
- Introduction to Digital Forensics
- Types of Digital Forensics
- The Future of Digital Forensics
- Key Tools in Digital Forensics
- Legal Issues with Digital Forensics
- Challenges in Digital Forensics
- The Digital Forensics Process
- Conclusion
Digital forensics is a continually evolving field that aims to identify, preserve, analyze, and present digital evidence for legal investigation. With the advent of technology, handling electronic evidence requires special techniques. Digital forensics is integral to solving crimes related to Cyber Awareness , data breaches, and other forms of digital misconduct. We’ll learn about the definition of digital forensics, its various forms, its procedures, and the difficulties those who work in this sector face.
Are You Interested in Learning More About Cybersecurity? Sign Up For Our Cyber Security Online Training Today!
Introduction to Digital Forensics
Digital forensics is discovering and decoding electronic data for criminal investigations. The field encompasses various devices and platforms, including computers, mobile phones, networks, and cloud services. It is an essential part of modern law enforcement, steganography and corporate cybersecurity. Cybersecurity Training Courses its most basic form, it tries to answer the question: What happened, and how did it happen? For instance, it can be used to unearth the events leading to a cyberattack, detect the perpetrator of a data breach, or recover evidence from a compromised device.
Types of Digital Forensics
Digital forensics encompasses several sub-disciplines, each focused on a specific type of digital evidence.
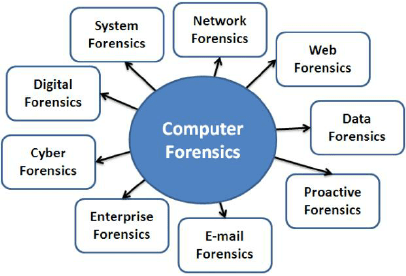
- Computer Forensics: Computer forensics involves the recovery, analysis, and presentation of data found on computer systems, including hard drives, servers, and other storage devices. Computer forensic experts typically recover deleted files, analyze logs, and extract valuable data for investigation.
- Network Forensics: Network forensics is the monitoring and analyzing network traffic to investigate security-related incidents such as data breaches, hacking attempts, and unauthorized access. Analyzing network logs and communication patterns gives a clue to trace malicious activities by forensic experts to detect intrusions and point out network infrastructure vulnerabilities.
- Mobile Device Forensics: Mobile device forensics has become an integral part of digital investigations with the widespread use of smartphones and tablets. It deals with extracting, recovering, and analyzing data from mobile devices, including text messages, call logs, emails, and even GPS data. Mobile device forensics can help law enforcement agencies track down suspects or uncover evidence in fraud, theft, or cyberbullying cases.
- Database Forensics: Database forensics is the process of identifying and tracing events or malicious activities possibly carried out in a Database Security . This can include looking for hashing,unauthorized access, analyzing audit trails, and retrieving missing or deleted data. Database forensics is usually integral in financial fraud, theft of intellectual property, or corporate espionage cases.
