
An ethical hacker also directed to as a white-hat hacker, is an information security (infosec) professional who penetrates a computer system, network, application, or another computing resource on behalf of its proprietors and with their permission.
- Introduction of Ethical Hacker Salary and Job Description
- Skills of Ethical Hacker
- Features / Characteristics of Ethical Hacker
- DNS spoofing
- Types/methods of Ethical Hackers
- Types of Hackers
- What it Takes to Become an Ethical Hacker
- Why Ethical Hacking is very important?
- Trends for Ethical Hacker
- Benefits of Ethical Hacker
- Conclusion
- By hijacking a computer program, the hacker must comply with the following rules:
- Written permission to scan the network and attempt to identify potential security risks.
- While engaging in fraudulent or related activities, a hacker should respect the privacy of the individual or the company.
- After completing his task, the scoundrel should not leave anything open for someone else to use later.
- Before hacking, a hacker should inform software developers or software developers that they are aware of any security risks to their software or hardware.
- In this case, the new Ethical Hacker can expect to receive Rs 4.8 lakh per year. However, candidates with higher education qualifications and work experience are up to Rs 30 lakh per year.
- Committing criminal acts involves repeating the tactics and actions of vicious attackers. This practice helps to identify security risks that can be addressed before a malicious attacker gets a chance to exploit them.
Introduction of Ethical Hacker Salary and Job Description:
An ethical criminal evaluates the organisation’s use of digital security to identify its weaknesses and propose development accordingly. They are professionals who can access networks to detect security risks. Black hat hackers use this threat to break the organisation’s cybersecurity system. Therefore, honest hackers often check the company’s network plans to identify areas that are at risk and repair them. They also train organisation staff on best practises and standards.
- Port scanners like Nmap or Nessus are used to scan organisational systems and find open holes. The risks for each port can be assessed and remedial measures taken.
- It checks the installation of security features and makes sure they are not exploited.
- Engaging in social engineering ideas such as dumpster diving — literally searching for trash cans to find passwords, charts, sticky notes, or anything else that has valuable information that can be used to produce an attack.
- Using other social engineering techniques such as shrugging your shoulders to gain access to important information or playing a kindness card tricks employees into giving up their passwords.
- Make efforts to avoid IDS (Intrusion Detection Systems), IPS (Access Control Programs), honey pots, and firewalls.
- Networks that smell, skip and break wireless encryption, and hijack web servers and web applications.
- Investigating issues related to mobile computer theft and employee fraud.
- Ethical hacker criminals are legally required to report any problems they encounter during their work, as this is legitimate information (in theory, at least) that could be used for illegal purposes. Of course, even the most sophisticated behavioural criminal skills are wasted if the organisation fails to adequately respond to any problems or weaknesses identified and reported.
Skills of Ethical Hacker:
Good Gang Skills and the Role of White Hats Hacks
Simply put, the job of a well-behaved criminal is to approach an organisation as if it were an internet criminal, repeating a vicious criminal on the job and then stop following the attack. Instead, they will report any danger or concern and seek counter-measures to strengthen the system’s defences.
A well-behaved criminal may use one or more of these tactics to get into the system or detect danger:
- They have good morals. Ethical hackers often gain access to confidential information.
- They are patient and persistent. Burglary in the system does not just happen.
- They think like a hacker.
- They think outside the box.
- Focus on the details.
- They love the challenge.
- They never stop reading.
- Smell of network traffic
- Set up various network attacks
- Use the risk of overflow baths
- SQL injection
- Guess and password
- Session hijacking and spoofing
Features / Characteristics of Ethical Hacker
A person with a code of ethics is expected to be proficient in managing database, network, and applications and has excellent soft skills as they need to communicate security issues across the organisation. In addition to these common skills, the ethical criminal also understands the following skills well:
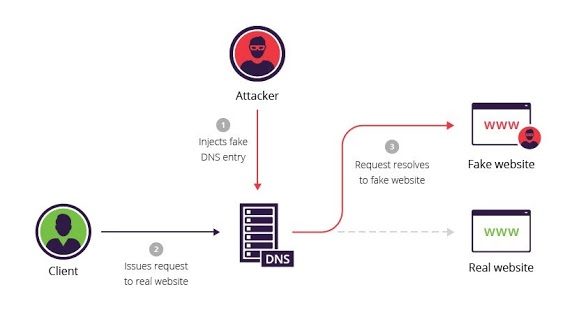
DNS spoofing
Apart from this, the moral hacker should be creative because black hat hackers always come up with clever ways to exploit the system and it is the job of the hacker of the character to predict and prevent such breaches.
