 is a cloud-based integrated development environment (IDE) that facilitates collaborative coding and real-time collaboration among multiple developers. With Cloud9, developers can edit code, build, run, and debug applications directly in the browser.
74. Explain the purpose of AWS Step Functions.
Ans:
- AWS Step Functions is a serverless orchestration service that simplifies the coordination of multiple AWS services into serverless workflows.
- It enables users to design and execute workflows that connect and coordinate various AWS resources and services.
75. How can you securely manage access to S3 buckets in AWS?
Ans:
Securely managing access to S3 buckets involves configuring a combination of AWS Identity and Access Management (IAM) policies, bucket policies, Access Control Lists (ACLs), and enabling versioning. IAM policies define which users or roles have access to the S3 resources, while bucket policies extend control to the entire bucket. ACLs provide additional fine-grained control over individual objects within a bucket.
76. What are AWS Lambda Layers?
Ans:
AWS Lambda Layers are a way to centrally manage code and data that can be shared across multiple Lambda functions. Layers enable developers to separate common functionality or dependencies from the function code, promoting code reuse and reducing duplication.
77. What is AWS Snowball, and in what scenarios would you use it?
Ans:
AWS Snowball is a physical data transfer device designed for large-scale data migration when transferring data over the network is impractical due to factors such as large volumes or limited bandwidth.
They are used in scenarios where uploading or downloading large amounts of data over the internet would be time-consuming or cost-prohibitive.
78. How does Amazon Kinesis handle real-time data streaming and analytics?
Ans:
Amazon Kinesis is a platform designed for real-time processing and analytics of streaming data at scale. It comprises multiple services, including Kinesis Streams for ingesting and processing real-time data, Kinesis Firehose for loading streaming data into other AWS services, and Kinesis Analytics for running SQL queries on streaming data.
79. How does Amazon ElastiCache enhance the performance of web applications?
Ans:
- Amazon ElastiCache is a fully managed, in-memory caching service that enhances the performance of web applications by reducing the load on backend databases.
- ElastiCache stores frequently accessed data in memory, allowing applications to retrieve information more quickly.
80. Explain the purpose of Amazon Elastic File System (EFS) Lifecycle Management.
Ans:
Amazon Elastic File System (EFS) Lifecycle Management allows users to automatically transition files between different storage classes based on access patterns. By moving less frequently accessed data to lower-cost storage classes, such as Amazon EFS Infrequent Access (IA), users can optimize storage costs without sacrificing data availability.
81. How can you implement cross-region replication for Amazon S3 buckets?
Ans:
- Implementing cross-region replication for Amazon S3 involves enabling versioning on both the source and destination buckets and configuring replication rules.
- These rules specify which objects should be replicated, and the destination bucket can be in a different AWS region.
82. Explain the concept of Amazon EKS (Elastic Kubernetes Service).
Ans:
Amazon EKS is a fully managed Kubernetes service that simplifies the deployment, management, and scaling of containerized applications using Kubernetes. With EKS, users can run Kubernetes clusters without the operational overhead of managing the underlying infrastructure.
83. How do you design a highly available architecture using Amazon Aurora?
Ans:
Designing a highly available architecture with Amazon Aurora involves leveraging features such as Aurora Replicas, Multi-AZ deployments, and Read Replicas.
Aurora Replicas provide read scalability by replicating the primary database to one or more read-only instances. Multi-AZ deployments ensure high availability by maintaining a standby instance in a different Availability Zone.
84. What is AWS Transit Gateway, and how does it simplify network architecture?
Ans:
- AWS Transit Gateway is a service that simplifies network architecture by allowing customers to connect multiple Virtual Private Clouds (VPCs) and on-premises networks through a centralized gateway.
- It acts as a hub, enabling scalable and efficient connectivity between different network environments.
85. What is AWS Direct Load Balancer?
Ans:
AWS Network Load Balancer (NLB) is a scalable and high-performance load balancer that operates at the network layer (Layer 4) of the OSI model. It distributes incoming traffic across multiple targets, such as Amazon EC2 instances, and enhances availability and fault tolerance by ensuring that traffic is directed only to healthy instances.
86. Explain the concept of AWS Organizations.
Ans:
AWS Organizations is a service that enables the consolidation and management of multiple AWS accounts within an organization. It helps centralize billing, apply policies across accounts, and simplify the management of users and resources. Organizations allow the creation of Organizational Units (OUs) to organize accounts hierarchically, making it easier to apply policies at different levels and delegate administrative responsibilities.
87. What is AWS Key Management Service (KMS)?
Ans:
- AWS Key Management Service (KMS) is a fully managed service that allows users to create and control cryptographic keys used to encrypt their data.
- KMS enhances data security by providing a centralized and scalable key management solution.
- It enables users to create and manage keys, control access to these keys, and integrate encryption seamlessly into other AWS services.
88. How does AWS CloudFormation support infrastructure as code (IaC)?
Ans:
AWS CloudFormation is a service that allows users to define and provision AWS infrastructure as code (IaC) in a declarative language. CloudFormation templates describe the resources and dependencies needed for an application.
89. What is Amazon VPC Peering?
Ans:
- Amazon VPC Peering is a networking connection between two Amazon Virtual Private Clouds (VPCs) that allows them to communicate securely.
- It enables instances in one VPC to connect to instances in another VPC using private IP addresses.
90. What is Amazon Redshift, and how does it differ?
Ans:
Amazon Redshift is a fully managed data warehouse service designed for high-performance analysis of large datasets. It differs from traditional relational databases in terms of its architecture and optimization for analytical queries. It is particularly well-suited for data warehousing and business intelligence applications.