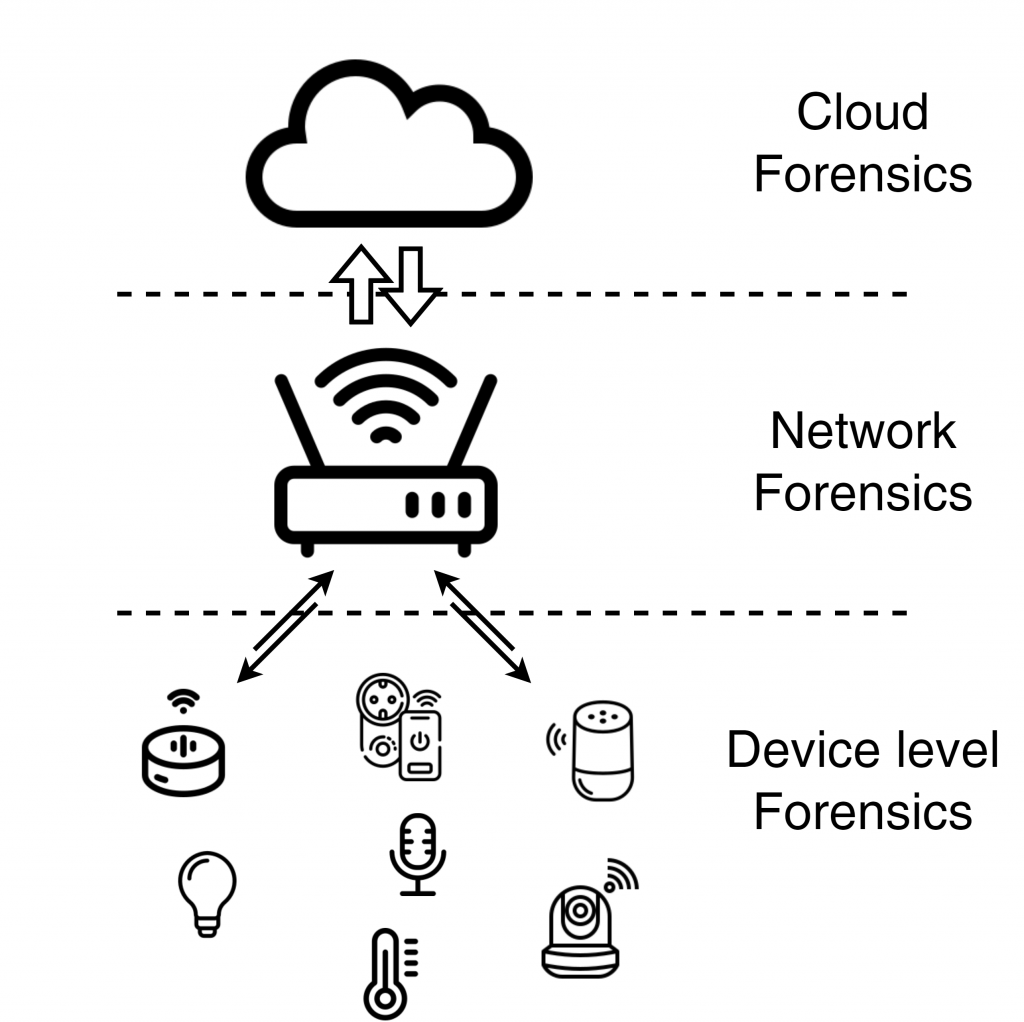
- Cloud Forensics: With more data and applications moving to the cloud, a new field, cloud forensics, is also being developed. Cloud forensics analyzes data stored in cloud environments for traces of cybercrime or data breaches. As the infrastructure is distributed, challenges related to retrieving data arise regarding jurisdiction over legal procedures and access controls.
- EnCase: It is a very common computer forensics software that can acquire, analyze, and report on data.
- FTK (Forensic Toolkit): A forensic tool used to analyze files, recover data, and handle evidence.
- Wireshark: Network protocol analyzer. This tool captures and analyzes network traffic.
- Cellebrite: Mobile device forensics. It extracts data from the mobile device for further analysis.
- X1 Social Discovery: This tool analyzes data from social media platforms. It is commonly used in cyberbullying or fraud cases.
- 6.1 Encryption and Anti-Forensics Techniques: Modern encryption methods and anti-forensics tools pose great challenges to investigators. These tools are meant to make accessing or manipulating digital evidence hard. Decrypting encrypted data or bypassing anti-forensic measures requires much technical expertise and time.
- Legal and Jurisdictional Issues: Jurisdictional issues arise because digital evidence frequently crosses national borders. Distinct jurisdictions have distinct rules and procedures that investigators must follow, which can cause delays in the investigative process. Accessing data kept in other nations frequently necessitates international cooperation.
- Rapidly Changing Technology: New technologies are evolving rapidly, and digital forensic specialists struggle to stay ahead. These technologies include blockchain, artificial intelligence, and Internet of Things devices, which present new challenges in gathering and analyzing evidence.
