
MAQ Software is a global IT services company specializing in software development, cloud solutions, and digital transformation. They offer a range of services, including application development, data analytics, and managed services, to help businesses optimize operations and drive growth. Known for their expertise and innovative approach, MAQ Software delivers tailored solutions to meet diverse client needs.
1. What’s MAQ software?
Ans:
MAQ Software is a digital metamorphosis and technology results company that specializes in data operation, analytics, and software development services. Innovated in 2000 and headquartered in Redmond, Washington, the company has sculpted out a niche for itself by offering acclimatized results that help businesses work the power of data to make informed opinions, optimize operations, and enhance client gests.
2. What is meant by BST?
Ans:
A double Hunt Tree( BST) is an abecedarian data structure that organizes rudiments in a hierarchical manner, where each knot contains a unique key and references to its left and right children. The key in each knot is lesser than all keys in the knot’s left subtree and lower than those in the right subtree. This property enables effective searching, insertion, omission, and traversal operations, making BSTs necessary in various operations, such as enforcing wordbooks, precedence ranges, and sorting algorithms.
3. State the differences between C and Java languages.
Ans:
| Aspect | C | Java |
|---|---|---|
| Type | Procedural | Object-Oriented |
| Memory Management | Manual memory management (e.g., malloc, free) | Automatic memory management (Garbage Collection) |
| Platform Dependency | Platform-dependent (compiled to native machine code) | Platform-independent (compiled to bytecode) and runs on Java Virtual Machine (JVM) |
| Pointers | Supports pointers | Does not support pointers (except for references) |
4. What’s the use of indexing in databases?
Ans:
Indexing in databases is a fashion used to speed up the reclamation of records, enhancing the performance of query operations. An indicator is created on one or further columns( fields) of a database table to enable effective quests, sortings, and access to the data records. Analogous to an indicator in a book, a database indicator allows the database operation system( DBMS) to find data without surveying the entire table, significantly reducing the quantum of data read from the fragment and perfecting query response times.
5. What’s the part of the compass resolution driver in C?
Ans:
- The compass resolution driver in C() specifies the environment in which a name is defined, thereby resolving inscrutability and allowing access to global variables, class members, and nested class delineations when the original delineations might overshadow them.
- It enables the unequivocal incantation of a class’s member functions or variables, particularly when an original variable’s name marks a class member’s name.
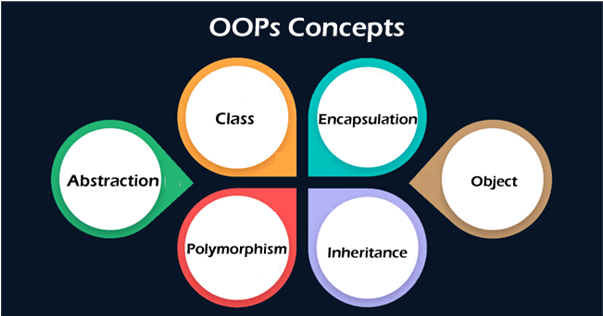
6. Define OOP?
Ans:
Object-acquainted Programming( OOP) is a programming paradigm grounded on the conception of” objects”, which can contain data in the form of fields, frequently known as attributes, and law in the form of procedures, frequently known as styles. OOP aims to apply real-world realities like heritage, caching, polymorphism, etc., in programming. It focuses on the objects that inventors want to manipulate rather than the sense needed to manipulate them. This approach to programming emphasizes modularity, ease of Testing, and reusability of law.
7. What is runtime polymorphism in C, and how is it implemented?
Ans:
Runtime polymorphism in C, also known as dynamic system dispatch, is a process in which a call to an overridden system is resolved at runtime rather than at collection- time. It’s achieved through heritage and virtual functions. When a deduced class overrides a system of its base class, the function to call is determined at runtime grounded on the object’s factual type that’s refocused to by a base pointer rather than the type of the pointer.
8. List the advantages of the Java package.
Ans:
- Namespace Management It helps in organizing classes, interfaces, repetitions, and reflections by furnishing a way to group related types.
- Access Protection Packages allow access control, which enhances security. Classes or interfaces defined in a package can be confined to be accessible within their package or to other packages via the public, private, and defended access modifiers.
- Code Reusability Packages support reusability through the encapsulation of classes. Other programs can work with these packages without demanding to rewrite the classes or interfaces.
9. What is meant by JDK?
Ans:
JDK stands for Java Development Kit. It is a software development environment used to develop Java applications and applets. It includes a comprehensive set of tools for Java programmers, such as a compiler (javac), a Java Virtual Machine (JVM), tools for archiving and documentation, and other utilities necessary for the development process. The JDK is platform-specific, with versions available for Windows, macOS, or Unix/Linux.
