CommVault is a data management solution that offers backup, recovery, and archiving services for on-premises and cloud environments. It enhances data efficiency with features like deduplication and automated workflows while ensuring data availability and compliance. Its user-friendly interface makes it a popular choice for enterprises seeking robust data protection.
1. Describe the term Commvault.
Ans:
A platform for managing data called Commvault helps businesses with cloud, virtualization, disaster recovery, security, and compliance. Modules for data backup, restoration, archiving, replication, and search make up the Commvault software. Its comprehensive features enable organizations to streamline data management and ensure regulatory compliance effectively.
2. What is Simpana, the Commvault?
Ans:
Commvault’s enterprise backup software platform includes Simpana, a feature specifically designed for data backup, archiving, and reporting. Commvault unveiled Simpana, a new iteration of the deduplication process. Commvault Simpana is well-integrated with the majority of cloud vendor infrastructures and streamlines the functionality management required to enable enterprise applications.
3. What are Commvault’s salient characteristics?
Ans:
- Offers backup, recovery, archiving, and replication capabilities for diverse data environments, including on-premises and cloud.
- Supports growing data needs, making it suitable for organizations of all sizes, from small businesses to large enterprises.
- Includes encryption, access controls, and compliance tools to safeguard sensitive data and meet regulatory requirements.
- Provides an intuitive dashboard that simplifies management and monitoring of data across multiple platforms.
4. How can one achieve high availability in different ways?
Ans:
- Implementing redundant hardware, such as servers and network components, ensures that if one fails, another can take over without downtime.
- Distributing incoming traffic across multiple servers helps prevent any single server from becoming a bottleneck and improves overall availability.
- Utilizing failover clusters allows multiple servers to work together, where if one server fails, another can immediately take over its tasks.
- Deploying applications and data across multiple geographic locations protects against localized failures, such as natural disasters or network outages.
5. What is the different between CommVault HyperScale and CommVault Activate?
Ans:
| Feature | CommVault HyperScale | CommVault Activate |
|---|---|---|
| Purpose | Scale-out infrastructure for modern data protection | Data insights and governance solution |
| Primary Function | Combines software and hardware for scalable backup | Provides data analysis, management, and governance |
| Environment | Suitable for large-scale, distributed environments | Works across various data sources and environments |
| Key Capabilities | Scale-out architecture, integrated hardware, resilient backup solution | File storage optimization, sensitive data governance, eDiscovery |
6. Describe in entirely the many kinds of copies that are accessible.
Ans:
We shall have many auxiliary/secondary sorts of copies in addition to our one primary copy. The following is a list of available secondary copies: Synchronous Copy: Compiles all of the accurate data from a source copy automatically.of work, encompassing partial backups. IntelliSnap Backup Copy: Controls how long jobs created by backup jobs are kept on file. If the snapshot is granularly indexed, it also contains archived indexed data.
7. What does Commvault’s DDB mean?
Ans:
- During backups, deduplication is an effective method of transferring and storing data by identifying and removing duplicate data blocks.
- DDB Backup Subclient protects Deduplication DataBase (DDB).
- DDB Backup Subclient is automatically formed under the file system agent on the media client agent where the DDBs are hosted when a storage policy is created with deduplication enabled.
8. How is the Commvault Proxy configured?
Ans:
Configuring a Commvault Proxy involves installing the software on a suitable server and logging into the CommCell Console to add a new Proxy Server. Set up data paths, adjust resource settings, and implement security measures like user access permissions and encryption.
9. What are the most frequent and prevalent backup failures that one encounters?
Ans:
- Disruptions or slowdowns in network connectivity can prevent successful backup transfers, leading to incomplete or failed jobs.
- Running out of storage space on backup destinations can result in failed backups, often due to unexpected data growth.
- Files may become corrupted during the backup process, rendering them unusable for recovery purposes.
- Incorrect settings in backup software, such as misconfigured schedules or target locations, can lead to failed backup jobs.
