
A security architect takes on a vital role in an IT department. You’ll design systems, manage employees and help evolve the security needs of the organization. You can rise to this senior-level position once you have garnered extensive experience and credentials in the computer security field.
RESPONSIBILITIES
As a security architect, you’ll be charged with designing security systems to thwart malware, hacker intrusions and Denial of Service attacks. Once the system is in place, you will need to test for any vulnerabilities and audit the entire system. To fully test your system, you may need to hire an outside consultant who can run a thorough penetration test to ensure that the system is secure from outside attacks.

On the managerial side, a security architect may work with other managers to implement employee protocols to maintain system integrity. These protocols are especially pertinent in high-level security situations such as work as a defense contractor. You might implement a policy that states that no workstation should be unattended and that all staff undergo a physical screening upon entering and exiting the department. While seemingly extreme, such measures may be necessary when you are handling data that is vital to national security. As a manager, you will need to implement training for your employees, conduct interviews for new hires, and even let people go when it is necessary.
When new standards and procedures are rolled out, it will fall to you to instruct your staff on these matters. As a management-level employee, you will likely need to stay abreast of current trends in the security field. You will need to travel to conferences and stay abreast of industry publications. Some find it gratifying to publish articles about new security software or best practices for designing a security architecture.
When you are up-to-date on trends in the industry, you will be equipped to assess when and how to upgrade your system. You will then need to oversee the roll out of new software packages, ensuring the integrity of the overall network while you do installations and uninstalls. After such upgrades, you can then perform a new audit to catch any software conflicts or glitches.
SECURITY ARCHITECT VS. SECURITY AUDITOR
Security architects and auditors usually work in the same departments, but the primary distinction between the two is that the architect is often the auditor’s manager. The architect is the one who designs and oversees the roll out of a system, and often the auditor is on the team of staffers who physically implement that roll out.
Security Architect: The architect is the one who designs and oversees the roll out of a system.
Security Auditor: The auditor is on the team of staffers who physically implement that roll out.
Once the architect’s system is in place, it falls to the auditor to test it and ensure that it is sound. He or she will run tests and scrutinize the results to see if there are any conflicts between various software packages, and determine how to best resolve any conflicts. The architect will review the auditor’s findings and then the two will discuss how to proceed.
Unlike the auditor, an architect will have other managerial duties such as reviewing costs and budgets. You will need to ensure that new software costs are within the budget and that any outside consultants can be paid in a timely fashion. You will often need to be prepared to defend any new expenses to the CEO or CISO of the company. If you are a consultant, it will be vital to discuss budgetary overages with the client so that the firm will be sure to receive payment.
POSSIBLE CAREER PATHS
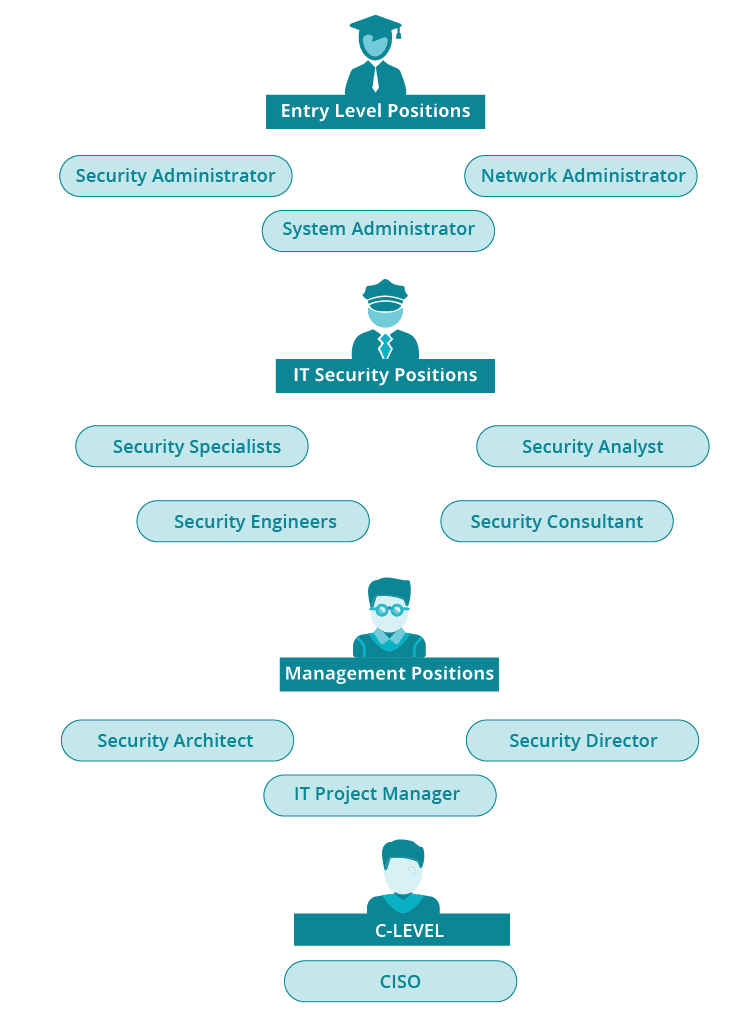
The road to becoming a security architect likely begins with a bachelor’s degree and proceeds through two tiers in the IT world. If you are interested in pursuing a security career into the management level, you will need to consider at least a graduate-level certificate in computer security, as well as any certificates from industry organizations. This graphic shows the various tiers in your profession:
SIMILAR JOBS
The IT field is full of differing job titles that appear to be very similar jobs. When you are pursuing a position as a security architect, make sure to read and understand the job description and duties so that you are assured that you are applying to the right position. As a security architect, you may be called upon to act as any of the following roles:
- Information Technology Architect
- Information Systems Security Architect
- Enterprise Information Security Architect
SALARIES

ANNUAL MEDIAN SALARY OF $101,210
Security Architect
Computer security is a field that has a high demand for qualified managers, including security and network architects. With such high demand comes high salaries and your years of hard work and service will pay off with a median salary of $101,210 a year, according to the Bureau of Labor Statistics and the job growth for the field is projected at 6 percent through 2026, which is significantly faster than average.
JOB REQUIREMENTS
Most security professionals will begin their career with a bachelor’s degree. While it is preferred that the degree be earned in computer science, information technology or cyber security, you can start with a degree in another field. However, to rise to the level of security architect, you likely need a master’s degree in cyber security or computer science with a security focus. You will need to be knowledgeable in the following topics:
- Windows, Unix and Linux operating systems
- Risk management and assessment procedures
- Security attack pathologies
- Cyber law and ethics
- Network security and architecture
- Wired and wireless security
- Enterprise and security architecture