10. Define Cloud Computing.
Ans:
Cloud computing is a technology that allows individuals and organizations to access computing resources—such as servers, storage, databases, networking, and software—over the internet on a pay-as-you-go basis. This eliminates the need for substantial upfront capital investments in hardware and allows for scaling resources up or down based on demand. Cloud computing is characterized by its flexibility, scalability, and cost-effectiveness, transforming how businesses operate and scale.
11. What are the different storage classes used in the C language?
Ans:
- The C programming language defines four storehouse classes that determine the lifetime, visibility, memory position, and original value of a variable. They are
- bus The dereliction storehouse class for original variables. Bus variables are automatically allocated and deallocated when the function block in which they’re defined is entered and exited.
- Register Suggests that the variable should be stored in a register rather than RAM to speed up its access. Still, the compiler can ignore this suggestion. Register variables can not be encyclopedically penetrated.
12. What exactly is a reentrant function in C?
Ans:
- A reentrant function in C( and in programming in general) is a function that can be safely called contemporaneously from multiple vestments or recursive calls without causing any non-deterministic geste.
- The crucial specific of a reentrant function is that it doesn’t calculate on or alter the participated state(similar to global or stationary data) without proper synchronization, or it maintains its state entirely within the original compass, using only original variables and parameters.
13. Why must we cover scrap collection nearly?
Ans:
Monitoring scrap collection( GC) is pivotal in managing an operation’s memory and ensuring smooth performance. Garbage collection automates the process of freeing up unused memory, but if not covered, it can lead to issues similar to memory leaks, where objects that are no longer demanded aren’t duly collected, consuming precious memory coffers. Inordinate scrap collection can also beget performance problems, as it can be CPU ferocious, leading to pauses in operation prosecution that affect users’ experience.
14. What’s Reentrancy?
Ans:
This conception is pivotal in concurrent programming environments, where participated coffers might be penetrated by multiple vestments or processes contemporaneously. A reentrant function can be called again without affecting its prosecution. This is frequently achieved by avoiding the participating state or by ensuring that all participating countries are penetrated in a thread-safe manner.
15. Does the return statement and exit() serve the same in C language?
Ans:
- In C, the return statement and the exit() function are used to terminate a program, but they do so in different surroundings and more.
- The return statement is used within a function to end its prosecution and voluntarily return a value to the calling function.
- When used in the main function, it terminates the program and returns control to the operating system, with the return value indicating success or error.
- The exit() function, provided by the standard library(stdlib. h), can be called from anywhere in a program.
16. Why do we have to cover scrap gathering so closely?
Ans:
Monitoring garbage collection is vital for optimal performance and resource management. Poorly optimized garbage collection can lead to increased latency and pauses, especially during full GC cycles. Analyzing GC logs and metrics helps identify and resolve memory leaks, inefficient allocation, and unnecessary object retention that can impact performance. Regular reviews ensure ongoing efficiency and system stability.
17. How is the NULL pointer different from a VOID Pointer in C?
Ans:
A NULL pointer is a pointer that does not point to any memory position; it’s used to signify that the pointer isn’t assigned to any object or function. In C, NULL is defined as a zero value. On the other hand, void pointers are the type of pointers that can point to any data type. Void pointers are used for general data type handling in C, allowing for flexible function delineations and data structures. The Crucial Difference lies in their operation.
18. Why is it important to declare a constant using#define?
Ans:
Using #define to declare constants in C is pivotal because it allocates no storehouse space and imposes no type constraint, allowing for flexible and effective law. Constants declared with#define are replaced by their values at collect time, which can lead to brisk prosecution since there is no runtime memory allocation. This system also helps in maintaining law, as changing the value of a#define constantly updates it across the entire codebase, ensuring thickness and reducing the eventuality of crimes.
19. How do logical addresses differ from physical addresses?
Ans:
Logical addresses, also known as virtual addresses, are used by operations to pierce memory locales, while physical addresses relate to factual locales on the memory tackle. The distinction lies in the position of abstraction; logical addresses are used within the environment of a program’s View, managed by the operating system to give memory insulation and security, whereas physical addresses correspond to the real memory layout managed by the tackle.
20. Distinguish Quick kind and combine kind algorithms.
Ans:
- Quick kind and combine kind are both effective sorting algorithms, but they differ significantly in their approach. Quick kind selects a pivot element and partitions the Array into rudiments lower than the pivot. Those lesser recursively sort the sub-arrays.
- It performs well on average but has a worst-case complexity of O(n2). Combine kind, on the other hand, divides the Array into halves, recursively feathers each half, and also merges them, always having a time complexity of O(n log n).
21. What’s polymorphism and abstraction?
Ans:
Polymorphism is a principle in object-acquainted programming that allows objects of different classes to be treated as objects of a common superclass. It enables a single interface to represent different beginning forms( data types), enhancing inflexibility and law reusability. Abstraction, on the other hand, is the conception of hiding the complex reality while exposing only the necessary corridor. It allows fastening on what an object does rather than how it does it, simplifying the design and commerce with complex systems.
