
The Five Phases of Ethical Hacking
A recent survey by PriceWaterhouseCoopers, “The Global State of Information Security Survey 2018”, shows that business leaders are concerned about the security risks associated with emerging technologies such as automated or robotic systems. For example, 39 percent of the 9,500 interviewed executives fear loss or compromise in sensitive data and over 32 percent believe that the quality of the product is susceptible to damage.
Cyber security is no longer ‘just an IT issue’, it is a problem that is affecting the brand equity of an organization. In fact, entrepreneurs like Elon Musk, founder, and CEO of Tesla, are giving top priority to security.
As more organizations move into the digital space, safeguarding data from hacking and cyber-attacks is more significant than ever before. Companies are now acknowledging the potential dangers of these attacks and thinking of preemptive solutions—one of them being ethical hacking.
What is Ethical Hacking and How Is It Different From Hacking?
Hacking means to illegally access other people’s computer systems in order to destroy, disrupt or carry out something illegal. Hacking is usually carried out remotely, i.e. someone outside a company wants to try to break into the computer system. About ETHICAL HACKING : Ethical Hacking is an Authorized way of Hacking.
In contrast, ethical hacking involves using the same hacking tools and techniques to identify vulnerabilities in a system and address them before they can be exploited. According to King, to beat a hacker, you need to think like a hacker.
There are different types of hackers:
- Black Hat Hackers: Individuals with extraordinary computing skills who use these advanced skills with malicious intent.
- White Hat Hackers: Ethical hackers with advanced computing skills who use their skills for defensive purposes.
- Gray Hat Hackers: Advanced computer users who work both offensively and defensively and often are security consultants, or white hat hackers who moonlight as black hat hackers.
The Five Phases of Ethical Hacking
This article explains 5 steps of Hacking taking an example of a Hacker trying to hack a company’s server and gaining access to all the data.
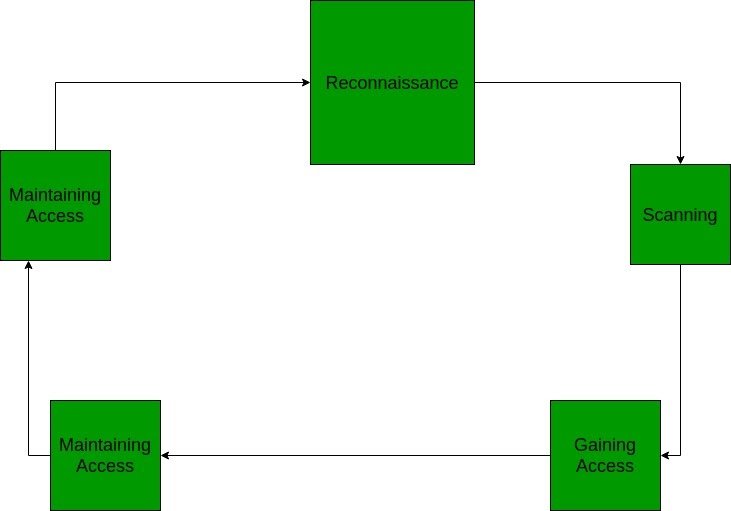
- Reconnaissance : This is the first phase where the Hacker tries to collect information about the target. It may include Identifying the Target, finding out the target’s IP Address Range, Network, DNS records, etc.Let’s assume that an attacker is about to hack a websites’ contacts.He may do so by : using a search engine like maltego, researching the target say a website (checking links, jobs, job titles, email, news, etc.), or a tool like HTTPTrack to download the entire website for later enumeration, the hacker is able to determine the following: Staff names, positions, and email addresses.
- Scanning: This phase includes usage of tools like dialers, port scanners, network mappers, sweepers, and vulnerability scanners to scan data. Hackers are now probably seeking any information that can help them perpetrate attacks such as computer names, IP addresses, and user accounts.Now that the hacker has some basic information, the hacker now moves to the next phase and begins to test the network for other avenues of attacks. The hacker decides to use a couple methods for this end to help map the network (i.e. Kali Linux, Maltego and find an email to contact to see what email server is being used). The hacker looks for an automated email if possible or based on the information gathered he may decide to email HR with an inquiry about a job posting.
- Gaining Access: In this phase, the hacker designs the blueprint of the network of the target with the help of data collected during Phase 1 and Phase 2. The hacker has finished enumerating and scanning the network and now decide that they have some options to gain access to the network.For example, say a hacker chooses Phishing Attack: The hacker decides to play it safe and use a simple phishing attack to gain access. The hacker decides to infiltrate from the IT department. They see that there have been some recent hires and they are likely not up to speed on the procedures yet. A phishing email will be sent using the CTO’s actual email address using a program and sent out to the techs. The email contains a phishing website that will collect their login and passwords. Using any number of options (phone app, website email spoofing, Zmail, etc) the hacker sends an email asking the users to login to a new Google portal with their credentials. They already have the Social Engineering Toolkit running and have sent an email with the server address to the users masking it with a bitly or tinyurl.Other options include creating a reverse TCP/IP shell in a PDF using Metasploit ( may be caught by spam filter). Looking at the event calendar they can set up a Evil Twin router and try to Man in the Middle attack users to gain access. A variant of Denial of Service attack, stack based buffer overflows, and session hijacking may also prove to be great.
- Maintaining Access: Once a hacker has gained access, they want to keep that access for future exploitation and attacks. Once the hacker owns the system, they can use it as a base to launch additional attacks.In this case, the owned system is sometimes referred to as a zombie system.Now that the hacker has multiple email accounts, the hacker begins to test the accounts on the domain. The hacker from this point creates a new administrator account for themselves based on the naming structure and tries to blend in. As a precaution, the hacker begins to look for and identify accounts that have not been used for a long time. The hacker assumes that these accounts are likely either forgotten or not used so they change the password and elevate privileges to an administrator as a secondary account in order to maintain access to the network. The hacker may also send out emails to other users with an exploited file such as a PDF with a reverse shell in order to extend their possible access. No overt exploitation or attacks will occur at this time. If there is no evidence of detection, a waiting game is played letting the victim think that nothing was disturbed. With access to an IT account the hacker begins to make copies of all emails, appointments, contacts, instant messages, and files to be sorted through and used later.
- Clearing Tracks (so no one can reach them): Prior to the attack, the attacker would change their MAC address and run the attacking machine through at least one VPN to help cover their identity. They will not deliver a direct attack or any scanning technique that would be deemed “noisy”.Once access is gained and privileges have been escalated, the hacker seeks to cover their tracks. This includes clearing out Sent emails, clearing server logs, temp files, etc. The hacker will also look for indications of the email provider alerting the user or possible unauthorized logins under their account.




