
- Introduction
- What is Carding?
- Carding Examples and Forums
- Carding Attack Process and Key Points
- Carding using Mobile Phones
- Avoiding Card-cracking Bots and Additional Security Measures
- Card Fraud Detection
- Conclusion
Carding is a form of cybercrime where stolen credit card details are used for unauthorized transactions. Fraudsters exploit vulnerabilities in payment systems to validate and use stolen data. This illegal activity thrives on dark web forums and automated bots. Mobile devices have made carding easier for criminals. Implementing strong security measures is crucial to detect and prevent such attacks, and Cyber Security Training Courses are essential in educating employees and individuals about the risks and best practices to protect against such fraud.
To Explore Carding Attack in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Introduction
Carding is a cybercrime technique where criminals use stolen credit card details to make unauthorized transactions. It involves testing the validity of card numbers through small purchases or automated bots before conducting larger fraudulent transactions. Hackers often share carding techniques, tools, and stolen data on underground forums and dark web marketplaces. Mobile apps, e-commerce sites, and payment gateways are frequent targets due to security loopholes and insufficient fraud detection mechanisms. Understanding the MD5 Algorithm its Role and Functionality is important, as it is sometimes used in the process of hashing and storing card data, making it crucial to ensure its proper use and avoid vulnerabilities that can be exploited by attackers. Implementing advanced fraud detection tools, multi-factor authentication, and AI-driven security measures is crucial in preventing carding attacks and protecting sensitive financial information.
What is Carding?
- A carding discussion board is an unlawful web website online wherein stolen credit score card information is shared. The discussion board additionally encourages discussions on strategies that may be used to gain credit score card facts, validate it, and use it for unlawful activities.
- These boards are hubs for crook organizations and folks who buy credit score card facts in bulk and promote them on the dark web. These boards are hidden with Tor routing, and bills are made in cryptocurrency to keep away from detection. The carder stays anonymous.
- Carding boards also can be used to percentage the effects of carding. For instance, promoting effectively stolen credit score playing cards to different criminals.
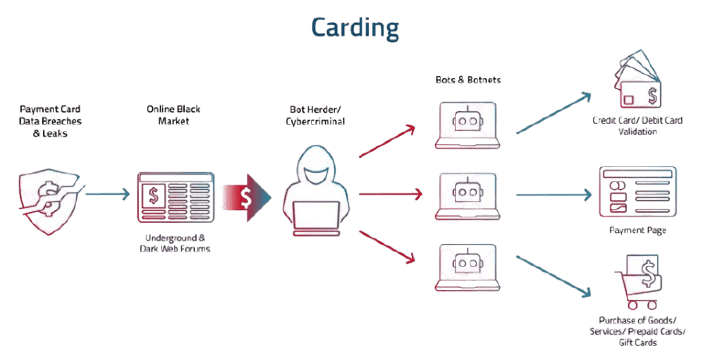
- Carders acquire stolen credit score card numbers from crook marketplaces, compromised websites, or price channels.
- Carders then install bots to make small purchases on numerous sites. In each attempt, a card quantity is examined in opposition to a merchant`s price tactics to decide the validity of card details.
- The validation technique is tried heaps of instances till it yields results.
- The obtained card numbers which can be efficaciously demonstrated are then prepared right into a listing and used for different crook sports or offered to prepared crook outfits.
- Carding is undetectable by card owners until it’s too late and their money is stolen. To prevent such attacks, implementing Access Control Lists can help restrict access to sensitive information, ensuring that only authorized users can make transactions and reducing the risk of carding activities.
- Computer: Carding entails a laptop system. Some additionally use a cellular device, however, it is much less stable and might appear to be unstable. Carders use others` PCs to execute this assault.
- SOCKS: SOCKS stands for SOCKet Secure. It is a web protocol that allows purchaser and server visitors to skip through a proxy server. This hides the actual IP, and the proxy IP is reflected. This enables a carder to apply a credit score card owner`s region at some stage in the technique. SOCKS are to be had for the carders to buy.
- MAC Address Changer: MAC Address Changer is the precise deal with each community interface card (NIC.) A MAC deal with a changer permits one to alternate the MAC of NIC instantly; it’s miles used for anonymity.
- CCleaner: CCleaner is beneficial for cleansing surfing history, cookies, and temp. Files, etc. Ignoring this step can show to be unstable for a carder.
- RDP: Remote laptop protocol, or RDP, allows computer systems in an equal community to connect. Carders misuse this protocol to connect with computer systems of the geolocation of the individual whose credit score card is targeted. This technique enables carders to live anonymously.
- DROP: DROP is a deal that is utilized by a carder because the delivery deal with at some stage in the carding technique. The deal has to fit with the location of the credit scorecard. Sometimes, carders use drop offerings with a further delivery cost.
- Credit Cards:
Discover, Mastercard, Visa, and Amex are 4 of the essential credit scorecard networks. Credit playing cards comprise the following information:
- Name
- Credit card quantity
- Expiry date
- CVV2 code
- Address
- Phone quantity, now and then no longer included)
- Unusual order sizes
- High purchasing cart abandonment rates
- A notably excessive variety of failed bills
- Abnormal usage, too excessive or too low, of the price step
- Increased chargebacks
- Multiple failed price authorizations from the identical session, consumer, consumer agent, IP address, tool ID, or fingerprint
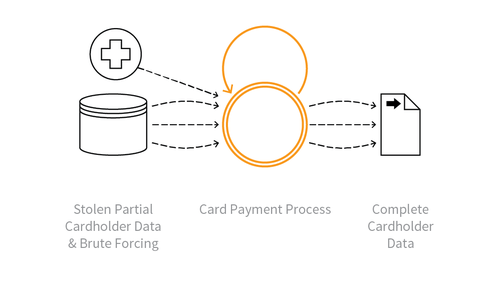
Carding is likewise referred to as credit score card stuffing or card verification. It is an internet protection chance wherein attackers try and authorize stolen credit score card credentials and use them to fee pay as you go playing cards or present playing cards. These playing cards are then bought or used to make purchases of goods, that could then be bought for cash. People who are worried about carding are referred to as carders. Carding is achieved with the assistance of bots and hacking software, which can perform automatic operations over the internet. Cryptanalysis plays a key role in identifying and breaking down encryption methods used in these attacks, allowing security experts to detect and prevent carding activities more effectively. The goal is to pick out card numbers or information that may be used to carry out purchases. The United States has an excessive goal for carding credit score and debit playing cards. This is due to the fact the USA has a big marketplace for playing cards that incorporate magnetic strips or chips and signature technology, not like the greater stable chip and PIN technology.
