
45+ [REAL TIME] PWC Interview Questions and Answers
Last updated on 30th Apr 2024, Popular Course
Formerly called PricewaterhouseCoopers, PwC is one of the biggest providers of professional services globally. It provides a broad range of services, such as advice services, tax consulting, audit and assurance, and legal support. With more than 150 member firms, PwC functions as a global network that employs hundreds of thousands of professionals. The company provides services to clients in a number of different industries, such as consumer markets, energy, healthcare, technology, and financial services. PwC is renowned for its knowledge, honesty, and dedication to supporting clients in overcoming difficult obstacles and realizing their corporate objectives.
1. What is PwC?
Ans:
PwC, known as PricewaterhouseCoopers, is a global professional services network that offers a range of services, including audit, consulting, tax, and assurance, across more than 150 countries. Renowned for its expertise in advisory, strategy, and risk management, PwC aids businesses in overcoming complex challenges. With a reputation for quality and innovation, PwC stands as one of the largest firms in its sector worldwide.
2. What does RDBMS stand for?
Ans:
- RDBMS stands for Relational Database Management System, which is essential software for efficient database management.
- It facilitates the creation, updating, and management of relational databases, ensuring smooth operations.
- Leading examples like MySQL, Oracle, and SQL Server enforce data integrity through features such as ACID properties.
- RDBMS plays a pivotal role in handling structured data efficiently.
3. What is DML or Data Manipulation Language?
Ans:
DML, an abbreviation for Data Manipulation Language, operates within the SQL framework. This subset of SQL commands, including INSERT, UPDATE, DELETE, and SELECT, manipulates data within relational databases. Essential for data consistency and integrity, DML operations ensure effective management of database content.
4. What are the characteristics of Vectors?
Ans:
- Vectors, serving as one-dimensional arrays, hold elements of a uniform data type.
- They maintain a fixed size, allowing access through zero-based indices.
- Supporting random access, vectors efficiently retrieve elements.
- Additionally, they dynamically adjust size, expanding or contracting as elements are added or removed
5. What is the difference between linear and non-linear data structures?
Ans:
| Aspect | Elements arranged sequentially | Elements connected in multiple ways |
|---|---|---|
| Examples | Arrays, Linked Lists, Stacks, Queues | Trees, Graphs |
| Traversal | Sequential traversal from start to end | May require specialized traversal algorithms |
| Memory Allocation | Contiguous memory allocation | Dynamic memory allocation, pointers/references |
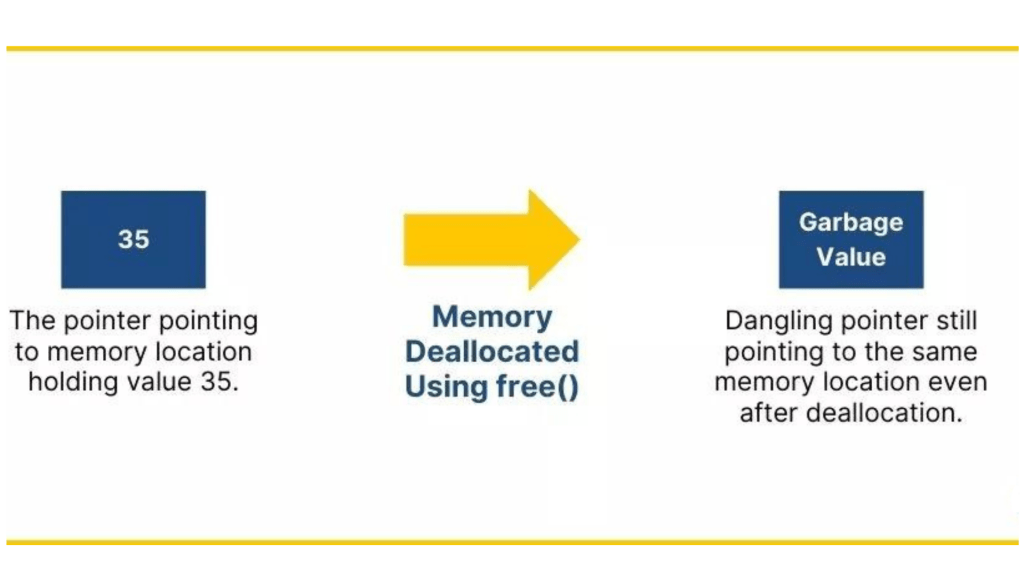
6. What is a Dangling Pointer?
Ans:
A dangling pointer points to deallocated memory. Dereferencing such a pointer can result in unpredictable program behavior. Typically arising from outdated pointer values post-deallocation, dangling pointers may lead to crashes or security vulnerabilities. Proper memory management is essential to prevent these issues.
7. What do you mean by Assessment Year?
Ans:
- Assessment Year denotes the period for evaluating income for taxation purposes.
- Following the Financial Year when income was earned, it determines applicable tax rates and deductions.
