
- Overview of the MD5 Algorithm
- Structure and Working of MD5
- The Hash Function in MD5
- MD5 Vulnerabilities and Security Concerns
- MD5 in Digital Signatures and Certificates
- MD5 vs SHA-1 and SHA-256
- Applications of MD5 in Data Integrity
- Conclusion
Overview of the MD5 Algorithm
The MD5 (Message Digest Algorithm 5) is a widely used cryptographic hash function that produces 128-bit values (32 hexadecimal characters). Designed by Ronald Rivest in 1991, MD5 was originally intended to be a secure algorithm for generating a fixed-length hash for variable-length inputs, such as files or messages. It became widely adopted for tasks like file integrity checking and digital signatures, among other cryptographic applications in Cybersecurity Training Courses . However, over time, vulnerabilities in MD5 became apparent, leading to its deprecation in favor of more secure algorithms like SHA-256. Despite its weaknesses, MD5 is still used in some legacy systems due to its efficiency and ease of implementation, though its use in security-sensitive applications is now generally discouraged.
Structure and Working of MD5
MD5 processes input data in blocks of 512 bits (64 bytes) at a time. The algorithm consists of four main steps: padding, initialization, processing, and output generation. Here’s a breakdown of the process:
- Padding: The input message is padded to ensure its length is 64 bits short of a multiple of 512 bits. Padding is done by appending a single “1” bit to the message, followed by enough “0” bits to make the total length 64 bits less than a multiple of 512. The length of the original message is then appended to the end of the padded message.
- Initialization: MD5 initializes four 32-bit variables (A, B, C, D) to specific constant values. These variables act as the initial hash values, and the RSA Algorithm uses them to process the data in the subsequent steps.
- Processing: The padded message is processed in 512-bit blocks. Each block is divided into sixteen 32-bit words. The main loop of MD5 applies a series of non-linear functions, bitwise operations, and additions to mix the data. These operations use the initialized hash values (A, B, C, D) and constants derived from the sine function.
- Output Generation: After all message blocks are processed, the final hash value is formed by concatenating the values of A, B, C, and D. This hash value is the MD5 message digest.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
The Hash Function in MD5
The core of MD5 is its hash function, which takes an input (or message) of arbitrary length and maps it to a fixed-length output, typically represented as a 128-bit number. MD5 uses a series of bitwise operations, modular additions, and non-linear functions (such as the bitwise AND, OR, XOR, and rotation operations) to generate a unique hash value for each unique input. MD5 operates in a Merkle–Damgård construction, which ensures that even a small change in the input message will result in a drastically different output hash.
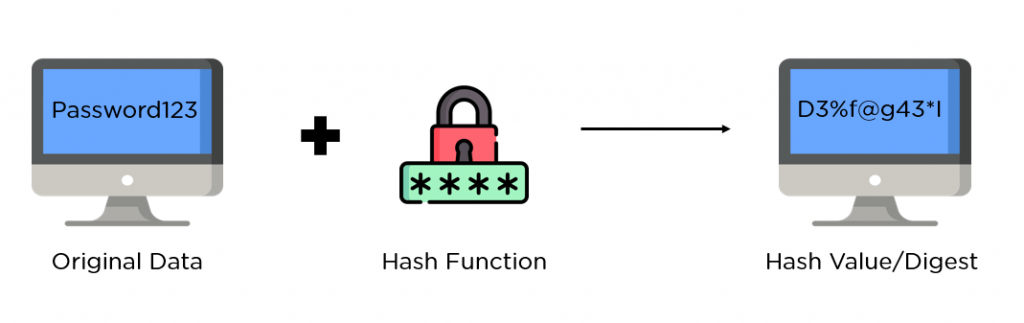
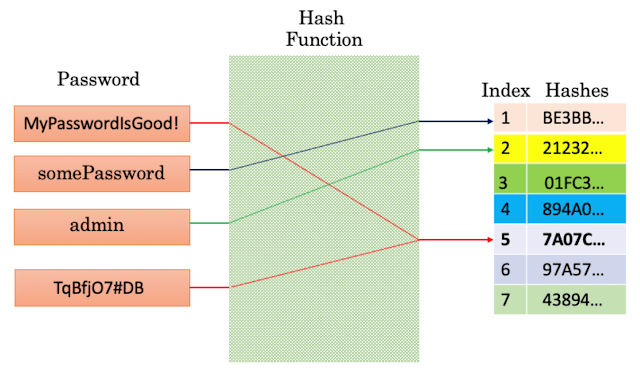
This property is known as the avalanche effect, where even a single-bit change in the input causes a significant change in the hash value. MD5 is no longer considered secure despite its widespread use due to its susceptibility to collisions (two different inputs producing the same hash). MD5 Vulnerability Scanning and Security Concerns 0Over the years, various vulnerabilities in MD5 have been discovered, particularly in collision resistance. A collision occurs when two distinct inputs produce the same hash output, compromising the algorithm’s integrity. This is a critical issue for security-sensitive applications, such as digital signatures, file integrity checking, and certificate generation, where the uniqueness of the hash is essential.
