
- Introduction to Intrusion Prevention
- How IPS Differs from IDS
- Types of Intrusion Prevention Systems
- Network-based vs Host-based IPS
- Signature-based Detection
- Anomaly-based Detection
- Inline Mode Functionality
- Common IPS Tools and Vendors
- Deployment Strategies
- Integration with Firewalls and SIEM
- Role in Modern Cybersecurity
- Conclusion
Introduction to Intrusion Prevention System (IPS)
An Intrusion Prevention System (IPS) is a network security technology that actively monitors, analyzes, and takes action to prevent modern cyber security threats in real time. Cyber Security Training, it’s important to understand that unlike passive detection systems, an IPS is designed to not only identify malicious activity but also to take immediate corrective action to prevent potential breaches. such as blocking traffic or resetting connections. The primary goal of an host based ips software is to protect networks and systems from exploitation by known and unknown threats by inspecting incoming and outgoing data packets.As cyber threats continue to evolve, IPS has become a vital component of comprehensive security strategies across enterprises.
How IPS Differs from IDS
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are often mentioned together, but they have distinct functionalities.
- An IDS is a monitoring tool that alerts administrators to potential threats based on traffic patterns and signatures.
- However, As covered in Certified Cloud Security Professional (CCSP) training, an IDS only monitors and alerts but does not take action to block or prevent threats. In contrast, an IPS sits directly in the path of network traffic and is capable of taking immediate action How IPS Differs from IDS
- IPS systems can drop malicious packets,Vendors block IP addresses, or reset
- sessions. This active intervention significantly reduces response time and limits damage from attacks.
Interested in Obtaining Your Cloud Computing Certificate? View The Cyber Security Training Offered By ACTE Right Now!
Types of Intrusion Prevention Systems
Intrusion Prevention Systems come in various forms, each tailored to specific environments and security needs. The four primary types are: Network-Based IPS (NIPS), Wireless IPS (WIPS), Network Behavior Analysis (NBA), and Host Based Ips Software (HIPS).
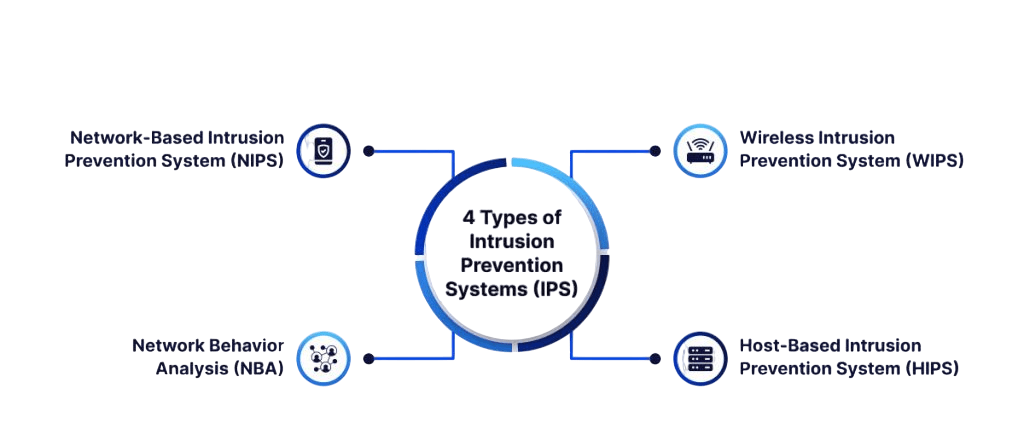
NIPS monitors network traffic for the entire network and provides a broad scope of protection. Cyber Security Training, WIPS is designed to secure wireless networks by detecting unauthorized access points and preventing potential intrusions.that could indicate attacks. HIPS is installed on individual hosts and monitors inbound and outbound traffic for that specific device. Each type serves a unique role, and organizations often deploy a combination to ensure comprehensive coverage.
Network-Based vs Host-Based IPS
- Network-Based IPS and host based ips software serve different purposes in a layered security architecture.
- Network-Based IPS analyzes traffic across the entire network, offering a centralized approach to modern cyber security threats detection and prevention.
- It is typically deployed at strategic points, such as the network perimeter or between network segments.
- Host based ips software , he context of Cybersecurity vs. Network Security, a host-based solution, on the other hand, resides on individual devices and offers granular protection tailored to the host’s specific environment.
- While NIPS is ideal for detecting large-scale attacks and monitoring internal communications, HIPS is better suited for protecting critical servers or endpoints against targeted attacks.
Signature-Based Detection
Signature-based detection is a fundamental technique used by IPS systems to identify known threats. It relies on a database of threat signatures, which are specific patterns or sequences of data associated with malicious activities. When traffic matches a known signature, the IPS triggers an alert or takes predefined action. This method is highly effective against known modern cyber security threats and offers fast and accurate detection. However, it may not be effective against zero-day exploits or sophisticated attacks that do not match existing signatures. To maintain effectiveness, signature databases must be updated regularly to include the latest threat intelligence.
To Earn Your Cloud Computing Certification, Gain Insights From Leading Blockchain Experts And Advance Your Career With ACTE’s Cyber Security Training Today!
Anomaly-Based Detection
- Anomaly-based detection is a more dynamic approach that identifies threats by analyzing deviations from established normal behavior.
- This the broader scope of Cryptography in Cybersecurity, this method uses machine learning algorithms or statistical models to define baseline behavior for network traffic,
- When a deviation is detected, such as an unusual spike in traffic or unexpected access to sensitive files, the IPS flags it as a potential threat.