- For example, income earned in FY 2023-2024 undergoes assessment in the following year, denoted as the Assessment Year 2024-2025.
- During this period, taxpayers file returns and fulfill tax obligations.
8. What do you mean by Financial Year?
Ans:
The Financial Year spans twelve months for financial reporting and accounting purposes. It commences on April 1st and concludes on March 31st of the subsequent year. Crucial for financial planning and taxation, the Financial Year guides budgeting and financial statement preparation. Understanding the Financial Year aids organizations in managing finances effectively.
9. What is a Statutory Audit?
Ans:
A Statutory Audit, mandated by law, verifies the accuracy of financial statements. Conducted by external auditors, it ensures compliance with legal and regulatory requirements. Detecting irregularities and providing assurance to stakeholders, a Statutory Audit enhances transparency and trust in financial reporting.
10. What is the purpose of Statutory Audit?
Ans:
- The purpose of a Statutory Audit is to offer an independent evaluation of financial statements.
- Ensuring a fair and accurate representation of an entity’s financial position, it guards against misstatements and fraud.
- Providing assurance to stakeholders and ensuring compliance with regulations are essential objectives.
- Ultimately, a Statutory Audit enhances transparency and credibility in financial reporting.
11. What is Internal Audit?
Ans:
Internal audit offers independent assurance and consulting services to enhance organizational value. Its focus lies in evaluating and improving risk management, control, and governance processes. Auditors assess internal controls and offer suggestions for improvement. Reporting directly to top management, they ensure transparency and accountability. In summary, internal audits play a vital role in fostering organizational efficiency and compliance.
12. What are the advantages of Internal Audit?
Ans:
- Internal audits pinpoint operational weaknesses, fostering enhanced efficiency and risk management strategies.
- They furnish management with insightful data, aiding informed decision-making and bolstering governance structures.
- Internal audits ensure regulatory compliance, mitigating legal risks and potential penalties effectively.
13. What are some advantages of proprietorship?
Ans:
- Proprietorship simplifies management and decision-making due to its single-owner structure.
- It grants direct control over operations and profits, facilitating prompt decision-making processes.
- With lower startup costs and fewer regulatory obligations, proprietorships offer a streamlined business setup.
14. What are some disadvantages of proprietorship?
Ans:
- Owners face unlimited liability, risking personal assets against business debts and obligations.
- Capital raising and financing can be challenging due to the limited resources inherent in a single-owner setup.
- The continuity of the business may be jeopardized by the owner’s illness, death, or retirement.
15. What do you mean by Amortization and Impairment?
Ans:
Amortization spreads the cost of intangible assets over their useful life, reflecting their gradual consumption or value reduction. Impairment occurs when an asset’s carrying amount exceeds its recoverable amount, leading to recognized decreases in value in financial statements.
16. What are Intercompany Reconciliation reports?
Ans:
- These reports reconcile transactions and balances among different entities or departments within an organization.
- They ensure financial accuracy and consistency by identifying and rectifying discrepancies across intercompany accounts.
17. What is a Stored Procedure?
Ans:
A stored procedure can be called by name and is a precompiled set of one or more SQL statements and procedural logic that is kept in a database management system (DBMS). On a database server, stored procedures are usually used to encapsulate and carry out commonly used database activities, including queries, data manipulation, and business logic.
18. Why do we create indexes?
Ans:
- Indexes enhance database query performance by expediting data retrieval processes.
- They organize data systematically, reducing the necessity for full-table scans and speeding up search operations.
19. What are the characteristics of Arrays?
Ans:
- Ordered Collection: Arrays store elements in a linear order, with each element having a unique index.
- Fixed Size: Once created, the size of an array typically remains constant, although some languages support dynamic resizing.
- Homogeneous Elements: Arrays usually contain elements of the same data type, ensuring uniformity.
- Random Access: Elements in an array can be accessed directly using their index, allowing for efficient random access.
20. Define BCNF.
Ans:
- BCNF (Boyce-Codd Normal Form) is a database normalization form that eliminates certain anomalies by ensuring every determinant serves as a candidate key.
- It minimizes redundancy and dependency issues within a relational database schema, thereby enhancing data integrity and efficiency.
21. What are the differences between symmetric and asymmetric encryption?
Ans:
Symmetric encryption is faster and more efficient for large data volumes, whereas asymmetric encryption is slower but eliminates the need for secure key exchange. Symmetric encryption is used for bulk data encryption, while asymmetric encryption is often used for key exchange and digital signatures.
22. How does digital signature function in asymmetric encryption?
Ans:
- Digital signatures in asymmetric encryption use the sender’s private key to encrypt a hash of the message, which can be decrypted using the sender’s public key.
- This process ensures message integrity and authenticity, as only the sender’s private key can create a valid signature.
- Recipients verify the signature using the sender’s public key, confirming the message’s origin and integrity.