Types/methods of Ethical Hackers
It is no secret that any system, process, website, device, etc., can be hacked. To understand how burglary can occur and how it can be detrimental, honest hearted hackers need to know how they feel as malicious hackers and know the tools and techniques they may use.
Types of Hackers:
The hackers are of different types and are named based on their intent to hack. Overall, there are two major hackers – White-Hat hacker and Black-Hat hacker. The names are derived from the ancient Spaghetti Westerns, where the good man wears a white hat and the evil one wears a black hat.
- Information Security Analyst
- Security Analyst
- Certified Ethical Hacker (CEH)
- Ethical Hacker
- Information Security Manager
- Login Checker
Job profile for Ethical hackers
After obtaining the much-needed CEH v10, a moral criminal could try the following roles:
- Moral criminals use their knowledge to protect and improve organisational technology. They provide essential services to these organisations by considering the risks that may lead to security breaches. An ethical hacker criminal reports an identified threat to an organisation.
- Here are some examples of real-life recruits from real hackers who represent the normal activities they may be performing in their roles.
- Manage work strategies and work collaboratively with various teams to improve site design and usability.
- Hire a hacker to hack facebook accounts!
- Hack, grade, & stack brick.
- Include inexpensive marketing strategies like Adwords and SEO to make money
- Perform daily data queries, create comments on the site using SQL.
- I worked ethically with Kali Linux and learned about physical security and cyber security.
- Established online consulting services.
- Use mobile-first interface designs using HTML5 levels.
- Update the list of available properties with information and photos.
- Support multiple departments in the development of intranet sites and applications.
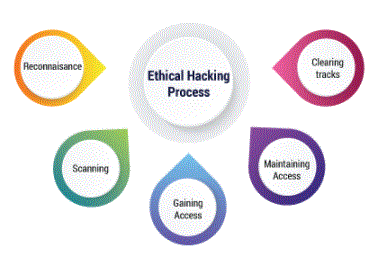
How its works:
structure of Ethical Hacker Process:
What it Takes to Become an Ethical Hacker :
If you are a former “bad hacker” who decided to wear your black and white hat, then you are probably familiar with trading strategies. However, you should also be aware that behavioural cheating skills (such as immoral cheating skills) are constantly changing. As good guys are always trying to keep up with the latest trends, it’s important to keep your edge by keeping your ear down.
As with any profession, love of industry is one of the keys to success. This, combined with strong network knowledge and planning, will help the professional to excel in the field of fine-tuning. Knowing how to think like a black hat shooter is fundamental to developing a person’s ethical cheating skills, but you also need to have a clear idea of your ultimate goal of improving the safety of your employer (or client).
Like other computer and network security roles, cybercriminals are in high demand, and this demand only grows as the intensity and cost of cyber attacks continue to rise. As you might expect, organisations that are in dire need of competent and certified ethical hackers are willing to pay a premium. In the United States, the average annual salary for a clever legal criminal is $ 90,000, but salaries usually go above $ 120,000 for experienced professionals.
- The main advantage of ethical theft is to protect the data from the theft and misuse of malicious attackers, as well as: To detect danger from the attacker’s POV so that weak points are corrected. Using a secure network that prevents security breaches.
- There are so many compelling reasons to consider moral fraud, and some of them may surprise you! For example, did you know that there are more cyberattacks happening now than ever before in the history of the universe? The latest measure of this is somewhere between one attack every 11 to 14 seconds.
