
Ethical hacking tools enable white hat hackers to better secure the web. And with over 47,000 users, Burp Suite is the world’s go-to web app hacking software.
- Introduction
- What is Hacking Tools
- Top Hacking Tools, Programs, And Software
- Conclusion
- Scans on all SQL Injection variants, XSS, and over 4,500 different vulnerabilities
- Detects over 1200 weaknesses withinside the WordPress heart, themes, and plugins
- Rapid & Scalable Crawling – crawls loads of hundreds of pages with out pause
- Integrates with famous internet utility firewalls and problem trackers to help with the SDLC
- Available each on-premises and withinside the cloud.
- An open-supply platform
- Support for numerous platforms
- Enables the simultaneous use of numerous computer systems in an unmarried machine.
- Utilization of quite a few interface paperwork withinside the identical structure
- It helps the established order of allotted cracking networks.
- Allows for immersive pausing/resuming
- Maintains classes and restores them
- Integrated benchmarking framework
- Thermal screen integrated
- Automatic output optimization is supported
- Complete device suites for time-reminiscence trade-offs, such as rainbow desk generation
- It is able to producing rainbow tables with each hash algorithm.
- Rainbow desk aid for each charset
- Rainbow tables are supported in each raw (.rt) and transportable report formats.
- Help for computation on multi-middle processors
- Runs on Microsoft Windows and Linux
- Rainbow desk report layout is universally supported on all supported working systems.
- User app for command line
- Graphical person experience
- GUI-primarily based totally and extraordinarily easy to use
- It functions a strong and green scanning engine.
- Suggestions for logging the login series
- Reporting in HTML and RTF
- It is one of the handiest hacking packages to be had because it scans over 25 one of a kind varieties of internet vulnerabilities.
- Detection of False Positives and Negatives
- It is Python and Ruby compatible.
- Extendable through plugins or modules are written in Python, Ruby, C#, or Visual Basic.NET
- Services that aren’t patched and misconfiguration
- Passwords which are too easy to guess – each default and famous
- Numerous tool flaws
- Open-supply software program
- Checks web website online servers and detects over 6400 in all likelihood dangerous CGIs or documents
- Checks repositories for out-of-date software program and version-particular problems
- Verifies plugins and incorrectly established directories
- Identifies packages and directories that aren’t stable
- Avoid detection through detection structures
- Conduct vulnerability assessments for safety vulnerabilities
- Carry out far flung assaults
- List hosts and networks
- Browser for packets
- A strong graphical consumer interface
- Comprehensive VoIP review
- Gzip documents are inspected and decompressed.
- Other seize document codecs which include Sniffer Pro, Tcpdump, Microsoft community control, Cisco Secure IDS IPlog, and others are supported.
INTRODUCTION
With the discovery of hacking software program, the sphere of moral hacking or penetration trying out has gone through a sea change. Several strategies for expediting the studies segment are being constructed on the moment.
Ethical hacking permits agencies to steady their facts and infrastructure greater effectively. Additionally, it’s far one of the simplest methods of improving an organization’s safety capabilities. Integrating moral hacking software programs into an organization’s protection sports is extraordinarily beneficial. Here is all you want to recognize approximately what software program is wanted for moral hacking.
HACKING TOOLS
A hacking device is a software program or carrier that aids withinside the hacking process. It can be used to steady a community or server from hackers proactively. Hacking is the planned alteration of a pc application or hardware in methods that violate the architectural limitations and style.
Hacking tools are programs that generally crack or break computer and network security measures. Hacking tools have different capabilities depending on the systems they have been designed to penetrate
Hacking gear are available in numerous kinds and are designed frequently to useful resource in hacking. Hacking gear are on occasion used to achieve unauthorized access to a pc to mount worms, spyware, malware, and Trojan horses. Hacking gear are applications and scripts that assist you discover and make the most vulnerabilities in working systems, internet services, servers, and networks. There are many such devices at the market. Users will speedy down load moral hacking software program. Several of them are open access, even though a few are proprietary.