23. What is the significance of Diffie-Hellman key exchange in cryptography?
Ans:
Diffie-Hellman key exchange allows two parties to securely establish a shared secret key over an insecure channel. It enables secure communication without the need for pre-shared keys, addressing the key distribution problem in symmetric encryption. The algorithm ensures that even if an attacker intercepts the communication, they cannot determine the shared secret key without solving the discrete logarithm problem.
24. Concept of one-way hash function?
Ans:
- One-way hash functions irreversibly convert input data into a fixed-size hash value.
- It’s computationally infeasible to reverse the process or find two inputs that produce the same hash (collision resistance).
- They are commonly used for data integrity verification, password hashing, and digital signatures.
25. Brute-force vs. dictionary attacks in encryption?
Ans:
- Brute-force attacks systematically try all possible combinations to crack a password or encryption key.
- Dictionary attacks use a predefined list of common passwords or phrases to attempt to gain unauthorized access.
- Brute-force attacks are more exhaustive but time-consuming, while dictionary attacks are faster but depend on the quality of the dictionary.
26. Role of certificate authority in asymmetric encryption trust?
Ans:
- Certificate authorities (CAs) issue digital certificates that verify the authenticity of entities in asymmetric encryption.
- CAs validate the identity of entities and bind their public keys to their identities through digital certificates.
- Users trust CAs to ensure that public keys presented by entities are genuine and have not been tampered with.
27. Encryption padding: explanation?
Ans:
Encryption padding involves adding extra bits to the plaintext before encryption to ensure it meets the block size requirements of the encryption algorithm. It prevents attackers from identifying patterns in the encrypted data, enhancing security. Padding schemes include PKCS#5/PKCS#7 and ANSI X.923, which specify how to add and remove padding.
28. What is the importance of randomness in encryption?
Ans:
- Randomness ensures unpredictability, making it harder for attackers to guess or deduce encrypted data.
- It strengthens encryption by introducing complexity and enhancing security against brute-force attacks.
- Randomness helps generate unique keys and initialize vectors and nonces, which are crucial for encryption protocols.
- Without randomness, patterns or repetitions in encrypted data may be exploited, weakening security.
- It enhances the resilience of encryption algorithms against cryptanalysis and statistical attacks.
29. Contribution of encryption to data privacy and security?
Ans:
Encryption transforms plaintext into ciphertext, safeguarding sensitive information from unauthorized access. It ensures confidentiality by making data unreadable to anyone without the decryption key. Encryption also contributes to data integrity by detecting any unauthorized modifications during transmission. It enhances data privacy, compliance with regulations (such as GDPR), and protection against data breaches.
30. What is the difference between a block cipher and a stream cipher?
Ans:
- Block ciphers process fixed-size blocks of plaintext simultaneously, while stream ciphers encrypt data bit by bit or byte by byte.
- Block ciphers are suited for encrypting large volumes of data, while stream ciphers are more efficient for real-time communication or low-bandwidth scenarios.
- Block ciphers require padding for input that doesn’t fit perfectly into blocks, whereas stream ciphers can handle arbitrary lengths of data.
- Block ciphers are typically used in symmetric encryption, while stream ciphers are commonly employed in both symmetric and asymmetric encryption.
31. How does symmetric encryption secure data transmission?
Ans:
The sender encrypts data using this shared key before transmission. Only the authorized recipient with the same key can decrypt the data. This process maintains confidentiality, thwarting unauthorized access. Symmetric encryption algorithms effectively secure data during its journey across networks. By ensuring data integrity, symmetric encryption bolsters secure communication channels.
32. Common vulnerabilities in symmetric encryption?
Ans:
- Weaknesses include challenges in securely distributing keys.
- The vulnerability arises from poor key generation, facilitating brute-force attacks.
- Symmetric encryption may be susceptible to chosen-ciphertext attacks if improperly implemented.
- The compromise of the encryption algorithm itself poses a significant risk.
- Inadequate protection of keys during storage or transmission heightens the threat of breaches.
- Reusing keys across different sessions introduces a notable security risk.
33. Digital envelope in cryptography: explanation?
Ans:
A digital envelope encrypts a message using symmetric encryption. Initially, a random symmetric key encrypts the message. This key is further encrypted with the recipient’s public key—the resultant encrypted message and symmetric key form the digital envelope. Upon receipt, the recipient decrypts the symmetric key with their private key. Subsequently, they use this key to decrypt the enclosed message.
34. How does the RSA algorithm handle message encryption and decryption
Ans:
- RSA, an asymmetric encryption algorithm, employs public and private keys.
- The sender encrypts messages with the recipient’s public key.
- RSA’s security relies on the complexity of prime factorization.
- Its strength lies in the challenge of factoring large prime numbers.
- This mechanism ensures secure message transmission in RSA encryption.
35. What is the importance and concept of key length in encryption?
Ans:
- Key length is pivotal in determining encryption strength.
- Longer keys heighten resistance against brute-force attacks.
