
The Data Encryption Standard (DES), as well as other documents, defines how to use the DES algorithm to encipher data.
- Introduction of Data cryptography standard (DES)
- However will DES work?
- Why is DES unsafe?
- Successors to DES
- How is DES used today?
- DES and 3DES still be used in restricted ways
- Conclusion
- good cards
- SIM cards
- modems
- routers
- set-top boxes
Introduction of Data cryptography standard (DES)
The recognition of DES has been slightly on the decline. Data Encryption customary (DES) is an out-of-date regular key methodology of knowledge encryption. it absolutely was adopted in 1977 for presidency agencies to guard sensitive data and was formally retired in 2005.
IBM researchers originally designed the quality within the early 1970s. it absolutely was then adopted by the U.S. National Bureau of Standards — currently the National Institute of Standards and Technology, or federal agency — as an officer Federal data Processing customary (FIPS) in 1977 for the cryptography of economic and sensitive however unclassified government pc data.
DES was the primary encodeion formula the U.S. government approved for public disclosure. This move ensured it absolutely was quickly adopted by industries, like monetary services, that required sturdy encryption. thanks to its simplicity, DES was additionally utilized in a spread of embedded systems, together with the following:
However will DES work?
DES uses constant key to encrypt and decipher a message, so each the sender and the receiver should understand and use constant non-public key. DES was once the go-to, regular key formula for the cryptography of electronic data, however it’s been outmoded by the safer Advanced cryptography customary (AES) algorithm.
Some key options moving however DES works embrace the following:
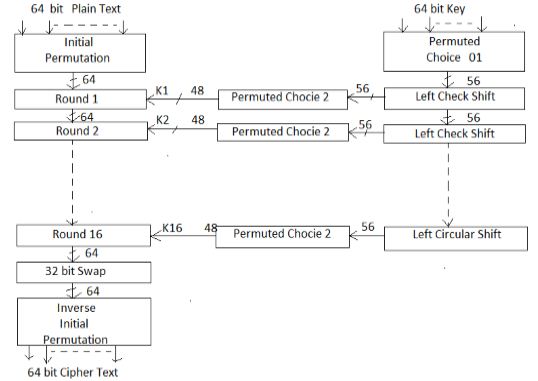
Block cipher. the info cryptography customary could be a block cipher, which means a cryptographical key and algorithm are applied to a block of knowledge at the same time instead of one bit at a time. To encode a plaintext message, DES teams it into 64-bit blocks.
many rounds of cryptography. The DES method involves encrypting sixteen times. It will run in four totally different modes, encrypting blocks severally or creating every cipher block captivated with all the previous blocks. coding is solely the inverse of encryption, following constant steps however reversing the order during which the keys are applied.
64-bit key. The encryption formula generates 16 different 48-bit subkeys, one for each of the sixteen cryptography rounds. Subkeys are generated by choosing and permuting components of the key as outlined by the DES formula.
Replacement and permutation. replacement and permutation that the ciphertext undergoes throughout the encryption process.
Backward compatibility. DES additionally provides this capability in some instances.
Why is DES unsafe?
The DES encryption algorithm has largely been replaced by the AES encryption algorithm.
For any cipher, the foremost basic methodology of attack is brute force, that involves making an attempt every key till you discover the proper one. The length of the key determines the amount of doable keys — and thence the practicability — of this kind of attack.
The effective DES key length of fifty six bits would need a most of 256, or concerning seventy two quadrillion, tries to seek out the right key. this can be not enough to shield information with DES against brute-force attempts with trendy computers.
Few messages encrypted victimisation DES before it absolutely was replaced by AES were possible subjected to this quite code-breaking effort. Nevertheless, several security specialists felt the fifty six-bit key length was inadequate even before DES was adopted as a standard. There have continuously been suspicions that interference from the National Security Agency weakened the first rule.
DES remained a sure and wide used encoding algorithm through the mid-1990s. By harnessing the ability of thousands of networked computers, the subsequent year, roll in the hay cut the secret writing time to twenty-two hours.
the website guarantees to crack DES keys, for a fee, in concerning twenty-six hours as of this writing. Crack. sh additionally offers free access to a rainbow table for proverbial plaintexts of 1122334455667788 which will come a DES key in twenty-five seconds or less.
There are way more secure algorithms available, cherish AES. very like an inexpensive baggage lock, DES will keep the contents safe from honest people, however, it won’t stop a determined thief.
Successors to DES
So, in 1997, customary and Technology|NIST|agency|federal agency|government agency|bureau|office|authority} proclaimed an initiative to decide on a successor to DES and undertook a five-year analysis method of fifteen encryption algorithms. In 2001, NIST selected the Rijndael cypher, and with some tweaks, it became the new AES. encryption Standard (FIPS 46-3) was formally withdrawn in could 2005.
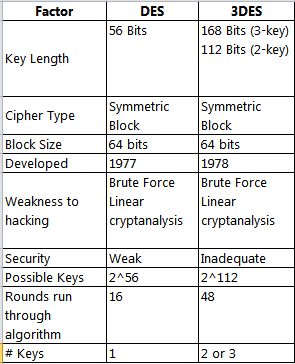
Triple DES (3DES), a variant of DES which will fritter away to 3 completely different keys for larger effective key length, has also been deprecated. However, because of the probability of a meet-in-the-middle attack, the effective security it provides is barely 112 bits. 3DES encoding is slower than plain DES.
How is DES used today?
As deprecated standards, each the DES and 3DES rules and key lengths may still be used. howeverever, users should settle for that there’s a security risk in victimization the deprecated algorithm and key length which the chance can increase over time.
DES isn’t any longer sure for encrypting sensitive data. Before it absolutely was deprecated and eventually disallowed, the quality was needed for U.S. government monetary transactions that used electronic funds transfer. It became the default encoding algorithm employed in financial services and different industries.
DES and TripleDES still be used in restricted ways:-
TripleDES office steerage for 3DES can modification to disallowed in 2023. At that point, the rule and key length won’t be used for scientific discipline protection. scientific discipline training. DES and its variants still be used these days for teaching concerning cryptography. The algorithms are well understood, and there’s a major body of analysis into each how effective DES will be and the way to effectively attack it. The technology remains employed in world to demonstrate the basics of digital cryptography, as well as the following:
Despite having reached the top of its helpful life, the arrival of knowledge encoding commonplace served to market the study of cryptography and also the development of recent encryption algorithms. till DES, cryptography was a dark art confined to military and government intelligence organizations.
The open nature of DES has meant academics, mathematicians and anyone curious about data security may study how the algorithm worked and take a look at to crack it. like any fashionable and difficult puzzle, a craze — or, during this case, a full trade — was born.
Conclusion
Cryptology has traditionally been a secretive science, so much so that it was only at the end of the 20th century that the principles on which the cryptanalysis of the Japanese and German cipher machines of World War II were based were declassified and released. What was different about the DES was that it was a totally public cryptographic algorithm. Every detail of its operations—enough to permit anyone who wished to program it on a microcomputer—was widely available in published form and on the Internet. The paradoxical result was that what was generally conceded to have been one of the best cryptographic systems in the history of cryptology was also the least secret.