22. Explain various phases of the SDLC.
Ans:
The Software Development Life Cycle( SDLC) comprises several phases to ensure effective and effective software development. It starts with the demand Analysis phase, where design pretensions and user requirements are defined. Next, the Design phase outlines the software armature. The perpetration or Coding phase follows, where the software is developed. Also, the software undergoes Testing to identify and fix blights.
23. What’s Boundary Value Testing?
Ans:
Boundary Value Testing is a software testing fashion that focuses on relating crimes at the boundaries rather than within the ranges of input data. It’s grounded on the principle that crimes are more likely to occur at the edges of the input sphere. This system involves testing the edges of input ranges; for illustration, if an input expects a range from 1 to 100, the test cases would include values like 0, 1, 100, and 101.
24. What’s Meant by Entry Controlled Loop?
Ans:
- An entry-controlled circle in programming is a circle construct in which the condition for the durability of the circle is estimated before the body of the circle is executed for the first time.
- The most common exemplifications of entry-controlled circles are the for and while circles in languages like C, C, and Java.
- This means that if the circle condition isn’t met from the beginning, the circle body won’t execute properly. Entry-controlled circles are useful for situations where a block of code needs to be executed multiple times, but only if a certain condition is true from the onset.
25. How many levels of indirection in pointers can exist in a single declaration?
Ans:
In proposition, a number of situations of indirection for pointers( i.e., pointers to pointers to pointers, and so on) in C isn’t explicitly limited by the language standard. Still, in practice, it’s constrained by the compiler and the coffers of the system on which the software is running. Deep situations of indirection can lead to complex and hard-to-maintain laws, so they’re generally discouraged. Utmost compilers handle multiple situations of indirection without issue, but exorbitantly deep indirection may lead to compiler or memory limits being reached.
26. What’s the Function of this Pointer?
Ans:
In C, this is a keyword that’s a pointer to the object on which a member function is being invoked. It’s used within class styles to relate to the object itself. This pointer is implicitly passed to all nonstatic member function calls and is available as an original variable within the body of all nonstatic functions. This allows members to be penetrated by their unqualified names, and it can be used to resolve nebulosity between member names and original variables or parameters.
27. What’s a Memory Leak in C?
Ans:
A memory leak in C occurs when a program allocates dynamic memory(e.g., using new or malloc) but fails to release it back to the system before losing all pointers or references to it. This means the allocated memory can not be penetrated again by the program or any other program, leading to a gradational reduction in the available memory for the system. Over time, memory leaks can beget an operation to consume further and further memory, potentially leading to system insecurity or crashes.
28. What is the concept of virtual memory, and how does it work?
Ans:
- Virtual memory is the memory operation capability of an operating system that uses tackle and software to allow a computer to compensate for physical memory dearths, temporarily transferring data from arbitrary access memory to a fragment storehouse.
- This process creates the vision for users of a veritably large( virtual) memory space indeed when the available physical memory is limited. Virtual memory allows for the prosecution of large operations or multiple operations contemporaneously, beyond what’s possible with just physical RAM.
29. What are replication statements in C, and how are they used?
Ans:
- Replication statements, or circles, in C, allow the prosecution of a block of law multiple times. The three primary replication statements are for, while, and do-while.
- The for a circle is used when the number of duplications is known before entering the circle. The while circle continues as long as its condition remains true, which is ideal for situations where the number of duplications isn’t destined.
- The do-while circle is analogous to the while circle but guarantees at least one prosecution of the circle body, indeed, if the condition is originally false.
30. Explain demand paging.
Ans:
Demand paging is a memory operation fashion used in virtual memory systems, where runners of data aren’t loaded into physical memory until they’re demanded, or” demanded”, by a program. This approach conserves physical memory, allowing a system to run operations that bear more memory than is physically available. When a program tries to pierce a runner that isn’t in physical memory, a runner fault occurs, egging the operating system to cost the needed runner from fragment and cargo it into memory.
31. Difference between internal and external fragmentation in-memory operation. ?
Ans:
Internal fragmentation occurs when allocated memory blocks are larger than the requested memory, leading to unused space within blocks. External fragmentation happens when free memory is resolved into small blocks between allocated blocks, making it insolvable to fulfil a request for a large block of memory. To reduce internal fragmentation, memory can be allocated using best-fit or exact-fit styles.
32. What will be if a pointer is deleted doubly?
Ans:
Deleting a pointer doubly leads to undetermined geste, including implicit crashes or memory corruption. This situation, known as a double-free error, occurs because the first omission deallocates the memory, and the alternate omission attempts to free memory that has formerly been freed, which can lose the memory operation data structures of the runtime terrain. To help this, it’s judicious to set pointers to nullptr after deleting them, ensuring that posterior omission attempts are inoffensive.
33. Define paging and impasse.
Ans:
- Paging is a memory operation scheme that eliminates the need for conterminous allocation of physical memory by dividing the virtual memory space into fixed-size units called runners, which are counterplotted to physical frames.