10. How is the Commvault operated?
Ans:
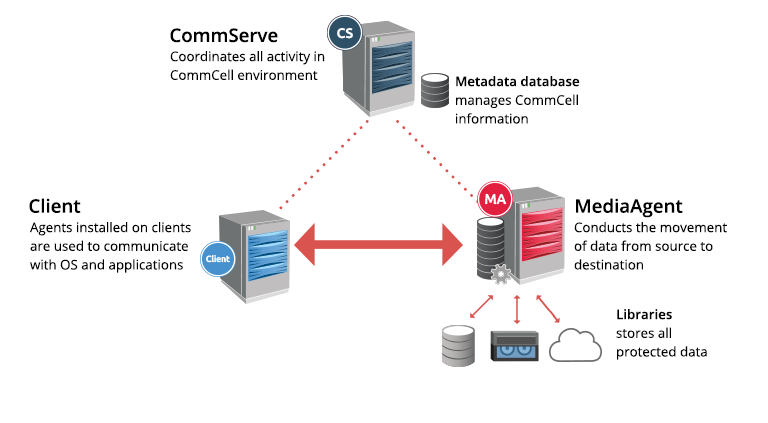
The Commvault software comprises modules designed to safeguard, analyze, replicate, and search data. These modules are seamlessly interoperable since they share a standard set of advanced capabilities and back-end services. To secure data in a consistent state, agent software that uses the application’s native APIs or operating systems is installed on the physical or virtual hosts. Then, Media is used to back up this data agent to cloud storage, tape, or disk. A centralized server known as CommServe is in charge of overseeing all data handling.
11. Describe Silo.
Ans:
A Silo refers to a system or department that operates in isolation, leading to inefficiencies and fragmented problem-solving. This isolation often results in duplicated efforts and barriers to collaboration within organizations. Breaking down silos involves fostering communication and integrating processes to enhance overall productivity and innovation. Promoting cross-functional teamwork is essential for improving organizational effectiveness.
12. What does Commvault’s hash algorithm entail?
Ans:
- Every time a block of data is read from the source, and a unique value is stored in the Commvault, a hash algorithm is employed in the deduplication process to create the block of data’s signature.
- Hashing is a technique in data security that allows for quick and secure Access by transforming data values into unique, alternate identifiers known as hashes.
13. What is the deduplicated storage policies’ default block size?
Ans:
The default block size for deduplicated storage policies in Commvault is typically 4 KB. This block size can be adjusted based on specific needs or performance requirements, but 4 KB is the standard configuration that allows for efficient deduplication and storage management. Choosing the right block size is crucial, as it can impact both storage efficiency and backup performance.
14. What portion of the deduplication ratio have we been able to keep up to date?
Ans:
This can be considered a generic wer, and the following ratio is one that we could keep:
- Roughly 90% of further information on filing system backups
- When it comes to database backups, between 70% and 95%
- The ratio of data that would be transmitted or stored without deduplication to that which is stored with deduplication is known as the deduplication ratio.
- Deduplication can significantly reduce backup size—in a typical enterprise backup scenario, by as much as 25:1.
15. From where may one obtain reports from Commvault?
Ans:
Reports from Commvault can be obtained through the CommCell Console, where users can access the “Reports” section for various built-in options, including backup status and storage usage. The Commvault Dashboard also offers real-time analytics and customized reports. For advanced reporting needs, users can integrate third-party tools or export data for analysis in applications like Excel.
16. How to access Commvault reports?
Ans:
Reports are available via the web console and cloud services portal. The Cloud Services Portal and the Web Console. For several reports on the Web Console and the Cloud Services Portal, can examine the information at the worldwide, CommCell group, and CommCell levels. These reporting options provide insights into backup status, storage utilization, and job performance, helping organizations monitor their data management effectively.
17. What distinguishes a Snapshot from a Clone primarily?
Ans:
- While a snapshot creates an initial copy and then makes further changes to it, cloning is just the process of generating a copy of something.
- Cloning and snapshotting are regarded as effective disaster recovery strategies.
- With a few exceptions, every clone is an identical copy of the original elements, like the compute shape and the instance name that specify or override.
18. Describe IRM and its operation.
Ans:
The IntelliSnap Recovery Manager, or IRM for short, is a tool that allows smaller environments to perform physical storage snapshots right into a recovery or protection process. It provides application support, centralized configuration, quick and straightforward Snap backups, and more. The steps below illustrate how IRM functions:
- The Intellisnap job from the Commcell console can be scheduled or started on demand to start a snapshot job.
- When a snapshot job is launched to take a content snapshot, it accesses the array.
- The snapshot is unmounted after it has been mounted on the source computer for post-snap activities.
19. What Constitutes the Building Blocks of Deduplication?
Ans:
Commvault Software uses a building block method to handle data. Regardless of the kind or source of the data, a building block consists of a server and storage combined for data protection. Large volumes of data can be protected with deduplication building blocks, which also improve scalability and speed backups. Twenty. Describe DDB seeding. DDB seeding is a preset process that enables the transfer of an initial baseline backup between two sites using a detachable disk drive.
20. How does IntelliSnap Backup’s Backup Copy function?
Ans:
IntelliSnap backup procedures store all changed blocks (obtained through Changed Block Tracking incremental backups) in an XML file that is then uploaded to the Index Server. The backup process uses file system APIs to read the data. The snapshot data stores are mounted to the VSA proxy machine during backup copy operations. This approach optimizes the backup process by minimizing data transfer and enhancing the efficiency of incremental backups.