- Large Volumes of Data: Digital investigations involve scanning massive amounts of data, which consumes time and resources. Sifting through terabytes of data to find evidence of relevance requires powerful Container Security Tools and well-trained professionals.
- Integrity and Authenticity of Digital Evidence: There is a constant concern for maintaining the integrity and authenticity of digital evidence. Data must not be modified during the investigation. Minor discrepancies might lead to evidence being excluded in court.
- Identification: This would entail determining possible evidence sources, such as whether systems, devices, and apps might contain pertinent information about the case. Depending on the case’s specifics, this procedure may concentrate on desktops, mobile devices, network logs, or cloud platforms.
- Preservation: The evidence must be kept safe when the pertinent systems and devices have been located. This is essential to prevent digital data from being destroyed or altered. Investigators frequently create a forensic copy or picture of the data to ensure the original data is not changed. Chain of custody documentation is crucial to preserve the integrity of the evidence at this point.
- Analysis: After gathering and storing evidence, forensic professionals proceed to the analytical process. In this process, the collected data is studied for traces of criminal intent or misconduct. Depending on the kind of digital forensics, this may encompass restoring deleted files, decryption, Network Penetration Testing, or extracting information from a mobile device. Forensic tools and techniques, including file carving or timeline analysis, are used to retrieve concealed or obscure evidence.
- Documentation: All actions, findings, and tools used throughout the investigation should be documented. Documentation will ensure the investigation is transparent, repeatable, and legally defensible. It includes recording details on data collection, analysis methods, and conclusions reached. Documentation is important for presenting evidence in court.
- Presentation: The final step is presenting the findings. Investigators will prepare detailed reports or testify in court to explain the evidence and how it was obtained. The presentation must be clear, precise, and easily understood by non-technical audiences, such as judges and juries.
To Earn Your Cyber Security Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
The Future of Digital Forensics
Increased AI and machine learning use will enable investigators to sift through large datasets efficiently and accurately. Focus data encryption on mobile and cloud forensics. That area will be critical with the widespread usage of smartphones and cloud services. Cybersecurity Training Courses and digital forensics professionals often work to prevent cybercrime and defend sensitive data.In terms of its future, digital forensics looks promising, emerging technologies to help overcome current challenges and improve the effectiveness of investigations.The very basic tool that would help the fight against cybercrime and other digital malpractices would be digital forensics. It can only be comprehended when types, processes, and challenges are known to help professionals better prepare themselves to answer the calls of this field that is rapidly growing in demand. Whether computer forensics, mobile device analysis, or network investigations, digital forensics is pivotal in doing justice in the ever-more digital world.
Key Tools in Digital Forensics
Gain Your Master’s Certification in Cybersecurity by Enrolling in Our Cyber Security Expert Masters Program Training Course.
Legal Issues with Digital Forensics
Laws and regulations governing digital forensics are highly controlled and differ from one nation to another. Investigators should understand the legal Cybersecurity Framework governing the acquisition and processing of digital evidence. Keeping an uninterrupted log of who handled the evidence, when, and how is known as the chain of custody. Search Warrants Often, investigators must get a court order to search networks or devices.Data Privacy Regulations Investigators must be aware of privacy regulations safeguarding personal information, particularly when social media or cloud storage is involved. Court Admissibility Digital evidence must adhere to stringent legal requirements to be admissible in court.
Challenges in Digital Forensics
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers.
The Digital Forensics Process
Conclusion
One of the most important fields in the modern period is Cybersecurity Training . It is essential to criminal investigations and maintaining security in online settings. It is a highly pertinent field for businesses, law enforcement, and cyber specialists. Digital forensics helps find the truth in a constantly changing digital landscape by identifying and preserving digital evidence and analyzing massive amounts of data across several platforms, including PCs, mobile devices, networks, and the cloud. Despite its importance, forensics has its struggles, such as encryption, legal implications, and the vast scale of data to process; yet, with advanced technologies and more sophisticated forensic devices coming into play, its future is promising, with high hope in the incorporation of artificial intelligence and machine learning into streamlining processes and accuracy.





