Our Azure Administrator Interview Questions & Answers provides a comprehensive overview tailored for individuals preparing for Azure Administrator roles. Curated by experts, it covers a wide range of topics essential for Azure administration, including virtual machine management, network configuration, identity management with Azure Active Directory, monitoring and logging using Azure Monitor, security implementation with Azure Security Center, and automation through PowerShell scripting. Additionally, it includes real-time case study questions and frequently asked questions, offering valuable insights and practical guidance to navigate Azure administration interviews successfully.
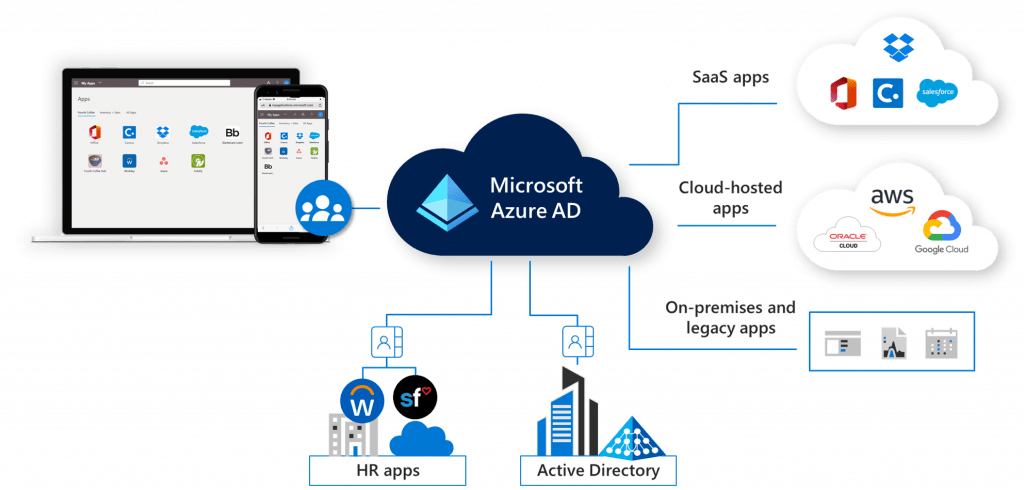
1. What is Azure Active Directory (Azure AD)?
Ans:
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service, which helps organizations manage and secure access to applications, data, and resources both in the cloud and on-premises. Azure AD enables administrators to control who has access to what through authentication and authorization mechanisms, supporting features like Multi-Factor Authentication (MFA), conditional access policies, and single sign-on (SSO) across thousands of cloud applications.
2. What are Azure Availability Zones?
Ans:
High-availability Azure Availability Zones shield data and apps from data center outages. In order to provide redundancy and high availability, they are physically distinct sites inside an Azure region, each with its power, cooling, and networking. Customers may obtain improved fault tolerance and isolation by architecting applications across several Availability Zones. The other zones keep running even if one has a failure, reducing downtime and data loss. Applications that are vital and need a high uptime should use this configuration.
3. What is Azure Blob Storage?
Ans:
Huge amounts of unstructured data, like as binary or text data, may be stored with Azure Blob Storage, a scalable object storage solution. Streaming music and video, writing to log files, storing data for disaster recovery, backup, and archiving, and delivering documents or pictures directly to a browser are just a few of the many uses for it. Blob Storage supports three types of blobs: block blobs for text and binary data, page blobs for VHD files, and append blobs for log files.
4. What are Azure Service Principals and Managed Identities?
Ans:
- Azure Service Principals and Managed Identities are both concepts related to managing identities for applications and services in Azure. This allows applications to authenticate against Azure services using an identity without embedding user credentials.
- Managed Identities provide an identity for Azure resources, automatically managed by Azure, to authenticate to services that support Azure AD authentication without needing to manage credentials.
- Managed Identities simplify the security model by automatically handling the management of credentials, making them ideal for secure access to Azure services without the overhead of credential management.
5. How do you secure data in Azure against unauthorized access?
Ans:
To secure data in Azure against unauthorized access, implement a combination of Azure Active Directory for identity and access management, use role-based access control (RBAC) to ensure users have only the access they need, encrypt data at rest using Azure Storage Service Encryption or Azure Disk Encryption, and encrypt data in transit with SSL/TLS. Additionally, use Azure Network Security Groups and Azure Firewall to control inbound and outbound traffic to resources, and regularly audit access and activities using Azure Monitor and Azure Security Center.
6. Explain the difference between Azure Backup and Azure Site Recovery.
Ans:
Azure Backup is a service that provides secure, one-click backup solutions for SQL Server, Azure Virtual Machines, and on-premises VMware machines. It’s designed for data protection, allowing you to recover files, folders, and entire VMs. Azure Site Recovery, on the other hand, is more focused on business continuity and disaster recovery (BCDR). It ensures minimal downtime of your applications by orchestrating replication, failover, and recovery of VMs and physical servers across Azure regions or between an on-premises data center and Azure.
7. What are the benefits of using Azure Virtual Machines?
Ans:
Azure Virtual Machines (VMs) offer several benefits, including flexibility in choosing the operating system (Windows or Linux) and the ability to customize configurations based on the workload’s requirements. VMs provide scalability, allowing you to easily adjust resources like CPU, memory, and storage. They support a wide range of computing solutions, from development and testing environments to high-performance computing and big data applications. VMs offer a cost-effective option with the ability to use spot instances for non-critical workloads.
8. Describe Azure Logic Apps and their use cases.
Ans:
It allows the visual designer to model and automate workflows without writing code. Use cases include:
- Automating business processes like order fulfillment.
- File synchronization.
- Data collection from social media.
- Integrating systems and services by connecting APIs.
Logic Apps supports the connectors for popular services like Office 365, Twitter, Dropbox, and many more, facilitating easy data exchange and process automation.