- They increase the number of possible combinations, bolstering security.
- Longer keys exponentially prolong the decryption duration.
- Hence, selecting an appropriate key length is essential for robust encryption.
- Key length directly influences computational demands in encryption and decryption.
36. Role of nonce in encryption protocols like TLS?
Ans:
A nonce, or unique random value, is generated for each encryption session. It thwarts replay attacks by ensuring session key uniqueness. Nonces, integral in protocols like TLS, bolster security during key exchange. They prevent interception and reuse of encrypted data from prior sessions. Employed alongside cryptographic algorithms, nonces introduce randomness and uniqueness. Their inclusion enhances encrypted communication channel integrity and security.
37. How does PKI enhance asymmetric encryption security?
Ans:
PKI (Public Key Infrastructure) facilitates digital certificate management. It verifies the authenticity of associated public keys in asymmetric encryption. Utilizing certificate authorities, PKI validates and issues digital certificates. These certificates bind public keys to their respective owners’ identities.PKI safeguards key exchange, mitigating man-in-the-middle threats. By instilling trust in public keys, PKI fortifies the security of asymmetric encryption.
38. Concept of forward secrecy in encryption protocols?
Ans:
- Forward secrecy safeguards session keys from compromise, even if long-term keys are exposed.
- It achieves this by generating unique session keys for each session.
- Adversaries cannot decrypt prior sessions, even with long-term key access.
- Forward secrecy defends against future vulnerabilities and breaches.
- It is vital for preserving confidentiality and security in encrypted communication.
- Many secure protocols, including TLS, incorporate forward secrecy for enhanced protection.
39. What are the examples and purposes of hybrid encryption schemes?
Ans:
- Hybrid encryption amalgamates symmetric and asymmetric encryption strengths.
- Typically, symmetric encryption secures the bulk of data.
- The symmetric key encrypts, while the recipient’s public key encrypts the symmetric key.
- This approach balances efficiency and security, leveraging symmetric encryption’s speed.
- Hybrid encryption is prevalent in secure communication and data transmission.
40. Impact of quantum computing on encryption?
Ans:
It can swiftly solve problems like integer factorization and jeopardizing RSA. Similarly, it undermines discrete logarithm problems, impacting the Diffie-Hellman key exchange. Post-quantum cryptography aims to develop quantum-resistant encryption. Cryptographers explore alternatives like lattice-based cryptography. Quantum computing accelerates the necessity for transitioning to quantum-safe encryption standards.
41. What is the significance of elliptic curve cryptography?
Ans:
Elliptic curve cryptography offers stronger security with shorter key lengths compared to traditional methods. It is highly efficient, making it ideal for resource-constrained environments like mobile devices and IoT devices. Its resistance to quantum computing threats makes it a future-proof choice for encryption. Elliptic curve cryptography is widely used in modern cryptographic protocols like TLS and PGP.
42. How does homomorphic encryption enable computations on encrypted data?
Ans:
- It preserves data privacy by ensuring sensitive information remains encrypted throughout processing.
- This enables secure outsourcing of computation tasks to untrusted third parties.
- Homomorphic encryption schemes support operations like addition and multiplication on ciphertexts.
- Applications include privacy-preserving data analysis and secure cloud computing.
- However, homomorphic encryption introduces computational overhead due to complex algorithms.
43. Relation of steganography to encryption?
Ans:
Steganography hides a message’s existence, while encryption disguises its contents. Steganography conceals messages within other harmless-looking data, such as images or audio files. Encryption scrambles the content of a message to make it unreadable without the proper decryption key. Steganography and encryption can be combined to provide layered security for sensitive information.
44. Role of entropy in cryptographic key generation?
Ans:
- Entropy is crucial for generating unpredictable cryptographic keys.
- High entropy ensures that generated keys are resistant to brute-force attacks.
- Entropy sources, like random number generators, provide randomness for key generation.
- Insufficient entropy can lead to weak keys, compromising the security of cryptographic systems.
- Cryptographic protocols rely on high entropy to ensure key secrecy and randomness.
- Adequate entropy strengthens the overall security posture of cryptographic systems.
45. Common attacks on encryption and mitigation strategies?
Ans:
Common attacks include brute force, ciphertext-only, and chosen-plaintext attacks. Mitigation strategies include using strong encryption algorithms and long key lengths. Implementing proper key management practices can prevent key compromise attacks. Regularly updating encryption protocols and algorithms helps mitigate known vulnerabilities. Utilizing secure communication channels and enforcing access controls add layers of defense.
46. Role of digital certificates in asymmetric encryption?
Ans:
Digital certificates bind public keys to entities, providing a means of identity verification. They are issued by trusted certificate authorities (CAs) after verifying the identity of the certificate holder. Digital certificates facilitate secure communication by enabling parties to authenticate each other’s identities. In asymmetric encryption, digital certificates ensure the integrity and authenticity of public keys.
