
Introduction to CyberSecurity Framework:
Cyber security is more important than ever. In the post-COVID-19 world, cyber threats are more prevalent than ever and protecting unauthorised access to data centres and other computerised systems is something a business cannot do without. For many businesses, an ad-hoc approach to cyber security is ineffective. With no clear plan in place, it is difficult to monitor and manage all potential cyber threats to your business. A cyber security framework is a great way for any business to have a clear plan to manage and mitigate cybercrime threats. Another way to deal with cybercrime is to create an incident response plan and you can read more about this in our previous post.
- The National Institute of Standards (NIST) first developed the Cyber Security Framework in 2014 to provide guidance for organisations that wish to strengthen their cyber security protections.
- The NIST Cybersecurity Framework (CSF) has recently been updated to version 1.1.
- It was created at the behest of President Barack Obama by cybersecurity professionals from government, academia and various industries and was later built into federal government policy by the new administration.
- NIST is the benchmark for CSF cyber security framework and can be tailored to meet the needs of any organization.
What is a cyber security framework?:
A cyber security framework is a series of documents that define best practises by an organisation to manage its cyber security risk. Such frameworks reduce the company’s exposure to vulnerabilities. When properly implemented, a cyber security framework enables IT security leaders to more intelligently manage their companies’ cyber risks. An organisation can adapt existing cyber security infrastructure to meet its needs or develop internally:
NIST Cyber Security Framework:
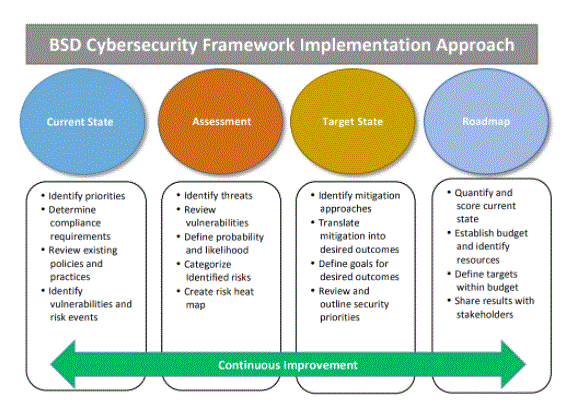
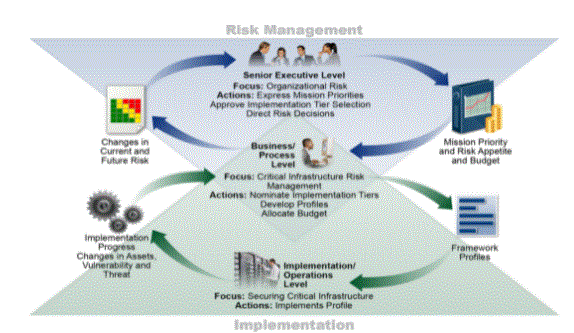
- Like most plans, the key to success is understanding what you want to achieve by establishing this framework. That way, you can better understand and measure what success looks like.
- For most businesses, the key decision to make when setting goals is the level of risk tolerance that is acceptable to both the C-suite and your IT department.
- Typically, it will be the responsibility of the IT management team to bring together a definitive agreement that makes it clear what level of risk is acceptable to your organisation.
- Setting a clear budget is also an important step and is essential when setting goals. Work within the limits of your own business when setting goals and include the financial constraints to achieve those goals.
- It may make sense to run a test within the same department to find out what works and what doesn’t. Once the whole business is outlined, feedback at this stage can save you valuable resources and help you streamline your goals to make them more precise and achievable.
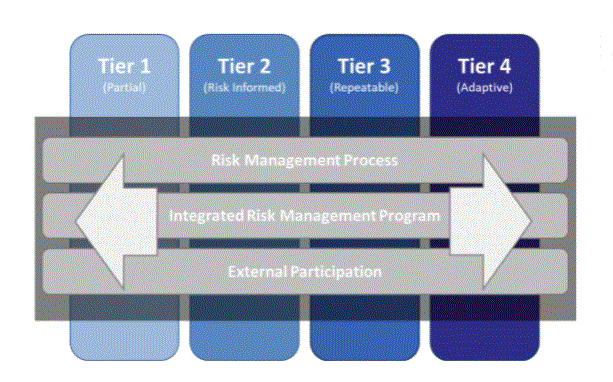
- Risk management process
- Integrated Risk Management Program
- External participation
- Each runs from Tier 1 to Tier 4.