21. What is CDR, or ContinuousDataReplicator?
Ans:
CDR, or ContinuousDataReplicator, duplicates data from one place to another. It offers support for file systems and application data, as well as data protection and recovery for all kinds of data. To achieve this in almost real-time, every file write activity—including the creation of new files and modifications to already-existing files—is recorded in a replication log on the source machine.
22. Is Commvault a software designed for enterprises?
Ans:
- The software is indeed enterprise-level. An enterprise-level data platform called Commvault includes modules for data backup, recovery, archiving, replication, and search.
- It is constructed entirely on a single platform with a single code base.
- The Commvault software is easy to use; it is constructed from the ground up and contains many modules that can be utilized separately according to the situation.
23. How is backup using Commvault done?
Ans:
Commvault offers the most effective way for businesses to back up and restore data from standard operating systems, databases, and applications. Commvault backup also makes data transfer from production systems to protected environments easier by interacting with programs or files using agents. This seamless integration ensures data integrity and accessibility, enabling organizations to efficiently manage their backup and recovery processes.
24. Which backup failures are frequent and prevalent enough that most people encounter them?
Ans:
Here are a few of the more frequent or serious backup problems that have been reported:
- Problems with network communication
- Media agent offline; destination disk library full; data path offline; potential maintenance shutdown of client services; failure of the VSS snapshot backup
25. How does IntelliSnap Backup’s Backup Copy function?
Ans:
Using the backup copy process, can copy data snapshots to any type of media. The metadata for the snap backups is stored in the primary snapshot, and the primary snapshot data is copied to the media linked to the primary copy while the backup copy operation is underway. There are two configuration options for the backup copy: Run an inline backup copy while the IntelliSnap backup task is running. Run the offline backup copy separately from the IntelliSnap backup job.
26. How is a VMware backup done?
Ans:
- Using the Commcell console, navigate to the client computers and choose Virtualization-client->virtual server->VMware->backup-set.
- Alright, now Select a subclient, then select Backup.
- Decide on the type of Backup: Complete, Gradual, Differential, Synthetic
- Select Advanced to change the default settings or provide advanced options.
- Select Immediate to start a job right away, or select Configure to specify a backup schedule, and then click OK.
- To monitor the job’s progress, click Home->Job Controller.
27. Which kinds of REPORT modes are compatible with VMware?
Ans:
Depending on the VSA proxy being used, as well as the virtual machines being backed up or restored, trunk modes are automatically chosen for backups and restores. These modes optimize performance by selecting the most efficient data transfer methods based on the specific environment and workload. By dynamically adjusting trunk modes, Commvault ensures reliable and speedy backup and restore operations while minimizing resource consumption.
28. Enumerate every daily task performed by a backup administrator.
Ans:
The backup administrator must first ensure that all of the jobs are scheduled and executed according to their instructions. If not, they will need to review the tasks, identify the issue, and fix it. Additionally, they need to participate in some of the following health checks must be performed. Verify that the media agent is not in offline mode by looking for it. Consistently monitor the amount of free space or remaining space in the disk libraries
29. Explain the infrastructure previously worked on.
Ans:
Since this is a question that may be answered in real time based on the experience that is accessible, it should be an honest response to the interviewer. An enterprise-level data platform called Commvault includes modules for data backup, recovery, archiving, replication, and search. It is constructed from the ground up using a single code base and platform.
30. What will occur when the proxy server does backup copy operations?
Ans:
The following tasks are carried out while the backup copy processes are underway:
- The ESX server, which is just used for the snap mount, is mounted with the information snapshot.
- After the snap is mounted, its contents are processed and read as if it were a file system.
- The primary copy of the storage policy is used for the file system backup.
- The snapshot will be unmounted after the backup copy procedure is completed.
31. In the context of application software, what is Commvault?
Ans:
Commvault is a data protection solution for medium-sized and large businesses. It is in high demand right now. It has an incredibly adaptable web user interface for managing an application’s data protection and disaster recovery tasks. Employing default, simplified procedures and configuration parameters reduces the amount of time needed to complete primary data recovery and protection tasks. Using Commvault’s command center, we can identify the items we wish to safeguard and initiate, monitor, and manage backups and restores.
33. What are Commvault’s salient characteristics?
Ans:
- Offers Backup: Backups safeguard files, databases, endpoints, virtual machines, apps (including cloud-based ones), and virtual machines. The following are some advantages of this:
- Personalised timetables with policy-driven automation, tracking, and monitoring to meet any SLA additionally
- Offers recuperation: There is guaranteed recovery for virtual machines, programs (including cloud-based ones), databases, endpoints, and files. The following are some advantages of this:
- Facilitates migration: It is possible to migrate workloads between clouds or from on-premises to the cloud.
