
- Introduction to Client-Server Architecture
- What is Client-Server Architecture?
- Client-server architecture example
- Components of Client-Server Architecture
- Advantages and Disadvantages of Client-Server Architecture
- How does Client-Server Architecture work?
- Types of Client-Server Architecture
- Conclusion
Client-server architecture is a network design model where client devices request services, and server systems provide them. Clients, such as computers, smartphones, or applications, initiate requests, while servers process these requests and send back responses.This model enhances efficiency, scalability, and security by centralizing resources and data management. Common examples include web applications, email systems, and database management. Cyber Security Training Courses are crucial in helping employees understand the potential vulnerabilities in these systems and how to safeguard sensitive data from evolving cyber threats. The architecture can be categorized into two-tier, three-tier, and multi-tier structures, depending on complexity and functionality. It is widely used in enterprise systems, cloud computing, and online services, ensuring seamless interaction between users and backend resources over networks.
To Explore Client-Server Architecture in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Introduction to Client-Server Architecture
Client-Server Architecture is a computing model that divides tasks between service providers (servers) and service requesters (clients). The server hosts, manages, and delivers resources or services, while the client requests and consumes them over a network. Kali Linux can be used by security professionals to test and assess the server-client setup for vulnerabilities, ensuring that both the server and the client are properly secured against potential attacks. This architecture enhances efficiency, scalability, and security, making it a fundamental model for modern applications, including web services, databases, and cloud computing. It operates on various protocols like HTTP, FTP, and SMTP, ensuring smooth communication. Common examples include web browsers accessing websites and email clients retrieving messages. Client-Server Architecture plays a crucial role in distributed computing, enabling seamless interaction between multiple devices.
What is Client-Server Architecture?
Before we provide an explanation for the customer-server structure and also you begin analyzing phrases consisting of servers, service, community, records, and documents and begin feeling crushed with jargon, allow us to first recognize this structure in layperson’s terms. The belief in customer-server structure may be understood through the analogy of ordering a pizza for delivery. You name the shop to reserve a pizza and a person alternatives the name, takes your order, and offers it. Simple, right? Yes, this analogy quite a lot solutions the essential precept of customer-server structure.
Client-Server Architecture example
Here are a number of the client-server model structure examples from our day-to-day life. Hope it lets you recognize the idea better. However, it’s important to be aware of potential risks like Spyware, which can secretly monitor your activities on client devices, compromising your privacy and security within such systems.
- Mail servers : Email servers are to be used for sending and receiving emails. There are distinct software programs that allow e-mail handling.
- File servers: File servers act as a centralized vicinity for documents. One of the each day existence examples to recognize is the documents that we shop in Google Docs. The cloud offerings for Microsoft Office and Google Docs may be accessed out of your devices; the documents that you store out of your pc may be accessed out of your phone. So, the centrally saved documents may be accessed via way of means of a couple of users.
- Web servers : Web servers are high-overall performance computer systems that host distinct websites. The server-facet information is asked via way of means of the consumer through high-velocity internet. Simply put, elements are involved :
- A server is the only one who gives asked offerings.
- Clients are those who request offerings.
- Client-server structure is a computing version wherein the server hosts, offers, and manages the maximum of the assets and offerings asked through the customer. The customer-server structure or version has different structures linked over a community in which assets are shared with most of the one-of-a-kind computers.
- Typically, the customer-server structure is organized in a manner that customers are regularly located at workstations or on private computers, even as servers are placed someplace else in the community, generally on greater effective machines. Such a version is mainly useful whilst the customers and server carry out habitual tasks. For example, in health center records processing, a customer pc may be busy walking a utility software for getting into affected person records, meanwhile, the server pc may be walking any other software to fetch and manipulate the database wherein the records are completely stored.