- Anomaly-based systems can detect previously unknown threats, including zero-day attacks.
- However, they may also generate more false positives, as legitimate activities may occasionally fall outside the defined norms. Tuning the system and refining behavioral baselines is critical for accuracy.
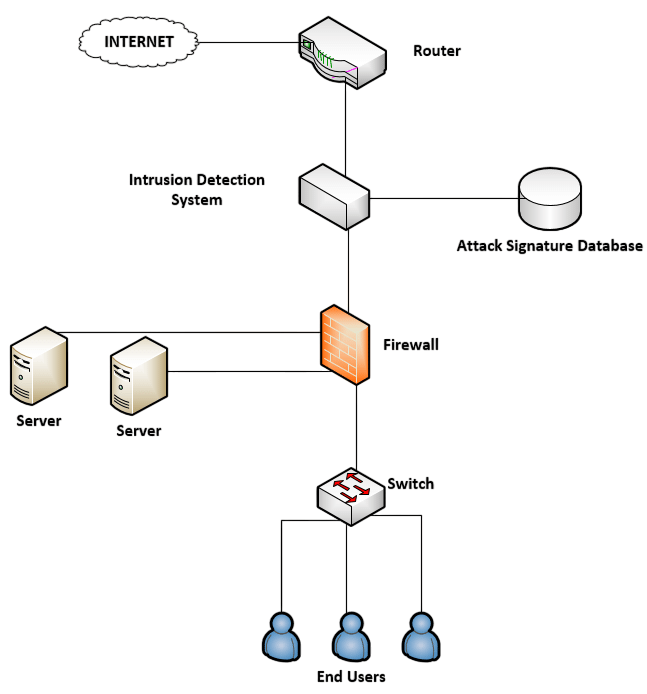
Inline Mode Functionality
One of the defining features of an IPS is its deployment in inline mode. This means the IPS is placed directly in the path of network traffic, allowing it to analyze and act on packets in real time. Inline deployment enables the IPS to block or allow traffic based on predefined policies. Unlike IDS, which passively monitors and alerts, an inline IPS can stop an attack midstream. This proactive approach is effective in minimizing damage from attacks such as malware infections, denial-of-service (DoS) attempts, network security and unauthorized access. However, inline mode also introduces potential performance bottlenecks, making hardware and configuration optimization essential.
Common IPS Tools and Vendors
- The market for IPS tools is vast, with several prominent vendors offering robust solutions.
- Cisco Firepower, Palo Alto Networks Threat Prevention, Snort, Suricata, McAfee Network Security Platform, and Trend Micro TippingPoint are some of the most widely used IPS platforms.
- These tools provide a As part of modern Cyber Security Tools, these solutions offer a range of features including signature and anomaly-based detection, integration with other security systems, and cloud-based management for streamlined protection and control.
- Open-source options like Snort and Suricata are popular in academic and research settings due to their flexibility and community support.
- Vendor selection should consider factors like ease of integration, support, scalability, and update frequency.
Deployment Strategies
Deploying an IPS effectively requires careful planning to ensure optimal protection without disrupting network performance. Common deployment strategies include placing the host based ips software at the network perimeter, network security, between VLANs, or behind firewalls.As emphasized in many Cybersecurity Certifications , in larger networks, segmentation-based deployment helps reduce false positives and allows tailored rule sets for each segment, enhancing both efficiency and security. Inline deployment is common, but some organizations also use passive deployment for less critical segments. Load balancing and failover mechanisms ensure high availability and reliability. Regular performance testing and tuning are essential to maintain throughput and minimize latency. Custom rules and policies should align with the organization’s specific modern cyber security threats landscape and compliance requirements.
Integration with Firewalls and SIEM
- Modern cybersecurity relies on the integration of multiple tools, and IPS is no exception.
- Integrating IPS with firewalls provides an added layer of filtering, allowing coordinated responses to threats.
- While While firewalls control access based on IP addresses and ports, IPS adds context by inspecting the actual content of the traffic—an approach increasingly enhanced byArtificial Intelligence .
- Integration with Security Information and Event Management (SIEM) systems enables centralized logging, correlation, and analysis of IPS events.
- This holistic view enhances threat detection and facilitates faster incident response.
- Many IPS tools come with built-in compatibility with leading SIEM platforms such as Splunk, IBM QRadar, and ArcSight.
Want to Pursue a Software Testing Master’s Degree? Enroll For Cyber Security Master Program Training Course Today!
Role in Modern Cybersecurity
In the modern cybersecurity landscape, IPS plays a vital role in a multi-layered defense strategy. As organizations face increasing threats from ransomware, insider threats, and nation-state actors, IPS provides real-time, automated protection. It complements other security tools like antivirus software, firewalls, and endpoint detection systems. By actively preventing intrusions, IPS helps maintain network integrity, safeguard sensitive data, and ensure compliance with regulatory standards. Its role has expanded with the growth of cloud computing and IoT, requiring adaptation to hybrid and distributed environments. As part of a broader security architecture, IPS contributes to resilience, threat visibility, and faster incident response.
Conclusion
Intrusion Prevention Systems are a cornerstone of proactive network security. he field of Cyber Security Training, these systems not only detect modern threats but also take immediate action to mitigate them, providing essential defense against a wide range of cyberattacks. From understanding their types and detection methods to deploying them effectively and integrating them with broader security ecosystems, IPS tools have evolved to meet the demands of modern IT environments. While challenges like false positives and encrypted traffic remain, ongoing advancements continue to enhance their accuracy and efficiency. As threats grow in complexity, the role of IPS in safeguarding organizational assets becomes increasingly indispensable.

