Apigee is a robust API management platform acquired by Google. Apigee facilitates the creation, deployment, and scaling of APIs. Offering a comprehensive suite of tools, Apigee covers the entire API lifecycle, starting from design to consumption. The platform’s API design features enable organizations to craft APIs with a focus on security, scalability, and usability. Serving as an API gateway, Apigee acts as an intermediary between backend services and applications, handling tasks such as routing, composition, and protocol translation.
1. What is Apigee?
Ans:
Apigee is an API management platform that facilitates the development, deployment, and management of APIs (Application Programming Interfaces). In order to provide smooth communication between various software applications, it assists enterprises in developing, scaling, and securing APIs.
2. Explain the purpose of API management.
Ans:
API management aims to streamline the entire lifecycle of APIs. It involves creating, documenting, securing, deploying, and analyzing APIs to ensure they meet organizational and industry standards. Building and using APIs is made more efficient overall, more interoperable, and faster with API management.
3. What are the key components of Apigee Edge?
Ans:
Apigee Edge consists of several key components, including API proxies, API products, developers, analytics, and the Apigee Edge management and runtime services. These components collectively enable the creation, deployment, and monitoring of APIs.
4. Describe the role of API proxies in Apigee.
Ans:
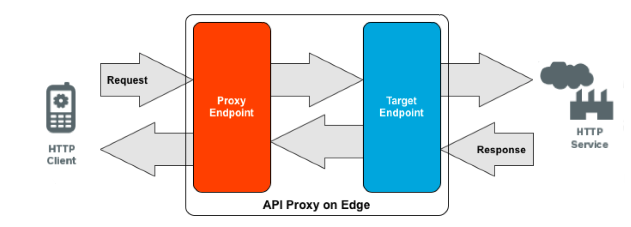
- API proxies in Apigee act as intermediaries between client applications and backend services.
- They handle requests, enforce security policies, perform traffic management, and enable analytics.
- API proxies provide a layer of abstraction, allowing for the implementation of various features without directly exposing the backend services.
5. How does Apigee help in API security?
Ans:
Apigee enhances API security through various features such as authentication, authorization, traffic encryption, and threat protection. It allows the implementation of security policies, access controls, and encryption mechanisms to safeguard APIs from unauthorized access, data breaches, and other security threats.
6. Explain the concept of API traffic management in Apigee.
Ans:
- API traffic management in Apigee involves controlling the flow of API requests to ensure optimal performance, reliability, and resource utilization.
- It includes features such as rate limiting, quota management, caching, and load balancing to handle different levels of API traffic effectively.
7. What are the main policies in Apigee Edge and their functionalities?
Ans:
Apigee Edge supports various policies, including authentication, traffic management, security, transformation, and analytics policies. Authentication policies secure API access, traffic management policies control request flow, security policies enforce data protection, transformation policies modify requests and responses, and analytics policies gather data for analysis.
8. Discuss the role of Apigee in API lifecycle management.
Ans:
- Apigee plays a vital role in API lifecycle management by facilitating the creation, deployment, versioning, and retirement of APIs.
- It provides tools for designing APIs, enforcing policies, monitoring traffic, and analyzing performance.
- In order to ensure agility, scalability, and consistency in API development, Apigee assists organisations in managing the full API lifecycle.
9. How does Apigee handle authentication and authorization for APIs?
Ans:
Apigee provides authentication mechanisms such as API keys, OAuth, and JWT to verify the identity of clients accessing APIs. Authorization is enforced through policies that control access rights based on predefined rules and permissions, ensuring that only authorized users or applications can access specific resources.
10. What is API caching, and why is it important in Apigee?
Ans:
- API caching in Apigee involves storing and reusing responses from backend services to reduce latency and improve API performance.
- It helps minimize redundant requests to the backend by serving cached responses when applicable.
11. Explain the role of API specification and Swagger in Apigee API development.
Ans:
API specifications, often described using tools like Swagger, define the structure and behavior of APIs. In Apigee, these specifications can be imported to create API proxies quickly and accurately.