9. How does Azure manage virtual networks and provide security?
Ans:
Azure manages virtual networks (VNets) by providing an isolated and highly secure environment to run VMs and applications. Can segment VNets into subnets, apply routing rules, and use Network Security Groups (NSGs) to filter network traffic to and from resources. Additionally, Azure provides Virtual Network Peering for secure connectivity between VNets, including those across Azure regions. Azure also offers services are Azure Bastion for secure and seamless RDP/SSH connectivity to your VMs, eliminating the need for public IP addresses and reducing exposure to threats.
10. What are Azure Kubernetes Service (AKS) and its advantages?
Ans:
- AKS offers integrated continuous integration and continuous delivery (CI/CD) experiences, enterprise-grade security and governance, and seamless integration with Azure services for monitoring, networking, and storage.
- It provides auto-scaling, self-healing, and load balancing, reducing the complexity and operational overhead of managing a Kubernetes environment.
- AKS accelerates application development and deployment, making it ideal for microservices architectures.
11. Explain the concept of Azure Functions and its use cases.
Ans:
With Azure Functions, serverless computing is possible without the need to explicitly deploy Infrastructure, enabling the execution of event-triggered code. Many languages are supported, such as Python, JavaScript, C#, Java, and PowerShell. Azure Function use cases include:
- Managing webhooks for GitHub operations.
- Processing orders in e-commerce websites.
- Automating administrative chores.
- Interacting with Azure services or other third-party services for data processing.
12. How do you monitor and manage Azure resources?
Ans:
To monitor and manage Azure resources, use Azure Monitor and Azure Service Health for comprehensive monitoring, diagnostics, and analytics to understand system performance and health. Azure Monitor collects, analyzes, and acts on telemetry data from Azure and on-premises environments, helping to maximize performance and availability while proactively identifying problems. Azure Automation and Azure Policy provide ways to automate tasks and enforce standards across your resources, ensuring compliance with corporate policies.
13. How does Azure Active Directory (Azure AD) differ from Active Directory Domain Services (AD DS)?
Ans:
| Aspect | |||
| Deployment | Cloud-based service provided by Microsoft | On-premises directory service | |
| Authentication | Provides identity and access management for cloud services | Manages authentication and authorization on-premises | |
| Integration | Integrates with various cloud services and applications | Integrates with on-premises Windows environments | |
| Access Control | Offers granular access control and role-based access | Provides access control within the on-premises network | |
| Device Management | Supports device registration and management for users | Focuses on managing devices within the local network |
14. Explain the process of migrating an on-premises virtual machine to Azure.
Ans:
- Migrating an on-premises virtual machine (VM) to Azure involves several key steps. Initially, assess the on-premises environment using tools like Azure Migrate to understand dependencies and evaluate the suitability for migration.
- Next, prepare Azure for the VM by setting up a resource group, virtual network, and storage account.
- Then, replicate the VM using Azure Site Recovery or a similar tool, which involves configuring the source VM, setting up replication, and initiating the replication process.
- After testing the VM in Azure to ensure it operates correctly, you can then complete the migration by cutting over to the Azure VM. Post-migration, optimize resources based on performance and cost.
15. How do you implement a hybrid cloud with Azure?
Ans:
Implementing a hybrid cloud with Azure typically involves integrating on-premises data centers with Azure services, maintaining some resources on-premises while leveraging Azure’s cloud capabilities for others. This can be achieved through several Azure services: The process involves:
- Planning and identifying which workloads to move to the cloud and which to keep on-premises.
- Ensuring network connectivity.
- Setting up identity and access management through Azure Active Directory for seamless access across cloud and on-premises resources.
16. Describe Azure Storage redundancy options.
Ans:
Azure Storage offers various redundancy options to ensure data availability and durability. Locally redundant storage (LRS) replicates data three times within a single location in the chosen Azure region. Zone-redundant storage (ZRS) spreads data across three availability zones to protect against zone failures. Geo-redundant storage (GRS) copies data to a secondary region to safeguard against regional failures. For maximum durability, geo-zone-redundant storage (GZRS) combines ZRS and GRS by replicating data across zones and a secondary location.
17. What is Azure Policy, and how does it help in governance?
Ans:
Azure Policy is a service that enables you to enforce organizational standards and assess compliance at scale across your Azure resources. With Azure Policy, you can apply constraints through policies that define rules and actions, ensuring your resources remain compliant with corporate standards and service level agreements (SLAs). It helps in governance by automatically applying policies to new and existing resources, evaluating resource compliance, and providing compliance reports.
18. Explain how Azure Load Balancer works and its use cases.
Ans:
A Layer 4 (TCP, UDP) load-balancing service called Azure Load Balancer divides incoming network traffic among several targets, like virtual machines (VMs), to make sure that no server is overworked. Requests are distributed over several resources, which improves application availability and dependability.
Use cases include:
- Distributing traffic for high-availability web applications.
- Managing traffic to VMs.
- Improving application reliability through health probes that detect failing instances and reroute traffic to healthy ones.
19. How does Azure Monitor work, and what does it monitor?
Ans:
Azure Monitor offers full-stack visibility into applications, infrastructure, and networks, enabling issue detection, performance optimization, and availability assurance. It collects data from application telemetry, Azure resources, and the platform itself, making it available for analysis, alerting, and dashboard visualization. Monitoring includes application metrics like response times and failure rates, as well as infrastructure metrics like CPU and memory usage, providing a comprehensive view of your environment.
20. What are Azure Service Levels (SLAs), and why are they important?
Ans:
The Azure Service Level Agreements (SLAs) outline Microsoft’s uptime and connection guarantees. Azure’s performance criteria are outlined in the SLA, along with the rights and remedies that customers have in the event that Azure fails to fulfill these standards. They are crucial since they provide clients with a precise idea of the level of service availability and dependability they may anticipate, assisting them in making high-availability architectural plans and comprehending how Azure integrates with their mission-critical workloads and applications.
21. What is Azure Resource Manager (ARM), and how does it benefit Azure administrators?
Ans:
- The deployment and management solution for Azure is called Azure Resource Manager, and it offers a management layer that lets you add, modify, and remove resources from your Azure account.
