
- Introduction to Antivirus Software
- How Antivirus Works
- Types of Malware Detected
- Signature-Based Detection
- Heuristic and Behavioral Analysis
- Real-Time Protection and Scanning
- Common Antivirus Software Tools
- Free vs Paid Antivirus
Introduction to Antivirus Software
Antivirus software is a critical line of defense in today’s increasingly digital world, where cyber threats like viruses, ransomware, spyware, and trojans are more sophisticated than ever. Designed to protect your devices from malicious attacks, system antivirus software works by continuously scanning files, applications, and network traffic to detect, quarantine, and eliminate harmful programs before they can compromise your system. It plays a vital role in preventing data breaches, identity theft, and performance issues caused by malware infections. Anti virus and malware software solutions are no longer limited to simple virus detection; modern tools offer features such as real-time protection, phishing prevention, secure browsing, and automatic updates to stay ahead of emerging threats. As part of a complete defense strategy, organizations and individuals are also investing in Cyber Security Training to better understand how these tools work and how to respond effectively to potential threats.Popular antivirus software like Norton, Bitdefender, Kaspersky, and McAfee have earned global recognition for their reliability and effectiveness, making them go-to options for both individuals and businesses. These programs are tailored to suit various needs, from basic home use to advanced enterprise-level protection. As our reliance on digital platforms grows, so does the importance of having robust antivirus protection in place. Choosing the right system antivirus software ensures peace of mind, allowing users to browse, work, and communicate online with greater security and confidence.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
How Antivirus Works
- Real-Time Scanning: Most antivirus programs provide continuous background monitoring that checks every file you open, download, or run. This ensures that threats are detected before they can act.
- Signature-Based Detection: Antivirus tools use a database of known malware signatures to identify malicious files. When a match is found, the file is flagged or removed immediately.
Antivirus software plays a crucial role in defending your devices against digital threats by identifying, isolating, and removing harmful programs before they can cause damage. Whether it’s viruses, spyware, or ransomware, malware software comes in many forms, and modern antivirus tools are designed to counter all of them. Here’s how antivirus systems work step-by-step:
- Heuristic Analysis: Advanced security software uses behavioral analysis to detect suspicious activities that might not match known threats, catching new or modified viruses. Similar to how Top Container Security Tools monitor container environments for anomalies, this approach helps identify and block emerging threats before they cause harm.
- Automatic Updates: To stay effective against evolving threats like antivirus ransomware, antivirus software regularly updates its virus definitions and algorithms.
- Quarantine and Removal: When threats are found, the protection software isolates the infected files to prevent further spread and allows users to delete or restore them safely.
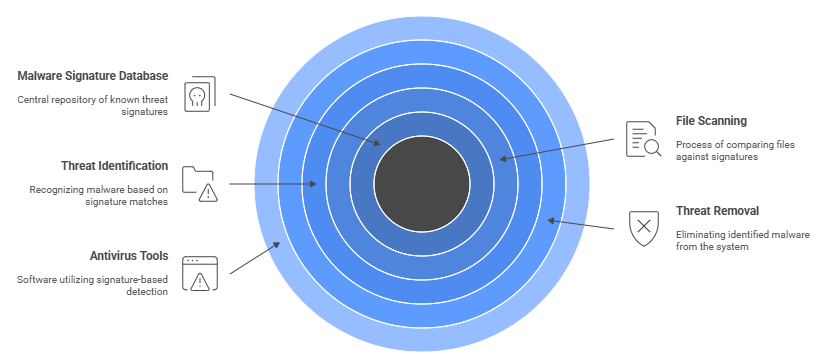
- Malware Signature Database: The antivirus maintains an up-to-date database containing the digital signatures of thousands of known threats, including viruses, worms, and antivirus ransomware.
- File Scanning: As files are accessed or downloaded, the protection software scans them in real-time or during scheduled scans to look for matching signatures. With proper Cyber Security Training, users can better understand how these scans work and respond effectively to potential threats.
- Exact Matching: If a file’s code matches any signature in the database, it is flagged as malicious and either quarantined or deleted immediately.
- Quick Identification: Because it relies on exact matches, this method is fast and efficient in detecting previously identified threats.
- Automatic Updates: Most antivirus tools frequently update their signature database to keep up with newly discovered threats and evolving malware.
- Layered Defense: While effective, signature-based detection is usually combined with other techniques in modern security software to detect unknown or modified malware.
- Live Monitoring: Protection software watches over files, applications, and processes in real time, detecting harmful actions the moment they occur.
- Automatic Threat Blocking: When a threat is detected like antivirus ransomware or trojans it is instantly blocked, quarantined, or deleted, preventing any impact on your system. While modern threats are far more advanced, understanding classic encryption methods like the Vigenere Cipher can help build foundational knowledge in cybersecurity and threat analysis.
- Behavior-Based Alerts: Unlike traditional methods, antivirus tools now monitor for suspicious behavior such as file encryption or system modification in real time.
- Web and Email Protection: Real-time scanning also covers online activities, blocking dangerous websites and infected email attachments before they load.
- Lightweight Operation: Most modern security software is designed to run quietly in the background without slowing down performance.
- Ongoing Updates: To stay effective, antivirus tools constantly update their threat databases to recognize the latest malware software in real-time.