Swagger helps document the API, define endpoints, request/response formats, and authentication methods, ensuring consistency and clarity in development.
12. What is the purpose of API product in Apigee, and how is it created?
Ans:
- An API product in Apigee bundles one or more APIs and provides a way to monetize or control access to those APIs.
- API products define usage policies, such as rate limits and quotas.
- They are made by specifying the behaviour, visibility, and conditions of use of the product.
13. How do you design a RESTful API in Apigee?
Ans:
Designing a RESTful API in Apigee involves defining resource URIs, HTTP methods, payload formats, and response codes. Use Apigee Edge’s API proxy configuration to set up request and response flows, apply security policies, and manage API traffic effectively. Follow RESTful principles for a clear, scalable, and maintainable API design.
14. Discuss the use of shared flows in Apigee.
Ans:
Shared flows in Apigee allow the reuse of logic across multiple API proxies. They are sets of reusable policies and resources that can be included in API proxies, providing a way to centralize common functionalities such as logging, security checks, and error handling. Shared flows enhance consistency and maintainability in API development.
15. Explain the process of creating a new API proxy in Apigee.
Ans:
- To create a new API proxy in Apigee, use the Apigee Edge management interface.
- Start by defining the API proxy name and base path, then select the desired proxy type (e.g., HTTP or SOAP).
- Establish the target backend services, implement security and traffic control policies.
- Deploy the API proxy to the intended environment after validation.
16. How can you prevent API abuse and ensure rate limiting in Apigee?
Ans:
Apigee provides rate limiting policies that can be applied to API proxies to prevent abuse and ensure fair usage of resources. These policies define limits on the number of requests a client can make within a specified time frame, helping to control traffic, protect backend services, and maintain overall system stability.
17. What is OAuth, and how does Apigee support OAuth for API security?
Ans:
- OAuth is an open standard for access delegation commonly used in API security.
- Apigee supports OAuth by enabling the creation of OAuth providers and configuring OAuth policies.
- This allows API developers to implement secure authorization mechanisms, token issuance, and access control for their APIs.
18. Explain the role of API keys in Apigee.
Ans:
API keys in Apigee serve as a form of authentication and access control. Developers obtain API keys to access protected APIs. Apigee allows the creation, management, and validation of API keys. API key policies can be applied to API proxies to enforce key-based authentication and control access to specific resources.
19. Discuss the use of API analytics in enhancing security.
Ans:
- API analytics in Apigee provide insights into API usage, performance, and potential security threats.
- By analyzing patterns and anomalies in API traffic, organizations can identify and respond to security issues promptly.
- Analytics contribute to proactive security measures, helping in the detection of suspicious behavior, traffic spikes.
20. How does Apigee handle versioning of APIs?
Ans:
Apigee supports API versioning through the inclusion of version information in the API proxy’s base path. This enables different versions of the API to coexist. Developers can access specific versions by using the versioned path, allowing for backward compatibility and phased rollout of new features without disrupting existing users.
21. How does Apigee integrate with backend services?
Ans:
Apigee integrates with backend services using API proxies. API proxies act as intermediaries, routing requests from client applications to the appropriate backend services.
Apigee supports various protocols, including HTTP, REST, SOAP, and others, allowing seamless communication between APIs managed by Apigee and backend systems.
22. Explain the concept of API mediation in Apigee.
Ans:
- API mediation in Apigee involves the transformation and manipulation of requests and responses as they pass through the API proxy.
- Mediation policies are applied to modify data formats, headers, ensuring compatibility between client applications and backend services.
- This mediation process enhances interoperability and allows for customization of API behavior.
23. What is the role of message processors in Apigee?
Ans:
Message processors in Apigee are responsible for processing API traffic asynchronously. They handle tasks such as analytics data collection, caching, and routing. Message processors play a crucial role in offloading non-critical tasks from the API proxy, optimizing performance, and ensuring that the proxy can handle a large volume of requests efficiently.
