
- Kerberos authentication is currently the default authorization technology used by Microsoft Windows, and implementations of Kerberos exist in Apple OS, FreeBSD, UNIX, and Linux.
- Microsoft introduced their version of Kerberos in Windows2000. It has also become a standard for websites and Single-Sign-On implementations across platforms. The Kerberos Consortium maintains Kerberos as an open-source project.
- Kerberos is a vast improvement on previous authorization technologies. The strong cryptography and third-party ticket authorization make it much more difficult for cybercriminals to infiltrate your network.
- It is not totally without flaws, and in order to defend against those flaws, you need to first understand them.
- Kerberos has made the internet and its denizens more secure, and enables users to do more work on the Internet and in the office without compromising safety.
- Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography.
- A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos is available in many commercial products as well.
- The Internet is an insecure place. Many of the protocols used in the Internet do not provide any security. Tools to “sniff” passwords off of the network are in common use by malicious hackers.
- Thus, applications which send an unencrypted password over the network are extremely vulnerable. Worse yet, other client/server applications rely on the client program to be “honest” about the identity of the user who is using it.
- Other applications rely on the client to restrict its activities to those which it is allowed to do, with no other enforcement by the server.
- Some sites attempt to use firewalls to solve their network security problems. Unfortunately, firewalls assume that “the bad guys” are on the outside, which is often a very bad assumption. Most of the really damaging incidents of computer crime are carried out by insiders.
- Firewalls also have a significant disadvantage in that they restrict how your users can use the Internet. (After all, firewalls are simply a less extreme example of the dictum that there is nothing more secure than a computer which is not connected to the network — and powered off!) In many places, these restrictions are simply unrealistic and unacceptable.
- Kerberos was created by MIT as a solution to these network security problems. The Kerberos protocol uses strong cryptography so that a client can prove its identity to a server (and vice versa) across an insecure network connection.
- After a client and server has used Kerberos to prove their identity, they can also encrypt all of their communications to assure privacy and data integrity as they go about their business.
- Kerberos is freely available from MIT, under copyright permissions very similar those used for the BSD operating system and the X Window System.
- MIT provides Kerberos in source form so that anyone who wishes to use it may look over the code for themselves and assure themselves that the code is trustworthy.
- In addition, for those who prefer to rely on a professionally supported product, Kerberos is available as a product from many different vendors.
- Kerberos is a client-server authentication protocol that enables mutual authentication – both the user and the server verify each other’s identity – over non-secure network connections.
- The protocol is resistant to eavesdropping and replay attacks, and requires a trusted third party.
- The Kerberos protocol uses a symmetric key derived from the user password to securely exchange a session key for the client and server to use.
- A server component is known as a Ticket Granting Service (TGS) then issues a security token (AKA Ticket-Granting-Ticket TGT) that can be later used by the client to gain access to different services provided by a Service Server.
Kerberos protocol overview
- A simplified description of how Kerberos works follows; the actual process is more complicated and may vary from one implementation to another.
- For the purposes of this discussion, the initiating client in the scenario below is a corporate laptop running Windows, and an end user is trying to log into the corporate network.
- To start the Kerberos authentication process, the initiating client sends a request to an authentication server for access to a service. The initial request is sent as plaintext because no sensitive information is included in the request.
- The authentication server retrieves the initiating client’s private key, assuming the initiating client’s username is in the KDC database. If the initiating client’s username cannot be found in the KDC database, the client cannot be authenticated and the authentication process stops.
- If the client’s username can be found in the KDC database, the authentication server generates a session key and a ticket granting ticket. The ticket granting ticket is timestamped and encrypted by the authentication server with the initiating client’s password.
- The initiating client is then prompted for a password; if what is entered matches the password in the KDC database, the encrypted ticket granting ticket sent from the authentication server is decrypted and used to request a credential from the ticket granting server for the desired service.
- The client sends the ticket granting ticket to the ticket granting server, which may be physically running on the same hardware as the authentication server, but performing a different role.
- The ticket granting service carries out an authentication check similar to that performed by the authentication server, but this time sends credentials and a ticket to access the requested service.
- This transmission is encrypted with a session key specific to the user and service being accessed. This proof of identity can be used to access the requested “kerberized” service, which, once having validated the original request, will confirm its identity to the requesting system.
- The timestamped ticket sent by the ticket granting service allows the requesting system to access the service using a single ticket for a specific time period without having to be re-authenticated.