- This system allows for more effective use of memory and reduces external fragmentation. An impasse is a situation in concurrent programming where two or more processes are unfit to work because each is staying for one of the others to release a resource.
34. In the case of heritage, what’s the prosecution order of the constructor and destructor?
Ans:
In heritage, constructors are called in the order of base class to deduced class, while destructors are called in the rear order, from deduced class to base class. When creating a case of a deduced class, the base class constructor executes first to ensure the base part of the object is initialized before the deduced class constructor initializes the deduced part. Upon object destruction, the deduced class destructor executes first to clean up the deduced part, followed by the base class destructor to clean up the base part.
35. How can apply polymorphism in Java?
Ans:
Polymorphism in Java can be enforced using system booting and interfaces. System booting occurs when a class provides a specific perpetration for a system that’s formerly defined in its superclass. This allows a class to knit a general system handed by the superclass to its specific requirements. Interfaces give a way to apply polymorphism through system perpetration contracts that multiple classes can agree to fulfil, allowing different classes to be treated slightly grounded on the interface styles they apply.
36. Explain Inner and external Joins with exemplifications.
Ans:
- LEFT JOIN( returns all rows from the left table and the matched rows from the right table),
- RIGHT JOIN( returns all rows from the right table and the matched rows from the left table),
- FULL OUTER JOIN( returns rows when there’s a match in one of the tables).
An inner join returns rows when there’s at least one match in both tables being joined. However, the rows aren’t returned If there’s no match. For illustration, If joining two tables, guests and Orders, on their CustomerID, an inner join gives only the guests who have made at least one order. There are three types of external joins:
37. Define Array and the 2-D Array.
Ans:
- Shared Cinches( S—cinches) allow a sale to read a data item. Multiple deals can hold participated cinches on the same item contemporaneously.
- Exclusive Cinches(X-locks), which allow a sale to both read and write a data item. Only one sale can hold an exclusive cinch on a data item at a time.
- Determining which lock is” better” depends on the specific conditions of a sale. Shared cinches are better for read-heavy operations to maximize concurrency, while exclusive cinches are essential for write operations to ensure data integrity.
- Wrapper classes in Java are used to convert Java savages into reference types( objects). Every primitive data type has a corresponding wrapper class. For Illustration, int has Integer, double has Double, and housekeeper has Character.
- This conversion is essential for exercising savages in surroundings and taking objects, similar to in collections. Wrapper classes also give mileage styles to convert between savages and strings, and vice versa, and to manipulate the values.
- When diving into delicate debugging issues, a systematic approach is vital. Start by reproducing the problem constantly to understand its conditions. Use logs, debuggers, and individual tools to gather information and insulate the issue.
- Break down the problem into lower, manageable corridors and test suppositions by changing one variable at a time. Communication with platoon members can also give perceptivity or reveal analogous issues encountered in history.
- Nimble methodologies prioritize client satisfaction, flexible responses to change, and iterative development. Agile is centred on principles such as continuous delivery, collaboration, and adaptability.
- Continuous delivery, a key principle of Agile, enables the team to deliver functional components of the product regularly, gather feedback early, and make necessary adjustments swiftly. This approach involves working in sprints, maintaining a product backlog, and conducting sprint planning, reviews, and retrospectives.
- The approach to problem-solving in software development begins with a thorough understanding of the problem, which is facilitated by effective communication. Breaking the problem down into smaller, manageable components and gathering all relevant information and constraints is crucial to analyze the issue comprehensively.
- The next step involves communicating potential solutions, weighing their pros and cons. Prototyping or sketching solutions can be beneficial in visualizing potential challenges. Once a solution is chosen, implementation is followed by rigorous testing to ensure it effectively resolves the issue without introducing new problems.
- Microservices armature is a system of developing software systems that are made up of singly deployable, modular services. Each service runs a unique process and communicates through a well-defined, featherlight medium to serve a business thing.
- This approach differs from monolithic infrastructures, where all processes are tightly coupled and run as a single service. Microservices allow for easier scaling, better fault insulation, and a more elegant deployment cycle, enabling faster updates and advancements without dismembering the entire system.
- When remedying a complex operation, start by trying to replicate the issue in a controlled terrain to understand under what conditions the bug occurs.
- Use a systematic approach to narrow down the possible causes, similar to assaying logs, using debugging tools to step through the law, and examining changes in interpretation control that might have introduced the bug.
- It also helps to divide the problem into lower, manageable corridors and insulate the factors involved. Collaboration with platoon members can give new perceptivity or reveal overlooked aspects.
- Handling tight deadlines with multiple systems necessitates effective time management, prioritization, and communication skills. The process begins by breaking each design into smaller tasks and assigning deadlines.
- This approach helps establish task precedence and prioritize high-impact activities. Maintaining constant contact with the group and interested parties is essential for managing expectations and requesting necessary adjustments or support.
- Inner Join Returns rows that have corresponding values in both tables. Left Join Returns all rows from the left table and matches rows from the right table. However, the result is NULL on the right side If there’s no match.