47. What are the differences between end-to-end encryption and other methods?
Ans:
- End-to-end encryption ensures that only the sender and recipient can access the plaintext message.
- Other methods, like transport layer security (TLS), encrypt data during transmission but may allow intermediaries to decrypt it.
- End-to-end encryption provides stronger confidentiality and privacy guarantees.
- It prevents unauthorized access to sensitive information even if the communication channel is compromised.
- End-to-end encryption requires encryption and decryption to be performed on the client devices.
48. What is the importance of the initialization vector (IV) in symmetric encryption?
Ans:
- The initialization vector (IV) adds randomness and uniqueness to encrypted data.
- It ensures that identical plaintexts encrypted with the same key produce different ciphertexts.
- IV prevents attackers from deducing patterns in encrypted data, enhancing security.
- Without an IV, repeated encryption of the same plaintext with the same key results in identical ciphertexts.
- IV is essential for secure encryption modes like CBC (Cipher Block Chaining) and GCM (Galois/Counter Mode).
49. What is the concept of key management in encryption systems?
Ans:
Key management involves securely generating, storing, distributing, and revoking cryptographic keys. It ensures that keys are accessible to authorized users while protecting them from unauthorized access. Key rotation and renewal practices help mitigate the risk of key compromise. Proper key lifecycle management includes key generation, usage, storage, and destruction phases.
50. How do encryption algorithms ensure data integrity?
Ans:
Encryption algorithms often incorporate integrity protection mechanisms, such as message authentication codes (MACs).MACs verify the integrity of encrypted data by generating a cryptographic checksum or tag. Encryption algorithms may also use cryptographic hash functions to verify data integrity before or after encryption. Combined with encryption, integrity protection mechanisms provide comprehensive security against data tampering.
51. Real-world applications of encryption beyond secure communication?
Ans:
- Encryption secures financial transactions, protecting banking systems from fraud.
- It safeguards healthcare data, ensuring patient privacy and compliance with regulations.
- Encryption secures data in cloud storage, preventing unauthorized access.
- It protects intellectual property in digital rights management systems.
- Encrypted messaging apps ensure privacy for sensitive communications.
52. Is the adoption of the AES encryption algorithm working?
Ans:
- AES (Advanced Encryption Standard) operates through substitution and permutation.
- It has widespread adoption due to its robustness and efficiency.
- AES uses a fixed block size of 128 bits and key sizes of 128, 192, or 256 bits.
- It employs multiple rounds of transformation for encryption and decryption.
- AES has become a standard for securing sensitive data in various applications.
- Its adoption is driven by its security, speed, and standardization by NIST.
53. Explanation of cryptographic nonce?
Ans:
A cryptographic nonce is a number used only once in cryptographic communication. It enhances security by preventing replay attacks and ensuring freshness. Nonces are typically randomly generated and included in cryptographic protocols. They are used in key exchange protocols like Diffie-Hellman to prevent replay attacks. Cryptographic nonces must be unpredictable to thwart adversaries’ attempts to predict or reuse them.
54. What is the significance of the birthday paradox in a key generation?
Ans:
The birthday paradox highlights the probability of collisions in randomly generated values. In a key generation, it underscores the likelihood of generating duplicate keys in large key spaces. This emphasizes the importance of ensuring keys are generated from a space large enough to minimize collisions. Proper key generation mitigates the risk of attackers guessing or brute-forcing keys.
55. How does perfect forward secrecy enhance security?
Ans:
- Perfect forward secrecy (PFS) ensures that past sessions’ encryption keys cannot be compromised.
- PFS generates unique session keys for each session, limiting the impact of a key compromise.
- It protects against retrospective decryption of past communications.
- PFS is crucial in scenarios where long-term keys might be vulnerable, such as in data breaches.
- Implementing PFS enhances overall security posture by limiting the scope of potential breaches.
56. Role of symmetric encryption in data-at-rest security?
Ans:
- Symmetric encryption secures data at rest using a single shared secret key.
- It ensures confidentiality by encrypting data using the same key for encryption and decryption.
- Symmetric encryption is efficient for large volumes of data.
- It’s commonly used in storage devices, databases, and file systems.
- Secure storage systems employ symmetric encryption to protect sensitive information.
- Key management is critical in symmetric encryption to maintain security.
57. What is the impact of the mode of operation on block cipher security and performance?
Ans:
The mode of operation determines how a block cipher encrypts plaintext of arbitrary length. Modes like ECB are vulnerable to data patterns and offer poor security.CBC mode enhances security by chaining ciphertext blocks, but parallelization is limited.GCM mode combines encryption with authentication, offering both confidentiality and integrity. Performance varies among modes due to factors like parallelizability and computational overhead.
58. Challenges in implementing encryption in large-scale systems?
Ans:
Key management becomes complex with a large number of users and devices. Ensuring performance scalability while maintaining security is challenging. Compatibility issues may arise when integrating encryption across diverse systems. Secure transmission and storage of encryption keys pose logistical challenges. Balancing security requirements with usability and performance can be difficult.
