
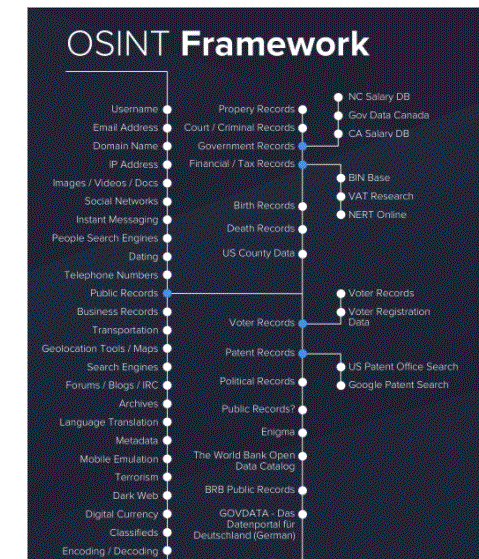
OSINT framework focused on gathering information from free tools or resources. The intention is to help people find free OSINT resources.
- Introduction to OSINT Tools – Open Source Intelligence
- OSINT history: From spycraft to IT
- What Is Open Source Intelligence
- Top OSINT tools
- How Is Open Source Intelligence Used?
- The Dark Side of Open Source Intelligence
- Why is OSINT important?
- Benefits of OSINT Framework
- Conclusion
Introduction to OSINT Tools – Open Source Intelligence:
Description of OSINT
Open source intelligence (OSINT) is the practice of gathering information from published or publicly available sources. OSINT operations, whether performed by IT security professionals, malicious hackers, or government-sanctioned intelligence agents, use advanced techniques to search the vast amount of visible data to find the needles they need to achieve their goals — and to learn information that many do not realize is public. Open source in this context does not refer to the flow of open source software, although most OSINT tools are open source; instead, it describes the social status of the data being analyzed.
OSINT in many ways is an operational security mirror image (OPSEC), a security mechanism by which organizations protect public data about them that can, if properly analyzed, reveal harmful facts. IT security departments are increasingly tasked with performing OSINT functions in its organizations to enhance operational security.

OSINT history: From spycraft to IT:
During the 1980’s, the military and intelligence services began removing some of their intelligence-gathering activities away from secret activities such as trying to read enemy emails or tapping their phones to discover hidden secrets. Instead, an effort was made to look for practical resources that were available free of charge or that were officially published.
The world at that time was changing, and although social media had not yet done so, there were many sources such as newspapers and public information that contained interesting and sometimes useful information, especially if someone was able to connect multiple dots. The name OSINT was originally coined to refer to this type of espionage.
These same methods can now be used for cybersecurity protection. Most organizations have large, community-oriented infrastructure that includes multiple networks, technologies, hosting resources and name spaces. Information can be stored on employee desktops, prem asset servers, by BYOD-managed devices, in the cloud, embedded within devices such as webcams, or even hidden in source code for applications and applications.
In fact, IT employees in large companies probably know nothing about every asset in their business, public or not. Add to this the fact that many organizations also own or control a few additional assets indirectly, such as their social media accounts, and there is a lot of potential information sitting there that could be harmful at the wrong hands.
- It is produced by information that is publicly available
- Collected, analyzed, and distributed in a timely manner to the right audience
- It deals with a certain need for ingenuity
- The key phrase to focus on here is “publicly available.”
- Maltego
- You want
- SpiderFoot
- Spyse
- Built By
- Intelligence X
- DarkSearch.io
- Grep.app
- Recon-ng
- Reaper
- Shodan
- Metagoofil
- Search code
- SpiderFoot
- Babe X
- Now, it’s time to handle the second major issue with open supply intelligence: once one thing is instantly on the market to intelligence analysts, it’s additionally simple to seek out discouraging characters.
- Terrorist actors use open supply intelligence tools and techniques to spot potential targets and exploit weaknesses in targeted networks. Once danger is known, it’s typically the quickest and easiest method to implement and deliver the goods through numerous malicious functions.
- This method is one amongst the many reasons why little and medium enterprises are hacked per annum. This can be not as a result of specifically vulnerable teams having an interest in them, however rather as a result of the danger to their network or web site construction is detected using of straightforward open supply methods. In short, they’re simple prey.
- And open supply intelligence doesn’t alter technological attacks on systems and networks. Chilling players additionally get data concerning people and organizations which will be accustomed to inform high-level social engineering campaigns of using, sensitive fraud (email), vishing (phone or voicemail), and SMiShing (SMS). Often, on the face of it innocent data shared through social media and blogs are often accustomed to develop convincing social engineering campaigns, that area unit accustomed to trick well-meaning users into compromising their organization’s network or assets.
- That’s why using of open supply intelligence for security functions is thus necessary – It offers you the chance to get proper weaknesses in your organization’s network and extract sensitive data before the threatening character uses equivalent tools and ways to use them.
- Now that we’ve coated the utilization of open supply intelligence (both smart and bad) it’s time to appear at alternative methods which will be accustomed to collect and method open supply info.