- Right( external) Join Returns all rows from the right table and the matched rows from the left table. However, the result is NULL on the left side If there’s no match.
- Full( external) Join Returns rows when there’s a match in one of the tables. It combines the results of both Left Join and Right Join.
- client satisfaction through early and nonstop delivery of precious software.
- Drinking changing conditions, indeed late in development.
- Delivering working software constantly, with a preference for shorter timescales.
- Business people and inventors must work together daily throughout the design.
- figure systems around motivated individualities, give them the terrain and support they need and trust them to get the job done.
- The platoon was carefully organized and coordinated to meet project objectives, involving detailed planning and strategic adjustments as required.
- Key stakeholders were engaged to provide input and ensure their needs were incorporated into the design. Regular feedback sessions helped align the design with their expectations.
- An effective risk management strategy was used to identify and address potential issues, with ongoing monitoring allowing for timely adjustments to any emerging problems.
- MAQ Software operates within the Information Technology and Services assiduity. It specializes in software development, data analytics, and business intelligence services, feeding guests across various sectors, including finance, healthcare, retail, and technology.
- The company leverages the rearmost in pall computing, artificial intelligence, and data analytics to give innovative results that drive digital metamorphosis and functional edge for businesses.
- Designing scalable operations requires a forward-allowing approach that concentrates on inflexibility, effectiveness, and the capability to handle increased loads without compromising performance. Exercising pall services ensures coffers can be stoutly allocated and gauged according to demand.
- Espousing microservices armature allows different factors of an operation to gauge singly, perfecting manageability and reducing backups. Enforcing effective data operation and hiding strategies reduces quiescence and enhances performance.
- Nonstop Integration( CI) and nonstop Deployment( CD) are crucial practices in ultramodern software development that enable frequent, automated, and dependable updates to software products. CI involves automatically testing all law changes in a participated depository several times a day to describe and fix integration crimes snappily.
- CD extends CI by automatically planting all law changes to a testing or product terrain after the figure stage. This robotization ensures that software can be developed, tested, and released more fleetly, efficiently, and with advanced quality.
- Use a distributed architecture to handle high traffic and scale effectively. This spreads the workload across multiple nodes, enhancing system capacity.
- Implement real-time processing with message brokers or streaming platforms. This ensures announcements are delivered and processed without delays.
- Deploy load balancers to distribute incoming requests evenly across servers. This avoids bottlenecks and maintains consistent performance.
- Securing operations and data in the cloud involves employing various strategies and tools. Establishing vital permission and authentication procedures, like OAuth and Multi-Factor Authentication (MFA), is essential to restrict access to authorized operations and data.
- Regular updates and patches to operations and underlying structures are essential for protecting against vulnerabilities. To control access in various scenarios, implement robust identity and access management (IAM), among other security measures, security groups, and network ACLs.
- Peaceful APIs are grounded on emblematic state transfer( REST), a set of architectural principles for designing networked operations. They use HTTP requests to pierce and use data, with operations like GET, POST, PUT, and cancel.
- Peaceful APIs are stateless, meaning that each request from a customer to Garçon must contain all the information demanded to understand and complete the request.
- They’re frequently used for web services that need to be scalable and easy to integrate with other services. Cleaner( Simple Object Access Protocol), on the other hand, is a protocol for swapping structured information in perpetration of web services.
- Mock objects play a pivotal part in unit testing by bluffing the geste of real objects in controlled ways. They’re particularly important for segregating the piece of law under test, ensuring that tests aren’t dependent on external systems or complex dependencies, which can make tests short and slow.
- By using mock objects, inventors can more precisely test the relations between objects, corroborate system magic, and control the test terrain. This leads to further dependable, brisk, and concentrated tests that directly validate the unit of law’s willed geste without the unpredictability of external dependencies.
- The SOLID principles are a set of design guidelines in software engineering intended to ameliorate law readability, scalability, and maintainability by managing dependencies.
- Single Responsibility Principle Each module or class should have responsibility over a single part of the functionality handled by software, and the class should entirely reprise responsibility.
- Open/Closed Principle Software realities should be open for extension but closed for revision, allowing systems to grow without demanding to change being law.
- Work-Life Balance: A few workers have expressed concern about how extended working hours at MAQ Software may impact their work-life balance due to the company’s fast-paced, project-driven work environment. This is a typical problem in the software and consulting industries, particularly when working with clients in different time zones or when project deadlines are approaching.
- Significant Pressure: The organization may experience significant pressure due to its emphasis on meeting deadlines while producing software solutions of the highest calibre. It might be frustrating for certain employees because they are frequently expected to perform at their best all the time.
An array is a collection of particulars stored at conterminous memory locales. The idea is to store multiple particulars of the same type together, making it easier to calculate the position of each element by simply adding a neutralize to a base value, i.e., the memory position of the first element of the Array. A 2-D array is basically an array of arrays representing a matrix or a table with rows and columns.