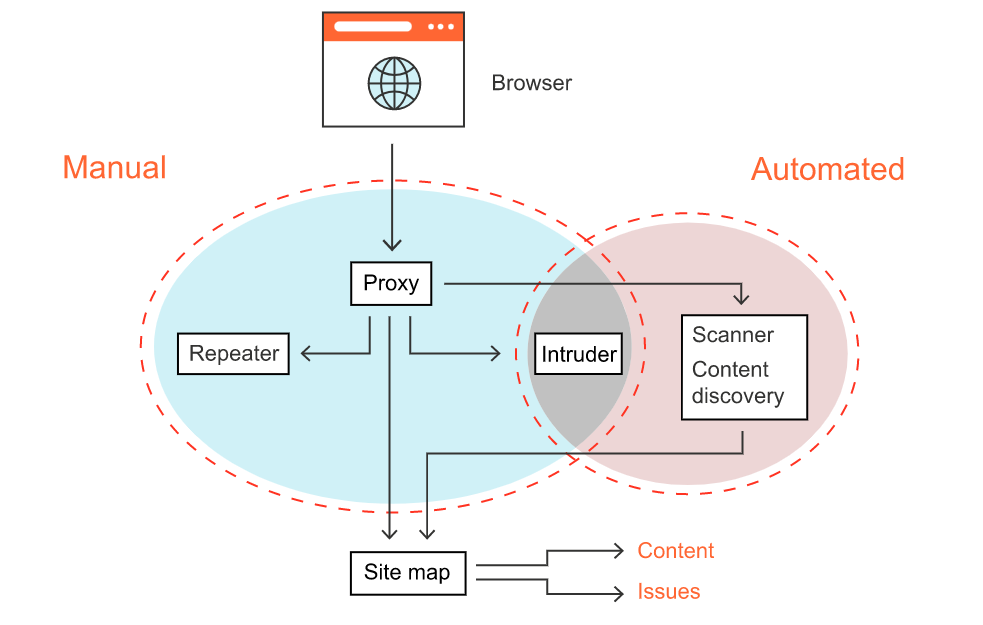
TOP HACKING TOOLS, PROGRAMS, AND SOFTWARE
Here is a hand-curated listing of the pinnacle moral hacking tools, along side a precis in their maximum not unusualplace functions.
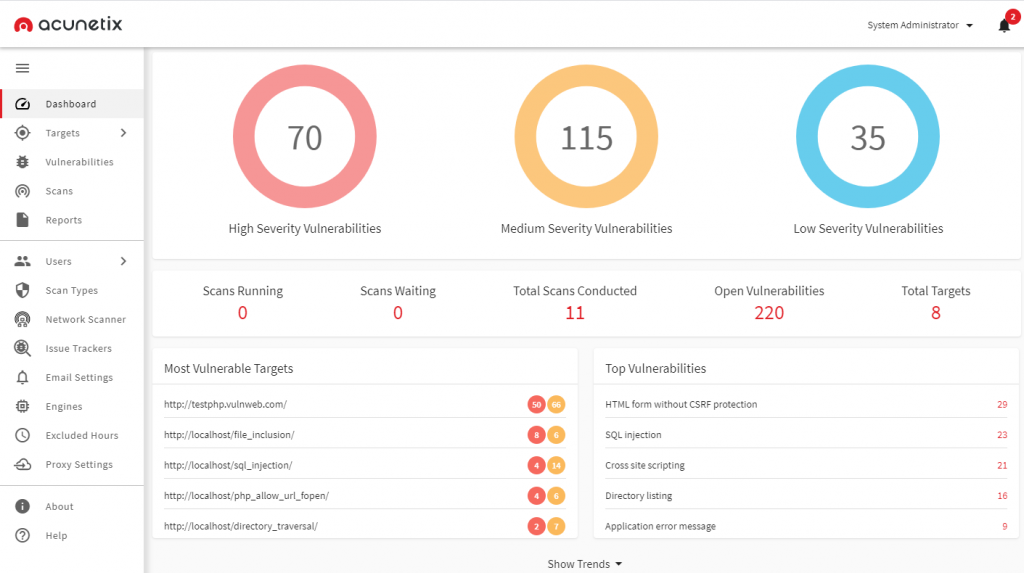
Acunetix
Acunetix is a totally self reliant moral hacking software program that takes on a hacker’s position to live one step beforehand of malicious intruders. The internet site safety scanner scans HTML5, JavaScript, and unmarried-web page apps with pinpoint accuracy. It is able to auditing sophisticated, authenticated internet packages and producing enforcement and control reviews on a huge spectrum of internet and community vulnerabilities.
WebInspect
WebInspect is a complicated hacking gadget safety studies device that allows moral hacking techniques to be performed. It is one of the most powerful hacker strategies to be had as it plays an intensive dynamic observe of complex community apps and services.
Allows for complicated conduct checking out of working internet apps to discover safety flaws.
Maintain strength of the test through quick getting access to pertinent information and statistics.
Management of Programs Centralized Advanced tools, including simultaneous move slowly monitoring, is to be had to even the maximum green safety testers.
Inform managers without problems approximately chance trends, enforcement control, and hazard control.
Hashcat
Hashcat is one of the maximum effective and dependable password cracking and moral hacking gadgets to be had. It will assist customers to get better-forgotten passwords, auditing password safety, or without a doubt figuring out what facts is blanketed in a hash.
RainbowCrack
RainbowCrack is a password-cracking and moral hacking utility this is regularly used for pc hacking. It makes use of rainbow tables to interrupt hashes. It accomplishes this through the usage of a time-reminiscence trade-off algorithm.

IronWASP
IronWASP is a unfastened and open-supply hacking device. It is a hazard evaluation in internet packages. It is meant to be modular, permitting customers to construct their personal safety scanners.
Nmap
Nmap is a community safety mapper able to locating offerings and hosts on a community and producing a community map. This app has many functions that resource in probing pc networks, host identity, and running machine detection. Due to the extensible nature of the script, it allows superior vulnerability identity and may even reply to community situations which includes congestion and latency even as scanning.