24. Differentiate between API and API proxy in Apigee.
Ans:
| Feature | API | API Proxy | |
| Definition |
Represents backend services for developers |
Acts as a gateway managing requests to the backend | |
| Responsibility | Business logic and functionality exposure | Intermediary for request handling, security, and policies. | |
| Visibility | Developers interact with backend services | Developers send requests to the proxy for centralized control | |
| Security |
Backend services handle security measures |
Proxy enforces security policies before reaching the backend |
25. How can you extend Apigee functionalities using Java callouts?
Ans:
- Java callouts in Apigee allow developers to extend functionalities by incorporating custom Java code into the API proxy flow.
- This enables the execution of custom logic, data manipulation, or integration with external systems.
- Java callouts provide a way to implement specific requirements that may not be achievable through standard Apigee policies alone.
26. Discuss the role of extensions and shared flows in Apigee.
Ans:
Extensions and shared flows in Apigee enhance reusability and customization. Extensions are custom code snippets or policies that extend the functionality of the API proxy, while shared flows are sets of reusable policies and resources. Both facilitate modular development, making it easier to maintain and scale API proxies across different projects.
27. How does Apigee provide analytics for API traffic?
Ans:
Apigee provides analytics for API traffic through its analytics capabilities. It captures and analyzes data on API usage, performance, and errors. Apigee Edge Analytics offers dashboards and reports that provide insights into traffic patterns, response times, and other metrics, enabling organizations to monitor, analyze, and optimize their APIs effectively.
28. Explain the importance of error handling and logging in Apigee.
Ans:
- Error handling in Apigee is crucial for gracefully managing unexpected issues during API interactions.
- Apigee allows the configuration of error handling policies to generate meaningful error responses.
- Logging is equally important for tracking API requests, responses, and errors, aiding in debugging, monitoring.
29. What are key performance indicators (KPIs) in Apigee analytics?
Ans:
Key performance indicators (KPIs) in Apigee analytics include metrics such as API traffic volume, latency, error rates, and resource utilization. These indicators help assess the overall performance, availability, and reliability of APIs, enabling organizations to identify areas for improvement and ensure optimal API operation.
30. How can you set up custom reports in Apigee?
Ans:
Custom reports in Apigee can be set up using the Apigee Edge management interface. By defining custom dimensions, metrics, and filters based on specific business requirements, organizations can create tailored reports to track and analyze API performance, usage patterns, and other relevant metrics.
31. What deployment options are available for Apigee?
Ans:
Apigee offers multiple deployment options, including Apigee Edge in the cloud (public or private), Apigee Edge for Private Cloud (on-premises), and Apigee Hybrid, which combines aspects of cloud and on-premises deployment. Organizations can choose the option that aligns with their infrastructure, compliance, and performance requirements.
32. Explain the process of deploying an API proxy in Apigee.
Ans:
API proxy deployment in Apigee involves creating a revision of the API proxy configuration, followed by deploying it to the desired environment. This process includes selecting the target environment, validating the configuration, and activating the API proxy revision. Apigee then manages the routing of API traffic based on the deployed revision.
33. What is the role of environments in Apigee?
Ans:
- Environments in Apigee represent different stages of the API lifecycle, such as development, testing, and production.
- Each environment has its own configuration, variables, and associated resources.
- Environments facilitate controlled API deployment and testing by separating the development.
34. Discuss best practices for securing Apigee deployment.
Ans:
Best practices for securing Apigee deployment include implementing proper authentication mechanisms, enforcing access controls, encrypting sensitive data in transit, regularly updating and patching the Apigee platform, and monitoring API traffic for anomalies. Using security policies offers an extra degree of security, such as OAuth and validation of API keys.
35. Describe how Apigee manages API security at different levels.
Ans:
- Apigee manages API security through various levels, including authentication, authorization, and traffic encryption.
- It supports authentication mechanisms such as API keys, OAuth, and JWT.
- Authorization policies control access rights, and traffic encryption ensures secure communication.