- By providing a standardized administration layer for resource management via the Azure portal, PowerShell, Azure CLI, REST APIs, and client SDKs, it helps Azure administrators.
- Because ARM enables templated deployments, Infrastructure may be defined through code, encouraging consistency, versioning, and repeatability in management procedures.
- Furthermore, it provides fine-grained access management and security by supporting role-based access control (RBAC) for resources.
22. Explain the concept of Azure Virtual Network and its key components.
Ans:
The basic building component of your private network in Azure is an Azure Virtual Network (VNet). It permits safe communication between Azure resources, such as virtual machines (VMs), the internet, and on-premises networks. Subnets, route tables, IP address ranges, and network security groups (NSGs) are essential parts of a VNet. With subnets, you may assign IP addresses in ranges and divide the network inside the VNet. Route tables specify the routing of traffic between subnets, areas, or the internet.
23. How do you achieve high availability in Azure?
Ans:
Achieving high availability in Azure means designing architecture to handle failures and keep applications functional. This involves deploying resources across multiple availability zones or regions, using Azure Load Balancer or Traffic Manager to distribute traffic, and implementing auto-scaling. Azure Site Recovery and geo-redundant storage (GRS) further enhance reliability. Effective planning ensures applications stay accessible even during outages.
24. Describe Azure Identity Protection and its functionalities.
Ans:
Azure Identity Protection, a feature of Azure Active Directory (Azure AD), helps detect vulnerabilities affecting your organization’s identities and configure automated responses for suspicious actions. It includes risk-based conditional access policies that assess sign-in or identity risks and enforce predefined measures to mitigate them. Key functionalities include detecting risky sign-ins and users, investigating incidents, and recommending or enforcing actions such as password changes or multi-factor authentication (MFA).
25. What is Azure ExpressRoute, and when would you use it?
Ans:
With Azure ExpressRoute, you can link your on-premises Infrastructure to Azure data centers with a private, dedicated, high-throughput network connection. ExpressRoute connections provide more security, reduced latency, quicker speeds, and greater reliability than public internet connections.
You would use Azure ExpressRoute in the following scenarios:
- Data Transfer
- Disaster Recovery
- Improved Security
- Hybrid Cloud Scenarios
26. Explain Azure Blueprints and how they differ from ARM templates.
Ans:
ARM templates are used to deploy and manage resources in Azure; however, Azure Blueprints orchestrate the deployment of various resource templates and other artifacts like policies and access control to systematically enforce organizational standards across multiple subscriptions and management groups. Blueprints help maintain consistency and compliance for your Azure environments. Azure Blueprints simplify large-scale Azure deployments by packaging key environment artifacts, such as ARM templates, RBAC assignments, and policies, into a single blueprint that can be deployed repeatedly.
27. Discuss Azure Cost Management and how it helps organizations.
Ans:
Azure Cost Management is a service designed to monitor, allocate, and optimize cloud costs across multi-cloud environments, including Azure, AWS, and Google Cloud. It offers detailed insights into resource usage, helping organizations identify and eliminate wasteful spending. Key features include budget setting, cost forecasting, and spending alerts. Additionally, it provides optimization recommendations to maximize cloud investment value, making it essential for effective financial management and accountability in cloud services.
28. What strategies would you use to optimize Azure costs?
Ans:
- To optimize Azure costs, start by analyzing your current resource usage and costs using Azure Cost Management and Advisor to identify underutilized resources.
- Consider resizing or shutting down underutilized VMs, using reserved instances for consistent workloads, and selecting the right pricing model for your use case.
- Implement auto-scaling to adjust resources based on demand, ensuring you’re not paying for idle capacity.
- Leverage Azure’s modern managed services like Azure Kubernetes Service (AKS) and Azure Functions for more cost-effective scaling. Regularly review and adjust your architecture and use Azure Advisor recommendations to identify opportunities for cost savings.
29. What are Azure Policies, and how do they enforce governance across Azure subscriptions?
Ans:
Azure Policies are a set of rules that enforce and manage your Azure resources’ compliance standards and operational best practices. They help in automating the governance of resources to ensure compliance with company policies and regulatory standards. By defining policies, administrators can restrict certain actions, like preventing VMs from being deployed in regions outside corporate governance or ensuring all resources have specific tags. Policies evaluate resources in Azure subscriptions and can automatically remediate non-compliant resources by either modifying them to become compliant or by deploying compliant resources.
30. How do you secure Azure resources with Network Security Groups (NSGs)?
Ans:
In an Azure Virtual Network (VNet), network traffic to and from Azure resources is filtered via Network Security Groups (NSGs).NSGs can be associated with subnets or individual virtual machine instances, providing a layer of security by defining a list of allow and deny security rules. These rules can filter traffic based on IP address, port, and protocol.
By carefully defining NSG rules, administrators can ensure that only authorized traffic can access or exit their Azure resources, effectively isolating them from unwanted access and potential attacks.
31. What is Azure Service Health, and how does it differ from Azure Monitor?
Ans:
Azure Service Health provides personalized alerts and guidance when Azure service problems are affected. It differs from Azure Monitor by focusing on the health of Azure services themselves, rather than the performance and availability of your specific resources. Service Health alerts you about service incidents, planned maintenance, and health advisories that could impact your resources. It offers detailed information on the status of Azure services and regions, allowing you to plan for maintenance and respond to issues as they arise. Azure Monitor, on the other hand, is more granular, providing data and insights about the operation of your applications and resources within Azure.
32. How do you set up a secure hybrid network between Azure and on-premises?
Ans:
Implementing a secure hybrid network between Azure and an on-premises environment typically involves setting up a Site-to-Site VPN or Azure ExpressRoute for connectivity. A Site-to-Site VPN creates a secure, encrypted connection over the internet between your on-premises VPN device and your Azure Virtual Network. ExpressRoute provides a private, dedicated network connection for more reliability, faster speeds, and lower latencies. Both options require configuring network gateways on Azure and on-premises. Implementing network security groups (NSGs) and Azure Firewalls can further secure the network by filtering traffic and protecting against threats.