- Making the ticket valid for a limited time period makes it less likely that someone else will be able to use it later; it is also possible to set the maximum lifetime to 0, in which case service tickets will not expire.
- Microsoft recommends a maximum lifetime of 600 minutes for service tickets; this is the default value in Windows Server implementations of Kerberos.
How Kerberos works?
So let’s see how this works. As I mentioned this includes following three entities,
- Client: a user, a service of any software.
- Server: where the kerberos protected resource/service is hosted
- Key Distribution Center (KDC): The trusted third-party authentication service
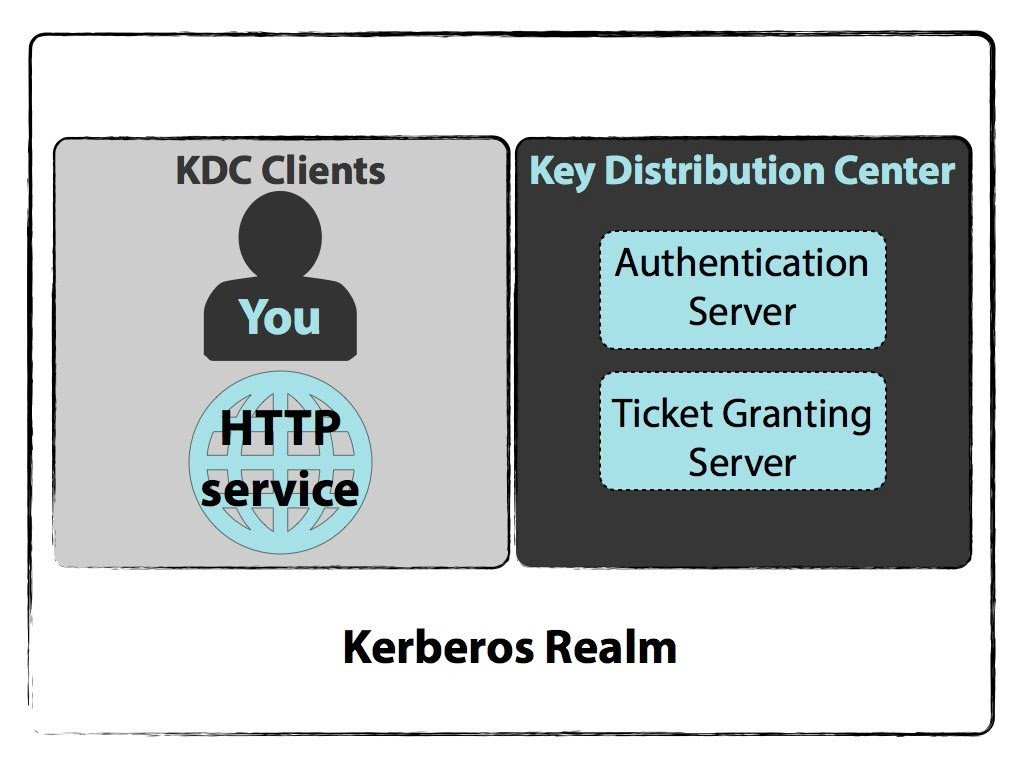
The KDC includes following two servers:
- Authentication Server (AS) that performs the initial authentication and issues ticket-granting tickets (TGT) for users.
- Ticket-Granting Server (TGS) that issues service tickets that are based on the initial ticket-granting tickets (TGT).
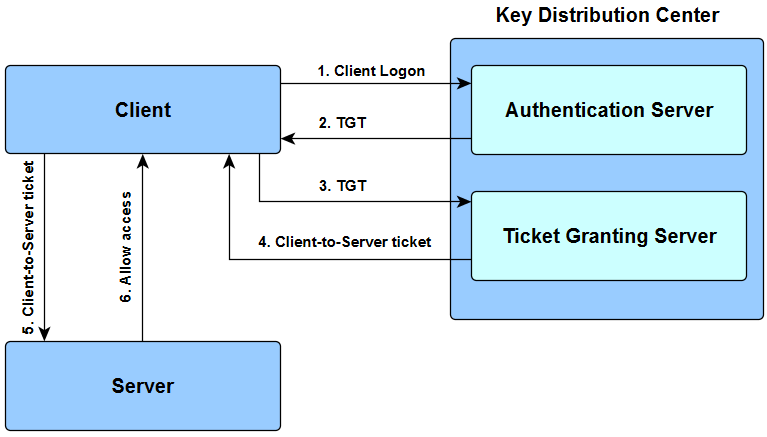
- Client sends a request to Authentication Server (AS) with plaintext user ID and asking for a server access on behalf of the user. This request is partially encrypted with a secret key which is the password of the client user.
