
- Introduction to the Salesforce Security Model
- Importance of Data Security in Salesforce
- Object-Level Security
- Field-Level Security
- Record-Level Security
- Profiles and Permission Sets
- Role Hierarchies and Sharing Rules
- Organization-Wide Defaults (OWD)
- Managing Access with Public Groups
- Using Salesforce Shield for Advanced Security
- Best Practices for Security Configuration
- Monitoring and Auditing Salesforce Security
Introduction to the Salesforce Security Model
Salesforce employs a comprehensive security model to protect data while providing flexible access control mechanisms. This security model is based on enforcing the least privilege, meaning users are granted only the necessary access to the data they need to perform their job duties. The multi-layered model involves multiple levels of security, including user authentication, profiles, roles, sharing rules, and record-level access. It helps maintain data confidentiality, integrity, and availability in a way that complies with organizational needs and legal requirements. For those looking to implement or manage these security protocols effectively, Salesforce Training offers valuable skills to ensure a secure and compliant Salesforce environment.
Importance of Data Security in Salesforce
- Data security is crucial in any enterprise application, including Salesforce.
- Salesforce stores sensitive customer data, and key Features of Salesforce include strong security measures to prevent unauthorized access and breaches.
- Salesforce’s security framework is designed to protect business-critical information.
- Access controls ensure users only view and interact with data they are authorized to access.
- The platform supports compliance with standards such as GDPR, HIPAA, and more.
- Strong data protection helps safeguard customer and employee privacy.
- Maintaining data security builds trust with clients, partners, and stakeholders.
To Explore Salesforce in Depth, Check Out Our Comprehensive Salesforce Training To Gain Insights From Our Experts!
Object-Level Security
Object-level security in Salesforce defines user access to entire Salesforce objects (e.g., Accounts, Contacts, Opportunities). Administrators can determine whether users can view, create, edit, or delete records for a particular object through profiles and permission sets. For example, an employee in the Sales department might be granted full access to Opportunity records but limited or no access to the Case object. This granular access ensures that users only have visibility and control over the documents necessary for their roles and responsibilities.
Field-Level Security
Field-level security provides an additional layer of data protection within an object by controlling user access to specific fields in a record, which is especially important when retrieving data through SOQL Queries. This feature ensures that even though a user may have access to an entire object, they might be unable to view or modify specific sensitive fields. For instance, while users can access the Account object, they might not have permission to view or edit fields such as “Annual Revenue” or “Social Security Number.” Field-level security is vital for safeguarding sensitive data and preventing unauthorized access or accidental changes to critical information.
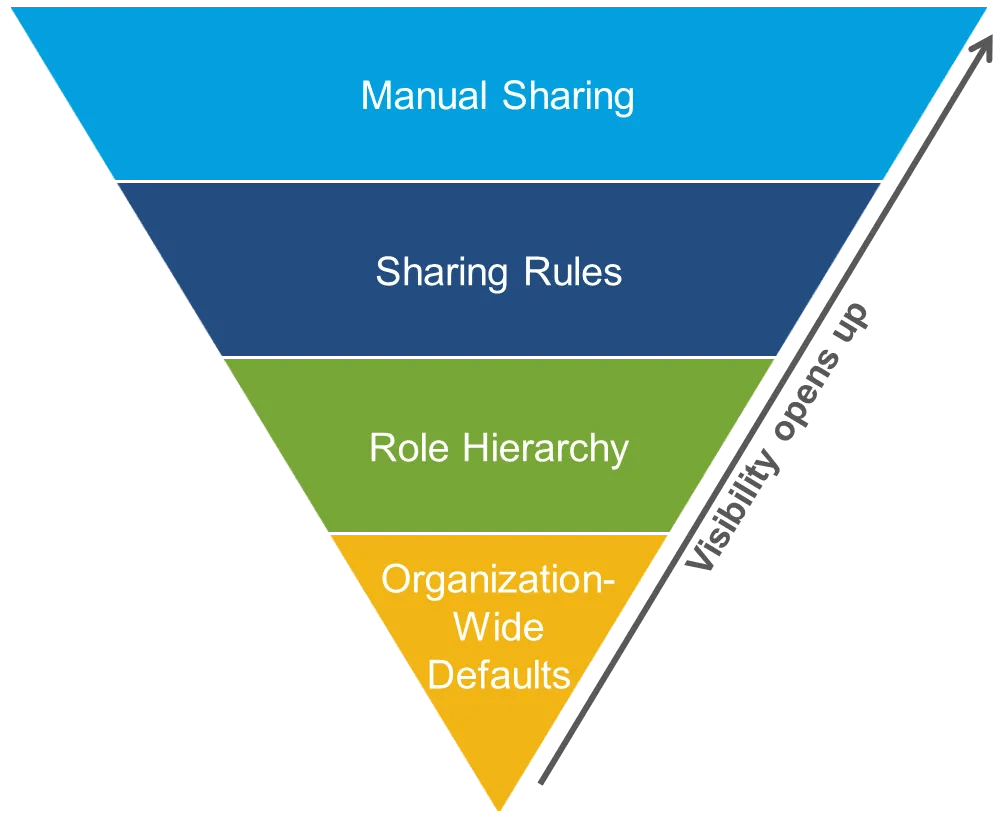
Record-Level Security
- Record-level security controls who can access and modify individual records within Salesforce.
