
- Introduction of TCP and UDP
- Overview of TCP (Transmission Control Protocol)
- Overview of UDP (User Datagram Protocol)
- Key Differences Between TCP and UDP
- Reliability and Data Integrity in TCP
- Speed and Efficiency of UDP
- Use Cases of TCP vs UDP
- TCP vs UDP in Network Performance
- Conclusion
Introduction of TCP and UDP
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are core communication protocols used for transmitting data over the Internet. TCP is a connection-oriented protocol that ensures reliable, ordered delivery of data by establishing a connection before data transfer and using error-checking mechanisms. It is commonly used for applications requiring accuracy, such as web browsing, email, and file transfers. In Cybersecurity Training Courses, UDP is a connectionless protocol that provides faster, but less reliable, data transmission without establishing a prior connection or performing error correction. It is ideal for time-sensitive applications like video streaming, online gaming, and voice communication, where speed is prioritized over accuracy. Both protocols operate at the transport layer of the OSI model and serve distinct purposes depending on the application’s needs.
To become a certified cyber security, have a look at our Cyber Security Online Training right now.
Overview of TCP (Transmission Control Protocol)
- TCP (Transmission Control Protocol) is one of the main protocols of the Internet Protocol (IP) suite and is used to ensure reliable and ordered communication between devices over a network.
- It is a connection-oriented protocol, meaning a connection must be established between the sender and the receiver before data transmission begins.
- TCP guarantees that data packets will arrive in the correct order and without errors, making it ideal for applications where reliability and data integrity are critical, such as Website Server, file transfers, and email.
- TCP operates by breaking down large data messages into smaller packets, which are transmitted across the network. Each packet contains sequence numbers, which help the receiver reassemble them in the correct order.
- If any packets are lost or corrupted, TCP ensures they are retransmitted, providing reliability. It also performs flow control to manage data transfer rates and congestion control to prevent network overload.
Overview of UDP (User Datagram Protocol)
- UDP (User Datagram Protocol) is another protocol in the IP suite, but unlike TCP, it is connectionless and does not guarantee reliable data delivery. UDP sends data in discrete packets, called Data Classification, without establishing a connection.
- This lack of a handshake makes UDP faster than TCP, as it avoids the overhead of connection setup, flow control, and error checking.
- Since UDP does not offer error correction or ensure the delivery of data, it is often referred to as an unreliable protocol.
- However, it is suitable for applications where speed is more important than reliability, such as real-time communications (VoIP), online gaming, video streaming, and DNS queries.
- Applications that use UDP are typically responsible for managing packet loss, reordering, and error correction if necessary.
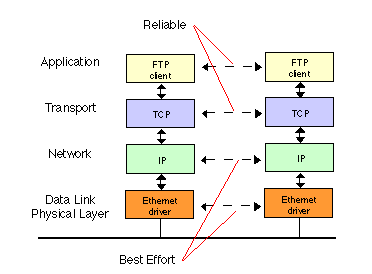
Key Differences Between TCP and UDP
- TCP: Connection-oriented protocol, requiring a three-way handshake before data transmission.
- UDP: Connectionless protocol, transmitting data without establishing a connection.
- TCP: Provides reliable data delivery, ensuring packets are delivered in the correct order and retransmitting lost or corrupted packets.
- UDP: This does not guarantee reliability or packet order, meaning packets can be lost, duplicated, or arrive out of order.
- TCP: Includes error checking and correction mechanisms, such as checksums and acknowledgments, to ensure data integrity.
- UDP: Includes basic checksums for error detection but does not offer retransmission or correction of errors.
- TCP: Implements flow control to avoid congestion and ensure that the sender does not overwhelm the receiver.
- UDP: Does not have flow control or congestion management mechanisms, making it faster but less reliable under Network Topology.
- TCP:Slower due to overhead from connection establishment, flow control, error correction, and retransmission.
- UDP: Faster, as it has minimal overhead and no mechanisms for ensuring data delivery or order.
- TCP:Used for applications where reliability is important, such as web browsing, email, and file transfers.
- UDP: Suitable for real-time applications like VoIP, online gaming, and video streaming, where speed is more critical than reliability.
- Minimal Overhead: UDP headers are much smaller than TCP headers, and there is no need for handshakes, acknowledgments, or retransmissions.
- Lower Latency: Because there are no connection setup procedures or error correction mechanisms, data is sent and received almost immediately, making UDP suitable for applications requiring low latency.
- Efficiency in Broadcasting: UDP supports broadcasting (sending data to multiple receivers), making it more efficient for scenarios like video streaming and online gaming, where Cybersecurity and Data Science needs to be sent to multiple clients at once.
