
- Introduction to Network Address Translation (NAT)
- How Network Address Translation (NAT) Works
- Types of Network Address Translation
- Why is NAT Important in Networking?
- Advantages of Using Network Address Translation
- NAT and Security: How It Benefits Network Security
- Common NAT Issues and Troubleshooting
- Conclusion
Introduction to Network Address Translation (NAT)
PAM is a security practice that involves tracking and monitoring who, with what, and when accesses critical systems, applications, and data of elevated privilege. Such users, including system administrators, have access well beyond the ordinary users, and thus, their accounts are desirable for attackers. Cyber Security Training Courses helps reduce the risks involved in these privileged accounts by controlling, securing, and auditing access. Generally speaking, pam security includes binding and managing credentials, introducing stringent access controls, along monitoring user activity against such security standards. Its objectives are to prevent unauthorized access, detect suspicious activity, and reduce the consequences of a possible violation. Organizations can take better security measures to protect their sensitive information, remain compliant with their regulatory requirements, as well as defend against insider and external security threats through PAM cybersecurity.
To learn about different Network Address Translation techniques, sign up for our Cyber Security online training right now!
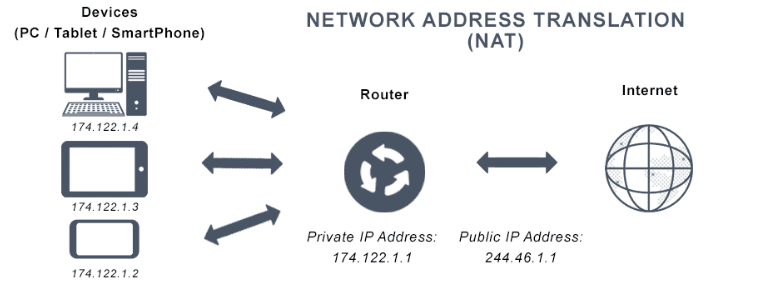
How Network Address Translation (NAT) Works
NAT works by converting the private IP addresses of the internal devices into public IP addresses when traffic goes out to the Internet. Similarly, when responses are received from external networks, the NAT device converts the public IP address back to the corresponding private IP address and routes the traffic to the appropriate internal device.This process is essential for maintaining the functionality of a network, especially in a world where IPv4 addresses are limited. To fully understand how NAT interacts within a network, it’s important to also consider Network Topology refers to the arrangement of various elements (such as devices, nodes, and connections) in a computer network.
- Outbound traffic: A device in the private network, such as a computer, sends a request to access an external resource, such as a website. The router, which supports NAT, replaces the computer’s private IP address with a public IP address.
- Inbound traffic:When the external server responds, the response is routed to the public IP address. The router then converts the public IP address back to the privateIP Masquerading address of the internal device and routes the response to it. This translation process allows multiple devices in the private network to access the Internet while appearing to have the same public IP address, making it a powerful tool for managing network traffic.
- Static NAT: Static NAT, also known as one-to-one NAT, is the simplest form of NAT. It creates a permanent mapping between a private IP address and a public IP address. This means that whenever the internal device sends a request to the Internet, the router will always use the same public IP address for that device when a particular device in the private network is always to be accessed from the Internet, such as a web server or an email server. Useful for hosting services that require a fixed IP address.
- Dynamic NAT:Dynamic NAT enables many-to-many address translations. It uses a pool of public IP addresses, and one private IP is mapped to any available public IP address in that pool. With Static NAT, the mapping is not permanent. Over time, one connection closes, or the mapping is gone over. The internet IP Masquerading can be assigned to another private IP in dynamic NAT. Most gadgets are for the Internet, but only a few public ips are available in Zero Trust Security. The internal machine does not require constant public IP mapping.
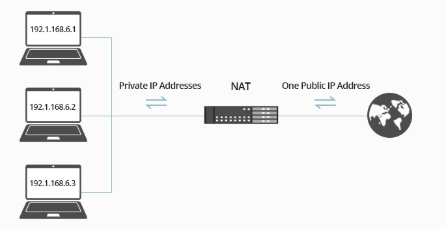
- Port Address Translation:Port Address Translation, also known as NAT Overload or many-to-one NAT, is the most prevalent type of NAT. Multiple private IP addresses in PAT share a common public IP address; however, each request is individually identifiable by its port number. This enables many internal devices to access outside networks using a public IP address. It is most commonly used in home networks and small offices, where multiple devices need to access the Internet through one public IP address. Enables a large-scale deployment of devices with limited public IP addresses.