- Object-level permissions do not guarantee access to every record within that object.
- Salesforce enforces record-level security using role hierarchies, sharing rules, and manual sharing.
- Role hierarchies allow users higher in the hierarchy (e.g., managers) to access records owned by subordinates.
- Sharing rules extend access to records based on criteria such as ownership or field values.
- Manual sharing enables individual users to grant record access to specific users.
- This layered approach ensures sensitive or confidential data is only accessible to authorized users.
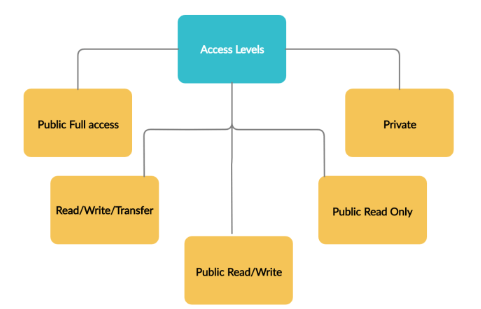
- Public Read/Write: All users can view and modify records.
- Public Read Only: Users can view records; only the record owner and admins can edit them.
- Private: Only the record owner and users with explicit access can view or modify records.
- Controlled by Parent: In related records like Contacts and Accounts, access is controlled by the parent. Setting proper OWD values and using APEX In Salesforce ensures secure, customized access.
- Apply the Principle of Least Privilege by granting users only the minimum access needed to perform their tasks.
- Conduct regular audits of profiles, roles, and permissions to ensure alignment with security policies and organizational needs.
- Enforce strong password policies, including requirements for complexity and expiration.
- Enable Multi-Factor Authentication (MFA) for all users to enhance account security.
- Use profiles and permission sets efficiently to reduce complexity while maintaining strong access control.
- Review access settings periodically to adapt to evolving business and security requirements.
Do You Want to Learn More About Salesforce? Get Info From Our Salesforce Training Today!
Profiles and Permission Sets
Profiles and permission sets are fundamental components of Salesforce’s security model. A profile is a collection of settings that define a user’s permissions across Salesforce objects and features, including object-level access, field-level access, and login restrictions. Profiles are typically assigned to groups of users with similar job functions. Permission Sets, on the other hand, are additional layers of permissions that can be assigned to specific users on top of their profiles. This flexibility allows administrators to fine-tune user access, granting them additional permissions without altering their entire profile. Salesforce Training can help administrators understand and implement these security features effectively, ensuring proper user access control.
Role Hierarchies and Sharing Rules
Salesforce’s role hierarchy allows administrators to define a structure that determines the visibility and access to records based on the user’s role within the organization, and this can work alongside Context Variables to ensure users see only the data relevant to their role and action. A higher-level user, such as a manager, can automatically access records owned by users in lower-level roles. In combination with sharing rules, administrators can further control record access by creating rules based on ownership or criteria. For instance, a sharing rule might allow all users in the “Sales” role to access Opportunity records belonging to the “Marketing” role. This layered approach will enable organizations to enforce business-specific access requirements.
Looking to Master Salesforce? Discover the Salesforce Masters Course Available at ACTE Now!
Organization-Wide Defaults (OWD)
The Organization-Wide Default (OWD) settings in Salesforce define the baseline level of access for records in an organization. These settings apply to all records in Salesforce and set the foundation for record visibility. Salesforce offers several OWD options:
Managing Access with Public Groups
Public groups in Salesforce are collections of users, roles, or other groups. They allow administrators to define access to records more efficiently by grouping users who need similar access permissions. Public groups can be leveraged in sharing rules, where records are shared with the group members based on criteria or ownership. For example, a public group of sales representatives might be granted access to all opportunities within a particular region. This makes it easier to manage access for large numbers of users without configuring individual sharing rules for each user.
Using Salesforce Shield for Advanced Security
Salesforce Shield offers advanced security tools like Event Monitoring to track user activity and detect threats. Earning a Salesforce Certification helps professionals better understand and manage these security features. Platform Encryption offers end-to-end encryption for data at rest and in transit, ensuring that sensitive information is protected. Additionally, Field Audit Trail helps organizations maintain detailed logs of changes made to records, ensuring compliance with regulatory requirements. These tools help organizations secure their Salesforce environment and comply with industry regulations.
Preparing for a Salesforce Job Interview? Check Out Our Blog on Salesforce Interview Questions & Answer
Best Practices for Security Configuration
Monitoring and Auditing Salesforce Security
Salesforce offers powerful tools for monitoring and auditing security within the platform. Login History provides detailed logs of user login attempts, showing successful and failed ones. The Setup Audit Trail captures changes to Salesforce configurations, allowing administrators to track modifications to security settings or user permissions. By enrolling in Salesforce Training, administrators can gain a deeper understanding of how to effectively utilize these tools to maintain a secure environment. For more detailed activity monitoring, Event Monitoring offers insights into user interactions with data, helping identify potential security threats or misuse. These auditing and monitoring tools ensure that organizations can quickly detect and respond to security risks. By following these practices and utilizing Salesforce’s various security features, administrators can maintain a secure, compliant, and efficient environment that protects sensitive data while ensuring the right users have the appropriate access.