59. Key exchange process in secure protocols like TLS?
Ans:
- In TLS, key exchange begins with client and server exchanging capabilities and cryptographic parameters.
- They negotiate a cipher suite and agree on a pre-master secret.
- The pre-master secret is encrypted using the server’s public key and sent to the server.
- Both parties derive session keys from the pre-master secret and other parameters.
- The session keys are then used for symmetric encryption and data decryption.
- The key exchange process ensures secure communication channels between client and server.
60. Concept of ciphertext indistinguishability in encryption?
Ans:
- Ciphertext indistinguishability means that an adversary cannot distinguish between two ciphertexts.
- It’s a fundamental property in modern encryption schemes.
- Indistinguishability ensures that encrypted data reveals no information about the plaintext.
- Adversaries cannot discern patterns or gain insights from encrypted messages.
- Achieving indistinguishability is essential for security against chosen-plaintext attacks.
61. What is purpose of salt in password hashing?
Ans:
Salting introduces random data to each password before hashing. This measure prevents attackers from leveraging precomputed tables. It elevates the complexity of password-cracking attempts. Security is bolstered by ensuring unique hashes for each password. Salting acts as a deterrent against dictionary and rainbow table attacks. Ultimately, it fortifies the overall integrity of password storage.
62. How does a rainbow table attack exploit password hashing weaknesses?
Ans:
Rainbow tables consist of precomputed hash value tables. Attackers exploit these tables by matching hashes to plaintext passwords. Such an attack capitalizes on the predictability of hash functions. It enables rapid reverse-lookup of passwords. Rainbow table attacks can bypass conventional hashing defenses. They are particularly effective against unsalted hashes.
63. Concept of cryptographic agility in encryption?
Ans:
- Cryptographic agility denotes the adaptability of encryption algorithms.
- It allows systems to switch algorithms as required.
- This capability safeguards against vulnerabilities in algorithms.
- Cryptographic agility ensures resilience against evolving threats.
- It facilitates seamless upgrades and changes in encryption methods.
- Ultimately, it enhances long-term security planning.
64. Role of key stretching in password-based encryption?65. Man-in-the-middle attack in an encryption context?
Ans:
- Key stretching prolongs the time required for brute-forcing passwords.
- Encryption keys are derived from passwords through iterative hashing algorithms.
- This process incurs computational overhead during key derivation.
- Key stretching bolsters resistance against dictionary and rainbow table attacks.
- It significantly enhances the security of password-based encryption.
- Ultimately, key stretching reinforces the defense mechanisms of password encryption.
65. Man-in-the-middle attack in an encryption context?
Ans:
The attacker impersonates both ends of the communication. Through this interception, they can decrypt and read intercepted data. This attack vector facilitates the alteration or injection of data. Significantly, it occurs without the knowledge of the communicating parties. Ultimately, it undermines the confidentiality and integrity of communication.
66. What is the Difference between data encryption at rest and in transit?
Ans:
- On the other hand, encryption in transit safeguards data during transmission.
- At rest, encryption protects against unauthorized access to stored data.
- Encryption in transit ensures data security during communication between systems.
- Different protocols and mechanisms may be employed for each scenario.
- Both methods aim to maintain data confidentiality and integrity.
67. Role of Initialization Vector (IV) in encryption?
Ans:
- The Initialization Vector (IV) is a random value utilized in encryption algorithms.
- Its primary function is to prevent the repetition of encrypted patterns.
- By ensuring unique ciphertext, the IV enhances security.
- Certain encryption modes, like CBC, require the use of an IV.
- The IV, combined with the key, encrypts plaintext data.
- Overall, the IV is critical for maintaining confidentiality and preventing attacks.
68. Impact of cipher mode choice on encrypted data security?
Ans:
Cipher mode dictates how plaintext data is encrypted. This choice affects security, speed, and parallelization capabilities. Some modes offer better security against specific attacks than others. For instance, the ECB mode lacks diffusion, making it less secure. Popular and secure modes include CBC, CTR, and GCM. Ultimately, the choice of cipher mode depends on specific security and performance requirements.
69. Explanation of digital rights management (DRM) and its relation to encryption.
Ans:
DRM manages access and usage rights of digital content. It utilizes encryption to protect content from unauthorized access.DRM oversees rights and permissions for content usage. Through encryption keys and access controls, it enforces restrictions on copying, sharing, and modifying content.DRM strikes a balance between content owner’s rights and user access and usability. Ultimately, DRM relies on encryption to safeguard digital content.
70. What is the relationship between ciphertext length and encryption scheme security?
Ans:
- Longer ciphertexts generally indicate stronger encryption.
- Increased complexity in longer ciphertexts makes them harder to crack.
- More extended ciphertexts provide greater cryptographic entropy.
- However, length alone does not guarantee security.