33. How can Azure administrators use Azure Automation to improve operational efficiency?
Ans:
Azure Automation allows administrators to automate the creation, monitoring, deployment, and maintenance of resources in the Azure environment. By using runbooks and PowerShell scripts, administrators can automate repetitive tasks such as patching VMs, monitoring services for health and performance, managing network configurations, and automating backups. This reduces the chance of human error, frees up administrators for more strategic work, and ensures a consistent environment setup. Azure Automation also supports Desired State Configuration (DSC) for managing configurations across virtual machines.
34. Explain how Azure’s scalability features support growing application demands.
Ans:
In order to meet the increasing demands of applications, Azure offers a number of scalability capabilities that guarantee apps can withstand load increases without sacrificing performance. Azure Auto Scaling enables the automatic addition or removal of resources in response to real-time demand for services such as Azure Virtual Machine Scale Sets, Azure App Service Plans, and Azure Database for MySQL. In addition to reducing expenses, this guarantees that applications have the resources they require at the appropriate time.
35. Describe the process of configuring backup and disaster recovery in Azure.
Ans:
Configuring backup and disaster recovery in Azure involves utilizing Azure Backup and Azure Site Recovery (ASR) services. Azure Backup provides a simple and secure backup of your data to the cloud, offering protection against ransomware and human errors. Start by defining the backup policy, including the frequency and retention of backups. For disaster recovery, ASR replicates workloads from your primary site to a secondary location (another Azure region or on-premises). The process involves setting up replication, planning for the network, and ensuring application consistency during failover.
36. Explain the difference between Azure IaaS, PaaS, and SaaS.
Ans:
- Azure provides three main service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
- IaaS provides virtualized computing resources over the internet, offering a fully outsourced solution for computing infrastructure with services like Virtual Machines, VPNs, and storage.
- PaaS provides the platform allowing customers to develop, run, and manage applications without the complexity of building and maintaining the Infrastructure associated with the process. It includes services like Azure Web Apps and Azure SQL Database.
- SaaS delivers software applications over the internet on a subscription basis, freeing users from software installation, maintenance, and management.
37. What is Azure Functions?
Ans:
With Azure Functions, serverless computing is possible without the need to explicitly provide Infrastructure, allowing event-triggered code to be executed. It enables developers to concentrate on creating code for a particular purpose, such as constructing straightforward microservices and APIs or processing data and integrating systems. Programming languages supported by Azure Functions include C#, Java, JavaScript, PowerShell, and Python. The pricing model is based on compute time only; it scales automatically based on demand.
38. How do you automate tasks in Azure?
Ans:
Automating tasks in Azure can be achieved through several services and tools, with Azure Automation and Azure Logic Apps being among the most prominent. Azure Automation allows you to automate your cloud management tasks using runbooks, providing a range of capabilities from process automation to configuration management and update management of Azure VMs.
For integrating and automating workflows across cloud services and on-premises systems, Azure Logic Apps offers a visual designer to build workflows that connect apps, data, services, and systems.
39. Describe how Azure manages data redundancy.
Ans:
Azure ensures data redundancy and high availability through several replication strategies across its global Infrastructure. Azure Storage offers locally redundant storage (LRS), where your data is replicated three times within a single data center, and zone-redundant storage (ZRS), which replicates data across three availability zones within a region. For extremely critical data, there’s also the option of geo-zone-redundant storage (GZRS), combining the benefits of ZRS and GRS.
40. How is the NSG created?
Ans:
An NSG can be created through the Azure Portal, Azure CLI, Azure PowerShell, or ARM templates. In the Azure Portal, you would navigate to the “Network security groups” section, click on “Add”, and then provide necessary details like name, subscription, resource group, and location. After creation, you define security rules specifying allowed or denied traffic by protocol, port, and source or destination IP address. These rules effectively control the flow of traffic to and from resources in Azure Virtual Networks, VMs, and subnets.
41. What distinguishes a managed disk from an unmanaged disk?
Ans:
| Aspect | ||
| Management | Managed by Azure | Self-managed by the user |
| Provisioning | Simplified provisioning process | Manual provisioning required |
| Availability | Highly available with built-in replication | Relies on user-configured replication for availability |
| Scalability | Automatically scales with VMs | Manual scaling required |
| Backup and Recovery | Integrated backup and recovery options available | Users must manage backup and recovery independently |
| Security | Encrypted by default with Azure-managed keys | Encryption and key management handled by the user |
| Monitoring and Logging | Integrated with Azure Monitor and Azure Resource Graph | Users must configure monitoring and logging separately |
42. Define a Site-to-Site VPN.
Ans:
A secure internet-based connection between two or more networks, such as an Azure Virtual Network and a business network, is called a site-to-site virtual private network (VPN). It enables safe internet-based communication between resources within each network, just like if they were on the same network. Setting up a VPN device on the on-premises network and connecting it to an Azure VPN Gateway set up in the Azure Virtual Network constitutes this VPN setup. The persistent connection is usually employed in situations when smooth and secure access between Azure and on-premises resources is required.
43. What benefits does Azure’s Active Directory offer?
Ans:
- Azure Active Directory (Azure AD) offers benefits including the secure single sign-on (SSO) to thousands of cloud (SaaS) apps and internal resources, multifactor authentication (MFA) for enhanced security, conditional access policies to control access based on conditions, and seamless integration with on-premises Active Directory.
- It provides identity protection capabilities to detect potential vulnerabilities affecting the organization’s identities, automate responses to detected issues, and provide guidance on mitigating risks.
- Azure AD also supports API access to its service for custom application integration and automation of identity and access management tasks.
44. What advantages does Azure Backup offer?
Ans:
Data backup in the Azure cloud is made easy, safe, and affordable with Azure Backup. It is compatible with multiple data sources, like as on-premises servers, SQL databases, and Azure Virtual Machines. Azure Backup provides a 99-year retention period to meet legal and regulatory obligations. It guarantees the security of your data by encrypting it both in transit and at rest. Because of the scalability of the service, you may backup as much data as you need to without worrying about storage management. Moreover, it provides centralized management and monitoring features, which simplify the management of backup operations for various services and data kinds.
