
- What is Malware?
- Types of Malware (Virus, Worms, Trojans, etc.)
- Infection Vectors (Email, Web, USB, etc.)
- Lifecycle of a Malware Attack
- Antivirus vs Anti-malware Tools
- Malware Analysis Techniques
- Prevention Strategies
- Malware in Mobile and IoT Devices
What is Malware?
Malware, short for malicious software, refers to any program or code designed to infiltrate, damage, or disrupt computers, networks, or systems without user consent. It poses a serious threat to individuals, businesses, and governments by stealing sensitive data, hijacking systems, or causing operational disruptions. Common types of malware attacks include viruses, worms, Trojans, ransomware, spyware, and adware each with unique methods of spreading and causing harm. For instance, ransomware encrypts data and demands payment for its release, while spyware secretly monitors user activity. With cyber threats growing more sophisticated, cyber security protection is more crucial than ever. Regular Cyber Security Training empowers individuals and organizations to recognize, prevent, and respond to these evolving threats more effectively. Effective protection from malware involves using updated antivirus software, enabling firewalls, applying regular system patches, avoiding suspicious downloads or email attachments, and practicing safe browsing habits. Organizations also rely on intrusion detection systems and employee training to reduce risks. Incorporating strong authentication and data backup strategies further ensures resilience against attacks. Ultimately, understanding what malware is and recognizing its many forms are essential first steps toward a proactive defense strategy. Staying informed and adopting layered cybersecurity practices can significantly lower the risk of falling victim to malicious software and help protect digital environments from evolving cyber threats.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Types of Malware (Virus, Worms, Trojans, etc.)
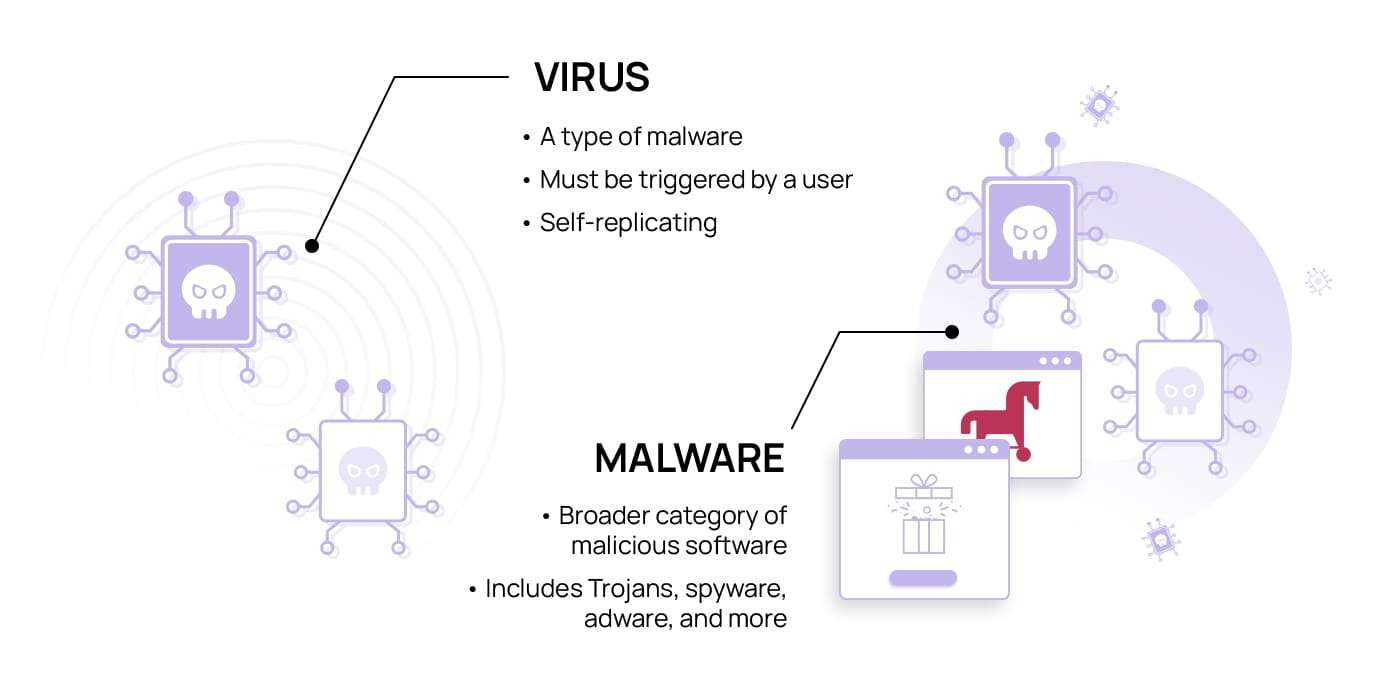
- Malware Virus: A traditional form of malware that attaches itself to legitimate files and replicates when executed. It can corrupt or delete data and often spreads through email attachments or software downloads.