35. What kinds of trailing edge modes does VMware support?
Ans:
- Storage Area Networks (SAN): To access virtual discs, a physical computer with Access to an iSCSI or Fibre Channel SAN is required for the installation of VMware Backup Host.
- Local Area Network (LAN): In this mode, the VMware Backup Host receives data from storage that the ESX/ESXi host reads and transmits across a network. A LAN is necessary for this type of port, in contrast to SAN ports.
36. Compose an inventory of all the everyday responsibilities of a backup administrator.
Ans:
A backup administrator’s responsibilities include monitoring backup job statuses, managing schedules, and performing data integrity checks to ensure recoverability. They troubleshoot failures, oversee storage management, and maintain documentation while ensuring security through encryption and access controls. They provide user support, collaborate with IT teams, and educate staff on backup policies and best practices.
37. Which backup failures are the most frequent and common ones that people experience?
Ans:
- Problems with network communication.
- There is a complete destination disk library.
- It’s possible that client services will stop for maintenance.
- Offline media agent.
- Failure of the VSS snapshot backup.
- Offline data route.
38. Define IRM CommCell, CommCell Console, MediaAgent, and IRM Clients in Commvault.
Ans:
- IRM CommCell: A centralized management framework that oversees all backup and recovery operations within an organization’s environment.
- CommCell Console: A graphical user interface (GUI) used to manage the IRM CommCell environment. It allows administrators to configure settings, monitor jobs, and manage backup policies and storage.
- MediaAgent: A component responsible for handling data movement between the source systems and storage locations.
- IRM Clients: They communicate with the CommServe and MediaAgent to perform data protection tasks, such as backups and restores, based on defined policies.
39. What does snapshot mean ? What are the benefits of owning pictures?
Ans:
A snapshot is a “picture” of the file system server taken at a specific moment in time. In situations when storage capacity is limited, new snapshots usually replace older ones. Snapshots are helpful in many different contexts, such as quick data recovery and system backups, allowing users to restore systems to a previous state easily. They can be used for testing and development purposes, enabling developers to work with data from specific points in time without impacting the live environment.
40. Describe the distinctions between a backup and a snapshot.
Ans:
- Backup: A copy of a file or other data set is referred to as a backup. A backup makes a copy of the files when it begins, and these copies are kept in a separate location. The duration of a backup can vary based on the volume of data being backed up, and it is essential for recovery in case of data loss.
- Snapshot: A snapshot can take a “picture” of the file system on the server at any moment. This photo captures the server as it was at that exact moment, allowing for quick restoration to that state without the need for a full backup process.
41. If a job has been encrypted, how can one tell, and if not, how?
Ans:
- To determine if a job has been encrypted, one can check the job’s properties or settings within the backup management console, where encryption status is typically displayed.
- Reviewing logs associated with the job may provide information about the encryption method used or confirm whether encryption was applied.
- If a job has not been encrypted, the properties will indicate that encryption is disabled, and the logs will not reference any encryption process.
- The data being backed up can be inspected, unencrypted data will be in its original, readable format, while encrypted data will appear scrambled or unreadable.
42. How much of a performance loss is reasonable given encryption?
Ans:
Software encryption uses a lot of CPU power, which might cause a 40% to 50% slowdown in Backup or additional copy speed. Since the deduplication process eliminates all duplicate data and only encrypts data blocks that are unique throughout the whole deduplication database, the anticipated performance hit does not apply to deduplicated data. Consequently, there will be little effect of deduplicated data on performance.
43. In the case of an emergency, how are keys stored and restored?
Ans:
The CommServe Database is routinely scheduled to be exported and backed up, which provides disaster recovery protection (DR Backup activity). A reliable third party can supply a private key backup, guaranteeing that the key can be found and transactions created in the event of a tragedy. This ensures that data integrity is maintained and recovery processes can be executed swiftly and effectively in case of a failure.
44. Who has the encryption keys in their possession?
Ans:
- Nobody is able to access the encryption keys.
- These keys are stored in the CommServe database and are encrypted using the client’s RSA public key.
- The client’s RSA private key is encrypted using a user-supplied passphrase or one that is pre-installed, depending on the settings.
- The user-inputted Pass Phrase is not retained. Only authorized users (as defined by user management) may set and modify these passphrases.
- One never writes down passphrases in plain text.
45.Where are Passphrases kept in Commvault?
Ans:
Passwords are not kept on file. Every recovery requires the user to enter the passphrase explicitly. However, by creating and exporting a file with the client’s computer’s encrypted passphrase to a specified directory on a different machine, the system is able to retrieve the client’s data to that (and only that) machine. This process enhances security by ensuring that only authorized devices can access the encrypted data.