- IP Address Conservation:NAT minimizes organizations’ need to acquire large public IP addresses. It saves a limited number of IPv4 addresses.
- Better Network Security: NAT conceals internal IP addresses and limits unauthorized access from external sources and cyberattacks.
- Flexibility in Network Architecture: NAT facilitates flexible designs in which any internal device can use any private IP range while accessing external resources.
- Support of multiple devices: NAT enables hundreds or thousands of devices in a private network to access the Internet using a single public IP address, Resolution Protocol an essential requirement in large organizations and residential networks.
- Ease of Scalability: As companies expand, NAT allows the networks to scale freely without needing extra public addresses, especially in IPv4-scant environments.
- Hiding Internal IP: NAT prevents external systems from accessing the devices inside the local network directly, thus concealing them from external threats.
- Blocking Direct Access:Without using NAT, external users could, for instance, access individual servers or workstations holding public IPs. With NAT, all traffic from the outer side must pass through the router or a firewall that can inspect or filter the traffic.
- NAT Translation Failures:This may happen if the router or firewall cannot correctly translate the internal private IP addresses to the public IPs. Configuring the NAT table usually corrects the problem.
- Port Forwarding Failures: Static NAT and PAT sometimes suffer from port forwarding issues when accessing services from outside users. Make sure port forwarding is properly set in the NAT settings.
- Overloaded NAT:When too many devices try to use the same public IP, NAT becomes overloaded, and connections become slow, or packets get dropped. Increasing the number of available public IPs, Address Resolution Protocol or optimizing port allocation may help.
- Application-Specific Issues: Some applications, such as VoIP or online gaming, will have problems with NAT because they handle incoming and outgoing traffic differently. Thus, configuring NAT to support particular application requirements or using UPnP can help solve this problem.
Sign up for ACTE Cyber Security online training and get a head start in your career Network Address Translation
Types of Network Address Translation
There are different types of Network Address Translation and their use cases, each with its use case. Now, the three commonly used types are categorized as static NAT, Dynamic NAT, and Port Address Translation (PAT).
Why is NAT Important in Networking?
Conservation of Public IP Addresses NAT solves the problem of IPv4 address exhaustion by allowing multiple devices in a private network to access the Internet through a single public IP address. Translating private IP addresses to public ones will enable organizations to have internal networks that are inaccessible on the Internet. Cybersecurity Training Courses enhances security and effective address management.Improved Security NAT also assists in hiding a network’s internal structure, making it more difficult for attackers to access specific devices inside the private network. This provides another layer of protection between internal systems and the public Internet. NAT simplifies the management of IP addresses in large networks, allowing internal devices to use private IP addresses without requiring a unique public IP for each one.
Leverage Network Address Translation to Unlock the Future! Enroll in the cybersecurity expert masters program Program at ACTE Right Away.
Advantages of Using Network Address Translation
NAT and Security: How It Benefits Network Security
One of the main security benefits of Network Address Translation is that it acts as a firewall. When communicating over the Internet, Encryption in Network Security NAT translates the private IP addresses of internal devices into a public IP address, hence masking the identity of a device, making it much harder for an external attacker to target specific machines.
Key security features of NAT:
While NAT offers some level of security, it should not be the only defense mechanism. Other forms of security, such as firewalls, IDS, and strong encryption techniques,should complement NAT.
Get interview-ready with our collection of Cybersecurity Interview Questions and Answers Questions. Equip yourself with the knowledge to impress potential employers!
Common NAT Issues and Troubleshooting
Although NAT is a very effective tool for managing network traffic and enhancing security, it does pose some challenges. Some of the common issues and troubleshooting tips are given below:
Conclusion
Network Address Translation, also known as NAT, is a very important technology in networking that addresses key challenges such as IP address shortages, network security, and traffic management. Thus, understanding the different types of NAT, how it works, and its benefits enables network administrators to design efficient, secure, and scalable network infrastructures for both small and large-scale deployments. Additionally, to effectively manage and secure network infrastructures, Cybersecurity Training plays a vital role. With the growing complexities of modern networks, continuous cybersecurity education is essential to stay ahead of emerging vulnerabilities and ensure a resilient network environment.