- Worms: Unlike viruses, worms are standalone programs that replicate and spread across networks without user interaction, consuming bandwidth and slowing down systems often creating conditions similar to Learn what is a DDoS attack, where services become overwhelmed and unavailable.
- Trojans: These appear as legitimate software but secretly carry malicious code. Once installed, they can give hackers remote access, steal credentials, or disable security systems.
Malware comes in many forms, each designed to harm systems, steal data, or disrupt operations. These malware programs can spread through downloads, emails, malicious websites, or even removable devices. Understanding the types of malware is crucial in identifying and mitigating various cyber threats before they cause serious damage. Below are six major types of malware that users and organizations should be aware of:
- Ransomware: One of the most dangerous ransomware types, it encrypts user data and demands payment for decryption. It often spreads through phishing emails or compromised websites.
- Spyware: This malware silently monitors user activity, capturing keystrokes, login details, and sensitive information, often without the victim’s knowledge.
- Malware Blocker Evasion Tools: Some advanced malware can bypass antivirus and malware blockers, making detection and removal more challenging and reinforcing the need for strong, up-to-date protection tools.
Infection Vectors (Email, Web, USB, etc.)
Infection vectors are the various pathways through which malicious software infiltrates systems, often catching users off guard. Common infection vectors include email attachments, malicious websites, infected USB drives, and unsecured network connections. Phishing emails remain one of the most prevalent methods, tricking users into clicking malicious links or downloading harmful attachments. Similarly, drive-by downloads from compromised or deceptive websites silently install malware without user consent. USB devices, often overlooked, can carry hidden malware that executes automatically when connected to a system. These vectors are exploited to deliver a range of threats, aligning with different types of malware attacks such as ransomware, Trojans, and worms. Resources like Learn Cyber Security Books can help users understand these risks and adopt safer practices when handling external devices. Understanding how malware spreads is essential for effective protection from malware, as it helps users recognize and avoid risky behaviors. Organizations can enhance their cyber security protection by implementing measures like email filtering, web protection tools, USB usage policies, and regular security training. Installing antivirus software, applying security patches promptly, and enforcing strong access controls also contribute to reducing the risk. As attackers continuously refine their tactics, staying vigilant and adopting a multi-layered defense approach remains the best strategy to defend against evolving malware threats and minimize the impact of infection vectors on personal and enterprise environments.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Lifecycle of a Malware Attack
- Delivery: The attacker sends or places a malware program onto a device or network, often via phishing emails, infected websites, or compromised USB drives.
- Infiltration: Once delivered, the malware installs itself silently. For example, a malware virus may attach to legitimate files, while a Trojan hides within seemingly safe applications. Through regular Cyber Security Training, users can learn to recognize these deceptive tactics and reduce the risk of infection.
- Execution: The malware is triggered, either by user action or automatically. This is where the code begins to perform its malicious tasks, such as creating backdoors or stealing data.
A malware attack doesn’t happen all at once it follows a structured process known as the malware lifecycle. By understanding each stage, individuals and organizations can better detect, respond to, and prevent cyber threats. This lifecycle typically involves multiple steps from the initial infection to the execution of the malicious payload. Here are six key stages in the lifecycle of a malware attack:
- Persistence: Advanced malware ensures it remains on the system, even after reboots. Some malware modifies system files or registry entries to maintain access.
- Payload Action: Depending on the intent, different ransomware types may encrypt files, demand payment, or exfiltrate sensitive data.
- Detection & Blocking: If defenses are in place, a malware blocker may detect the behavior and neutralize the threat before it spreads or causes major damage.
Antivirus vs Anti-malware Tools
While often used interchangeably, antivirus and anti-malware tools serve slightly different purposes in the fight against cyber threats. Antivirus software was traditionally designed to detect and remove older, more established threats like the classic malware virus programs that replicate and infect files. On the other hand, anti-malware tools are built to combat a broader and more modern range of threats, including Trojans, spyware, and advanced ransomware types. In today’s threat landscape, relying solely on traditional antivirus may not provide complete protection. Many modern malware programs are designed to evade outdated detection methods, which is where anti-malware tools excel. These tools often use behavior-based detection to identify suspicious activity even before a threat is fully known. Together, antivirus and anti-malware solutions form a comprehensive malware blocker system, working hand-in-hand to secure devices against both known and emerging attacks. While modern threats require advanced defenses, understanding classical encryption methods like the Vigenere Ciphe can also enhance foundational knowledge in cybersecurity and data protection. As cybercriminals continue to innovate, a layered defense that includes both types of software enhances overall system protection. Whether dealing with legacy viruses or complex ransomware, combining both antivirus and anti-malware tools provides stronger and more adaptive cyber security protection, ensuring users and organizations stay one step ahead of the constantly evolving threat landscape.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Malware Analysis Techniques
Malware analysis techniques are essential in understanding how malicious software operates, helping cybersecurity experts develop strategies for detection, response, and prevention. By analyzing the behavior and structure of malware, security teams can identify specific threats, classify the types of malware attacks, and assess their potential impact. There are two main approaches: static analysis and dynamic analysis. Static analysis examines the malware’s code without executing it, helping uncover hidden instructions, payloads, and patterns. Dynamic analysis, on the other hand, runs the malware in a controlled environment to observe its real-time behavior, such as system modifications, file creation, or communication with external servers. These techniques not only aid in uncovering advanced persistent threats but also support reverse engineering efforts that can reveal vulnerabilities the malware exploits. Understanding how a particular malware functions is critical for crafting specific defenses and updates to antivirus databases. Additionally, incorporating knowledge of Encryption and Decryption Concepts helps analysts understand how malware may conceal its code or communicate covertly, further strengthening overall security measures. Robust cyber security protection relies heavily on continuous malware analysis to stay ahead of evolving threats. Furthermore, effective protection from malware requires a combination of detection tools, threat intelligence, and skilled analysis. By integrating malware analysis into cybersecurity strategies, organizations can respond more rapidly and accurately to threats, reducing the risk of widespread infection and data breaches.
Prevention Strategies
Effective prevention strategies are the cornerstone of defense against the growing number of cyber threats in today’s digital world. As malware programs become more sophisticated, it is critical to adopt a multi-layered approach to security. One of the first lines of defense is maintaining updated antivirus and malware blocker tools that can detect, quarantine, and eliminate both known and emerging threats, including various ransomware types and malware viruses. Regular software updates and system patches help close security gaps that attackers often exploit. Organizations and individuals should enforce strong password policies, use multi-factor authentication, and limit user permissions to reduce the chances of unauthorized access. Educating users about phishing attacks, malicious links, and suspicious downloads is equally vital, as human error often plays a major role in successful infections. Awareness programs can also include What Is Cyber Trolling Concepts Concepts to help users identify and respond appropriately to online harassment, which is another growing concern in the digital landscape. Backing up data regularly ensures recovery in the event of a ransomware attack, while deploying firewalls and intrusion detection systems adds an extra layer of protection. Email filtering, safe browsing practices, and network segmentation can further isolate and contain threats before they spread. Ultimately, preventing malware requires a proactive mindset, continuous monitoring, and the integration of both technology and awareness to stay resilient against the ever-evolving landscape of malware threats.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Malware in Mobile and IoT Devices
As mobile and IoT (Internet of Things) devices become more integrated into daily life and business operations, they are increasingly targeted by malware programs designed to exploit their vulnerabilities. Unlike traditional systems, these devices often lack strong security protocols, making them attractive entry points for attackers. From Android smartphones to smart thermostats and wearable tech, malware can infiltrate through malicious apps, unsecured networks, or outdated firmware. Mobile malware viruses can steal sensitive data, track user activity, or even control the device remotely. In the case of IoT, attackers may use infected devices as part of botnets for large-scale cyber threats like DDoS attacks. Proper Cyber Security Training helps users and organizations identify vulnerabilities in connected devices and implement best practices to prevent such attacks. Even more concerning is the rise of mobile ransomware types, which can lock users out of their phones or encrypt valuable data until a ransom is paid. Traditional malware blockers and antivirus tools often struggle to protect these devices due to their varied operating systems and limited processing power. As a result, securing mobile and IoT environments requires dedicated security solutions, regular software updates, strong password practices, and careful app installation habits. Without these measures, these interconnected devices can become vulnerable gateways for malware, threatening not just individual users but entire networks and infrastructures.