46. What happens when users perform a backup of a Deduplication Database (DDB)?
Ans:
- All contact with the active DDB is suspended for a brief period. The information in memory is committed to memory in order to guarantee that the DDB is in a dormant state.
- The DDB procedure creates a volume snapshot using LVM (Linux) or VSS (Windows) snapshots.
- VERITAS Volume Manager (VxVM) and the file systems Extended 3 File System (ext3) are also supported by the Linux operating system.
- When the snapshot is created, all communication with the DDB is restored, and the DDB is automatically backed up from that snapshot.
47. Describe the terms storage policy, job manager, backup set, subclient, collect files in relation to Commvault.
Ans:
- Storage Policy: A storage policy in Commvault defines the rules for how data is stored, including the destination storage location, retention periods, and data protection methods.
- Job Manager: The Job Manager is a component that oversees the execution of backup and recovery jobs in Commvault.
- Backup Set: It typically contains a collection of files or databases that need to be protected, allowing for organized management and execution of backup jobs.
- Subclient: A subclient is a specific configuration within a backup set that defines a subset of data to be backed up.
- Collect Files: The “collect files” feature in Commvault refers to the process of gathering files or data from specified sources for backup.
48. What distinguishes a virtual machine clone from a snapshot?
Ans:
To preserve the present state of the virtual machine, a snapshot copies the disk file. It serves as a fallback system. If needed to store a virtual machine’s configuration may return to it later in case something goes wrong, create a snapshot. Conversely, a clone is a replica of the virtual machine. If needed to build a new virtual computer that can operate independently, only choice is to clone it.
49. Does Commvault encryption require a Certificate Authority?
Ans:
Asymmetric cryptography is the only situation in which separate keys are utilized for both encryptions and decryption. All of our encryption is symmetric, meaning that the same key is used for both encryption and decryption. Therefore, neither a certificate nor a certificate authority is required. Asymmetric cryptography is used when data is being sent over insecure channels and the identities of the parties involved are unknown.
50. Can encryption affect compression while writing for the media?
Ans:
- Yes, when encryption is used for backup procedures, data is actually randomized.
- This means that using compression techniques to compress encrypted data will have less impact.
- As a result, when this data is written to the medium, the compression ratio will clearly change.
- For instance, when encryption is applied, a tape that was originally compressed to 190GB and had a native capacity of 110GB could only write 124GB to the same tape.
51. Does enabling encryption for both backup and offline/auxiliary copy mean that the data is encrypted twice?
Ans:
Enabling encryption for both backup and offline/auxiliary copy does not necessarily mean the data is encrypted twice. Instead, it means that the data is encrypted during both the initial backup process and again during the auxiliary copy operation. However, the encryption processes are typically independent, and the same encrypted data may be used for both, rather than applying two separate encryption layers.
52. How are keys kept in the CommServe database?
Ans:
The client’s RSA public key is used to encrypt data encryption keys before they are kept in the database. The client’s RSA private key is encrypted using a user-supplied passphrase or one that is pre-installed, depending on the settings. The software generates a fresh key for every data stream (archive file). The program encrypts the keys using the storage policy copy’s public key and then saves the encrypted keys.
53. What does the term “different kinds of copies” mean in the context of Commvault?
Ans:
- Selective Copy: From a source copy, which may be primary or synchronous, can copy specific complete backup jobs. Tape rotation can be done more effectively with a selective copy.
- Inline copy: Both the Primary and Secondary copies are written to storage during the Backup Phase. If there is not enough space on the secondary storage, backups will not work.
- Synchronous copy: This type of copy copies every piece of information from the primary.
54. What is the difference between a dash complete and an artificial full backup?
Ans:
Synthetic complete Backup combines all the incremental backups added to the previous complete Backup to make it a complete backup. In this case, the server’s (client’s computer and network) utilization is likewise appallingly low in comparison to normal full. In contrast, a full backup could be an exact copy taken from the server. In order to produce a complete backup, Dash also copies the unique blocks of the de-duplicated knowledge and updates the DDB and index files.
55. How is the Proxy Server being used?
Ans:
- The load on the assembly server can be reduced by using a proxy server. The backup copy procedure uses the proxy to transform the snap to backup media.
- To take a picture, Access to the storage array is required.
- There is no counting on the photo.
56. How to measure daily activities as the backup administrator?
Ans:
The first step is to watch the jobs running in the job controller and make sure that there is no reason why any work should be left unfinished or in the waiting state. Check for queued and suspended jobs as well. Examine the job to see if there are any delays, and look for any roles that require more than 24 hours of work. Many of the medical tasks are measured below square measure.