To learn about different Cybersecurity techniques, sign up for our Cyber Security Online Training!
MD5 Vulnerabilities and Security Concerns
- Collision Vulnerabilities: In 2004, researchers demonstrated that MD5 is vulnerable to collision attacks, where two different inputs can generate the same hash. This is particularly dangerous because it allows an attacker to substitute a malicious file or message for a legitimate one while maintaining the same hash value, bypassing integrity checks.
- Preimage and Second Preimage Attacks: While preimage attacks (finding an input that hashes to a specific hash) and second preimage attacks (finding a different input that produces the same hash as a given input) are still computationally difficult for MD5, the vulnerabilities in collision resistance make MD5 less secure for modern Cryptographic Techniques applications.
- Speed of MD5: MD5 is fast and efficient at producing hash values, which was originally a benefit. However, this speed also makes it easier for attackers to perform brute-force or dictionary attacks to find a matching hash for a message. Due to these vulnerabilities, MD5 is considered insecure for cryptographic purposes, especially in applications that require integrity verification or digital signatures.
MD5 in Digital Signatures and Certificates
MD5 has historically been used in digital signatures and certificates. A digital signature typically involves creating a hash of a message and then encrypting that hash with a private key to generate a signature. The recipient can then verify the signature by decrypting it using the sender’s public key and comparing it with the hash of the original message. However, due to MD5’s vulnerability to collision attacks, it is no longer recommended to use MD5 for digital signatures or certificates in Cybersecurity Training Courses . An attacker could forge a message with the same MD5 hash as a legitimate message, leading to fraudulent signatures. As a result, modern signature algorithms now use more secure hash functions like SHA-256. In the context of SSL/TLS certificates, MD5-based hashing algorithms (such as in signing certificates) have also been deprecated in favor of algorithms like SHA-256 to prevent possible certificate forgery.
Want to Take the Lead in Cyber Security ? Enroll Cybersecurity Expert Masters Program Training Course.
MD5 vs SHA-1 and SHA-256
SHA-1 and SHA-256 are cryptographic hash functions considered more secure than MD5.
- SHA-1: The NSA designed SHA-1 (Secure Hash Algorithm 1), which is widely used in security protocols such as SSL/TLS and digital signatures. Like MD5, SHA-1 has been found to have vulnerabilities to collision attacks, but it is considered more secure than MD5. However, SHA-1 is now also deprecated for many Database Security applications, and its use is being phased out in favor of more secure algorithms like SHA-256.
- SHA-256: SHA-256 (part of the SHA-2 family) is considered much more secure than MD5 and SHA-1. It produces a 256-bit hash value, making it resistant to collision attacks. SHA-256 is widely used in modern security protocols and is recommended for cryptographic applications that require strong hash functions.While MD5 and SHA-1 have collision vulnerabilities, SHA-256 offers better security by providing a larger hash size and more robust attack resistance.
Applications of MD5 in Data Integrity
Despite its vulnerabilities, MD5 is still widely used in non-security-critical applications where the primary goal is data integrity rather than cryptographic security. Some common applications of MD5 include:
Preparing for a job Interview? Check out our blog on Cybersecurity Interview Questions and Answers!
- Checksums in Software Distribution: When software is distributed via download, MD5 checksums are often provided to verify that the downloaded file matches the original file and has not been tampered with. However, due to MD5’s collision vulnerabilities, more secure hash functions like SHA-256 are being used instead of MD5 for these purposes.
- Fingerprinting and Hash Tables: MD5 is also used in hash tables and data indexing, where the hash value serves as a unique identifier for data. While MD5 is fast, its Web Security issues make it less suitable for applications requiring high security.
- Deduplication: In data storage and file systems, MD5 hashes are used for deduplication. This process involves storing only a single copy of a file or block of data, identified by its hash. While MD5 may still be used in some systems, more secure hashing algorithms are recommended for critical systems.
Conclusion
While MD5 was once a cornerstone of cryptographic functions, its vulnerabilities to collision attacks have rendered it unsuitable for security-sensitive applications today. Its use in data integrity checking and legacy systems continues, but for critical applications such as digital signatures in Cybersecurity Training , certificates, and data security, stronger hash functions like SHA-256 are recommended. Understanding MD5’s limitations and weaknesses is essential for ensuring that cryptographic practices evolve to meet modern security challenges.





