
- Introduction to Access Control Lists
- Types of Access Control Lists
- Implementing ACL on Network Devices
- Benefits of Using ACLs in Networking
- Common ACL Configuration Commands
- Troubleshooting and Best Practices for ACLs
- Conclusion
In most cases, ACLs are implemented on routers, firewalls, or switches, and they function by examining each packet’s header and determining whether to permit or deny the packet based on the specified conditions. Cybersecurity Training Courses are one of the fundamental building blocks of network security, traffic filtering, and traffic management.
To become a certified cyber security, have a look at our Cyber Security Online Training .
Introduction to Access Control Lists (ACLs)
Access Control Lists (ACLs) are used in networking to define the rules that control incoming or outgoing traffic on a network device. They are essentially lists of regulations applied to interfaces, controlling the flow of packets based on defined conditions such as IP address, subnet, and protocol type. ACLs are primarily used to improve network security, prevent unauthorized access, and prioritize network traffic by specifying which users or systems are allowed or denied access to certain resources.Additionally, ACLs can be used to prioritize traffic, ensuring critical applications or services receive the necessary bandwidth and performance. By defining explicit access rights, ACLs help to minimize potential attack vectors, preventing unauthorized access and reducing the risk of Network Topology . ACLs can be applied to both inbound and outbound traffic, giving administrators full control over data flow in both directions. With proper configuration, ACLs contribute to the overall security posture of an organization’s network, preventing unwanted access, mitigating threats, and optimizing resource utilization. They also provide audit trails that help with network monitoring and troubleshooting. Ultimately, ACLs are a foundational tool in maintaining the integrity, confidentiality, and availability of network systems.
Types of Access Control Lists
There are primarily two types of ACLs: Standard ACLs and Extended ACLs. Each serves a different purpose and has varying levels of granularity when it comes to filtering traffic.
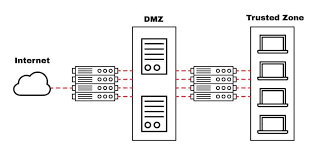
- Standard ACLs: Standard ACLs filter traffic based only on the source IP address. They do not consider the destination Address Resolution Protocol , protocol type, or port numbers. The rules in a standard ACL are simple: they either allow or deny traffic from a specified source. Standard ACLs are numbered 1 to 99 (in most network devices like Cisco routers). For example, an ACL rule could allow or deny all traffic from a certain source IP address, but it would not be able to specify conditions for destination addresses or services.
- Extended ACLs: Extended ACLs are more powerful and flexible. They can filter traffic based on the source IP address, destination IP address, protocol types (such as TCP, UDP, or ICMP), port numbers, and more. This allows for more precise control over traffic flow and security. Extended ACLs are typically numbered from 100 to 199. For instance, an extended ACL could be used to deny traffic from a certain source IP to a specific destination IP on a certain port, providing a finer level of security control.
- #Router(config)# access-list 10 deny 192.168.1.0 0.0.0.255
- #Router(config)# access-list 10 permit any
- #Router(config) # interface g0/1
- #Router(config-if)# ip access-group 10
- Enhanced Security: ACLs help in filtering unwanted or unauthorized traffic. Enhanced Security ACLs prevent unauthorized devices from accessing sensitive network resources by specifying which traffic is allowed or denied.
- Traffic Management: ACLs can prioritize traffic by allowing certain packets while denying others. For instance, an ACL can prioritize VoIP traffic while restricting non-essential services in Cybersecurity Training Courses .
- Improved Network Performance: ACLs can help reduce congestion by limiting unnecessary traffic. This ensures that only the required traffic reaches critical network resources.
- Access Control: ACLs provide granular control over who can access specific resources on the network, allowing organizations to control access based on IP addresses, users, or applications.
- Monitoring and Auditing: ACLs enable network administrators to track access attempts and detect potential security breaches or misuse of network resources by monitoring the logs generated by ACL rules.