57. How does Commvault protect data?
Ans:
Installing agent software on physical or virtual hosts protects data by maintaining consistency using native operating systems or application APIs. On the client, the agent program processes production data. Machines and stored on disk, tape, or cloud storage via a data manager called the MediaAgent. Administrators can oversee all data management operations within the system via a central user interface, which is monitored by a centralized server called the CommServe. End users can use mobile devices and web browsers to access protected data.
58. What are Commvault’s main characteristics?
Ans:
- Offers backup, recovery, archiving, and disaster recovery for various data sources, including physical, virtual, and cloud environments.
- Supports small to large enterprise environments, allowing businesses to scale their data protection solutions as needed.
- Automates backup processes and workflows to enhance efficiency and reduce manual intervention.
- Provides flexible recovery options, including file-level, application-level, and full-system recovery, ensuring quick access to critical data.
- Implements robust security features, including encryption, access controls, and compliance reporting to protect sensitive data.
59. What is the CommVault Tool all about?
Ans:
A data and executives arrangement called CommVault provides for the management and security of a company’s information. CommVault is a publicly listed software company based in the United States that was founded in 1988. Data backup and recovery, as well as cloud administration, are applications for this product. Many businesses utilize the CommVault as a bulwark for information recovery purposes, and this software solution updates the data security for the expensive NetApp storage portfolio.
60. How is the Commvault Proxy configured?
Ans:
To set up the new client’s Commvault Proxy, take the actions listed below:
- Step 1: From the Commvault browser, right-click on the client PC that will be used as a proxy and choose Properties.
- Step 2: In the properties dialog box, click the Network button, then check the box next to Configure Firewall Settings.
- Step 3: Select “This computer is in DMZ and will work as a proxy checkbox” by clicking on the settings tab.
- Step 4: Choose Add from the Incoming Connections tab.
- Step 5: From the list, choose the CommServe_client_name.
61. Describe the surroundings of the Commcell.
Ans:
- The logical collection of all the software elements that transfer, manage, and safeguard data and information is called a Commcell environment.
- It has Clients, MediaAgent, and CommServe hosts in it.
- The primary management element that plans and carries out every Commcell function is called CommServe.
- In the Commcell context, MediaAgent is a data transmission manager that manages data storage libraries and permits high-performance data transfer.
62. How is the Commvault operated?
Ans:
The Commvault software comprises modules designed to safeguard, analyze, replicate, and search data. These modules are seamlessly interoperable since they share a standard set of advanced capabilities and back-end services. To secure data in a consistent state, agent software that uses the application’s native APIs or operating systems is installed on the physical or virtual hosts. After that, the Media Agent backs up this data to a disk, tape, or cloud storage account.
63. Describe the different approaches to High Availability?
Ans:
- Implementing redundant components, such as servers, network connections, and power supplies, ensures that if one component fails, others can take over, maintaining system functionality.
- Distributing workloads across multiple servers helps prevent any single server from becoming a bottleneck. Load balancers monitor server health and direct traffic to available resources.
- Grouping multiple servers into a cluster allows them to work together. If one server in the cluster fails, another can take over its workload, ensuring continuous service availability.
64. What does CommVault’s storage policy entail?
Ans:
Customer reinforcement and storage pl usually are the foundations of the storage strategy. It describes the types of data that should be stored as well as the data that should be stored. In addition, the data is kept in a secure setting. Storage regulations serve as a conduit for backup and restoration procedures. A storage policy’s primary purpose is to map data from its original location to a physical place.
65. What are the different Copies that CommVault has available?
Ans:
- A selective copy allows the replication of a specific set of data from a source copy.
- The primary copy, asynchronous copy, or accompanying copy can all be the source.
- Primary data from the source copy is included in the synchronous copy.
- This copy phase keeps both the auxiliary and necessary duplicates to access in the reinforcement phase.
66. What is Silo about?
Ans:
- A group of disk volume folders connected to the Deduplication Database is called a silo.
- It includes the deduplicated data that has been stored on disk.
- A building used to store bulk goods is called a silo.
- Grain and other goods are more frequently stored in bulk in silos.
- Tower silos, bunker silos, bag silos, and silage heaps are the three types of silos.
67. What Does Commvault’s Hash Algorithm Mean?
Ans:
Every time a square of data is viewed from the source during the deduplication process in the Commvault, a hash algorithm is applied, and an exceptional mark is made for the square. Of data by applying a hash algorithm. A centralized server known as CommServe is in charge of overseeing all data handling. This ensures efficient storage management and facilitates quick data retrieval when needed.
68. What is the deduplicated storage policies’ default block size?
Ans:
128 KB is the standard block size for deduplicated storage policies, while the default block size for write operations is 64 KB. Block size, as it relates to mount pathways, is the buffer size utilized for each write operation. (When the disk is formatted, the file system allocation unit size is determined.) Proper configuration of block sizes can significantly impact performance and storage efficiency.