- Authentication Server (AS) retrive the secret key (user’s password) from the user DB based on the user ID and use his password as a key to decrypt the request. That is how the user is verified. Then the AS sends a Ticket-Granting Ticket (TGT) encrypted with another secret key which is shared between AS and Ticket-Granting Server (TGS).
- Client send the encrypted TGT to the Ticket-Granting Server (TGS) requesting the access for the server.
- Ticket-Granting Server (TGS) decrypt the TGT with shared secret key with AS and issue a kerberos token to the client which is encrypted with another shared secret key with TGS and server.
- Client sends a request to server with the encrypted kerberos token.
- Then the server allow the access to the requested resources to the client for a certain period of time specified in the token.
- That’s how the basic kerberos flow works and it’s pretty straightforward. So all the communication steps involve shared secret keys which makes kerberos is a very good example of symmetric key encryption!
How do you authenticate with Kerberos?
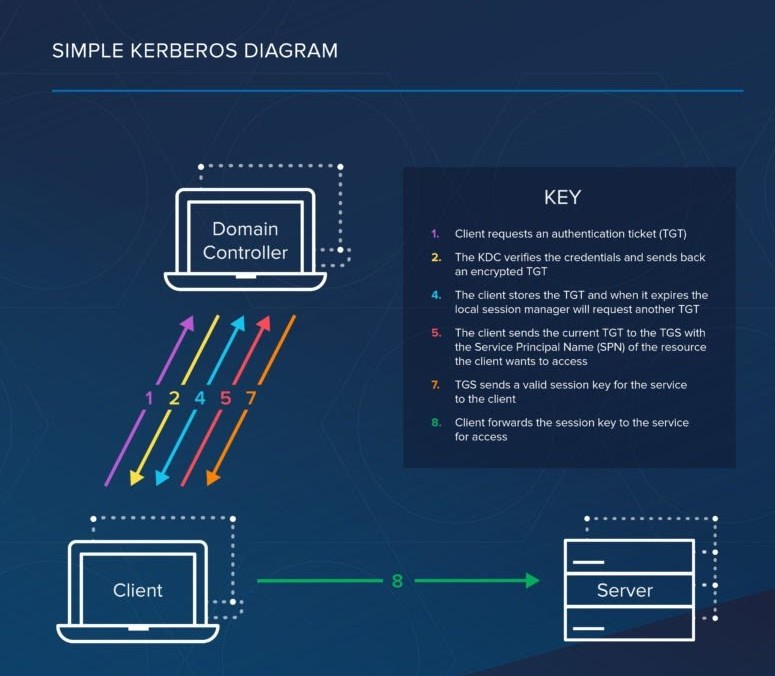
Here are the most basic steps taken to authenticate in a Kerberized environment.
- Client requests an authentication ticket (TGT) from the Key Distribution Center (KDC)
- The KDC verifies the credentials and sends back an encrypted TGT and session key
- The TGT is encrypted using the Ticket Granting Service (TGS) secret key
- The client stores the TGT and when it expires the local session manager will request another TGT (this process is transparent to the user)
- The client sends the current TGT to the TGS with the Service Principal Name (SPN) of the resource the client wants to access
- The KDC verifies the TGT of the user and that the user has access to the service
- TGS sends a valid session key for the service to the client
- Client forwards the session key to the service to prove the user has access, and the service grants access.
What is going to replace Kerberos?
- There are no real contenders to replace Kerberos in the pipeline. Most of the advancements in security are to protect your password or provide a different method of validating who you are to Kerberos.
- Kerberos is still the back-end technology. Kerberos excels at Single-Sign-On (SSO), which makes it much more usable in a modern internet based and connected workplace.
- With SSO you prove your identity once to Kerberos, and then Kerberos passes your TGT to other services or machines as proof of your identity.
- The weakest link in the Kerberos chain is the password. Passwords can be brute-force cracked or stolen by phishing attacks. For this reason, Multi-Factor Authentication (MFA) is becoming more popular to protect online identities.
- With MFA, you need the password and something else – a randomized token, mobile phone, email, thumbprint, retina scan, facial recognition, etc. – to prove that you are in fact who you are telling Kerberos you are.