38. Define Scheduling in OS.
Ans:
Scheduling in operating systems refers to the system by which work specified by processes or vestments is assigned to coffers that complete the work. The scheduler is a part of the operating system that determines which process runs at a given moment and for how long.Scheduling in operating systems refers to the system by which work specified by processes or vestments is assigned to coffers that complete the work.
39. Explain various Types of Cinches in a sale. Which is More and Why?
Ans:
40. What’s the Difference Between a Vector & an Array List?
Ans:
In the Java environment, both Vector and ArrayList are executions of the List interface, but there are crucial differences. Vector is accompanied, meaning it’s thread-safe out of the box but at the cost of reduced performance due to the outflow of synchronization. ArrayList, on the other hand, isn’t accompanied and provides better performance in scripts where thread safety isn’t a concern. Both can stoutly grow and shrink as demanded.
41. What’s JVM, and is it platform-independent?
Ans:
The Java Virtual Machine( JVM) is a machine that provides a runtime terrain to drive the Java Code or operations. It converts Java bytecode into machine language. While Java programs are platform-independent, the JVM itself is not. Each operating system( Windows, Mac, Linux, etc.) needs its own JVM perpetration. This is why a Java program can run on any platform without revision. The JVM acts as a conciliator, ensuring the Java program behaves the same on every Platform despite the underpinning tackle and software differences.
42. What are wrapper classes?
Ans:
43. What is the difference between primary memory and secondary memory?
Ans:
Primary memory, also known as main memory or RAM, is the central storehouse area in a computer that the CPU directly accesses for executing instructions and processing data. It’s unpredictable, meaning it loses its content when the power is turned off. Secondary memory, on the other hand, refers to storehouse bias as hard drives, SSDs, and USB drives. Non-volatile, meaning it retains data indeed when the computer is turned off.
44. What are the advantages of multi-programming, and what are they?
Ans:
Multi-programming is a system used in operating systems to maximize CPU application by running multiple processes coincidently. The main advantage of multi-programming is increased effectiveness, as it allows the CPU to switch to another process when one process is staying for I/ O operations to complete, thereby reducing idle time. This approach leads to better resource application and can significantly lessen the outturn of calculating systems.
45. What is the approach to remedying delicate issues in software development?
Ans:
46. How can the quality of a law be ensured?
Ans:
Ensuring code quality involves a multifaceted approach that includes adhering to coding standards, conducting code reviews, writing unit and integration tests, and continuous refactoring. Utilizing version control systems is essential for managing changes and collaborating efficiently within the team. Regular code reviews help identify issues early and promote best practices. Writing tests ensures that each unit functions as expected and the system remains stable after modifications.
47. What is the understanding of agile methodologies?
Ans:
48. How should a problem be approached when working in software development?
Ans:
49. Describe a design using machine learning algorithms, the challenge, and the solution.
Ans:
In a recent project, the task was to optimize client churn predictions for a telecom company. The main challenge involved directly predicting potential churn customers to enable the company to implement effective retention strategies. The Random Forest Classifier was chosen because it can handle imbalanced datasets and is effective in feature importance ranking. The data preprocessing phase involved managing missing values and standardizing the dataset.
50. How does one stay current with the latest software engineering technologies?
Ans:
One effective strategy is to regularly read specialized blogs, papers, and exploration papers published on estimable spots similar to Medium, Stack Overflow, and ACM Digital Library. Joining professional networks like LinkedIn and following assiduity leaders and influencers can give perceptivity into emerging trends and stylish practices. Sharing in online forums and communities, similar to GitHub or Reddit’s programming vestments, allows for engaging with real-world systems and conversations.
51. Explain the conception of microservices. How do they differ from monolithic infrastructures?
Ans:
52. What strategies are employed to remedy a complex operation?
Ans:
53. Explain the significance of data normalization in databases?
Ans:
Data normalization is a process in database design that organizes tables and their relationships to reduce redundancy and dependency. Its main goals are to eliminate unnecessary data, ensure logical data dependencies to prevent anomalies, and simplify the schema for better organization and accessibility. Normalization helps save storage space and enhances database performance by streamlining data updates, insertions, and deletions, thereby ensuring data integrity and consistency.
54. Explain a complex SQL query.
Ans:
A complex SQL query might use subqueries, joins, window functions, and tentative sense to recoup or manipulate data from multiple tables grounded on specific criteria. For illustration, consider a query that retrieves the top 3 highest-dealing products for each order in a store’s database. This query will likely use a combination of JOIN to link products and orders, GROUP to aggregate deals by product and order, and a window function like ROW_NUMBER () partitioned by order to rank products within each order by deals.
55. How would a slow-running database query be optimized?
Ans:
To optimize a slow-running database query, start by examining the query execution plan for issues like full table scans or inefficient joins. Indexing is a key strategy, particularly on columns used in WHERE clauses or joins, to reduce execution time. Query refactoring can also help by breaking complex queries into simpler subqueries, excluding unnecessary columns, and using aggregations appropriately.