- First, you wish to own a transparent strategy Associate in Nursing, an existing framework for deed and mistreatment of open supply intelligence. it’s not suggested to approach open supply information with a read to find something and everything which may be attention-grabbing or helpful – as we’ve already mentioned, the Brobdingnagian quantity of knowledge accessible through open sources can merely be frustrating.
- Instead, you wish to grasp specifically what you’re making an attempt to realize – as an example, to spot and proper weaknesses in your network – and specialize in your strengths particularly in achieving those goals.
- Second, you must determine a group of tools and techniques for aggregation and process open supply info. Once again, the number of knowledge accessible is just too giant for manual processes to be ineffective.
- As we have a tendency to speak, assortment|The gathering} of open supply intelligence falls into 2 categories: the sensible assortment and therefore the practical collection.
- Inactive collections usually involve the utilization of spying forums (TIPs) to integrate a spread of threatening feeds into one, simply accessible space. whereas this is often a serious step in gathering hand-made intelligence, the danger of knowledge overload continues to be important. Advanced intelligent solutions like Record Future address the matter by mistreatment AI, machine learning, and tongue process to make a prioritization method and eliminate warnings supported specific structure wants.
- In the same manner, organized threat teams usually use botnets to assemble necessary info mistreatment techniques like traffic sniffing and key work.
- A practical cluster, on the opposite hand, is the use of varied techniques to go looking for specific info or info. For security professionals, this kind of assortment work is typically in hot water one in every of 2 reasons:
- A slightly collected warning highlights the potential threat and any understanding is required. The focus of the intelligence-gathering work is extremely clear, as is that the entry assessment task.
- All OSINT strategies do not always work. Although this book covers a wide range of search tools and theater theories that apply to OSINT’s professional practice, not all of these tools can be used in all situations. Instead, an integrated approach is required that requires the use of the right tool at the right time. The obvious question is how does a detective know this? By identifying the web layer (High, Deep and Dark) which is their investigation. From this point on, identifying the right tools and methods should be straightforward.
- Do not try to memorize all the OSINT methods mentioned in this manual. Try not to memorize the details of the procedure but focus on understanding the broad concept that underpins the process. Once a detective knows what they are trying to do, it is an easy task to re-identify the tools and how they will achieve their goal. Thus, this manual should be used as a reference manual for OSINT stated strategies.
- OSINT is not a silver coin or a storage device. Like any other intelligence-gathering skill, OSINT can be both successful and unsuccessful within a comprehensive investigation process. The key to avoiding disappointment is looking at what POINT is: another investigation tool. If it does not produce a result within the context of the investigation, be prepared to use alternatives to achieve your goal.
- OSINT is a changing environment. As soon as this book is published it will be out of date. This is a testament to how quickly open-mindedness grows with new tools, techniques and best practice practices emerging almost daily. Keep pace with this upgrade and align your OSINT toolbox correctly; this will keep current and up-to-date capabilities and OSINT compliant with your professional performance.
What Is Open Source Intelligence:
Before we look at common sources and the use of open-source wisdom, it is important to understand what they really are. According to U.S. civil law, open-source intelligence:
The term “open source” refers specifically to the information available to the public. If any special skills, tools, or techniques are required to access a piece of information, it will not be considered an open-source. Most importantly, open-source knowledge is not limited to what you can find using large search engines. Web pages and other services that can be accessed through Google are certainly great sources of open-source information, but they are far from the only source.
First, a large portion of the Internet (over 99 percent, according to former Google chief executive Eric Schmidt) could not be found using large search engines. The so-called “deep web” is a host of websites, websites, files, and more (for many reasons, including the presence of login pages or payment walls) that cannot be identified by Google, Bing, Yahoo, or any other method. search engine you like to think. Apart from this, much of the deep web content can be considered as open source because it is easily accessible to the public.
Top OSINT tools:
Using the right OSINT tool for your organization will improve cybersecurity by serving to access info concerning your company, employees, IT assets and alternative confidential or sensitive info which will be exploited by the assailant. obtaining that info initially and so concealment or deleting it will scale back everything from fraud to malicious activity. The following (random) area unit a number of the highest tools employed by OSINT, what areas they focus on, why they’re distinctive and completely different from others, and what certain quantity they’ll be ready to wake the organization’s on-line security efforts.
Maltego
Maltego focuses on exposing relationships between people, companies, domains and in public accessible info on-line. It’s additionally glorious for taking giant amounts of knowledge typically and organizing it all with easy-to-read charts and graphs. Graphs do a decent job of capturing immature intelligence and creating it work, and every graph will have up to ten,000 information points.
You want
Available as a Chrome extension and Firefox extension, Mitaka allows you to hunt for over a dozen search engines for IP addresses, domains, URLs, hashs, ASNs, Bitcoin case addresses, and varied compatibility indicators (IOCs) in your application.
Izembe Sharma
Extension saves it slow by serving as a cutoff to an internet information that may be asked with a click. For those choosing a centered, restricted set, another satellite extension is on the market.