Types of Malware Detected
Modern cybersecurity relies heavily on the ability of system antivirus software to detect and neutralize a wide variety of malicious threats that can compromise data, privacy, and performance. These threats come in many forms, with some of the most common types including viruses, worms, trojans, ransomware, spyware, adware, and rootkits. Each type of malware behaves differently viruses attach themselves to clean files and spread, worms replicate independently to infect other systems, while trojans disguise themselves as legitimate software to trick users into installing them. Ransomware locks down files and demands payment, making it one of the most dangerous forms of attack. Spyware quietly monitors user activity, often for identity theft, and adware bombards users with unwanted ads. Rootkits hide deep in the system, making them difficult to detect and remove. Understanding threats like these is crucial when exploring How Cyber-Physical Systems Work as malware can also target the interconnected hardware and software layers that control physical processes in critical infrastructure. Popular antivirus software like Avast, McAfee, Bitdefender, and Norton offer comprehensive protection by combining multiple detection methods and regularly updating their threat databases. These tools ensure that even new and evolving forms of malware are identified quickly, helping users maintain a secure and efficient digital environment.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Signature-Based Detection
Signature-based detection is one of the oldest and most widely used methods in security software to identify and remove malicious threats. It works by comparing files on a device against a database of known malware “signatures,” unique strings of code or behavior patterns found in malware software. This method is fast and reliable for known threats and forms the backbone of many antivirus tools. Here’s how it works in detail:
Heuristic and Behavioral Analysis
Heuristic and behavioral analysis are advanced techniques used by system antivirus software to detect threats that traditional signature-based methods might miss. Instead of relying solely on known malware signatures, this approach analyzes how programs behave and searches for suspicious patterns or actions typically associated with malicious intent. For example, if a program suddenly starts modifying system files, encrypting data, or communicating with unknown servers, the antivirus flags it as potentially harmful even if it has no known signature. This proactive approach is especially useful for identifying zero-day attacks and new variants of anti virus and malware software that have not yet been cataloged. It enhances detection across various Types of Malware Attacks including those that evolve rapidly to bypass traditional security measures. Popular antivirus software like Bitdefender, Kaspersky, and Norton integrate heuristic and behavioral analysis to provide an extra layer of protection, ensuring that even sophisticated or newly released malware can be detected before it causes harm. This method not only improves threat detection rates but also enhances the overall responsiveness of system antivirus software, making it more adaptive to evolving cybersecurity threats. By combining heuristic analysis with real-time monitoring and threat isolation, anti virus and malware software become far more robust and reliable, helping users stay safe in an ever-changing digital environment where threats are becoming smarter and more evasive.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Real-Time Protection and Scanning
Real-time protection is a critical feature of modern security software that continuously monitors your system for threats as they happen. Instead of waiting for scheduled scans, this technology provides instant responses to suspicious activities, helping to stop attacks before they can do damage. Whether it’s detecting harmful downloads or blocking background processes, real-time scanning is essential in staying ahead of advanced malware software threats. Here’s how it works:
Common Antivirus Software Tools
Common antivirus tools are essential in protecting personal and enterprise systems from the constant threat of malware software. These tools come equipped with advanced features designed to detect, block, and remove a wide range of digital threats, including viruses, spyware, and especially dangerous threats like antivirus ransomware. Leading security software solutions such as Norton, Bitdefender, McAfee, Kaspersky, and Avast have become household names due to their reliability, user-friendly interfaces, and multi-layered protection mechanisms. They offer real-time scanning, firewall integration, email protection, safe browsing tools, and heuristic-based analysis to catch even the most elusive forms of malware. These protection software solutions also support automatic updates, ensuring users are always shielded from the latest cyber threats. Some antivirus tools are even cloud-powered, leveraging vast threat intelligence networks to detect malware faster and more accurately. For users looking to enhance their understanding of these tools and best practices, a Quick Guide To Cyber Safety can offer essential tips on staying secure in an ever-evolving digital landscape. Many of them also include features like parental controls, password managers, and VPN services to provide all-around digital safety. Whether you’re safeguarding a personal device or securing a business network, choosing trusted security software ensures peace of mind in an environment where new forms of malware software emerge daily. These tools are not just optional they are a vital component of modern digital defense.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Free vs Paid Antivirus
When choosing between free and paid system antivirus software, it’s important to understand the key differences in features, performance, and protection levels. Free anti virus and malware software typically offers basic protection, such as virus scanning, quarantine, and removal of common threats. While it can be effective for casual users with limited online activity, it often lacks advanced features like real-time protection, firewall integration, phishing detection, and ransomware defense. On the other hand, paid versions of popular antivirus software like Norton, Bitdefender, Kaspersky, and McAfee provide a more comprehensive security suite. These premium tools offer features such as multi-device support, secure browsing, identity theft protection, automatic updates, and priority customer support, making them ideal for users who handle sensitive data, perform online banking, or use multiple devices. When combined with Cyber Security Training, these tools empower users to recognize threats early and take proactive steps to secure their digital environments. Additionally, paid system antivirus software is more likely to include frequent updates and heuristic analysis to detect emerging threats that free versions might miss. While free anti virus and malware software is a good starting point, investing in popular antivirus software ensures stronger, more consistent protection. Ultimately, the decision depends on your specific security needs, online behavior, and how much value you place on advanced digital safety and peace of mind.