45. How is software development managed with Azure DevOps?
Ans:
A set of development tools for work planning, teamwork on code development, and the creation and deployment of apps are offered by Azure DevOps. Build and release services to automate CI/CD pipelines, Agile planning tools, version control using Git for code management, and a range of testing tools to guarantee software quality are all supported. Software development lifecycle (SDLC) management may be accomplished using Azure DevOps. It is a versatile and all-inclusive solution for managing complicated software projects from conception to deployment and maintenance.
46. What distinguishes Azure Resource Manager from the traditional deployment model?
Ans:
Azure Resource Manager (ARM) is a modern deployment and management service that provides a consistent management layer for creating, updating, and deleting resources in Azure. It represents a significant shift from the traditional (classic) deployment model by enabling template-based deployment. ARM allows for the grouping of related resources into logical containers called “resource groups,” enabling easier management and deployment of applications as a single unit, applying role-based access control (RBAC) to all resources in a group, and defining dependencies between resources so they’re deployed in the correct order.
47. Which security flaws are frequently present in Azure?
Ans:
Common security flaws in Azure environments can stem from misconfigurations, insufficient network controls, inadequate access management, and lack of data encryption. Misconfigured storage accounts leading to unintended data exposure, overly permissive network security group (NSG) rules allowing unauthorized access, not enabling multi-factor authentication (MFA) for user accounts, and leaving management ports open to the internet are typical examples. Additionally, not applying the principle of least privilege through role-based access control (RBAC).
48. Talk about Azure’s resource group concept.
Ans:
Azure’s resource group is a foundational concept that acts as a container for holding related resources for an Azure solution. The idea behind resource groups is to simplify the management of Azure resources by grouping them based on their lifecycle, application, environment (such as production, test, or development), or any other criteria that suit the organizational needs. This grouping allows for easier deployment, management, and monitoring of resources as a collective rather than individually. It also aids in implementing access control and applying policies at the group level. Resources can interact across different resource groups, but managing them within a resource group facilitates streamlined lifecycle management and organization.
49. What do Azure Subscriptions mean?
Ans:
An Azure subscription is a logical container used to manage access to Azure cloud services, where the billing for the services used is aggregated. Each subscription can have one or more resource groups and serves as a boundary for managing resources. It acts as an agreement with Microsoft to use Azure services, which can include access to cloud service resources, the Azure portal, and configuration options. Subscriptions help in organizing access to cloud service resources, managing costs, and ensuring that user access and permissions are appropriately segregated within an organization.
50. Could you provide a comprehensive description of the Azure Machine Learning Text Analysis API?
Ans:
The Azure Machine Learning Text Analysis API is part of Azure Cognitive Services. It provides natural language processing over raw text for sentiment analysis, keyphrase extraction, and language detection.
Sentiment analysis evaluates text input and determines the underlying sentiment (positive, negative, neutral). Key phrase extraction identifies the main points in the text, whereas language detection identifies the language the text is written in from a wide range of languages.
This API is powerful for applications that require understanding and interpreting human language. It enables developers to easily integrate natural language processing into their applications without needing machine learning expertise or complex data models.
51. How is a virtual machine (VM) created using the Azure CLI?
Ans:
Creating a virtual machine (VM) using the Azure Command Line Interface (CLI) involves a few straightforward commands:
- You log in to your Azure account using az login.
- You create a resource group with az group, specifying the name and location.
- You can create the VM with az vm, providing the required details such as the name for the VM, the resource group, the image to use (e.g., Ubuntu, Windows), and the authentication method (password or SSH key).
You can also specify the size of the VM, network settings, and storage configurations. This process simplifies VM creation, allowing for automation and scripting in managing Azure resources.
52. What makes the Azure Diagnostics API necessary?
Ans:
The Azure Diagnostics API is crucial for enabling the collection, storage, and retrieval of diagnostic data from cloud services and virtual machines running in Azure. This includes performance metrics, log files, crash dumps, and other telemetry that is essential for monitoring the health and performance of Azure applications and Infrastructure. The Diagnostics API facilitates real-time monitoring and proactive management of Azure resources, helping identify and diagnose issues before they impact services. By providing detailed diagnostic data, it supports deep analysis and troubleshooting, enabling developers and administrators to ensure the high availability, performance, and reliability of their Azure deployments.
53. Why is the “Migration Assistant” tool available in Azure Websites?
Ans:
The “Migration Assistant” tool is available in Azure Websites (now part of Azure App Service) to simplify the process of migrating existing web applications from an on-premises environment to Azure.
This tool assesses the readiness of web applications for migration, identifies any compatibility issues with Azure, and provides guidance and automation to help move applications to Azure App Service smoothly.
Automating much of the migration process reduces the complexity and time involved in moving applications to the cloud, enabling organizations to take advantage of Azure’s scalability, reliability, and managed services with minimal disruption.
54. How are web apps deployed in Azure?
Ans:
Azure App Service is the platform-as-a-service that enables developers to quickly design, deploy, and scale web applications and APIs. Web apps are launched in Azure utilizing this service. Other ways to deploy include local Git, GitHub, FTP, and Azure DevOps. Developers can concentrate on the application code using Azure App Service’s fully managed platform, which takes care of Infrastructure, patching, scalability, and load balancing. The service supports numerous languages and frameworks, including .NET, Java, Node.js, Python, and PHP. For automated deployments, continuous integration and delivery (CI/CD) pipelines are simple to set up, and Azure CLI, PowerShell, or the Azure site are available to the developers for deployment activities.
55. Define Update Domains
Ans:
Update domains in Azure are a logical collection of devices that are rebooted or undergo maintenance simultaneously. They are a component of Azure’s architecture that guarantees deployed services high availability and fault tolerance. To make sure that only a portion of instances are impacted at any given moment during maintenance operations (such as software upgrades or hardware replacements), a service can be deployed across different update domains. This strategy keeps availability and reduces downtime.