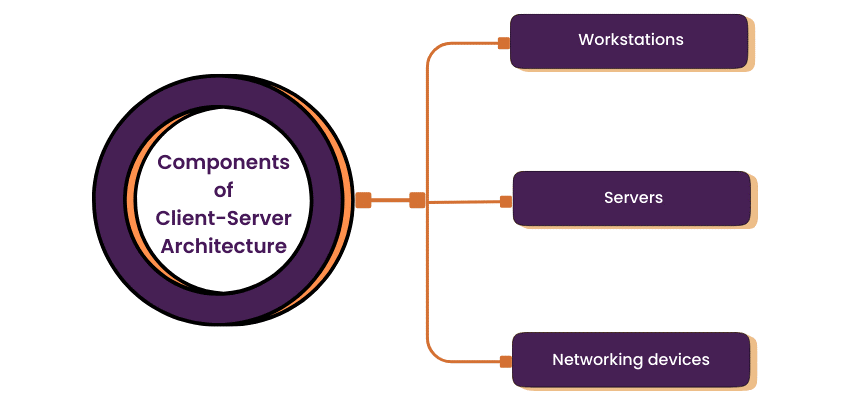
- Workstations: Workstations are also referred to as client computers. A server requests facts from the workstation and performs numerous functions as an essential repository of files, programs, databases, and control policies. Workstations are governed by server-defined policies. Cyber Security Training Courses are important for educating employees on these policies, ensuring they understand the security measures in place to protect both the workstations and the server from potential threats.
- Servers: Servers are described as fast-processing gadgets that act as centralized repositories of community documents, programs, databases, and policies. Servers have a massive garage area and sturdy reminiscence to cope with more than one request, coming near concurrently from numerous workstations. Servers can carry out many roles, including mail server, database server, record server, and area controller, in a customer-server structure at the same time.
- Networking gadgets: Now that we recognize approximately the jobs that workstations and servers play, allow us to find out about what connects them, networking gadgets. Many networking gadgets are used to carry out numerous operations throughout the community. For example, a hub is used for connecting a server to numerous workstations. Repeaters are used to efficiently switch records among gadgets. Bridges are used to isolate community segmentation.
- Centralized Control: The server acts as a principal factor for coping with resources, records, and security, making management simpler and extra efficient.
- Data Security: A centralized records garage at the server permits for higher implementation of safety features like getting entry to manage and backup policies.
- Scalability: Additional customers may be introduced to the community without considerably affecting the performance, supplied the server has enough capacity.
- Ease of Maintenance: Updates, upgrades, and troubleshooting may be carried out at the server while not having to make adjustments on character purchaser systems. Disadvantages of Client-Server Architecture
- Single Point of Failure: If the server fails, the whole network may be disrupted, affecting all clients depending on the server. Additionally, a Watering Hole Attack can target the server, compromising it to infect users when they access the system, further amplifying the potential impact of server failure or security breaches.
- Cost: Setting up and retaining an effective server, alongside licensing and software program requirements, may be expensive.
- Complexity: Configuring and coping with the server and community infrastructure calls for professional IT personnel, growing operational complexity.
- Scalability Limitations: While scalable to an extent, a server might also additionally come to be a bottleneck if too many customers are introduced without upgrading its hardware or software program.
- 1-Tier Client-Server Architecture: The structure of this particular customer-server class includes diverse settings, together with configuration settings and advertising and marketing common sense, inside an unmarried device. Although the huge variety of offerings supplied with the aid of using the 1-tier structure establishes it as a reliable useful resource, coping with such a structure proves challenging. This issue in the main arises from the variety of facts, frequently main to duplicated efforts. The 1-tier structure accommodates a couple of layers, which include the presentation layer, enterprise layer, and facts layer, that are unified through a specialized software program package. The facts dwelling inside this sediment are commonly saved both in nearby structures or on a shared drive.
- 2-Tier Client-Server Architecture: The high-quality surroundings are possessed with the aid of using this structure, wherein the customer`s facet shops the person interface and the server homes the database, even as both the customer`s facet or the server`s facet manages the database common sense and enterprise common sense. The 2-tier structure outpaces the 1-tier structure because of its absence of intermediaries between the client and server. However, this direct communication also makes it more vulnerable to threats like Cryptojacking, where attackers exploit the server or client to use its processing power for mining cryptocurrency without consent. Proper security measures are essential to prevent such malicious activities. Its number one utility is to do away with customer confusion, and an example of its reputation lies inside the online price price tag reservation system.