69. What portion of the deduplication ratio have we been able to keep up to date?
Ans:
This can be generalized war, and the ratios we could keep are as follows: • Between 70% and 95% for database backups; around 90% or more for filing systems backups; the deduplication ratio is the ratio of the amount of data that is stored with deduplication compared to that which is transmitted or stored without it. Deduplication can significantly reduce backup size—in a typical enterprise backup scenario, by as much as 25:1.
70. Where are the reports in Commvault available for download?
Ans:
- Via the web console, can download and see the reports in Commvault.
- Select Reports from the navigation window. The page for reports loads.
- Click Actions > Connect to store at the top of the page. The page for the Commvault Store loads.
- Click Install next to the report to install a new one.
- Update the Reports section of the Command Center.
71. How does CommVault define IRM?
Ans:
Hardware storage operations snapshots are implemented into recovery procedures with IntelliSnap Recovery Manager (IRM) without affecting the server in use. Additionally, it provides a uniform setup wizard that allows for configuring storage media, policies, and other elements. This streamlined process enhances efficiency and reduces the complexity of managing backup environments.
72. Enumerate the different kinds of backups that CommVault has to offer.
Ans:
CommVault replaces productive Backup and brings back all of a company’s functionality. The several backup kinds that are offered in CommVault are as follows: Complete, incremental, differential, synthetic, full, and selective online backups are among the options available. Block-Level Redundancy
73. What standard backup failures do most CommVault clients encounter?
Ans:
- Client Services may be suspended for upkeep.
- Offline data path
- Offline media agent
- Problems with network communication
- Issues with VSS snapshot backups
- Tell about the destination disk library full
74. Explain to us what Intellisnap is.
Ans:
Using Intellisnap reinforcement, a point-in-time snapshot of the data is created. This is typically used to make backups of real-time data and then carry out real-time operations. IntelliSnap backup makes a snapshot of the data at a specific moment in time for use in a variety of data protection procedures. Together with hardware and software snapshot engines, IntelliSnap backup provides snapshot functionality for data protection operations.
75. Tell the difference between a CommVault snapshot and a clone.
Ans:
Whereas a snapshot makes an underlying copy and then rolls out, improving things, a clone duplicates something. Cloning and snapshotting are recognized as legitimate disaster recovery techniques. An instantaneous picture of a service instance is called a snapshot. To make many clones of an example, use snapshots. With the exception of a few properties that can change or override, like the instance name and compute shape
76. How is each clone identical to the original, and is Commvault for enterprises?
Ans:
- Commvault software is easy to use; it is designed from scratch and contains many modules that may be used independently depending on the necessity.
- Yes, it is enterprise-level software.
- An enterprise-level data platform called Commvault includes modules for data backup, recovery, archiving, replication, and search. It is constructed entirely on a single platform with a single uniform code
77. What are the primary elements that comprise the CommCell Environment?
Ans:
- Communicate: This is the crucial management element that handles all CommCell data processing. Assignments.
- Media Agent: This is a framework for information transmission management that manages information storage packages and enables high-level information development execution.
- Client: A client is an organized team of information agents that carries out tasks such as data protection, management, and information association movement.
78. What are the building blocks of deduplication?
Ans:
Commvault programming uses a structural block method to process information for executives. A structural block is a combination of labor and capability that guarantees informative indices regardless of the type or source of information. With the help of Building Blocks, will be able to safeguard massive amounts of data with minimal foundation, improved flexibility, and more substantial reinforcements.
79. What is CommVault Appliances?
Ans:
The Commvault HyperScale Appliance offers solutions for data safety and smooth scaling, with scaling as its primary purpose. It features cloud-like economics and provides a storage architecture that includes frameworks for reporting, automation, data protection, indexing, and storage. This makes it a versatile choice for managing large volumes of data efficiently.
80. What does Commvault’s scalability mean?
Ans:
- Applications expand throughout time, and in order to safeguard the dataset quickly and effectively while preserving an economy of scale that allows the system to continue producing business value, a data management solution must adjust to the rate of change.
- Out of the box, Commvault supports 5,000 servers or laptops by default. Get in touch with software vendor to request an increase if require more than 5,000 clients.
- The software vendor will request diagnostic reports from order to assess an environment when a request is made.
81. What Does Commvault Automation Mean?
Ans:
Automation is encouraged by the cloud not just because the infrastructure may be programmed but also because repeatable activities lower operating costs, increase robustness by using well-known configurations, and enable larger scales. Using the Commvault interface, may execute automated test cases thanks to a feature called automation.
82. What does a cross-join mean?
Ans:
A cross-join is a JOIN that yields the cross-product of two tables. It is also referred to as a cartesian join. A cross-join creates a new table containing a row for every conceivable combination of rows from the two input tables by matching every row from the first table with every row from the second table. Assume developing an ML model for a neural network that attempted to estimate the likelihood that a buyer would purchase a Commvault item.
