
- Introduction
- What is a Computer Virus?
- How Does a Computer Virus Work?
- Types of Computer Viruses
- How to Detect a Computer Virus
- How to Protect Your Computer from Viruses
- Conclusion
Introduction
Computer viruses are one of the oldest and most dangerous types of malware in the world of cybersecurity that still pose a great threat to both individuals and organizations. A computer virus is like a biological virus, which infects living organisms. It spreads from one system to another and causes damage to files, systems, and Power of Network Address Translation . In this blog, we will explore what a computer virus is, how it works, the different types of viruses, how to recognize them, and most importantly, how you can protect your system from getting infected.
What is a Computer Virus?
- A computer virus is the kind of malicious software that clings itself to a legitimate program or file and spreads from one computer to the other in Cybersecurity Training Courses .
- It not only corrupts your data and causes interference with system functions but can delete or steal sensitive information too.
- Viruses can be spread through all means, including email attachments, software downloads, infected websites, and infected USB drives.
- The term “virus” is frequently used interchangeably with other types of malware, but it specifically refers to malicious programs that replicate and spread by modifying other computer programs and files.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
How Does a Computer Virus Work?
A computer virus works by attaching itself to a legitimate file or program. After the infected file is executed, the virus is activated and begins replicating itself. It spreads into other programs, files, or even other computers on the same network. Here’s a step-by-step process of how a typical virus works:
- Infection:The virus attaches itself to a legitimate file or program, such as an executable file (.exe) or a Word document.
- Replication:Once the infected file is opened or run, the virus replicates itself and spreads to other files or programs on the system.
- Execution:The virus executes its Payloads, which could include deleting files, stealing information, or damaging system components.
- Spread:The virus may then spread through email, networks, or removable storage devices to infect other computers or systems.
- Latency Period:Some viruses may lie dormant in the system for a certain period before they become active and cause harm.
The ability of a virus to replicate itself makes it particularly dangerous. Viruses can quickly spread to many systems and cause widespread damage, especially if they are not detected early.
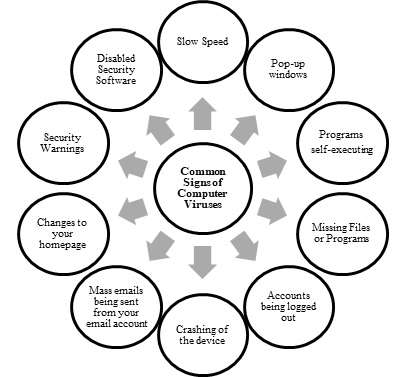
Types of Computer Viruses
Computer viruses can be very different in their behavior, methods of spreading, and the kind of damage they cause. Below are some of the most common types of computer viruses:
File Infector VirusA file infector virus attaches itself to executable files, such as programs with the.exe or.com extension. Once the infected program is run, the virus executes and spreads to other executable files on the system. These viruses can cause a wide range of damage, from corrupting files to completely disabling a system.
Macro VirusIt affects software applications that employ macros, including word processors and spreadsheets. It attacks files developed using these applications, such as Word or Excel documents. It achieves this by exploiting the macro language used in automating procedures. Once opened, the user facilitates the spreading of the macro virus to other documents by opening them.
Boot Sector VirusA boot sector virus infects the master boot record (MBR) of a computer’s hard drive or removable storage devices, such as USB drives. These viruses are particularly dangerous because they load before the operating system, making them difficult to detect and remove. Boot sector viruses can prevent a system from booting properly or cause it to crash.
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
Polymorphic VirusA polymorphic virus is developed to change its form every time it infects a system. Therefore, this Firewall and Antivirus Software cannot be easily detected by the antivirus program since its signature changes each time it replicates. Polymorphic viruses are advanced and may change to accommodate various environments. Therefore, it becomes hard to eliminate them.
Metamorphic VirusA metamorphic virus is even like a polymorphic virus. In other words, every time a virus replicates, it writes over its code. This will be even harder to detect since it changes appearance as well as behavior with every infection. As stealthy, these metamorphic viruses are very often utilized for targeted attacks.
How to Detect a Computer Virus
The most difficult thing is to identify a computer virus since most viruses are programmed to go undetected or even hide their activities. However, there are some common signs that your computer may be infected: slow system performance; if your computer suddenly becomes slow or unresponsive, it could be a sign of a virus consuming system resources in Cybersecurity Training Courses .
- Unexpected pop-ups:Viruses often display unwanted pop-up ads or error messages, which may seem out of place or appear randomly.
- Corrupted files:If files are disappearing, becoming unreadable, or showing strange behavior, this could indicate that a virus has corrupted them.
- Unusual network activity: Sudden high network traffic or unusual data transfers may indicate that your computer is part of a botnet or is being used for malicious purposes.
- Disabled antivirus software: Some viruses disable or manipulate antivirus programs, leaving your system open to more infections.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Effects of a Computer Virus Infection
The consequences of an infection by a computer virus vary depending on the type of virus and the degree of damage that it causes. Some of the potential effects of a virus infection include:
- Data loss: Viruses can delete or corrupt files, causing you to lose important data, such as documents, photos, or software configurations.
- System instability: A virus can cause your operating system to become unstable, resulting in crashes, freezes, or even system failures.
- Identity theft: Certain viruses, like Keylogger, can record your keystrokes and steal sensitive information, such as usernames, passwords, and credit card numbers.
- Financial loss: Viruses can lead to financial loss by stealing money from your bank account, credit cards, or other payment methods.
- Network disruption: Viruses can spread across networks, infecting other devices and causing massive disruption in an organization’s infrastructure.
- Reputation damage: In business, viruses can harm a company’s reputation, especially when they compromise sensitive customer information.
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
How to Protect Your Computer from Viruses
Protecting your computer from viruses involves a combination of prevention and good habits. Here are some tips on what to do for system safety:
- Install and update antivirus software: Use good antivirus software to detect and remove viruses. Ensure that your antivirus software is always updated.
- Keep your operating system updated: To protect against Vulnerability Management, regularly update your operating system with the latest security patches.
- Be cautious of email attachments: Don’t open attachments or click on links from unknown or suspicious email addresses.
- Avoid downloading software from untrusted sources: Only download software from reputable websites or official app stores.
- Use firewalls: Enable firewalls to protect your computer from unauthorized access and prevent viruses from spreading.
- Regularly back up your data: Create backups of important files to ensure that you can recover them in case of a virus infection.
- Use strong passwords:Set strong, unique passwords for all your accounts to prevent hackers from gaining access to sensitive information.
Conclusion
A computer virus is a harmful program that can replicate itself and spread to other systems, causing damage, data loss, and security breaches. Viruses work by infecting files, programs, or boot sectors, and Cybersecurity Training can be spread through various methods, such as email attachments and software downloads. By understanding how viruses work, recognizing the signs of infection, and following preventive measures, you can protect your computer from becoming a victim of these malicious programs. Keep your software updated, use reliable antivirus tools, and adopt safe online habits to keep your system secure and your data safe from viruses.