- The security of the encryption scheme depends on the algorithm and key length.
- Achieving optimal security requires a balance between length, algorithm, and key strength.
71. What is the role of the key derivation function (KDF) in encryption protocols?
Ans:
- KDFs derive cryptographic keys from a source material.
- They ensure keys are secure and consistent.
- KDFs enhance security by making keys resistant to brute-force attacks.
- They provide a way to generate multiple keys from a single secret.
- KDFs are crucial in key management systems.
- They strengthen encryption by producing keys with high entropy.
72. How does public key pinning enhance web encryption security?
Ans:
Public key pinning binds a host to a specific public key. It defends against rogue certificate authorities and prevents malicious certificate substitution. It enhances trust by ensuring only designated keys are accepted. It helps detect man-in-the-middle attacks and increases security by limiting acceptable certificates.
73. Common encryption standards and their applications?
Ans:
- AES (Advanced Encryption Standard) for symmetric encryption in various applications.
- RSA for asymmetric encryption, especially in digital signatures and key exchange.
- TLS/SSL is used to secure network communications over the internet.
- DES (Data Encryption Standard) for legacy systems.
- ECC (Elliptic Curve Cryptography) for resource-constrained environments.
- PGP (Pretty Good Privacy) for email encryption and digital signatures.
74. What is the concept of a cryptographic backdoor and its security implications?
Ans:
A backdoor is a deliberate vulnerability inserted into a cryptographic system. It allows unauthorized access while appearing secure. Backdoors undermine trust and compromise security. They can be exploited by attackers or abused by authorities. Backdoors pose risks of data breaches and privacy violations. They weaken overall system integrity and resilience.
75. What is the Difference in key lengths between symmetric and asymmetric encryption?
Ans:
- Symmetric encryption typically uses shorter key lengths (e.g., 128 to 256 bits).
- Asymmetric encryption requires longer key lengths due to its complexity (e.g., 1024 to 4096 bits).
- Shorter symmetric keys offer comparable security to longer asymmetric keys.
- Asymmetric encryption’s longer keys are necessary for its security.
- Key length affects encryption strength and computational requirements.
- Balancing security and performance is crucial in choosing key lengths.
76. Contribution of quantum key distribution to secure communication?
Ans:
- It utilizes principles of quantum mechanics for secure communication.
- QKD detects eavesdropping attempts through quantum properties.
- It provides unconditional security based on physical laws.
- QKD ensures secret keys are exchanged without an interception.
- It promises future-proof encryption that is resistant to quantum attacks.
77. What is the description of zero-knowledge proofs and their relevance to encryption?
Ans:
Zero-knowledge proofs verify the truth of a statement without revealing the information itself. They ensure privacy while validating data integrity. Zero-knowledge proofs are crucial in authentication and access control systems. They enable secure transactions without disclosing sensitive data. The relevance lies in privacy-preserving authentication and cryptographic protocols.
78. How does salt enhance password storage security?
Ans:
Salt is random data added to passwords before hashing. It prevents identical passwords from producing the same hash. Salt mitigates rainbow table attacks by increasing complexity. It adds uniqueness to each hashed password, enhancing security. Salt defends against precomputed hash attacks. It’s essential in secure password storage practices.
79. What are the common methods for securely storing encryption keys?
Ans:
- Hardware Security Modules (HSMs) for physical protection of keys.
- Key Management Systems (KMS) for centralized key storage and management.
- Secure Enclaves or Trusted Execution Environments (TEEs) for isolated key storage.
- Split-key encryption, where keys are divided among multiple parties.
- Use of strong encryption and access controls for stored keys.
- Regular key rotation and auditing to maintain security.
80. What is the role of a passphrase in enhancing encryption key security?
Ans:
- Passphrases add a layer of security to encryption keys.
- Passphrases increase resistance to brute-force and dictionary attacks.
- They strengthen key-based encryption by protecting against unauthorized access.
- Passphrases can be used to generate cryptographic keys.
- Their role is vital in securing encrypted data and communications.
81. Concept of the digital timestamp in cryptographic protocols?
Ans:
Digital timestamps authenticate cryptographic operations by indicating the time of occurrence. They prevent replay attacks and establish chronological order in events. Trusted third parties often generate these timestamps. In protocols like TLS, timestamps validate session continuity. Digital timestamps reinforce non-repudiation in digital signatures. Overall, they enhance the security and reliability of cryptographic transactions.
82. Contribution of hardware security modules (HSMs) to encryption security?
Ans:
HSMs provide secure storage and management of encryption keys, create tamper-resistant environments for cryptographic operations, contribute to key generation, and safeguard key material. They also ensure protection against physical and logical attacks and maintain compliance with security standards and regulations. Ultimately, HSMs significantly bolster encryption security.
83. Challenges in implementing end-to-end encryption in messaging apps?
Ans:
- Ensuring both a seamless user experience and robust security is challenging.