Spyse
Spyse describes itself as a “complete on-line plus register” targeted at on-line security specialists. Hoping on the likes of OWASP, IntelligenceX, and Spiderfoot as mentioned above, Spyse collects in public on the market knowledge from websites, owners, connected servers, and IoT devices. This knowledge was then analyzed by Spyse engine to find any security risks and communications between the varied organizations.
Built By
As the name implies, BuiltWith enables you to discover what in style websites square measure engineered for. completely different|completely different} technical stacks and forums change different sites. BuiltWith, as an example, might realize that an internet site uses WordPress, Joomla, or Drupal as its CMS and provides further data.
Intelligence X
Intelligence X may be a service of its reasonably archiving and computer programme that not solely retranslates historical versions of websites however conjointly leaks knowledge that has been aloof from the net because of unfavorable nature of content or legal reasons. whereas which will sound like what the web Archive’s Wayback Machine will, Intelligence X encompasses a massive distinction once it involves content-oriented content management. Once it involves storing knowledge sets, however controversial , Intelligence X doesn’t discriminate.
DarkSearch.io
Although frequent internet guests could also be acquainted with wherever to seem, for people who could also be new, DarkSearch.io is an excellent place to begin for his or her analysis activities. Just like the different black internet computer programme Ahmia, DarkSearch is free, however it comes with a free API to use automatic search. Although each Ahmia and DarkSearch have .onion sites, you do not have to attend particle versions or use Tor to access one amongst these search engines. Quick access to darksearch.io from a customary application can enable you to look at the dark internet.
Grep.app
How does one seek for million crumb repos across the Internet? positively, you’ll strive for the only search bars provided by GitHub, GitLab, or BitBucket, but Grp.app will do the task all right. In fact, Grep.app has recently been utilized by Twitter users and journalists persistently to urge a plan a plan several shelves are using the Codecov Bash
Reaper
One of the best tools you’ll be able to use on this list, Harvester is intended to capture public data accessible outside the organization’s network. It will observe dangerous objects on internal networks similarly, however most of the tools it uses look outward. It will serve as a pre-test take a look at or entry take a look at or similar tests.
Shodan
Shodan may be a dedicated program wont to realize insights into devices just like the billions of internet-enabled (IoT) devices that are seldom searchable, however are happening everywhere of late. It also can be wont to observe such things as open holes and vulnerabilities in targeted systems. Some OSINT tools like Harvester use it as a knowledge supply, though deep interaction with Shodan needs a paid account.
Metagoofil
Another tool freely offered on GitHub, Metagoofil is meant to extract information from public documents. Metagoofil will browse virtually any sort of document I will access through public channels together with .pfd, .doc, .ppt, .xls and lots of a lot of.
search code
For people who got to get extremely deep into the advanced matrix of the OSINT assortment, the search code may be a terribly specialized programme that seeks usable ingenuity at intervals in the ASCII text file. This improbably powerful engine is the work of one engineer.
Babe X
Important info isn’t forever in English. solely a few quarter of net users speak English as their primary language consistent with Statista, though numerous sources say concerning fifty fifth of on-line content in English. the knowledge you wish could also be in Chinese, Spanish or Tamil.
How Is Open Source Intelligence Used?
The Dark Side of Open Source Intelligence:
Why is OSINT important?
OSINT is critical to keeping tabs on that information mess. It needs to accomplish three key functions within OSINT, and a variety of OSINT tools have been developed to help meet those needs. Many tools work for all three functions, though many do well somewhere.
Acquisition of publicly traded assets
Their most common function is to help IT teams find community resources and to map out what information each person has that may be contributing to a potential attack. Usually, they do not attempt to look for things like system vulnerability or login testing. Their main function is to record what information a person can obtain publicly or about company assets without fraud.
Get important information outside of the organization
The second function of certain OSINT tools is to search for related information outside the organization, such as social media posts or domains and locations outside of a well-defined network. Procurement agencies, who deliver the IT assets of the company they meet, can find this service very useful. In view of the extreme growth and popularity of social media, looking outside the company’s perimeter with sensitive information is probably useful for any group. Collect obtained information into usable form.
Finally, some OSINT tools help to compile and compile all the information obtained into usable and useful intelligence. Starting an OSINT scan for a large business can produce hundreds of thousands of results, especially if both internal and external assets are installed. Gathering all that data and being able to deal with the biggest problems first can be very helpful.
Benefits of OSINT Framework:
OSINT strategies and methods have many benefits:
Money-Save- For small or medium-sized companies, common data collection tools and strategies may seem like a huge investment. Using OSINT requires little or no investment as by definition the information is free.
It’s legal- Since the information collected has not yet been described as segmented and publicly disclosed with the permission of the actual source, it is absolutely legal to collect any data you may find.
Always Updated- Due to the public nature of the resources used by OSINT, users are likely to add and update their information regularly.
Homeland Security- OSINT has proven to be a very useful tool in dealing with national security issues.
Great Photo View- Business owners and other company decision-makers can get a broader perspective on their research using OSINT information, which allows them to develop long-term strategic plans to achieve a range of business objectives.
Conclusion:





