
Splunk is centralized logs analysis tool for machine generated data, unstructured/structured and complex multi-line data which provides the following features such as Easy Search/Navigate, Real-Time Visibility, Historical Analytics, Reports, Alerts, Dashboards and Visualization.
- Introduction To Splunk Logging
- Splunk ‘logging’ with Java (with a model)
- Steps to incorporate Splunk with a Java project
- Use of key-value pairs
- Utilization of stack-follows for your exemptions
- Utilization of auth-actions
- Conclusion
Introduction To Splunk Logging :-
Splunk is a product that empowers one to screen, search, picture and furthermore to examine machine-created information (best model are application logs, information from sites, data set logs for a beginning) to enormous information utilizing a web style interface. It is progressed programming that lists and searches log records put away on a framework or something like that, close by that, it is an adaptable and intense programming. Splunk spans the holes which a solitary straightforward log the executives programming or a security data item or a solitary occasion the board item can deal with without anyone else.
Splunk ‘logging’ with Java (with a model) :-
To take a gander at the different conceivable outcomes of logging models, let us design Splunk on to a Java project climate and check how we can use the utilization of Splunk. With the goal for us to accomplish this, there a bunch of steps that we really want to finish – and accepting that everything is finished, we will keep on investigating a Java model and test our application with different mixes of logging with Splunk.
- Add Splunk logging to your Java project
- Pick among the accessible choices and add the logging library
- Open a TCP input on your Splunk occasion to log your occasions to
- Arrange your logging framework
- At last, use SplunkCimLogEvent class to produce the log sections in a satisfactory way
- Taking into account that you can design Splunk logging to your Java projects or some other programming dialects that you mean to utilize Splunk with, we will continue with the logging models. This point briefs you on the most ideal ways as does when you make occasions for Splunk Software to file.
Steps to incorporate Splunk with a Java project :-
According to the means referenced over, the article in the hour of its compositions has picked Logback as its logging library and gives the essential antiques to get yourself UP and Running with a functioning model in Java. Taking into account that your Splunk Enterprise is running on your localhost and on the default port of 15000, let us currently design a TCPAppender to Logback as it doesn’t send one all alone. Underneath arrangement shows the essential setup on the direct to get yourself rolling.
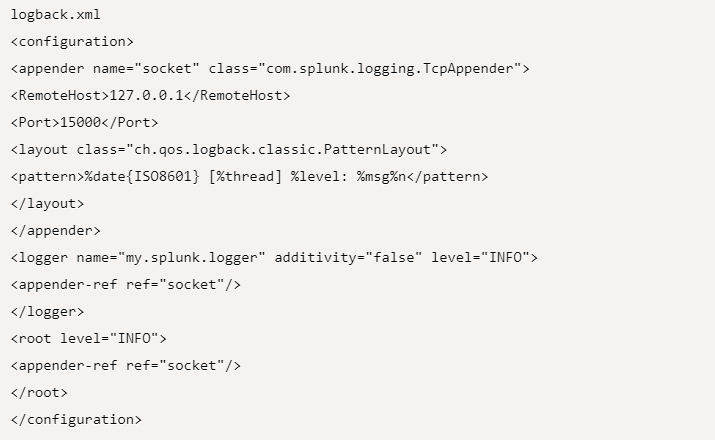
This arrangement that has been given above, will guarantee that you make yourself with a log back library empowered signing on your Java project with the name my.splunk.logger which logs beginning from your INFO messages to the most significant level of ERROR messages.
Presently we can make our own logging class by bringing in com.splunk.logging.SplunkCimLogEvent and utilize that class to make occasions for logging the fundamental data at your will.
- Log.debug(“orderStatus=error, errorcode=546, userId=%d, orderId=%s”, userId, orderId)
Use of key-value pairs :-
This is one of the most incredible potential ways of adding your troubleshoot subtleties to your application log through Splunk or some other logging structure. For Splunk’s utilization, it is strongly suggested that you log data in significant key and worth sets as Splunk can place in its own arrangement of highlights like Reporting being used to give significant subtleties on examining something very similar. It turns out to be exceptionally simple for any to utilize a straightforward quest (for instance, orderStatus=error) to get the subtleties at the same time. Close by that, to utilize Splunk’s Reporting element to snatch a report dependent on the request status, then, at that point, it gets extremely simple (model, success=96%, error=3%, cancelled=1%).
One of the most incredible potential ways of adding key/esteem sets to your logging is as displayed underneath, the very model that is considered above has been altered for better agreement.
- logger.info(new SplunkCimLogEvent(“KeyValuePairEvent”, “keyValuePairEventID”) {{
- addField(“orderStatus”,”error”);
- addField(“errorcode”,”546”);
- }});
- logger.info(new SplunkCimLogEvent(“StacktraceEvent”, “stacktraceEventID”) {{
- addThrowableWithStacktrace(exceptionObject);
- }});
Utilization of stack-follows for your exemptions :-
Cases and situations where you expect that there can be exemptions, you can generally depend on the stack hint of the special case for investigate the errored out situation well. There is a way that you can accomplish this utilizing Splunk to add the stack-follow related subtleties alongside the key/esteem sets as displayed in the above model. Be that as it may, until further notice, we will focus on adding the essential exemption’s stack-follow in our logging source.
Utilizing the add Throw capable With Stack follow() technique designs the special case and adds it to your logging source.
- logger.info(new SplunkCimLogEvent(“AuthActionEvent”, “AuthActionEventID”) {{
- setAuthAction(“LoggedIn”);
- setAuthAction(“LoggedOut”);
- }});
Utilization of auth-actions :-
Situations when you need to log and check the validation related exercises, or even follow back every one of the exercises done by a particular client on your application – this comes into wonderful use. Utilize the set Auth Action() technique to determine the activity performed on the asset. Allow us to see an illustration of its utilization:
Conclusion :-
In this article, we have attempted to demystify what Splunk can do as independent programming and where its utilizations can be. We have additionally attempted to see how to utilize Splunk logging element to examine your application logs.
Trust this article has given every one of the important subtleties to you to comprehend the idea by and large. Assuming you will search for additional subtleties on this theme, we recommend you go through the Splunk documentation.