56. How are tight deadlines managed when multiple systems are on the plate?
Ans:
57. Describe a gruelling platoon design project and the contributions made to its success.
Ans:
In a challenging platoon design project, streamlining communication between inventors and the design team was essential for ensuring timely delivery. The project encountered issues due to unclear conditions and frequent changes. Daily stand-up meetings were initiated for quick status updates to address these challenges, and a shared document was created for all team members to log changes and progress.
58. Explain the Difference between mound and mound memory.
Ans:
Mound and heap memory are two types of memory used in operations for different purposes. Mound memory, managed by the system, is primarily used for static memory allocation, including function calls and local variables. It operates in a last-in-first-out manner, adding a block to the “mound” with each new function call and removing it upon completion. Heap memory, on the other hand, is used for dynamic memory allocation, allowing memory to be allocated at runtime for objects and variables that need to persist beyond the scope of function calls.
59.What is a join in SQL, and what are the different types?
Ans:
60. What are the principles of agile software development?
Ans:
61. What’s SQL injection, and how can it be averted?
Ans:
SQL injection is the type of security vulnerability that allows the bushwhackers to intrude with the queries that the operation makes to its database. It generally involves fitting or” edging in” vicious SQL law into an input field for prosecution(e.g., to leave database contents to the bushwhacker). To help SQL injection, use set statements with parameterized queries. This ensures that the input is handled as data, not as part of the SQL command.
62. Explain the armature of the Model-View-ViewModel (MVVM).
Ans:
A design pattern called the Model-View-ViewModel (MVVM) armature is used in software development to distinguish between the graphical user interface (GUI) and the business or back-end sense (the data model). The Model represents the facts and business sense. The user interface is called the View. By binding to the View, the ViewModel serves as a mediator between the Model and the View, managing sense that gets data ready for display (as well as reacting to user inputs).
63. How can database performance be optimized?
Ans:
Optimizing database performance involves several strategies aimed at reducing inactivity and adding outturn. Indexing is a primary system that allows hastily data reclamation by reducing the amount of data scrutinized. Proper normalization helps in organizing the data efficiently, although denormalization can occasionally speed up read operations at the cost of write operations. Query optimization, through jotting effective SQL queries, directly impacts performance by minimizing prosecution time.
64. Describe a time when a platoon was led through a delicate design phase.
Ans:
65. Is MAQ Software a service-grounded company?
Ans:
MAQ Software is a service-based company specializing in data operations, analytics, and software engineering. It focuses on digital transformation, leveraging cloud platforms and AI technologies to improve business intelligence, customer experiences, and operational efficiency. By providing customized software solutions and consultancy services, MAQ Software addresses diverse business needs across various industries, driving growth and innovation through technology.
66. Why does one want to join MAQ Software?
Ans:
Joining MAQ Software is appealing due to its reputation for delivering cutting-edge technology solutions and its focus on data analytics and software development. The company’s commitment to innovation aligns with a desire to work on complex systems involving the newest technology, such as cloud computing and AI. Additionally, MAQ Software’s continuous learning and professional development culture presents valuable opportunities for skill enhancement and career advancement.
67. What’s the assiduity of MAQ Software?
Ans:
68. How can scalable operations be designed?
Ans:
69. How is software development quality tested and guaranteed?
Ans:
Software development quality is ensured through a mix of automated and manual testing methods, such as unit tests, integration tests, system tests, and user acceptance tests. Key practices include continuous integration and deployment, code reviews, adherence to coding standards, performance evaluations, and security assessments.
70. Explain the conception of nonstop Integration/ nonstop Deployment( CI/ CD).
Ans:
71. How is the choice of sorting algorithm determined for a given situation?
Ans:
Choosing the applicable sorting algorithm depends on several factors, including the size of the dataset, the nature of the data(e.g., if the data is formerly incompletely sorted), and the specific conditions for time and space complexity. For small datasets, simple algorithms like bubble kind or insertion kind might be sufficient due to their low outflow. For larger datasets or operations taking high performance, more effective algorithms like quicksort or mergesort are preferable.
72. How can a scalable announcement system be designed?
Ans:
73. Explain the Difference between IaaS, PaaS, and SaaS.
Ans:
Structure as a Service( IaaS), Platform as a Service( PaaS), and Software as a Service( SaaS) are pall computing models that offer different situations of abstraction and control. IaaS provides virtualized computing coffers over the internet, giving users control over the operating system, storehouse, and station operations, making it largely flexible. PaaS offers a platform allowing guests to develop, run, and manage operations without dealing with the underpinning structure, simplifying the development process.
74. What are the crucial benefits of pall computing?
Ans:
Pall computing offers several crucial benefits, including scalability, inflexibility, cost-effectiveness, and availability. Scalability allows businesses to fluently acclimate coffers grounded on demand, ensuring performance and effectiveness. Inflexibility and skill come from the capability to snappily emplace and experiment with new operations without outspoken investment in tackle. Cost-effectiveness is achieved by moving from capital expenditure to functional expenditure, paying only for consumed coffers.