- Creating an ACL:
- To create a standard ACL: # access-list [ACL Number] [permit/deny] [source IP] [wildcard mask]
- To create an extended ACL: # access-list [ACL Number] [permit/deny] [protocol] [source IP] [wildcard mask] [destination IP] [wildcard mask] [port]
- Applying the ACL to an Interface:
- To apply the ACL to an interface (inbound or outbound): # interface [interface name]
- To create an extended ACL: #ip access-group [ACL Number] [in/out]
- Viewing the ACL Configuration:
- To view the configured ACL:show access-lists
- Removing an ACL:
- To delete an ACL:No access-list [ACL Number]
- Editing ACL Rules:
- ACL rules cannot be directly modified. If an existing rule needs to be changed, it must be deleted and recreated with the new configuration.
- Implicit Deny Rule: ACLs include an implicit deny rule at the end. A packet will be automatically rejected if it does not match the permit or deny rules. This behavior should always be considered while creating ACLs to avoid unintended access denial.
- Order of Rules: ACLs process rules in a sequential manner. If a packet matches an earlier rule, no further rules are processed. Therefore, the order in which rules are configured is critical for the correct operation of ACLs.
- Testing ACLs: After configuring ACLs, Network Penetration Testing and verifying them is important to ensure they work as expected. Use commands like ping, traceroute, and show access lists to test and troubleshoot ACLs.
- Use of Comments: For better documentation and clarity, it is a good practice to include comments when creating ACLs to explain the purpose of each rule. In Cisco devices, comments can be added using a remark.
- Minimize ACL Complexity: Keeping ACLs simple and organized is essential. Overly complex ACLs can be hard to maintain and troubleshoot. Always try to structure the rules logically and avoid redundant entries.
- ACL Logging: For troubleshooting purposes, you can enable logging for ACL hits, which helps track how packets are being filtered. The logging option can be added to specific deny rules to log traffic.
- Example:#access-list 101 deny ip any 192.168.1.0 0.0.0.255 log.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Implementing ACL on Network Devices
ACLs are implemented on network devices, most commonly on routers and firewalls. The implementation involves the following basic steps Create the ACL: Define the ACL rules that specify the conditions for allowing or denying traffic. The rules can be based on IP addresses, Internet Protocol Address, ports, etc. Apply the ACL to an Interface: Once the ACL is created, it must be applied to the appropriate network interface on a router or switch. The ACL can be applied either inbound or outbound Inbound ACL: Filters traffic coming into the device. Outbound ACL: Filters traffic leaving the device. Configure ACL on Device: The network device will inspect the traffic against the defined rules after creating and applying the ACL to an interface. The configuration can be done using command-line interface (CLI) commands.
Benefits of Using ACLs in Networking
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Common ACL Configuration Commands
Configuring ACLs generally involves the following steps and commands on network devices like routers and switches
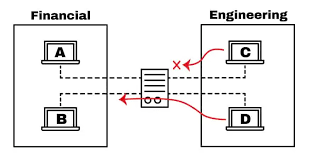
Troubleshooting and Best Practices for ACLs
Preparing for Cyber Security job interviews? Check out our Cyber Security Interview Questions and Answers now!
Conclusion
Access Control Lists (ACLs) are fundamental tools used in network security to define which users or devices can access specific network resources and what actions they are allowed to perform. ACLs operate by filtering traffic based on rules such as source IP address, destination IP address, protocols, and ports, providing a granular approach to security. There are two main types of ACLs: standard ACLs, which filter traffic based solely on source IP address, and extended ACLs, which allow for more detailed filtering based on additional criteria such as protocol type and port numbers. Configuring ACLs requires careful planning to ensure that the rules are both effective and not overly restrictive, which could inadvertently block legitimate traffic. Network administrators must also understand the priority of ACL rules, as the first matching rule determines whether traffic is allowed or denied in Cybersecurity Training . Proper ACL configuration can significantly improve a network’s security by limiting unauthorized access and preventing malicious activities. Additionally, ACLs can enhance network performance by controlling unnecessary traffic and reducing congestion. However, ACLs must be regularly reviewed and updated to adapt to changes in the network environment and evolving security threats. By following best practices, such as applying the principle of least privilege and testing ACL rules before deployment, administrators can effectively safeguard their network while maintaining optimal performance. Ultimately, well-implemented ACLs form a critical layer of defense in a comprehensive network security strategy.