- Additionally, Apigee provides threat protection mechanisms to safeguard APIs from potential attacks.
36. How would you handle versioning changes in an existing API deployed in Apigee?
Ans:
Apigee supports versioning by including version information in the API proxy’s base path. To handle changes, create a new revision of the API proxy, modify the necessary configurations, and deploy it to the appropriate environment. Clients can then migrate to the new version gradually, maintaining backward compatibility until the transition is complete.
37. Explain how to secure an API in Apigee using OAuth.
Ans:
- To secure an API in Apigee using OAuth, configure an OAuth provider and apply OAuth policies to the API proxy.
- Define OAuth scopes, specify client credentials, and enforce token validation.
- This ensures that only authenticated and authorized clients with valid OAuth tokens can access protected resources, enhancing API security.
38. Discuss strategies for handling backward-compatible API changes in Apigee.
Ans:
Strategies for backward-compatible API changes in Apigee involve thoughtful versioning, maintaining consistent URIs, and providing clear documentation for developers.
Implementing backward-compatible changes, such as adding new fields without breaking existing contracts, allows for smooth transitions and minimizes disruptions for API consumers.
39. How can you monitor and troubleshoot API issues in Apigee?
Ans:
Apigee provides monitoring and troubleshooting tools, including the Apigee Edge management interface, which offers real-time analytics, traffic metrics, and error details. Additionally, developers can use trace sessions for detailed debugging, and Apigee Edge logs provide information on API traffic, errors, and system events, aiding in issue identification and resolution.
40. Describe a scenario where you had to optimize API performance in Apigee.
Ans:
- In an API performance optimization scenario, one might review and optimize policies such as caching, traffic management, and response transformation in the API proxy configuration.
- Adjusting connection pools, leveraging distributed caching, and minimizing unnecessary processing can contribute to improved API response times and overall performance in Apigee.
41. What is Apigee SmartDocs, and how does it enhance API documentation?
Ans:
Apigee SmartDocs is a feature that automatically generates interactive API documentation from the API proxy configuration. It provides a user-friendly interface, allowing developers to explore and test APIs directly within the documentation. SmartDocs enhances API documentation by ensuring it remains up-to-date, interactive, and easily accessible, fostering a better understanding of API functionalities.
42. Explain the role of API traffic management policies in Apigee.
Ans:
- API traffic management policies in Apigee enable control and optimization of the flow of API requests.
- These policies include features such as quota enforcement, spike arrest to prevent traffic spikes, and response caching.
- By applying traffic management policies, organizations can regulate API usage, ensure fair access, and enhance overall performance.
43. How can you implement API rate limiting in Apigee using policies?
Ans:
API rate limiting in Apigee is implemented using the Spike Arrest policy. This policy allows you to define a limit on the number of requests a client can make within a specified time period.
By configuring the Spike Arrest policy in the API proxy, you can control the rate of incoming requests, preventing abuse and ensuring fair usage of API resources.
44. Discuss the use of Quotas in Apigee.
Ans:
- Quotas in Apigee limit the number of requests a client can make to an API within a defined time frame.
- Quotas are often used to prevent abuse, ensure fair usage, and manage resource consumption.
- By applying quota policies in API proxies, organizations can control the rate at which clients access APIs, balancing usage across different user or app scenarios.
45. How do microservices architecture and Apigee complement each other?
Ans:
Microservices architecture and Apigee complement each other by enabling the efficient management and exposure of microservices as APIs. Apigee acts as an API gateway, providing a unified entry point for accessing microservices. It enhances security, facilitates versioning, and allows for traffic management, analytics, and monitoring, contributing to the overall scalability and manageability of microservices.
46. What is the purpose of fault handling in Apigee, and how can it be configured?
Ans:
- Fault handling in Apigee involves managing errors and unexpected situations during API interactions.
- Fault handling policies, such as Raise Fault and Fault Rules, allow developers to define how Apigee should respond to errors.