83. Define Inform the Commcell setting.
Ans:
- The practical collection of all the software elements that protect, transfer, and manage actual data is known as a Commcell environment. It has Clients, MediaAgent, and CommServe hosts in it.
- CommVault offers press sharing and data protection for PCs, laptops, and servers from any place.
- It protects distant and mobile data while simplifying management with a single solution and low total cost.
84. Describe the term Silo.
Ans:
In data management, a “silo” refers to an independent system or repository that is not easily integrated with others. This often leads to inefficiencies, data duplication, and difficulties in sharing information across departments. Silos hinder collaboration and create barriers to obtaining a comprehensive view of data. Breaking down these silos is crucial for improving accessibility and fostering a unified data management approach.
85. What are the inbound Commvault hash algorithm and SHA algorithm?
Ans:
- Inbound Commvault Hash Algorithm: This algorithm generates a unique hash value for data being backed up, allowing Commvault to identify and deduplicate data efficiently. It ensures that any changes in the data result in a different hash value, thus maintaining data integrity.
- SHA Algorithm: SHA is a family of cryptographic hash functions designed to produce a fixed-size hash value from input data of any size. Common variants include SHA-1, SHA-256, and SHA-512. These algorithms are used for verifying data integrity and secure transmission, detecting any alterations by comparing hash values.
86. What is the deduplicated data policy’s default block size?
Ans:
128 KB is the default block size for deduplicated storage policies, while the default for write operations is 64 KB. Block size, as it relates to mount pathways, is the buffer size utilized for each write operation. (The unit for allocating file systems) When the volume is formatted, the size is determined. Proper configuration of these block sizes can significantly impact performance and storage efficiency.
87. What portion of the deduplication ratio have we been able to maintain thus far?
Ans:
The ratio of data that would be transmitted or stored without deduplication to that which is stored with deduplication is known as the deduplication ratio. Deduplication can significantly reduce backup size—in a typical enterprise backup scenario, by as much as 25:1. This reduction not only saves storage space but also enhances data transfer efficiency and reduces backup times.
88. Where to access reports and downloads in Commvault?
Ans:
- Via the Woven Console, can access and examine the Berichtswesen in PDF format in Commvault.
- Open the Web Console and select Reports after logging in. The page for reports loads.
- Select Store from the navigation window. The page for the Commvault Store loads.
- Next to the report, click to install a new one.
- Download. Installing the report script on the Web Console requires downloading it.
89. How to view reports in Commvault?
Ans:
Reports are accessible through the web console and Cloud Services Portal. They are available via the CommCell Console, Cloud Services Portal, Web Console, and Command Center. The Commvault installation automatically includes a number of reports, providing valuable insights into data management activities. Additionally, users can customize and create reports to meet specific needs.
90. What is the primary distinction between a clone and a snapshot?
Ans:
An instantaneous picture of a service instance is called a snapshot. To quickly generate several clones of an example, use snapshots. With the exception of a few parameters that can change or override, such as the instance name and compute shape, every clone is an exact duplicate of the original instance. This capability enhances flexibility and efficiency in managing service instances within cloud environments.
91. How does IRM actually operate?
Ans:
- The IntelliSnap Restoration Manager, or IRM for short, is a tool that allows physical storage snapshots to be easily imported into a recovery or protection edit for smaller environments.
- It provides application support, centralized configuration, quick and straightforward Snap backups, and more.
- A proactive set of corporate-wide procedures known as integrated risk management, or IRM, helps shape an organization’s risk tolerance profile, security, and strategic choices.
92. What Constitutes the Building Blocks of Deduplication?
Ans:
With Deduplication Building Stops, can safeguard vast volumes of data while utilizing less infrastructure, improving scalability, and achieving significantly faster backups. A building block is a server and storage combo that offers a modular design for managing data. Considering the environment, storage needs, and the volume of production data, this building block guide shows how to select the appropriate number of deduplication nodes.
93. What is seeding a DDB?
Ans:
- DDB seeding is a preset process that uses a detachable disk drive to enable the transfer of the first Backup between the twin sites.
- Using a readily available detachable disk drive, like a USB drive, can transfer the first baseline backup between two sites using a predetermined method called DDB Seeding.
- The CommCell Console allows to initiate this operation manually.
94. Whose Continuous DataReplicator (CDR) is it?
Ans:
Data is replicated from a source computer to a destination computer using ContinuousDataReplicator (CDR). This is accomplished in almost real-time by recording every file write operation in a replication log, including newly created and modified files in the source computer. This ensures that the destination remains synchronized with the source, minimizing data loss and downtime.