- This means that companies, regardless of their size or power or profit, are always at risk of losing their valuable data, as well as any industry secrets they may be keeping close by. Needless to say, this translates to a very specific concern when it comes to assessing online safety concerns, as well as being at risk of threats, no matter what part of the spectrum is open to blocking.
- And there is a very good reason behind the increased responsibility now that needs to be borne by ethical hackers. Think about it – data, without a doubt, is one of the most important things a company can produce, acquire, or exchange today. Therefore, it can have a direct impact on the company’s line, not to mention the top one.
- Ethical criminals are therefore much needed these days, not only because they can protect the data needed by companies on a daily basis, but also because they can provide valuable ideas on how to make existing security systems better and more efficient in terms of monitoring. against malicious attacks and malware.
- If you love work when you feel the pressure to do it every day, then moral cheating is the right decision for your career! If you have already accepted that one of the best ways to be recognized is to put yourself in a position to die or to die, then moral ethics might be just right for you! Keep reading to find out what kind of jobs you expect in the amazing field of ethical fraud.
Why Ethical Hacking is very important?
Trends for Ethical Hacker:
Growing at the highest rate in all other IT areas, cybersecurity security has emerged as a platform for the highest growth of 2017, and possibly throughout the decade. During the 5 years between 2012 and 2017, the list of cybersecurity activities increased by 75% according to a survey by the Bureau of Labour Statistics. This has led to many vacant posts so many jobs are well paid.
Benefits of Ethical Hacker:
1. Think Like a Criminal
To be able to understand the hacker world you have to be able to think like him. Because most people do not think of them as hijackers it gives the hijackers an advantage. The average person does not know what technologies or methods criminals use to exploit the systems they control. When you take a certified ethical hacker course, you will learn the techniques used in digging and testing entries. You will receive practical training in thinking and acting like a criminal. A location similar to the criminal area has been set up, so you can see for yourself and mimic the types of situations you may encounter.
2. Protect Systems From Attack
As a CEH, you will have complete control over your organisation’s systems so that you can effectively protect them from cyber attacks. There is a huge amount of data available online for cyber criminals to use. With proven cybercrime training you will have the hacking skills needed to get into all the weaknesses in your organisation’s programs to learn how to protect that data. Knowing the weaknesses in your system will allow you to double your security perimeter. Possible attacks and intrusion on your organisation can lead to the loss of important data, often credit card breaches that make waves in the news, which can have far-reaching consequences and damage the reputation of the organisation.
3. The hacking business is booming
Aside from the fact that hackers make a lot of money by stealing, those on the hacking side of ethical hacking are also facing a boom. The need to train certified ethical hackers has grown exponentially due to the need for more than 500,000 security professionals. With so many organisations under attack, the demand for money has gone far beyond that. Although ethical hijackers are heavily employed by IT firms, other industries such as aviation, financial institutions, and hotels also employ CEHs. The types of profitable jobs available include network security managers, security managers and web security managers.
4. Obtain Professional Recognition
This capability alone has emerged as one of the most important in protecting the data infrastructure of an organisation. In addition to the financial compensation associated with such a certificate, you are also recognized as an expert in your field. The CEH certificate is internationally recognized as the most important certification we can have in the field of information security. Displaying this certificate will open many closed doors that some experienced but not yet certified have found impossible to open. According to the EC Council, this certificate is a complete industry-wide robbery course, containing 20 current security bases.
5. Gain Information
Learning all that you need to know about robbery, while it may be a sensitive subject, can also be fun. Not only do you increase awareness, but you also protect your online presence by ensuring that it is not compromised. One of the best points to study in order to become a criminal is to expose yourself to the world of the dark web. Being able to sift through and navigate through the deep black waters of the black web will expose you to the onslaught of pre-existing attacks.
Conclusion
Being a Certified Ethical Hacker can be beneficial for almost any information security or professional career. Not only will you learn about the innovative and rewarding industry, but you will also be well rewarded for your skills.
The availability of jobs in this sector guarantees that you will never run out of money when it comes to income. Otherwise you will be recognized as an expert in the field, which can create more jobs and increase your chances of earning money.