- Tier 1 – Partial – generally reflects an inconsistent and reactive cyber security stance.
- Tier 2 – Risk Information – Allows for some risk awareness, but the plan is consistent.
- Tier 3 – Repeatable – Indicates organisation-wide CSF standards and consistent policy.
- Tier 4 – Adaptive – refers to proactive threat detection and prediction.
- Once you have set your goals and created a detailed profile, it is time to assess your current situation.
- The starting point for this is a detailed risk assessment to establish your current situation. You can use open source or commercial software tools capable of scoring your target areas or connect with a cyber security expert to conduct an independent assessment of your current situation.
- Once all areas are scored, you will be able to present findings to your key stakeholders, showing the security risks to organisational operations, assets and individuals. Vulnerabilities and threats should be clearly identified at this stage of the process.
- With a deep understanding of the risks and potential business impacts, you can move on to gap analysis.
- In this step of the process, you can compare your actual score with your target score. You may want to create a heat map to represent the results in an accessible and digestible way. Any significant differences immediately highlight the areas you would like to focus on.
- Work on what you need to do to bridge the gap between your current score and your target score.
- Identify a range of actions you can take to improve your score and prioritise them through discussions with all key stakeholders. Specific project requirements, budgetary considerations and staffing levels can all affect your planning.
- With a clear picture of the current health of your rescue, a set of organizationally aligned target goals, a comprehensive gap analysis and a set of remedial actions, you are now ready to implement NIST CSF.
- Use your first implementation as an opportunity to document processes and create training materials for wider implementation down the line.
- Implementation of your action plan is not the end.
- Your CSF’s performance should be continuously reviewed to be monitored and targets continually re-evaluated to ensure that they are meeting the changing landscape of the cyber security sector.
- This should involve an ongoing process of iteration and verification with key decision makers. To get maximum benefits, you need to speed up the implementation process and further customise NIST CSF to suit your business needs.
Tailoring the NIST Cyber Security Framework for your business:
The content of the NIST CSF is freely available and there are many useful resources available to IT managers to help them understand the content of the CSF. Creating a framework for your own business needs is easier said than done, however in this post, we have taken five key steps to build your own cyber security framework using NIST CSF. Structure.
Step 1: Set your goal goals
Step 2: Create a detailed profile
The next step is to go more in-depth and profile your specific business needs. NIST’s Framework Implementation Tier will help you understand your current situation and where you need to be. They are divided into three areas:
Like most NIST CSFs, these should not be taken as set in stone. They can be customised for your organisation.
These levels should be aligned with the goals you set in step one of this process. Higher levels are considered a more complete implementation of CSF standards and are what you should aspire to. Your ability to proactively detect and predict threats to your business is likely to depend on the budget allocated for cyber security and your ability to match your goals and targets to these levels.
Step 3: Assess your current situation
Step 4: Gap Analysis and Action Plan
Step 5: Implement your action plan
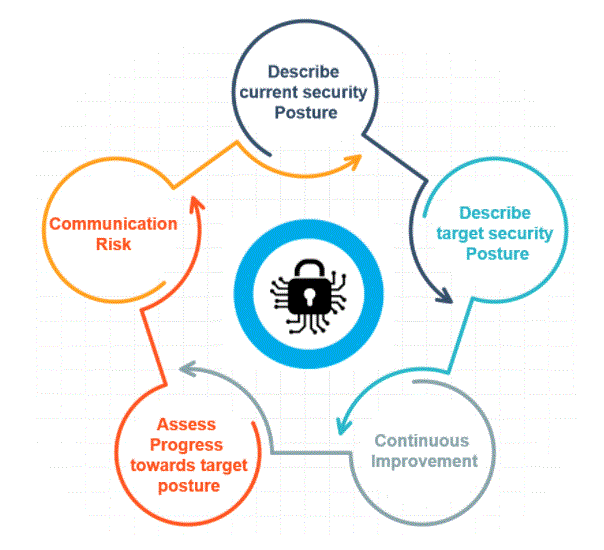
- The NIST RMF is dedicated to actively assessing risk-informed control implementations that make SP800-30 so important to NIST’s framework for both risk management as well as cybersecurity management. CSF is driven by results and maps on specific security controls – overall, although strategic planning requires a risk assessment to inform NIST CSF where to begin. While O’Reilly sees any framework for risk quantification as a step in the right direction (from three-by-three metrics to 800-30 and FAIR models) he believes it comes down to How much are the results worth? other members of your organization.