- Better for Real-Time Communication: Since UDP does not wait for acknowledgments or retransmit lost packets, it can maintain real-time communication, even if some data is lost, such as in voice or video calls.
- Web Browsing (HTTP/HTTPS): Reliability and correct delivery of web pages are essential.
- Email (SMTP, IMAP, POP3): Reliable delivery of emails is required, including attachments.
- File Transfer (FTP): Ensures that large files are transferred correctly and completely.
- Remote Access (SSH, Telnet): Secure connections with guaranteed data integrity for remote system management. UDP Use Cases:
- Streaming Media (Video, Audio): RUDP is commonly used for real-time streaming of video and audio, where a few lost packets are not critical.
- VoIP (Voice over IP) Real-time voice communication, where latency is critical, and occasional lost packets do not severely impact the conversation.
- Online Gaming: Speed is more important than reliability, and a few dropped packets may not disrupt gameplay.
- DNS Queries: The Domain Name System (DNS) uses UDP because it’s fast, and most DNS responses are small enough that reliability is less of a concern.
- TCP
Pros: Reliable, ordered, and error-free transmission. Ensures data integrity, flow control, and congestion management.
Cons:Slower due to connection setup, error correction, and retransmissions.
- UDP
Pros: Faster and more efficient with minimal overhead, making it suitable for real-time applications that tolerate some data loss.
Cons:Unreliable, with no guaranteed delivery, no ordering of packets, and no flow control.
Connection-Oriented vs. Connectionless:
Reliability:
Error Checking:
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training.
Flow Control and Congestion Control:
Speed and Efficiency:
Use Cases:
Reliability and Data Integrity in TCP
TCP ensures reliable data transmission through several key mechanisms. Each byte of data sent over TCP is assigned a sequence number, enabling the receiver to reorder packets that may arrive out of order. To further ensure reliability, the receiver sends an acknowledgment (ACK) for each packet it receives. If the sender doesn’t receive an ACK within a specified time, it retransmits the packet. Additionally in Cybersecurity Training Courses , TCP includes error checking via a checksum in each segment, allowing for the detection of transmission errors, which results in the retransmission of corrupted packets. Flow control, such as the sliding window protocol, regulates the data transmission rate between sender and receiver to prevent congestion and ensure the receiver’s buffer isn’t overwhelmed. Finally, TCP employs congestion control algorithms like slow-start and congestion avoidance to identify network congestion and reduce transmission rates when necessary. Together, these features guarantee data integrity, making TCP ideal for applications where reliable data delivery is essential.
Transform Your Career with Cyber Security Knowledge Enroll in ACTE’s Cyber Security Expert Masters Program Training Course Today!
Speed and Efficiency of UDP
UDP is often favored for its speed and low overhead. Since it is connectionless and does not establish a handshake or perform error checking and retransmissions, UDP is much faster than TCP in terms of raw data transmission. This speed comes at the cost of reliability, as packets may be lost or arrive out of order.
The key advantages of UDP’s speed and efficiency include:
Prepare For Your Cybersecurity Interview Questions and Answers With Our Comprehensive Cyber Security Interview Questions Bank. Get Started Now!
Use Cases of TCP vs UDP
TCP Use Cases: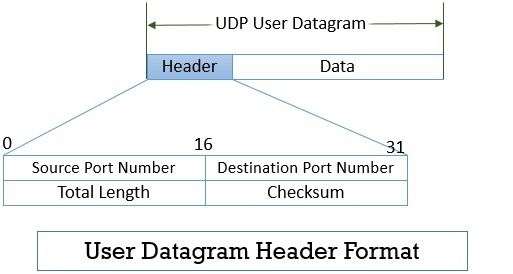
TCP vs UDP in Network Performance
In terms of network performance, TCP and UDP serve different purposes, and their performance depends on the specific requirements of the application:
Choosing between TCP and UDP for network performance largely depends on the specific application needs. If the application requires the guarantee that data will arrive in the correct order and without loss, TCP is the better choice. On the other hand, if the application is time-sensitive and can tolerate occasional packet loss, UDP is preferred for its speed and efficiency.
Conclusion
In conclusion, TCP is best suited for applications where reliability and data integrity are essential, while UDP excels in scenarios where speed and low latency are critical, and minor data loss is acceptable.Overall, the choice between TCP and UDP depends on the specific requirements of the application, such as security, efficiency, and performance in Cybersecurity Training . Understanding their strengths and limitations helps in selecting the right protocol for optimal network communication.