- Configuration includes specifying error codes, custom error messages, and defining actions to take when faults occur.
47. Discuss the impact of serverless computing on API management.
Ans:
Serverless computing impacts API management by abstracting infrastructure concerns from developers. With serverless platforms, organizations can focus on building and deploying APIs without managing underlying servers. Apigee can integrate with serverless environments, providing a consistent API gateway, security, and analytics layer, ensuring seamless API management in a serverless architecture.
48. How does Apigee support GraphQL APIs?
Ans:
- Apigee supports GraphQL APIs by allowing developers to create API proxies that expose, secure, and manage GraphQL services.
- Through configuration and policies, Apigee enables traffic management, security, analytics, and other essential features for GraphQL APIs.
- This ensures a consistent and secure experience for API consumers while leveraging the benefits of GraphQL.
49. What role does Apigee play in DevOps for API development?
Ans:
Apigee plays a vital role in DevOps for API development by providing tools for continuous integration, deployment, and monitoring of APIs. It allows for version control, automated testing, and seamless deployment across different environments. Apigee’s analytics and monitoring capabilities also support ongoing performance optimization and issue resolution in a DevOps workflow.
50. How can Apigee contribute to building a scalable and resilient API ecosystem?
Ans:
Apigee offers services including traffic management, caching, security, and analytics, which help create an ecosystem of APIs that is robust and scalable. Performance is improved overall, misuse is avoided, and effective API utilisation is guaranteed. A robust and durable API ecosystem is facilitated by Apigee’s fault tolerance, scalability, and ability to handle high volumes of traffic over the API.
51. How does Apigee handle API traffic encryption?
Ans:
Apigee handles API traffic encryption by providing support for HTTPS (TLS/SSL) protocols. API proxies can be configured to enforce encryption for data in transit, ensuring secure communication between clients and the Apigee gateway. This helps protect sensitive information from unauthorized access during transmission.
52. Explain the role of API key validation in Apigee security.
Ans:
- API key validation in Apigee is a security mechanism where clients must include a valid API key in their requests.
- Apigee validates the key against predefined criteria, ensuring that only authorized clients can access the API.
- API key validation is commonly used for authentication and access control, enhancing the overall security of APIs.
53. What is the OAuth 2.0 authorization code grant type?
Ans:
The OAuth 2.0 authorization code grant type is a flow used for obtaining access tokens. In Apigee, it involves redirecting the user to an authorization endpoint, obtaining an authorization code, and exchanging it for an access token. For client-server applications when the client may maintain the client credentials private, this approach is appropriate.
54. Discuss the importance of mutual TLS (mTLS) in Apigee.
Ans:
- Mutual TLS (mTLS) in Apigee enhances API security by requiring both the client and server to authenticate each other using SSL/TLS certificates.
- This ensures a two-way trust relationship, preventing unauthorized parties from accessing the API.
- mTLS is crucial for secure communication, particularly in scenarios where the identity of both the client and server needs to be verified.
55. How can you implement IP whitelisting and blacklisting in Apigee?
Ans:
Apigee allows the implementation of IP whitelisting and blacklisting through security policies. By configuring an IP filter policy, organizations can specify a list of allowed (whitelisted) or blocked (blacklisted) IP addresses. This helps control access to APIs based on IP addresses, adding an additional layer of security and access control.
56. Describe the purpose of the Extract Variables policy in Apigee.
Ans:
- The Extract Variables policy in Apigee is used to extract information from the request or response and store it in variables.
- This extracted data can then be used in subsequent policies or flows within the API proxy.
- The Extract Variables policy is valuable for manipulating and capturing specific parts of the incoming or outgoing messages.
57. How can you transform data using the Message Transformer policy in Apigee?
Ans:
The Message Transformer policy in Apigee is used to transform data within the API proxy flow. It allows developers to modify request and response payloads, headers, or other message attributes. Using the Message Transformer policy, organizations can perform data transformation, format conversion, and content enrichment to ensure compatibility between clients and backend services.
58. Explain the functionality of the OAuthV2 policy in Apigee.
Ans:
The OAuthV2 policy in Apigee is used to enforce OAuth 2.0 authentication and authorization for APIs. It allows organizations to configure OAuth providers, define authentication and authorization endpoints, and enforce policies for validating access tokens. The OAuthV2 policy plays a central role in securing APIs and controlling access based on OAuth credentials.
59. Discuss the role of the Spike Arrest policy in API rate limiting.
Ans:
- The Spike Arrest policy in Apigee is used for API rate limiting, preventing sudden spikes in traffic that could overwhelm backend services.
- It sets limits on the number of requests a client can make within a specified time interval.
- The Spike Arrest policy helps ensure fair usage, prevent abuse, and maintain overall system stability.
60. What is the function of the Assign Message policy in Apigee?
Ans:
The Assign Message policy in Apigee may be used to add, remove, or modify material from the message payload, headers, or other attributes. During the API proxy flow, it allows developers to dynamically change the request or response. The Assign Message policy is helpful for customising messages based on particular requirements and situations.
61. How does Apigee capture and store API analytics data?
Ans:
Apigee captures and stores API analytics data through its built-in analytics capabilities. As API traffic passes through Apigee, relevant data such as request/response times, error rates, and usage patterns are automatically collected. This data is then stored in the Apigee analytics database, allowing organizations to access and analyze it through the Apigee Edge management interface.
62. Explain the difference between developer and app-level analytics in Apigee.
Ans:
Developer-level analytics in Apigee provide insights into how individual developers interact with APIs. This includes data on developer activity, API consumption, and error rates specific to each developer.
App-level analytics, on the other hand, focus on the performance and usage patterns of the applications consuming the APIs. Both levels of analytics contribute to a comprehensive understanding of API usage.
63. How can you set up custom alerts based on analytics data in Apigee?
Ans:
Custom alerts in Apigee can be set up using the Apigee Edge management interface. By defining custom conditions based on specific analytics metrics (e.g., error rates, traffic spikes), organizations can create alert rules. When these conditions are met, Apigee triggers alerts, allowing administrators to proactively respond to potential issues and ensure the stability of API operations.
64. Discuss the role of Apigee analytics in identifying performance bottlenecks.
Ans:
Apigee analytics plays a crucial role in identifying performance bottlenecks by providing insights into API traffic patterns and response times. Through analytics, organizations can pinpoint areas of high latency, analyze error rates, and identify inefficient API calls. This information helps in optimizing API proxies, addressing performance bottlenecks, and enhancing overall API efficiency.
65. Explain the concept of canary releases in Apigee.
Ans:
- Canary releases in Apigee involve deploying a new version of an API proxy to a subset of users or traffic before making it available to the entire audience.
- This allows organizations to test the new version in a real-world scenario, identify potential issues, and gradually roll out changes.
- Canary releases in Apigee contribute to a controlled and risk-mitigated deployment process.
66. What is API monitoring in Apigee, and how is it configured?
Ans:
API monitoring in Apigee involves tracking and analyzing the real-time performance and availability of APIs. It can be configured through the Apigee Edge management interface, where organizations can set up monitors for specific API proxies. API monitoring includes metrics such as response time, error rates, and availability, allowing for proactive identification of issues and ensuring optimal API performance.
67. What is blue-green deployment, and how can it be applied to Apigee?
Ans:
Blue-green deployment is a strategy where two identical environments, “blue” and “green,” run simultaneously. In Apigee, this can be applied by deploying two versions of an API proxy—blue representing the current version and green representing the new version. Traffic is initially routed to the blue environment, and after validating the green environment, traffic is switched seamlessly, minimizing downtime and enabling efficient testing.
68. How does Apigee support multi-region deployment for high availability?
Ans:
- Apigee supports multi-region deployment for high availability by allowing organizations to deploy API proxies in different geographical regions.
- This ensures redundancy and fault tolerance, as traffic can be redirected to alternate regions in case of outages or performance issues.