- The framework for NIST CSF implementation relies on three core principles: profile, implementation level, and implement framework core functions (detect, protect, trace, respond, retrieve). Starting with a risk assessment allows your organisation to be grounded and integrated into the underlying CSF profile. From there, determining your implementation level (current and desired) helps make it more relevant to the current state of your organisation. Ultimately, the Framework Core will guide where you need to invest and continuously monitor resources based on gaps in your security program.
- A NIST SP 800-30 risk assessment is of particular value because it rolls in well in CSFs because they were developed by the same organisation. While CSF is flexible enough to use any risk assessment framework, O’Reilly recommends SP 800-30 for established InfoSec programs and using a combination of 800-30 and FAIR models in the Cyberstrong platform.
Using a NIST Risk Assessment to Implement the NIS:
Cyber security framework:
How to Implement the NIST Cybersecurity Framework:
The National Institute of Standards and Technology’s Framework for Improving Critical Infrastructure Cyber Security – later called the NIST Cyber Security Framework (CSF) – is considered the gold-standard framework profile on which to build your cybersecurity program. could. Designed to facilitate dialogue about cyber security risk management between cyber security professionals and stakeholders in both public and private sector organisations, the NIST CSF, when combined with the NIST Risk Management Framework (RMF), is a powerful tool. The RMF is a process-based framework that is applied practically using several more direct specialised publications from NIST and SP 800-30 is one of them. While NIST is the gold standard for CSF cyber security management, being the most comprehensive and flexible, it is also the most challenging to implement. In his most recent webinar, Cyberscent’s Chief Product Officer, Padraic O’Reilly, discussed the relationship between CSF, RMF and the new privacy framework on our official website. Here we will go through the steps to use RMF, SP 800-30 and implement this cyber security framework.
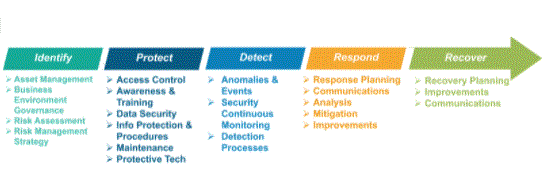
- Asset Management
- Business climate
- Governance
- Risk assessment
- Risk management strategy
- Supply chain risk management
- Identity Management and Access Control
- Awareness and Training
- Data security
- Information Protection Procedures and Procedures
- Maintenance
- Protective technology
- Anomalies and incidents
- Security Continuous Monitoring
- Detection process
- Response plan
- Communications
- Analysis
- Mitigation
- Improvement
- Recovery plan
- Improvement
- Communications
5 Functions of the Cybersecurity Framework:
What is the goal of the NIST Cybersecurity Framework? Broadly speaking, this is to ensure that your data is secure. However, more specifically, the NIST Cybersecurity Framework has five distinct functions that all work together to keep data secure. Here are five tasks and their roles in maintaining cyber security.
1. Identify
The first task, Identify, focuses on how you evaluate and identify risk in your business and IT systems. This requires taking a detailed look at your current data practises. The following actions come under identity:
2. protect
How can you protect your organisation from cyber security breaches? To maintain control over who is accessing your data, you must implement the following mandates that are covered by the Protect function:
3. Locate
To ensure that data protection incidents are kept to a minimum, you need ways to detect incidents when they do occur. The detect function includes the following steps:
4. Reply
When there is a data breach, every second counts. With every passing minute, countless valuable files can be compromised. As such, you need to react quickly to any sign of a violation by taking the following actions:
5. Recover
Ultimately, the final steps you take in the cyber security framework are focused on how to recover lost or compromised data. To ensure that your data is easily recovered and safe in the future, use these steps:
- Conduct an independent risk assessment so that you can determine your current data protection status. A risk assessment of your current efforts shows what is working and what steps you need to take to get your other security efforts up to NIST standards.
- One way to determine your current status is to use a software tool capable of scoring your security efforts. Train staff members on how to use these tools or partner with a third party vendor to perform the evaluation. Make sure the evaluating parties have no prior knowledge of your target score, preventing any bias in scoring.