75. How are operations and data secured in the pall?
Ans:
76. How can a high-vacuity system be designed in the pall?
Ans:
Designing a high-vacuity system in the pall involves architecting the operation to be flexible and tolerant of failures. Use multiple vacuity zones and regions to place your operation, ensuring that a failure in one area doesn’t lead to system-wide time-out. Employ cargo balancers to distribute business unevenly across servers and help with any single point of failure. Apply bus- -scaling to acclimate coffers automatically grounded on demand, ensuring performance is not compromised.
77. How can a being operation be resettled to the pall?
Ans:
Migrating an operation to the cloud requires a structured approach. Assess the operation’s architecture, dependencies, and data to identify challenges. Choose a migration strategy (rehosting, re-platforming, refactoring, or reconditioning) based on complexity and needs. Use cloud migration tools for efficiency, and test the operation in the cloud to address any security, compliance, and performance issues.
78. What are some of the key differences between NET Core and NET Framework?
Ans:
Microsoft offers two fundamental operations platforms—NET Core and NET Framework. However, they differ greatly from one another. Although NET Framework is only compatible with Windows, NET Core is cross-platform and open-source, allowing use on Linux, macOS, and Windows. Because it enables containerization and microservices, NET Core is suitable for modern, scalable enterprise operations. It also offers better performance and is optimized for scalable, high-performance systems.
79. Explain the conception of peaceful APIs. How do they differ from SOAP?
Ans:
80. What is the experience with front-end development frameworks?
Ans:
Experience with front-end development frameworks includes utilizing React.js, Angular, and Vue.js to design and build interactive, responsive user interfaces. These frameworks simplify development by offering reusable components and effective state management. They also leverage modern JavaScript features to deliver engaging user experiences with smooth, interactive elements. Proficiency in these frameworks allows for the creation of scalable and maintainable web applications.
81. How should unit tests be approached for a specific law?
Ans:
Unit tests for a specific law should first identify the legal requirements and create corresponding test cases. These tests must confirm that the implementation adheres to the legal standards and addresses all specified scenarios. They should also cover edge cases to ensure appropriate responses to various inputs. Additionally, continuous testing is needed to ensure that updates or changes maintain compliance with the legal requirements.
82. Describe the significance of mock objects.
Ans:
83. How can database queries be optimized in a high-cargo operation?
Ans:
Optimizing database queries in a high-cargo operation involves several strategies to reduce inactivity and increase outturn. Indexing is consummate, allowing the database to cost data more efficiently. Assaying and optimizing query performance using EXPLAIN plans helps identify slow queries and the need for indicators. Caching constantly penetrates data and reduces database cargo. Employing pagination for large datasets can minimize the quantum of data transferred.
84. Explain the SOLID principles in software engineering.
Ans:
85. How is state managed in a React application?
Ans:
In React operations, state operations can be handled in various ways, depending on the complexity and scale of the app. For simpler operations, React’s erected-in-useState and useContext hooks may serve, enabling element-position state operation and environment for propagating data without mount drilling. For further complex global state operations, libraries like Redux or MobX offer robust results.
86. What are the differences between GET and POST HTTP styles?
Ans:
GET and POST are two primary HTTP styles used in web development to transfer requests from a customer to a garçon. GET requests are used to recoup data from a specified resource and shouldn’t produce any side goods on the garçon, making them idempotent. They can be cached and bookmarked as they remain in the cybersurfer history and URL. POST requests, on the other hand, are used to submit data to a garçon to produce and modernize a resource, frequently performing in a change in garçon state or side goods.
87. How is thread safety ensured in a multi-threaded operation?
Ans:
Ensuring thread safety in a multi-threaded operation involves using strategies to help prevent concurrent vestments from penetrating participated coffers in ways that can beget corruption or inconsistent results. This can be achieved through synchronization mechanisms like mutexes, cinches, and semaphores that control vestments’ access to participated coffers, ensuring that only one thread can modify the resource at a time.
88. what are the disadvantages of MAQ Software?
Ans:
89. How can an introductory e-commerce system be designed?
Ans:
Designing an introductory e-commerce system involves creating a scalable and flexible armature that can handle various functionalities such as product table, hunt, wain operation, user authentication, and payment processing. The system should have a well-defined database schema for storing product information, user data, and order histories. An effective hunt medium is pivotal for helping users find products.
90. How should an announcement system be designed to transfer real-time cautions to users?
Ans:
Designing a real-time announcement system involves setting up a scalable, effective armature that can handle high outturn and low quiescence. Use a publish-subscribe model where services or operations publish announcements to a communication line or broker, and subscribers admit these announcements in real time. Websockets can be employed to maintain patient connections with guests, enabling the instant delivery of dispatches.