56. Can Azure scale sets and availability work together?
Ans:
Yes, Azure Virtual Machine Scale Sets (VMSS) and availability sets are designed to work together to improve application availability and scalability. VMSS allows you to create and manage a group of identical, load-balanced VMs, enabling you to easily scale out or in as demand changes. When you combine VMSS with availability sets, the VM instances are distributed across multiple fault domains and update domains. This distribution ensures that your application remains highly available by protecting it from failures of physical hardware and minimizing downtime during maintenance events.
57. What’s the CSPack on Azure?
Ans:
CSPack is a command-line tool provided by Azure that is used to create service packages for cloud services. Before deploying an application to Azure Cloud Services, you need to package your application files and configurations into a cloud service package (.cspkg) and a service configuration file (.cscfg). CSPack prepares these files by compiling your application code and configurations. This tool is part of the Azure SDK. It plays a critical role in the deployment process for Azure Cloud Services, allowing developers to package their applications from the development environment in preparation for deployment to Azure.
58. Why is IP address correction done using Azure?
Ans:
IP address correction in Azure refers to the process of updating or changing the IP address assignments to Azure resources to accommodate network changes, scaling requirements, or compliance needs. Azure provides dynamic IP allocation, allowing resources like virtual machines and web apps to automatically receive an IP address from a pool assigned to the virtual network.
However, for scenarios requiring predictable IP addresses, such as allowlisting in firewall rules or configuring DNS, static IP addresses can be assigned. Azure enables the correction or adjustment of these IP settings to ensure that networking configurations remain optimal, secure, and in line with organizational policies without disrupting the services.
59. What is an Azure guest operating system?
Ans:
The Azure guest operating system refers to the operating system installed on virtual machines running in Azure. It operates within the virtualized environment provided by Azure, similar to how an operating system runs on physical hardware in on-premises environments. Azure supports a wide range of guest operating systems, including various versions of Windows Server, Linux distributions (such as Ubuntu, CentOS, Red Hat Enterprise Linux), and others.
60. What is meant by a VNet?
Ans:
A VNet, or Virtual Network, in Azure, is an isolated network within the Azure cloud that allows resources like virtual machines (VMs) and applications to serely communicate with each other, the internet and on-premises networks. It is the fundamental building block for your private network in the cloud, providing a range of networking functions and services, including DNS, routing, and network flow control. VNets offer control over IP address ranges, subnets, route tables, and network gateways. They enable segmentation of the network, enhance security through isolation and boundary protection, and facilitate hybrid cloud scenarios by connecting with on-premises networks using VPNs or Azure ExpressRoute.
61. Can a virtual machine that already exists be added to an availability set?
Ans:
No, a virtual machine (VM) that already exists cannot be directly added to an availability set. Availability sets ensure the high availability of VMs by distributing them across multiple fault domains and update domains. This configuration must be defined when the VM is being created. If you need to add an existing VM to an availability set, you would have to recreate the VM within the desired availability set. This involves deleting the existing VM (while preserving the disks) and creating a new VM using the preserved disks, specifying the availability set during creation.
62. How many jobs does Azure offer for cloud services?
Azure provides a wide range of job roles and services that cater to various aspects of cloud computing, including infrastructure management, application development, data analytics, AI and machine learning, and security. While it’s challenging to quantify the exact number of jobs as Azure continuously evolves, key roles include Azure Administrator, Azure Developer, Azure Solutions Architect, Azure DevOps Engineer, Azure Security Engineer, Azure Data Engineer, Azure AI Engineer, and more.
63. What is Multi-Factor Authentication for Azure AD?
Ans:
In order to obtain access to resources and apps, users must provide two or more verification methods for Azure Active Directory (Azure AD) to enable Multi-Factor Authentication (MFA). By adding a crucial second layer of protection, it helps guard against hackers and dangerous malware during user sign-ins and transactions. There are three types of verification methods: something you own (like a hardware token or phone), something you know (like a password), or something you are (like a fingerprint). Azure AD MFA ensures that weak or stolen credentials cannot be used without further verification.
64. What are an Azure Administrator’s duties and responsibilities?
Ans:
- Infrastructure Management: Azure Administrators oversee cloud infrastructure setup, maintenance, and monitoring, including virtual machines, networks, and storage.
- Security and Compliance: They ensure data security and compliance with regulatory standards, implementing measures to protect sensitive information.
- Access Control: Administrators configure access controls using Azure Active Directory, managing user permissions to secure resources.
- Cost Optimization: They optimize resource usage to minimize costs, identifying and implementing efficiency improvements.
- Disaster Recovery: Administrators manage disaster recovery solutions, ensuring business continuity during outages or incidents.
65. Who makes use of an Active Directory in Azure?
Ans:
- Azure Active Directory (Azure AD) is utilized by IT administrators, app developers, and end-users. IT administrators use it to manage access to applications and resources, enforce security policies and compliance, and manage user identities, including groups and roles.
- App developers use Azure AD to integrate identity management in their applications, allowing for secure sign-on, user authentication, and authorization services.
- End-users benefit from Azure AD through seamless, secure access to internal and external applications with single sign-on capabilities. Essentially, any organization leveraging Azure services for cloud computing would use Azure Active Directory to facilitate secure and efficient access management.
66. List each of a virtual machine’s power states.
Ans:
Virtual machines (VMs) in Azure have several power states, including:
The VM is being started.
- Running: The VM is up and running.
- Stopping: The VM is in the process of being stopped.
- Stopped: The VM has been stopped but still exists and can be restarted. It does not incur compute charges but may still incur charges for other resources like storage.
- Deallocating: The VM is being deallocated, releasing the compute resources.
- Deallocated: The VM has been deallocated, releasing the compute resources and stopping any compute charges. It can be started again but might be assigned a different virtual IP address.
- Unknown: The state of the VM is unknown, possibly due to communication or other issues.