- Once scores are collected, they can be presented to key stakeholders in your business. With this knowledge, you are equipped to identify areas of risk and create a strategy that can close the cyber security gap.
- Using these scores also makes it easier to prioritise where you need to focus your efforts. Addressing areas where there is a large disparity between your actual score and your target score should be your first priority. With this essential knowledge, you can create a strategic plan for implementing the NIST Framework.
- Once you have a plan, now is the time to implement it. Using the knowledge you have about the current state of your cyber security efforts, you can begin to improve at risk areas. It’s also important to remember that your cyber security plan isn’t just a box to check and forget. Instead, you need to see it as an ongoing effort that needs to be updated and reevaluated as your business and security features change.
- As you implement your plan, you should also use this opportunity to document all processes associated with your cyber security efforts and create training materials based on those processes.
- Finally, be sure to check out all the resources NIST has to offer. These guides will help you navigate the framework implementation process, and determine the best course of action for your business. Resources, divided by function, are especially helpful for understanding the precise application of these security efforts in your business.
- Using the NIST Cybersecurity Framework is a smart way to reduce the risk of a data breach. One way to easily align with NIST cyber security standards is by adopting secure file sharing solutions. With built-in security measures, you can save time by adopting a single solution with multiple security functionalities. With the right strategy and a secure file sharing solution implemented in your organisation, you will know that your data is sufficiently secure.
6 Steps for Implementing the NIST Cybersecurity Framewor:
1. Set Your Goals
The first thing you should do before implementing the NIST Framework is to set your own organisational goals regarding your data security. What level of risk are you comfortable with? Which areas of your business need security the most? Setting goals allows you to organise your actions, establish a scope for your safety efforts, and prioritise which steps are most important and should be taken first. Plus, it allows everyone in your organisation to be on the same page.
2. Create a Detailed Profile
Not every business has the same cyber security requirements. Although the NIST framework is billed as a voluntary set of guidelines applicable to many industries, its application to your business may look different from your peers. The Framework Implementation tiers help you identify where your business needs improvement and what steps should be taken to make those improvements a reality. The levels are listed below:
Tier 1: Partial – This means that your cyber security practises are generally responsive to any cyber security incident.
Tier 2: Risk-Informed – This level describes companies that may be aware of certain risks and are regularly planning how to respond to that risk.
Tier 3: Repeatable – The repeatable tier applies to companies that have clearly outlined and regularly repeatable cyber security procedures.
Tier 4: Adaptive – Adaptive companies are proactive in terms of cyber security measures, responding to incidents rather than preventing them.
It is not necessary that you move from Tier 1 to Tier 4 as soon as possible. Conversely, progress through the levels should be when it is the smartest decision for your company from a cost and safety standpoint.
3. Set Your Current Position
4. Analyse any gaps and identify necessary actions
5. Implement Your Plan
6. Leverage NIST Resources
- It’s easy to think that NIST compliance and data security only apply to IT departments. In fact, everyone in your organisation who owns or has access to your computer plays a role in maintaining cyber security standards. Since the framework is a voluntary cyber security measure, it is easy for employees to feel that this is not their problem. Certainly not so.
- For example, an email sent over a public Wi-Fi connection at a coffee shop can have dire consequences. Therefore, you need everyone on board with your security efforts. While it is imperative that your IT team is familiar with and actively aligned with the NIST framework, it is wise for everyone in your organisation to be aware of it and the role individuals play in maintaining standards.
- The NIST Cybersecurity Framework is a set of best practises that organisations can use to keep their data secure. Created by the National Institute of Standards and Technology, the framework was designed to make cost-effective data security possible for organisations of any size. While implementation of the framework is voluntary, it is wise for your organisation to implement these processes and work towards ongoing alignment. Doing so reduces the risk of cyber security breaches.
Who Is Impacted by the NIST Framework?:
- A cyber security framework is an essential element in dealing with the threat of cybercrime for your business. Without clear goals and an understanding of the level of risk tolerance, it becomes extremely difficult to measure the success of your cyber security efforts.
- By following these five clear steps and tailoring NIST CSF to your business, you are providing your business with the best possible path to successfully combating cybercrime, helping to protect unauthorised access to data centres and other computerised systems. are doing.
- If you’d like to talk to us about your cyber security needs and learn more about building a cyber security infrastructure for your business, talk to one of our teams today.
Conclusion:





