
- Introduction to the OSI Model
- Purpose and Importance
- Layer 1: Physical Layer
- Layer 2: Data Link Layer
- Layer 3: Network Layer
- Layer 4: Transport Layer
- Layer 5: Session Layer
- Layer 6: Presentation Layer
- Layer 7: Application Layer
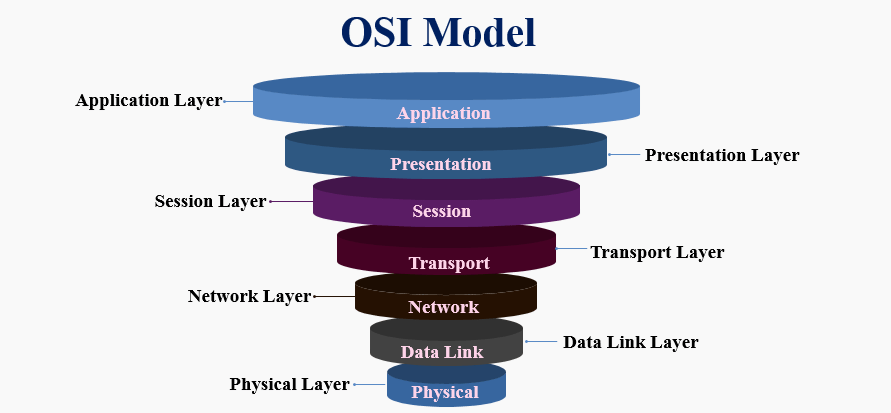
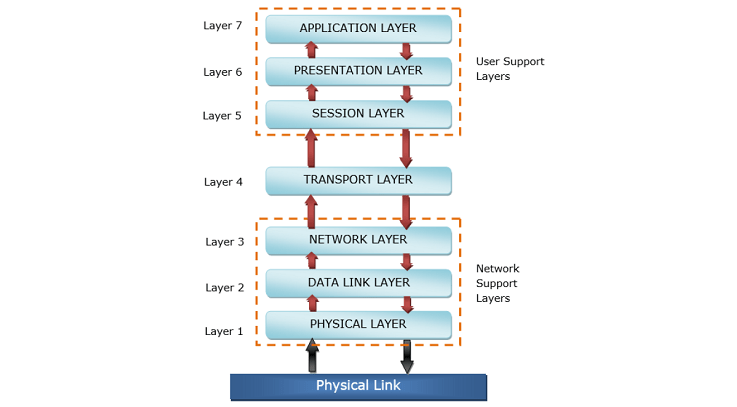
Introduction to the OSI Model
The OSI Model (Open Systems Interconnection Model) is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. This layered approach helps in understanding how different networking protocols interact and operate, forming the backbone of 7 layers of network security. Each layer Physical, Data Link, Network, Transport, Session, Presentation, and Application plays a crucial role in data transmission and security enforcement. In the context of OSI Model cyber security, the model allows cybersecurity professionals to pinpoint vulnerabilities and apply appropriate protections at each layer, making it a foundational topic in Cyber Security Training programs. For example, data encryption occurs at the Presentation layer, while threat detection can be addressed at the Network or Transport layers. This structure becomes especially relevant in cloud environments where securing data and resources across all layers is essential. One modern advancement is the Native cloud firewall OSI layer integration, which provides security directly at specific OSI layers within cloud-native platforms. These firewalls can inspect traffic at layers 3 and 4, and sometimes at the Application layer (layer 7), offering fine-grained control and threat prevention. Understanding the OSI Model is fundamental for anyone looking to build, maintain, or secure a networked environment effectively in today’s digital world.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Purpose and Importance
- Standardization of Communication: The OSI model offers a universal structure that guides vendors and developers in creating compatible networking hardware and software.
- Layered Troubleshooting:With seven layers, issues can be isolated more efficiently, allowing network administrators to pinpoint and resolve problems at specific layers a principle often emphasized in resources like a Guide to Multi-Factor Authentication to enhance layered security strategies.
- Compatibility Across Protocols: The OSI model ensures interoperability between devices and applications using different communication protocols, bridging gaps between systems and the TCP/IP model.
The Purpose and Importance of the OSI model lies in its ability to standardize networking functions, making communication between different systems and protocols seamless. By breaking down the communication process into seven distinct layers, the OSI model layers help in isolating issues, improving interoperability, and guiding the development of networking technologies. It also provides a universal language for understanding complex data exchanges, especially when comparing models like the TCP/IP model or adapting to modern solutions like OSI model Cloudflare implementations.
- Guidance for Network Design: It acts as a blueprint for building secure, scalable, and efficient networks, including integrations with modern technologies like blockchain OSI model structures.
- Supports Cloud-Based Architecture: Technologies like OSI model Cloudflare use the OSI framework to enhance security and performance in cloud networking.
- Security Implementation Across Layers: The 7 application layers allow for targeted security policies, enabling data protection, encryption, and access control across every stage of communication.
Layer 1: Physical Layer
Layer 1: Physical Layer is the foundation of the OSI Model, responsible for the actual transmission of raw bits over a physical medium such as cables, switches, and network interface cards. It deals with electrical signals, light pulses, or radio waves, depending on the transmission technology used. Although it seems purely hardware-based, the Physical Layer plays a vital role in the broader context of OSI Model cyber security. Any disruption or tampering at this layer, like wiretapping or signal jamming, can compromise the entire network infrastructure. These types of risks are often highlighted in resources such as Vulnerability Management Explained, which stress the importance of securing even the most foundational layers of a network. As part of the 7 layers of network security, securing this layer involves ensuring proper physical access controls, using shielded cables, and deploying intrusion detection systems in data centers. In modern cloud environments, while the Physical Layer is abstracted, its principles still influence how data centers are protected and monitored. Innovations like Native cloud firewall OSI layer solutions focus more on higher layers but are built upon a secure and reliable physical foundation. Without the integrity and proper functioning of Layer 1, the security and performance of all other OSI layers are at risk. Therefore, even in today’s cloud-driven world, the Physical Layer remains a critical piece of network design and cybersecurity strategy.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Layer 2: Data Link Layer
- Framing and Addressing: It organizes bits into frames and adds MAC (Media Access Control) addresses, which help identify the source and destination devices on a local network.
- Error Detection and Correction: Basic error-checking mechanisms like CRC (Cyclic Redundancy Check) are implemented to ensure data integrity during transmission, making it a key concept covered in Cyber Security Training for identifying and mitigating transmission vulnerabilities.
- Media Access Control: Determines how devices share the communication channel, using methods like CSMA/CD in Ethernet networks.
Layer 2: Data Link Layer of the OSI model ensures reliable node-to-node data transfer across a physical link. It manages error detection, frame synchronization, and flow control, making sure that data packets are delivered correctly between directly connected devices. In the context of the OSI model layers, the Data Link Layer plays a key role in framing and managing access to the physical medium. It also acts as a bridge between hardware-level functions and higher-layer protocols, including those in the TCP/IP model and modern cloud systems like OSI model Cloudflare implementations.
- Compatibility with TCP/IP Model: While the TCP/IP model merges Layers 1 and 2, the Data Link Layer’s functionality is essential in both models for successful data exchange.
- Foundation for OSI Model Cloudflare Security: Security services like Cloudflare rely on secure data link operations to maintain efficient routing and traffic management.
- Support in Blockchain OSI Model: The Blockchain OSI model benefits from secure and verified data transfer at Layer 2, especially in peer-to-peer communication within distributed networks, contributing to the reliability of 7 application layers in secure environments.
- Reliable Data Transfer: It ensures data is delivered completely and accurately using protocols like TCP, which confirm receipt and request retransmission if needed.
- Segmentation and Reassembly: Breaks large messages into smaller segments at the sender’s end and reassembles them at the receiver’s side a process that ensures data reliability, which is especially important when addressing online threats discussed in topics like What Is Cyber Trolling.
- Flow Control: Manages the rate of data transmission to prevent overwhelming the receiving device, maintaining efficiency and stability.
- Error Handling: Detects errors during transmission and ensures that lost or corrupted data is retransmitted.
- Supports OSI Model Cloudflare Efficiency: Cloudflare leverages Transport Layer capabilities to optimize speed and protect against attacks like DDoS at this layer.
- Enables Blockchain OSI Model Reliability: In a Blockchain OSI model, this layer helps ensure data packets within decentralized systems arrive in order and uncorrupted, forming a secure foundation for the 7 application layers to operate on.
- Data Translation: Converts data formats between sender and receiver (e.g., ASCII to EBCDIC), enabling compatibility across diverse systems.
- Encryption and Decryption: Adds a security layer by encrypting data before transmission and decrypting it upon receipt, enhancing secure communication in 7 application layers.
- Data Compression: Reduces the size of data to improve transmission speed and save bandwidth, especially useful in streaming and cloud-based services a concept often paired with secure access measures found in a Guide to Multi-Factor Authentication to ensure both efficiency and protection in data transmission,
- Support for OSI Model Cloudflare Services: Services like OSI model Cloudflare often rely on this layer for handling SSL/TLS encryption and ensuring secure data exchanges.
- Format Standardization: Ensures consistent data structure and encoding, which is essential for cross-platform applications and web services.
- Blockchain OSI Model Integration: In a Blockchain OSI model, this layer ensures that data entering or leaving the chain is properly formatted and encrypted for secure interaction across decentralized networks.