- Key management, including secure exchange and storage, poses a significant hurdle.
- Balancing encryption strength with computational resources is crucial.
- Safeguarding metadata and ensuring its protection adds complexity.
- Legal and regulatory challenges across jurisdictions need to be addressed.
- Achieving interoperability among diverse platforms and devices remains a key obstacle
84. What is the description of a digital signature and its role in data integrity verification?
Ans:
Digital signatures authenticate the sender and integrity of a message or document. They generate a unique signature using the sender’s private key. They ensure data integrity, as any alteration invalidates the signature. They offer non-repudiation, preventing the sender from denying message transmission. Vital for securing electronic transactions and communications, digital signatures play a crucial role.
85. Impact of quantum resistance on encryption algorithm design?
Ans:
- Quantum-resistant algorithms are engineered to withstand such attacks.
- They rely on mathematical problems that are challenging for both classical and quantum computers.
- Development demands extensive research and testing.
- Transitioning to these algorithms requires significant effort and investment.
- Quantum resistance is paramount for future-proofing encrypted data.
86. What is the importance of forward secrecy in encrypted communication?
Ans:
- Forward secrecy secures past communications against compromised keys.
- It thwarts the decryption of previous sessions using compromised keys.
- Protecting against long-term data breaches enhances confidentiality.
- Forward secrecy mitigates risks associated with key exposure.
- Its implementation hinges on efficient key management strategies.
- Ultimately, forward secrecy fortifies encrypted communication security.
87. Explanation of key escrow and its implications for encryption.
Ans:
Key escrow involves entrusting encryption keys to a third party. It permits authorized access to encrypted data under specific circumstances. Concerns arise regarding privacy and security in key escrow arrangements. Compromising escrowed keys could lead to unauthorized access. Balancing lawful access needs with user privacy presents challenges. Key escrow arrangements significantly impact encryption trust and adoption.
88. What is the relationship between trust and encryption protocol security?
Ans:
Trust is pivotal for the adoption and efficacy of encryption protocols. Users must have confidence in the security and correct implementation of protocols. Security breaches undermine trust in encryption. Transparent security practices and independent audits bolster trust. Trust influences users’ willingness to share sensitive information. Maintaining trust is indispensable for widespread encryption use.
89. What is the concept of data masking and its relation to encryption?
Ans:
- Data masking obscures or replaces sensitive data with fictional or randomized values.
- Unlike encryption, it doesn’t mathematically alter the data.
- Primarily used for protecting data in testing or non-production environments.
- While encryption secures data during transit or at rest, data masking obscures it.
- Both techniques contribute to data security, serving distinct purposes.
90. What are the common protocols for secure key exchange in encryption?
Ans:
- Diffie-Hellman key exchange facilitates shared secret agreement over an insecure channel.
- RSA key exchange involves exchanging keys using the RSA algorithm.
- Elliptic Curve Diffie-Hellman (ECDH) employs elliptic curve cryptography.
- Key Exchange Algorithms in SSH (Secure Shell) enable secure remote access.
- IKE (Internet Key Exchange) is utilized in IPsec VPNs for secure internet communication.
91. The threat posed by side-channel attacks on encryption systems?
Ans:
Side-channel attacks exploit unintended information leaks. They target the physical implementation of encryption. By monitoring power or timing, they can expose secrets. Encryption algorithms themselves may remain secure. However, vulnerabilities in implementation compromise security. Protecting against them requires meticulous implementation and hardware safeguards.
92. Concept and development of quantum-resistant encryption?
Ans:
Quantum-resistant encryption aims to withstand quantum computer attacks. Shor’s algorithm poses a threat to quantum computers. Post-quantum cryptography explores alternative mathematical problems. Examples include lattice-based or hash-based encryption. These methods are believed to resist quantum attacks. Transitioning to them necessitates extensive research and standardization.
93. What is the role of nonce in preventing replay attacks in encryption?
Ans:
- A nonce is a unique value employed in each encryption session.
- It ensures message freshness, thwarting replay attacks.
- Attackers are unable to reuse intercepted ciphertext to impersonate.
- Nonces are integrated with encryption algorithms.
- They guarantee unique ciphertexts even when plaintexts are identical.
- Effective security requires proper management of nonces.
94. How does multi-factor authentication enhance security in encrypted systems?
Ans:
- Multi-factor authentication necessitates multiple verification steps.
- It adds layers of security beyond password-based methods.
- Factors can include biometrics, tokens, or one-time codes.
- This approach significantly heightens the security threshold.
- It diminishes the likelihood of unauthorized access.
95. Description of perfect secrecy in encryption?
Ans:
- Perfect secrecy ensures that ciphertext reveals no information about the plaintext.
- Claude Shannon introduced this concept in information theory.
- Each key is used for as long as the message and is used only once.
- Without the key, any plaintext is equally probable.
- Achieving perfect secrecy in practice encounters challenges in key management.