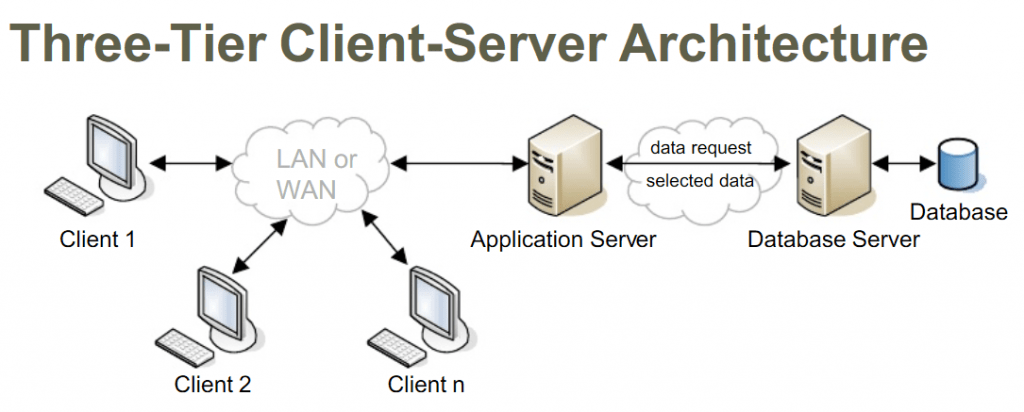
- 3-Tier Client-Server Architecture: If the purchaser locations a request to fetch precise facts from the server, the request will first be obtained via way of means of middleware. It will then be dispatched to the server for addition action. The equal sample might be accompanied whilst the server sends a reaction to the purchaser. The framework of a 3-tier structure is categorized into 3 fundamental layers, presentation layer, software layer, and database tier. All 3 layers are managed at exclusive ends. While the presentation layer is managed on the purchaser`s device, the middleware, and the server cope with the software layer and the database tier respectively. Due to the presence of a 3rd layer that gives records management, a 3-tier structure is extra secure, has an invisible database structure, and gives records integrity.
- N-tier structure: The n-tier structure is likewise known as a multi-tier structure. It is the scaled shape of the opposite 3 sorts of structure. This structure has a provision for finding every characteristic as a remoted layer that consists of presentation, software processing, and control of records functionalities.
To Earn Your Client-Server architecture Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Components of Client-Server architecture
Essentially, 3 additives are required to make customer-server structure paintings. The 3 additives are workstations, servers, and networking gadgets. Let us, now, talk about them in detail:
Advantages and Disadvantages of Client-Server Architecture
Advantages of Client-Server ArchitectureAre You Considering Pursuing a Master’s Degree in Cybersecurity? Enroll in the Cyber Security Expert Masters Program Training Course Today!
How does Client-Server Architecture work?
We have understood that the customer-server structure is made from elements, one that offers offerings and the opposite that consumes the one offering. To get a clearer photograph of the process, allow us to find out how the browser interacts with the server. The user enters the uniform resource locator (URL) of the website or document, and the browser sends a request to the domain name system. To secure this process and protect sensitive data, using a Virtual Private Network encrypts the connection, ensuring that the data transferred between the browser and the website is secure from potential eavesdropping or interception. DNS server is answerable for looking and retrieving the IP cope with related to an internet server after which starting up movements the usage of that IP cope with. After the DNS server responds, the browser sends over an HTTP or HTTPS request to the internet server`s IP, which becomes supplied with the aid of using the DNS server. Following the request, the server proceeds to transmit the vital internet site documents required. Ultimately, the documents are processed with the aid of using the browser, and the internet site is sooner or later offered for viewing.
Types of Client-Server Architecture
The capability of the Client-Server structure is in diverse tiers.
Are You Preparing for Cyber Security Jobs? Check Out ACTE’s Cyber Security Interview Questions and Answers to Boost Your Preparation!
Conclusion
This weblog explains how individuals, computers, or groups actively set up strategic alliances via way of means of speaking and replacing records, that is called networking. Within the networking model, the client-server structure allows multiple clients to access a shared database via a graphical user interface. Cyber Security Training Courses are essential in educating users on how to securely interact with these systems, ensuring proper access controls, data protection, and awareness of potential security risks when accessing shared resources. Networking empowers groups of all sizes to scale and digitize their businesses, sell their products, and decorate their enterprise understanding via way of means of staying up to date on information and events.