Layer 3: Network Layer
Layer 3: Network Layer of the OSI Model is responsible for determining the best physical path for data to travel across networks, primarily through logical addressing and routing. It uses IP addresses to ensure data packets are sent from source to destination across multiple networks, making it essential for internet communication. In the context of OSI Model cyber security, the Network Layer is critical as it’s often targeted by attacks such as IP spoofing, route manipulation, and Denial of Service (DoS). Implementing firewalls, intrusion prevention systems, and secure routing protocols helps strengthen this layer’s defenses. As part of the 7 layers of network security, Layer 3 introduces segmentation and filtering based on IP, which reduces the attack surface and improves threat response. These measures are supported by various Cyber Security Tools that enable real-time monitoring, IP blocking, and network traffic analysis to fortify defenses at this layer. With the rise of cloud infrastructure, Native cloud firewall OSI layer solutions increasingly focus on Layer 3 to apply intelligent traffic filtering, enforce zero-trust principles, and ensure secure access across virtual networks. These firewalls inspect and control traffic based on IP addresses, geolocation, and protocol types, making Layer 3 a vital control point in modern security architectures. Without a secure and properly configured Network Layer, all subsequent layers and services risk compromise, highlighting its foundational role in resilient and secure digital communication.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Layer 4: Transport Layer
Layer 4: Transport Layer of the OSI model is responsible for end-to-end communication, ensuring complete data transfer between devices. It manages segmentation, flow control, and error correction, making sure that data is delivered reliably and in the correct sequence. Within the OSI model layers, the Transport Layer plays a pivotal role in maintaining data integrity across networks and is often mapped to the Transport Layer in the TCP/IP model, which uses protocols like TCP and UDP. This layer is vital in systems such as OSI model Cloudflare for maintaining performance and security.
Layer 5: Session Layer
Layer 5: Session Layer of the OSI Model manages and controls the connections between computers, enabling them to establish, maintain, and terminate sessions. It plays a crucial role in coordinating communication between applications, ensuring that data is properly synchronized and organized during active sessions. This layer becomes especially important in continuous data exchanges, such as video conferencing or online banking, where uninterrupted and organized data flow is critical. In the context of OSI Model cyber security, the Session Layer adds a layer of protection by managing secure session setups, using protocols that support authentication and encryption a function often reinforced by implementing some of the Top Cloud Security Tools to monitor and safeguard active sessions in real-time. This helps prevent session hijacking and unauthorized access during communication. As part of the 7 layers of network security, the Session Layer ensures that ongoing communications remain secure and that data integrity is maintained throughout the session duration. In modern cloud environments, Native cloud firewall OSI layer solutions are increasingly designed to recognize and manage session-level data, allowing for more granular monitoring and threat prevention. These firewalls can detect anomalies like multiple session requests from a single source, flagging potential bot or DDoS attacks. Overall, the Session Layer forms a vital checkpoint in maintaining both the structure and security of communication processes across networks.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Layer 6: Presentation Layer
Layer 6: Presentation Layer of the OSI model acts as the translator for the network. It ensures that data sent from the application layer of one system can be read and understood by the application layer of another, regardless of differences in encoding, formatting, or data structure. This layer is responsible for data encryption, decryption, compression, and conversion making it essential for smooth communication across platforms within the OSI model layers and even when bridging with the TCP/IP model, where its functions are merged into the Application Layer.
Layer 7: Application Layer
Layer 7: Application Layer is the topmost layer in the OSI model layers and serves as the interface between the user and the network. It provides network services directly to end-users and applications, enabling activities like web browsing, email communication, file transfers, and remote access. This layer supports protocols such as HTTP, FTP, SMTP, and DNS, which make modern digital communication possible. In comparison to the TCP/IP model, the Application Layer includes functionalities found in the Application, Presentation, and Session layers, emphasizing its broad role in managing data interaction. Understanding this layer is essential in Cyber Security Training, as it plays a critical role in securing user-facing applications and preventing threats like phishing, data breaches, and malicious payloads. With technologies like OSI model Cloudflare, Layer 7 plays a crucial role in enabling secure and efficient application delivery through tools like reverse proxies, DDoS protection, and content caching. Security at this layer focuses on filtering malicious requests, authenticating users, and ensuring encrypted communication via SSL/TLS protocols. As the final piece in the 7 application layers, it completes the full networking stack by making data human-readable and interactive. Furthermore, in a Blockchain OSI model, the Application Layer facilitates smart contract execution and decentralized application (dApp) interactions, ensuring seamless data handling at the user level. Overall, Layer 7 is vital for bridging technical protocols with user experience, making networks functional and accessible.