Nessus
Nessus is the following moral hacking platform at the list. Nessus is the maximum broadly used vulnerability scanner withinside the world, advanced through tenable community safety. It is absolutely loose and is more often than not encouraged for non-business use. This community weak spot detector without difficulty identifies essential flaws in each tool.
Nessus is able to figuring out the subsequent vulnerabilities:
Nikto
Nikto is an internet scanner that assessments and opinions numerous net servers for out of date applications, malicious CGIs or archives, and different problems. By amassing acquired cookies, it’s miles able to carrying out server-particular in addition to wellknown assessments and prints. It is a loose, open-supply software that scans 270 servers for version-particular problems and detects default packages and directories.
SQLMap
SQLMap is a Python-primarily based totally hacking software. This device assessments far flung hosts the usage of SQL injection. SQL injection is a way this is used to goal facts-pushed structures through exploiting a safety flaw. Thus, researchers will use SQLMap to simulate a SQL injection assault to decide whether or not the tool beneathneath research is insecure.
This device has loads of functions, which include hash identity and dictionary-primarily based totally password cracking. This demonstrates that the usage of actual phrases as passwords is dangerous and that it’s miles frequently ultimate to create a random alphanumeric string the usage of a password generator to assist steady the accounts.
Maltego
This is a facts series device. It can fast set up hyperlinks among telecellsmartphone numbers, e-mail addresses, businesses, individuals, and social media accounts, amongst different things. Additionally, you can use this device to take a look at interactions and hyperlinks among numerous infrastructures, which include DNS servers, directories, websites, area names, and IP addresses.
Needless to add, that is only a sampling of what it’s miles able to considering a number of its number one functions contain actual-time facts exchange, entity lists generation, and evaluation of as much as 10,000 entities in step with graph. Additionally, as is the case for maximum equipment at the market, this application runs on Windows, Linux, and macOS.
Metasploit
This is a Ruby-primarily based totally open-supply penetration trying out software program. It serves as a shared platform for trying out and designing code for safety vulnerabilities. One can damage into their very own community to evaluate safety threats and decide which insects may be resolved first. Additionally, it’s miles one of the most effective felony hacking strategies that amateur programmers use to hone their expertise.
The platform consists of safety sources for appearing the subsequent tasks:
Wireshark
Wireshark is a software program software this is loose, open-supply and allows actual-time community site visitors evaluation. Wireshark is famous for recognizing vulnerability problems in any community, in addition to its usefulness in resolving wellknown networking problems because of its sniffing technology. When sniffing the community, you could seize and interpret facts in a human-readable format, which permits figuring out feasible problems (which includes low latency), risks, and insects simpler.
Analyses are stored for offline review.Ettercap
Ettercap is a platform for felony hacking. It lets in each lively and passive dissection and presents community and host assessment functionality. It is one of the most powerful hacker strategies because it permits each lively and passive protocol dissection.
ARP poisoning is a characteristic that permits sniffing on a switched LAN among hosts. Characters can be inserted right into a server or a database while the hyperlink remains lively. Ettercap is able to sniffing a full-duplex SSH hyperlink.
It is one of the great hacking software program to be had because it permits sniffing of HTTP SSL-encrypted facts despite the fact that the hyperlink is set up thru a proxy.
Savvius
It is one of the greatest moral hacking software program to be had. Omnipeek’s deep visibility removes performance issues and minimizes safety danger. With Savvius packet intelligence, it may come across community issues extra speedy and accurately.Network forensics application this is each effective and easy to apply
Savvius automates the gathering of community facts essential to analyze safety warnings easily. Solutions primarily based totally on software program and included appliances
L0phtCrack
L0phtCrack 6 is a treasured approach for auditing and recuperating passwords. It locates and evaluates login vulnerability on nearby computer systems and networks.
Support for numerous cores and GPUs contributes to hardware optimization.

IKECrack
IKECrack is a unfastened and open-supply platform for cracking authentication. Such unfastened hacking equipment are supposed for the usage of brute-pressure and dictionary attacks. It is one of the greatest hacker techniques to be had, and it permits the execution of cryptography sports. IKECrack is an application that permits the execution of cryptographic operations.
The starting up patron sends an unencrypted packet to the gateway/responder with a suggestion for encryption solutions, the DH public key, a random number, and an ID.
It is one of the maximum a success hacking structures this is extensively reachable for private and commercial use. As a result, it’s far an amazing desire for customers looking for an answer for Cryptography programs.
CONCLUSION
Professional and educated moral hackers who’ve taken instructions along with the Master Certificate In Cyber Security Course (Red Team) to assist fight fraudulent crimes and identification robbery are continually in demand. End customers have traditionally turn out to be the weakest connection in cybercriminals’ chain of command, letting them breach even the maximum superior defences. Several huge corporations have currently introduced giant safety breaches. Ethical hacking equipment help organizations in figuring out ability era flaws and stopping facts breaches.





