
- What is Dorking on Google?
- Basic operations within Dorking
- Approaches to Dorking
- Methods of Dorking
- How to Stop the Infiltration of Google Dorks
- Advantages and Disadvantages of Google Dorking
- Conclusion
Google Dorking, or ethical hacking, employs advanced operators in a search query. Commands like site:, filetype:, and intitle: can constrain the search to look for sensitive information, so it makes access to difficult or sensitive data possible, locates vulnerabilities, or accesses publicly available files not easily found in a run-of-the-mill search. To mitigate such risks, it is crucial to test and secure web applications and networks within a controlled Sandbox Environment, where vulnerabilities can be safely identified and addressed without exposing live systems to potential threats. Legitimate uses for all these techniques are thus applied in most cases, like scientific research and cybersecurity assessments, and are carried out ethically and legally. Otherwise, malice in the case of dork hacking dorks may lead to serious legal consequences that underlines responsible application in discovering digital information.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
What is Dorking on Google?
Google security experts and ethical hackers frequently use a technique called Google Hacking, or Dorking Google. By leveraging Google’s search engine, they can retrieve sensitive information from websites or web pages.There are numerous types of operations by which we can do the Google Dork Hacking in Cyber Security Training Courses: filetype:, Info:, intext:, cache:, and more. In the section that follows, we will go over each of these operations.
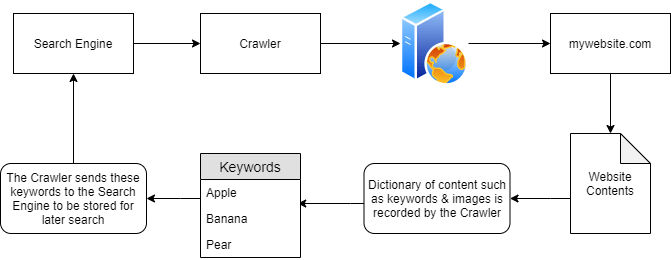
Dork hacking is a means of making web searches more exact by using special commands on Google. These commands, known as operators, assist users in locating data that may be challenging to find through standard search methods.Assume you work in computer security and are tasked with finding publicly available directories that might hold private data. You could utilize the “filetype:” Google Dork function to define the kind of file you’re looking for in the Google search engine.
Basic operations within Dorking
- Site-Specific Searches: This search narrows down the results to a specific website or domain. This can be applied if you want to find something that is hosted on a particular website.
- File Type Searches: Google will help you search for the following types of documents, namely PDFs, a Word document, an Excel spreadsheet, and lots more. However, to prevent unauthorized access to such documents, organizations can implement Whitelisting .
- Directory Listings: Using Google, it is possible to search the publicly accessible directory listings. These include pages that have the list of files stored in a web server; these have often been inadvertently made available to the public.
- URL-Based Searches: You can find a specific word or pattern on the URL of a webpage. The URL-based search is usually applied for finding login pages, admin panels, or web pages with specific parameters.
- Title-Based Searches: Searches can also be restricted to page names, which comes in handy for finding pages with certain names or functions, such as login portals or error pages.
- Text Searches: It searches for specific words or phrases in the text of a given webpage. It is used when finding pages carrying keywords like “password,” “confidential,” or “user details.”
- Negative Terms: Sometimes you would want to remove particular words from the search results. This procedure deletes specific terms, and this narrows down certain searches with less rubbish.
- Wildcard Searches: Wildcard can be loosely referred to as a holder for unknown or variable words. This is handy for searching on different variations of a term or phrase.
- Employ “NonFollow” and “NoIndex.” Labels: There are tags that instruct Google search engines not to follow links on particular pages or index particular pages. This will assist in preventing sensitive information from showing up in search results.
- Create a robust Robots.txt file: Tells web crawlers and web robots which pages on your website need to be crawled. If not properly configured or secured, malicious actors can exploit vulnerabilities in websites to deploy Keylogger malicious software designed to track keystrokes.