Carding Example and Forums
An instance of carding occurred while hackers constructed a malicious bot named GiftGhostBot. The reason for this bot was to hack the balances of present playing cards. Around 1,000 e-trade websites have become sufferers of this carding assault. The advanced, chronic bot exams tens of thousands and thousands of present card numbers robotically to perceive those with balances. This bot continues to be attacking websites. The established present card numbers are used to make purchases. This card-cracking or token-cracking assault is usually untraceable as soon as the stability is stolen.
Interested in Obtaining Your Carding Attack Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Carding Attack Process and Key Points
A carding assault technique generally entails the following steps:
Carding using Mobile Phones
Carding using mobile devices, particularly rooted Android phones, is a method employed by more experienced and skilled cybercriminals due to its complexity and the risks involved. Rooting an Android phone allows the user to gain full administrative control over the device, enabling them to run specialized applications designed to mask their activities and bypass security measures. These applications, such as CCleaner, proxy apps, IMEI changers, Android ID changers, and others, are used to manipulate or hide crucial identifiers, including device information and location, making it harder for authorities or financial institutions to track the illicit activity. The carding process on mobile devices typically involves stealing or using stolen credit card details to make unauthorized purchases or commit fraud. To prevent such activities, Cyber Security Training Courses are crucial in educating users on recognizing signs of fraud and implementing safe practices to protect sensitive information. By utilizing tools to disguise the device’s identity and mask the user’s actions, carders can evade detection from security systems that rely on standard patterns or device identifiers. This approach has become increasingly popular among cybercriminals because it offers greater mobility, anonymity, and the potential for avoiding detection compared to traditional carding methods carried out on computers. However, the use of rooted Android phones in carding can be dangerous, as it increases the risk of exposure and security vulnerabilities, especially if the malicious applications are not carefully managed.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Avoiding Card-cracking Bots and Additional Security Measure
Device fingerprinting identifies the browser and tool parameters that stay consistent among sessions, i.e. if the identical entity is attempting to attach repeatedly, you’ll be capable of knowing. This era creates a unique tool, browser, and cookie identifier. If there is more than one login, it’ll without delay enhance the suspicion that those are fraud attempts. Browser validation is some malicious bots can pretend to be the users of a browser, and that they keep away from being detected via way of means of biking through person agents. Browser validation verifies that a browser is actual with the anticipated JavaScript agent and ordinary browser operations. It guarantees that a human and now no longer a bot in the usage of the browser. Machine studying behavior evaluation are real customers touring a charged internet site show off regular behavior styles. Bots do not follow this pattern. Behavioral analysis technology analyzes a person’s behavior and detects any anomalies. This can prevent cracking attempts. Digital Forensics plays a vital role in investigating such incidents, identifying how bots or attackers exploit vulnerabilities, and gathering evidence for further action. Reputation evaluation having a database of acknowledged predictable, technical, and behavioral bot styles or originating IPs can assist in becoming aware of horrific bots.
Progressive challenges when a device detects a suspicious bot, there are revolutionary mechanisms in the area for checking out customers to verify if they’re a bot or human. It first makes use of the least intrusive method, decreasing the disruption for actual customers some revolutionary challenges are Captcha its Most disruptive to actual customers, JavaScript challenge are slightly slows down the person’s experience and Cookie Challenge Goes ignored to actual customers Aside from the above techniques, one also can take subsequent measures to bolster the safety perimeter in opposition to cracking bots. Multifactor authentication Most e-trade websites require login usernames and passwords in addition to maintaining tabs at the tool used for login. While this doesn’t save you cracking, it units up a task for carders and renders it not possible or fairly tough for them to take over present accounts. API security E-trade web sites the usage of credit score card APIs are regularly prone to assaults which include rerouting of statistics or JavaScript injection. For protection, those websites can employ an aggregate of shipping layer security (TLS) encryption and sturdy authentication mechanisms which include OAuth and OpenID.
Card Fraud Detection
Sniffing and Spoofing techniques are often used by these bots to intercept and manipulate data, making it crucial for websites to implement strong encryption and fraud detection systems to protect against such attacks. Here are numerous forms of bills that paid websites are capable of stumbling on as attempts by carding bots:
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
This weblog is meant to unfold recognition about carding, which is a growing concern in the digital world. In no manner is it a manual to encourage or promote such illicit activities. The rise of online transactions has made carding a widespread issue, affecting businesses, financial institutions, and individuals globally. However, with the right security measures, such as AI-driven fraud detection, multi-factor authentication, encryption, and real-time monitoring, organizations can significantly reduce the risk of carding attacks. Additionally, Cyber Security Training Courses are vital for educating employees on recognizing and preventing carding attempts, ensuring a holistic approach to cybersecurity.There are multiple solutions available today that can safeguard against carding, and continuous awareness, strict regulations, proactive cybersecurity strategies, and advanced authentication methods are essential to combat this evolving threat effectively.