67. Which command is used to tag resources?
Ans:
To tag resources in Azure, the Azure CLI command used is:
- -az tag az tag create –name <tag-name> –value <tag-value>create –name <tag-name> –value <tag-value> –name <tag-name> –value <tag-value>
This command allows you to create and apply tags to manage and categorize Azure resources based on customizable criteria, such as environment, department, project, or any other identifier that helps in organizing resources for billing or management purposes.
68. How will the VPN gateway with a static public IP address be configured?
Ans:
Configuring a VPN gateway with a static public IP address in Azure involves several steps:
- Create a virtual network (VNet) if you haven’t already.
- Create a public IP address with the allocation method set to “Static.”
- Create a VPN gateway in the VNet and associate it with the created static public IP address.
- Configure the VPN gateway settings, including the type (VPN), VPN type (Route-based or Policy-based), and the SKU that meets your performance and SLA requirements.
- Once the VPN gateway is created and configured, you can set up site-to-site, point-to-site, or VNet-to-VNet connections as required.
- Configure your on-premises VPN device with the static public IP address of the Azure VPN gateway for the connection.
- Test the connection to ensure it is established and secure.
69. Mention the protocols that the application gateway is compatible with
Ans:
The following protocols are compatible with Azure Application Gateway:
- HTTP: Facilitates web transmission via the Hypertext Transfer Protocol.
- HTTPS: Facilitates safe communication over a computer network by supporting the safe Hypertext Transfer Protocol.
- WebSocket: Facilitates two-way interactive communication sessions between a user’s browser and a server by supporting the WebSocket protocol.
- HTTP/2: Facilitates the HTTP/2 protocol, which is the enhanced performance version of the HTTP network protocol.
- In order to provide different application delivery controller (ADC) features, such as SSL termination, cookie-based session affinity, and URL-based routing, Application Gateway is made to operate with these protocols.
70. Which common instruments and methods are employed for monitoring Azure resources?
Ans:
Azure Monitor and Azure Application Insights are primary tools for monitoring Azure resources. Azure Monitor collects and analyzes performance metrics and logs across Azure services, enabling administrators to understand the health and operation of their applications and Infrastructure. It provides alerts, dashboards, and machine learning-powered insights for a comprehensive view of resources. Application Insights specifically targets web application monitoring, offering deep analytics and performance monitoring, including user behavior, application dependencies, and failure diagnostics.
71. What are a few typical security risks in Azure?
Ans:
Typical security risks in Azure include misconfigured cloud storage, inadequate access controls, compromised credentials, and unpatched systems. Misconfigured cloud storage can lead to unintended data exposure. Inadequate access controls may give unauthorized users access to sensitive resources. Compromised credentials, often due to weak or reused passwords, can lead to unauthorized access. Unpatched systems are vulnerable to exploitation. These risks underscore the importance of following best practices in security configuration, regular audits, and the principle of least privilege.
72. What is Azure Stack, and how can it help businesses with a hybrid cloud solution?
Ans:
- Azure Stack is an addition to Azure that extends cloud computing’s agility and rapid innovation to on-premises settings. It enables companies to run Azure services from within their data centers, resulting in a genuinely consistent hybrid cloud solution.
- Applications that must stay on-premises because of latency, regulatory, or connection limitations will especially benefit from this.
- Azure Stack offers a smooth transition between on-premises and cloud computing, enabling enterprises to use the same tools and procedures to develop and launch applications in both Azure and on-premises environments.
73. What is Service Fabric by Azure?
Ans:
Scalable and dependable microservices and containers may be packaged, deployed, and managed with ease using Azure Service Fabric, a distributed systems platform. By offering stateful services and actors that significantly reduce the coding complexity of intricate, large-scale applications, Service Fabric tackles the major issues associated with creating and maintaining cloud applications. It is capable of self-healing, rolling updates, and automatically resolving errors while preserving the intended state. Because of its durability and high availability, Service Fabric is the perfect platform for mission-critical applications.
74. What distinguishes Microsoft Azure from AWS?
Ans:
- Service Offerings: While both Azure and AWS provide comprehensive cloud services, Azure integrates seamlessly with Microsoft products like Office 365, while AWS offers a wider range of specialized services, especially in AI and machine learning.
- Market Penetration: AWS holds a larger market share as the longstanding leader, while Azure is rapidly gaining ground, particularly among organizations entrenched in the Microsoft ecosystem.
- Global Infrastructure: AWS boasts a more extensive global presence with data centers in more regions compared to Azure, though both offer extensive global infrastructure.
- Platform Ecosystem: Azure deeply integrates with Microsoft development tools like Visual Studio, while AWS has a broader ecosystem of third-party tools and services, including a robust marketplace for pre-built solutions.
- Security and Compliance: Both prioritize security and compliance, but Azure and AWS may differ in their specific approaches and certifications to meet various regulatory requirements.
75. How Function Fault Domains?
Ans:
Fault domains function in Azure to provide physical separation in a data center, such as different power sources, network switches, and cooling units, reducing the potential impact of hardware failures. When you deploy your VMs across multiple fault domains within an availability set, Azure ensures that your VMs are distributed across these physical boundaries. This distribution minimizes the risk that a single hardware failure will affect all VMs in your application, enhancing the overall availability and reliability of your services.
76. What Are Update Domains?
Ans:
Azure update domains are logical collections of hardware that support concurrent reboots. When virtual machines are deployed inside an availability set, Azure automatically allocates them across many update domains. This guarantees availability by only rebooting a portion of your virtual machines (VMs) at a time during scheduled maintenance activities. This feature guarantees that your application is constantly operating, even when the system is updating, and helps to minimize downtime.
77. How does Azure Redis Cache operate, and what is it?
Ans:
- Azure Redis Cache is a distributed, in-memory managed cache that lets you store and retrieve data from the cache instead of depending just on slower disk-based databases, which improves application performance.
- Its high throughput and low latency data access make it perfect for high-performance applications. It is built on the well-known open-source Redis cache.
- Azure Redis Cache is flexible for various caching requirements since it supports data types, including strings, hashes, lists, sets, and sorted sets with queries.
- In addition, it integrates with Azure services smoothly and provides capabilities like security, clustering, and durability.