- Limit the permissions of files and directories: Make sure the permissions on files are set appropriately, and restrict access to directories that are sensitive.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Approaches to Dorking
There are multiple approaches, depending on what a person wishes to accomplish, in using Dorking. One popular approach is targeted queries, where people craft unique search strings to yield particular types of information, such as sensitive files or vulnerable web sites. This method often utilizes multiple search operators in order to limit the results, thus conducting a focused search on data which is desired. This technique, known as Google Hacking Database, can be particularly powerful for discovering sensitive information that may not be easily found through standard searches. Another good usage is the operator combination that enables the user to write a more complex query, hence obtaining very specific results.
For instance, combining site and filetype operators could be helpful in finding specific file types hosted on a certain domain. Another useful strategy could be an iterative search process where the users refine their queries based on the findings from the earlier searches. In this manner, the results of subsequent searches are more refined and relevant. Finally, utilization of free public resources, such as forums or websites related to Dorking Google, may be used by researchers because this provides the community’s wise and effective queries in order to improve the search technique, bringing subjects to maximum success using Dorking.
Methods of Dorking
Information CollectionBasically, Dorking is used as a means of collection of information from the websites. A researcher, security analyst, even a marketer might use it for gathering data about a selected website. This may include discovering its structure, files as well as possible security vulnerabilities.For example, a researcher may want to gather all public available documents regarding a particular organization.
Detection of Vulnerable WebsitesGoogle Dorking in Cyber Security Training Courses can be utilized to assist in the detection of sites having known vulnerabilities or misconfigurations; most security professionals make use of this method to aid them in the detection of weaknesses that can be exploited by attackers.Professionals can identify the security posture of a site by looking for known configurations or known-insecure pages and make a recommendation about remediation.
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Finding Sensitive FilesThere are many organizations that leak sensitive files of financial information or HR reports hosted on a website for public access. In Dorking, some words, file types, or more will discover sensitive files.For instance, one can search for Excel sheets that carry confidential financial information.
Accessing Login PagesThe process of Dorking even identifies login pages. It can be used by both white hats and black hats as the technique is applicable for accessing points meant for authentic users and also by the malicious actors that may use it for exploitation.For example, with Dorking, an analyst may be searching for admin login pages to try to test their security vulnerability while an attacker uses it in order to seek out areas of a site that can be set up for brute-force attacks.
Vulnerabilities of Specific TechnologiesBy using Dorking, one may find details about what technologies and software are being used at any specific site. These can be useful when the project is new for developers; again, for attackers.For example, a user could be interested in finding WordPress sites to either identify a potential blog or to see if sites still use outdated software versions.
How to Stop the Infiltration of Google Dork
Advantages and Disadvantages of Google Dorking
| Topic | Advantages | Disadvantages |
|---|---|---|
| Privacy Concerns | With sophisticated search operators, you can quickly locate precise information. | May inadvertently reveal private or sensitive information. |
| Constitutional Concerns | Beneficial for compiling information for competitive analysis or research reasons. | When Google Dorking tactics are misused, there could be legal repercussions. |
| Ethical Consequences | Aids in locating security holes in websites so they may be tested. | Has the potential to be maliciously utilized to exploit weaknesses. |
| Efficiency | Finds just what you need by restricting search results, saving you time. | Just to the extent that indexed data is available. |
Conclusion
In conclusion, Google Dorking is an effective strategy that lets users utilize sophisticated search queries to find hidden information in Cyber Security Training Courses, spot security holes, and carry out in-depth investigation. People can obtain important information that could otherwise remain hidden by employing search operators skillfully, which is advantageous for enterprises, cybersecurity experts, and researchers alike.But it’s important to approach Dorking with a strong sense of responsibility and ethics. Ensuring that information is utilized responsibly and ethically requires respecting privacy, being aware of legal restrictions, and following responsible disclosure standards. As the landscape of information accessibility evolves, so does the need for awareness about the potential risks associated with Google Dork Hacking. While it can uncover valuable insights, it also poses ethical dilemmas and can inadvertently expose sensitive data. Users must remain vigilant about the implications of their findings and the broader impact on individuals and organizations. Engaging with this practice not only requires technical skill but also a commitment to ethical standards and a proactive approach to safeguarding privacy. By balancing the quest for knowledge with ethical considerations, users can harness the power of Dorking responsibly.