- Apigee’s global distribution capabilities contribute to building a resilient and highly available API infrastructure.
69. Discuss the process of rolling back a failed deployment in Apigee.
Ans:
In Apigee, rolling back a failed deployment involves reverting to a previous version of the API proxy configuration. This can be done by creating a new revision with the desired, known-good configuration and deploying it to the target environment. Organizations can quickly and efficiently roll back to a stable state, mitigating the impact of a failed deployment.
70. What are the best practices for version control of API proxies in Apigee?
Ans:
Best practices for version control of API proxies in Apigee include using source control systems (e.g., Git) to manage and version API proxy configurations. Each significant change or update should be tracked as a new revision, allowing for easy rollback and collaboration among development teams. Regularly documenting changes and maintaining a clear versioning strategy helps ensure consistency and traceability in API development.
71. Discuss the role of shared flows in reusability and extensibility.
Ans:
Shared flows in Apigee play a crucial role in reusability and extensibility. They allow developers to define sets of reusable policies and resources that can be applied across multiple API proxies.
This promotes consistency, reduces duplication of effort, and simplifies maintenance. Shared flows are instrumental in achieving modular and scalable API proxy design.
72. What is the Java Callout policy, and when is it used in Apigee?
Ans:
- The Java Callout policy in Apigee allows developers to execute custom Java code within the API proxy flow.
- It is used when specific functionalities cannot be achieved with standard Apigee policies.
- Java Callout policies provide a way to extend Apigee’s capabilities by incorporating custom code into the API proxy.
73. Explain how to create a custom OAuth 2.0 authorization server in Apigee.
Ans:
Creating a custom OAuth 2.0 authorization server in Apigee involves configuring OAuth policies and providers. Define OAuthV2 providers, set up authorization and token endpoints, and configure OAuth policies in the API proxy. This allows Apigee to act as a custom authorization server, handling authentication and authorization for API access.
74. How can you integrate custom code or libraries into Apigee?
Ans:
- Apigee allows integration of custom code or libraries through policies like the Java Callout policy or Node.js policies.
- For Java Callout, developers can upload custom JAR files containing their code.
- In the case of Node.js policies, JavaScript code or external libraries can be added directly.
- This integration enables the use of custom logic or third-party libraries within the API proxy flow.
75. Describe the process of debugging an issue in Apigee.
Ans:
Debugging an issue in Apigee involves using tools like the Apigee Edge management interface and the Apigee Trace tool. Developers can review logs, examine analytics data, and utilize the Trace tool to step through the API proxy flow and observe request and response details. This iterative process helps identify and resolve issues in the API proxy configuration.
76. How can you use trace sessions for debugging in Apigee Edge?
Ans:
Trace sessions in Apigee Edge allow developers to capture detailed information about API proxy execution. By enabling trace sessions, developers can step through each policy in the API proxy flow, inspect variables, headers, and payloads, and identify issues or bottlenecks. Trace sessions are invaluable for real-time debugging and understanding the behavior of API proxies.
77. Discuss the role of error handling policies in Apigee.
Ans:
- Error handling policies in Apigee are essential for gracefully managing unexpected issues during API interactions.
- Policies like Raise Fault and Fault Rules allow developers to define how Apigee should respond to errors.
- Proper error handling ensures that error responses are clear, informative, and controlled.
78. What tools and techniques are available for monitoring Apigee performance?
Ans:
Apigee provides several tools and techniques for monitoring performance. The Apigee Edge management interface offers real-time analytics dashboards, while the Apigee Trace tool allows developers to trace API proxy execution.
Additionally, organizations can use external monitoring tools, integrate with Apigee’s analytics API, and set up alerts to proactively monitor and address performance issues.
79. How does Apigee help in identifying and resolving API traffic bottlenecks?
Ans:
Apigee helps in identifying and resolving API traffic bottlenecks through its analytics and monitoring capabilities. By analyzing metrics such as response times, error rates, and traffic patterns, organizations can pinpoint areas of congestion or latency. This information guides optimizations in API proxy configurations, ensuring efficient handling of traffic and addressing bottlenecks to enhance overall performance.