78. Describe the various Azure service types.
Ans:
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Software as a Service (SaaS)
- Function as a Service (FaaS)
- Storage as a Service
- Database as a Service (DBaaS)
- Networking Services
79. How do Azure Security Center and Azure Key Vault improve organizational security?
Ans:
Azure Security Center and Azure Key Vault significantly enhance an organization’s security posture. Azure Security Center provides unified security management and advanced threat protection across hybrid cloud workloads, offering recommendations to improve security posture and detect threats using integrated Microsoft intelligence. Azure Key Vault allows organizations to safeguard cryptographic keys and other secrets used by cloud applications and services, minimizing the risks associated with key management and storage.
80. What is RBAC in Azure?
Ans:
Role-based access Control (RBAC) in Azure is a method that provides fine-grained access management to Azure resources. It allows organizations to precisely define who can do what with specific resources, giving them the ability to control access to resources based on the roles assigned to users, groups, and applications. RBAC helps enforce the principle of least privilege, ensuring that users have only the access they need to perform their jobs. This not only enhances security but also simplifies management by allowing administrators to segment duties within their team.
81. Define AppFabric for Windows Azure.
Ans:
- AppFabric was a set of middleware technologies for Windows Azure designed to facilitate the building, managing, and hosting of applications on Microsoft’s cloud platform.
- It provided enhanced capabilities for developing composite applications, such as service bus queues for messaging, access control for authentication and authorization, and caching services for improved application performance.
- Although Microsoft has evolved its cloud offerings significantly since the introduction of AppFabric, integrating and replacing much of its functionality into Azure services like Azure Service Bus, Azure Active Directory, and Azure Cache for Redis, AppFabric laid the groundwork for today’s sophisticated Azure middleware services.
82. What is SQL Azure database?
Ans:
Microsoft Azure offers a fully managed relational database service called SQL Azure Database, which is currently called Azure SQL Database. It delivers a minimal downtime, highly available, scalable, and secure database platform with automatic backups and built-in intelligence that automates performance optimization, upgrades, and tuning. A variety of data-driven applications can benefit from Azure SQL Database’s support for the T-SQL and advanced data security capabilities, including data masking, encryption, and access control.
83. What does Azure Conditional Access entail?
Ans:
Azure Conditional Access is a security feature within Azure Active Directory that allows organizations to apply automated access-control decisions for accessing cloud apps based on conditions. It integrates with Microsoft 365 and other SaaS applications to enforce policies that ensure only authorized users under specific conditions can access sensitive information. Conditional Access policies can include the requirements for multi-factor authentication, device compliance, location-based rules, and risk levels.
84. What does Azure profiling entail?
Ans:
Azure profiling refers to the process of collecting performance data from applications running in Azure to identify potential bottlenecks, inefficiencies, or areas for optimization. Azure offers various tools for profiling, including Application Insights and Visual Studio Profiler, which can monitor application performance in real time, providing insights into CPU usage, memory consumption, response times, and other critical performance metrics. Profiling enables developers and administrators to understand how applications perform in a production environment, helping to diagnose issues, improve application responsiveness.
85. What is a cmdlet in Azure?
Ans:
- A cmdlet (command-let) in Azure, particularly in the context of Azure PowerShell, is a lightweight command used in the PowerShell environment that performs a single function or operation. Azure PowerShell cmdlets are specialized scripts designed to automate tasks and manage Azure resources.
- Each cmdlet follows a verb-noun naming convention, such as Get-AzVM for retrieving information about Azure VMs or New-AzResourceGroup for creating a new resource group.
- Cmdlets make it easier to interact with Azure services by encapsulating complex operations into simpler command-line instructions, enabling efficient management of Azure resources directly from the command line or through scripts.
86. what are Azure resources?
Ans:
Azure resources are individual components within Azure that provide specific functionality as part of the broader Azure cloud platform. Examples include virtual machines, storage accounts, web apps, databases, and virtual networks. Each resource exists within a resource group, which acts as a lifecycle boundary for organizing and managing resources that share a common lifecycle. Resources can be managed through the Azure portal, Azure PowerShell, Azure CLI, or ARM templates, allowing for automation and efficient management at scale.
87. What does Azure autoscaling entail?
Ans:
Azure autoscaling is a feature that automatically adjusts resources in an Azure application to match its current demand, improving performance while optimizing costs. It supports scaling out (adding more instances) or scaling in (removing instances) based on predefined rules or metrics, such as CPU utilization or request rates. Autoscaling can be applied to various Azure services, including Azure Virtual Machine Scale Sets, App Services, and Azure Functions. This ensures that applications remain responsive during peak loads without over-provisioning resources, leading to more efficient resource utilization and cost savings.
88. What is NSG?
Ans:
An Azure Virtual Networks (VNet) resource’s network traffic can be allowed or denied by a Network Security Group (NSG), a networking filter that holds a list of security rules. In the Azure environment, NSGs can be linked to specific virtual machine instances or subnets. To regulate incoming and outgoing traffic, these rules are processed in priority order, from the lowest to the greatest number. NSGs are a vital part of Azure’s network communication security, ensuring that only authorized traffic may access your resources. This helps to increase security.
89. Which tools are you going to utilize to make the Vnets?
Ans:
- Azure Portal
- Azure PowerShell
- Azure Resource Manager (ARM) Templates
- Azure SDKs (Software Development Kits)
- Azure Terraform Provider
- Azure CLI with Azure Resource Manager (ARM) templates
- Azure Management Libraries for .NET
- Azure Networking Resource Provider API
90. What role does an Azure administrator play?
Ans:
An Azure Administrator manages and maintains Microsoft Azure cloud services and resources. Their primary functions include:
- Deployment and Management: Deploying, configuring, and managing Azure resources, as well as networking components.
- Monitoring and Maintenance: Monitoring the performance and health of Azure services and ensuring the availability of resources.
- Security and Access Management: Manage access control and secure Azure environments.
- Automation and Optimization: Automating repetitive tasks using tools like Azure PowerShell and Azure CLI.