80. How can you extend Apigee using JavaScript policies?
Ans:
Apigee allows you to extend its functionality using JavaScript policies. By adding a JavaScript policy to an API proxy flow, you can execute custom JavaScript code to manipulate requests, responses, or perform other logic. This extensibility enables developers to implement custom behaviors and enhancements in their API proxies.
81. Explain the purpose of Apigee Developer Portal.
Ans:
- The Apigee Developer Portal serves as a centralized platform for API developers to access, explore, and collaborate on APIs.
- It provides a user-friendly interface for developers to discover API documentation, access key resources, test APIs.
- The Developer Portal enhances the developer experience and facilitates the adoption of APIs by providing a self-service environment.
82. How does Apigee support API versioning in the Developer Portal?
Ans:
Apigee supports API versioning in the Developer Portal by allowing developers to access different versions of APIs. Organizations can publish multiple versions of APIs with distinct endpoints, and developers can choose the version they want to use. This ensures backward compatibility while allowing for the introduction of new features or improvements in subsequent API versions.
83. Discuss the role of API documentation in the Apigee Developer Portal.
Ans:
- API documentation in the Apigee Developer Portal serves as a comprehensive guide for developers to understand the functionalities, endpoints, and usage of APIs.
- It includes details such as request and response formats, authentication methods, and example use cases.
- Well-documented APIs streamline the development process, encourage adoption, and contribute to a positive developer experience.
84. How does Apigee handle API security in a multi-cloud environment?
Ans:
Apigee ensures API security in a multi-cloud environment through a range of features such as authentication, authorization, encryption, and threat protection. Security policies can be applied consistently across different cloud environments, and organizations can configure access controls and identity management to protect APIs and sensitive data regardless of the cloud infrastructure.
85. Explain the concept of API monetization and how it can be implemented in Apigee.
Ans:
API monetization in Apigee involves generating revenue from API usage. Organizations can implement various monetization strategies, including tiered pricing, subscription plans, and usage-based billing.
Apigee provides features to track and manage API usage, set pricing rules, and generate reports for billing purposes, allowing organizations to create effective API monetization models.
86. Discuss the role of Apigee Sense in protecting APIs from threats.
Ans:
- Apigee Sense plays a crucial role in protecting APIs from threats by providing threat detection and prevention capabilities.
- Apigee Sense enhances API security by proactively identifying and responding to potential threats in real time.
87. What is Apigee’s approach to supporting GraphQL APIs?
Ans:
Apigee helps organisations support GraphQL APIs by allowing them to establish API proxies that expose, protect, and manage GraphQL services. Apigee delivers GraphQL APIs with traffic management, security, analytics, and other capabilities via configuration and rules. This guarantees a uniform and safe API customer experience while harnessing the benefits of GraphQL.
88. Explain the role of Apigee in data privacy regulations.
Ans:
- Apigee plays a crucial role in ensuring compliance with data privacy regulations by providing features for data protection and security.
- Apigee helps organizations meet data privacy requirements and safeguards user data throughout the API lifecycle.
89. Discuss the impact of containerization on Apigee deployment.
Ans:
Containerization, such as Docker, streamlines Apigee deployment by providing a lightweight and consistent environment. Apigee can be containerized, allowing for easier scaling, versioning, and portability across different infrastructure environments. Containers enhance deployment flexibility, making it more efficient to manage Apigee components, especially in microservices and container orchestration platforms like Kubernetes.
90. How does Apigee support serverless API deployments?
Ans:
Apigee supports serverless API deployments by integrating with serverless computing platforms, such as AWS Lambda or Google Cloud Functions. Apigee acts as an API gateway, providing security, analytics, and traffic management capabilities, while the serverless platform handles the execution of serverless functions. This allows organizations to benefit from the scalability and cost-effectiveness of serverless architectures.