
- Introduction to the Playfair Cipher
- History and Development of Playfair Cipher
- Key Generation in Playfair Cipher
- Encryption Process of Playfair Cipher
- Decryption Process of Playfair Cipher
- Example of Playfair Cipher with a Keyword
- Limitations and Security of Playfair Cipher
- Conclusion
The Playfair Cipher is a classical encryption technique that encrypts pairs of letters (digraphs) rather than individual letters, making it more secure than simple substitution ciphers. Developed by Charles Wheatstone in 1854, it uses a 5×5 grid of letters constructed from a keyword or phrase. Each letter of the plaintext is replaced by another letter based on its position in the grid. If a pair of letters appears in the same row or column, they are substituted by others from the same row or column. This method can be used in Cyber Security Training Courses to enhance cryptographic understanding and application of various encryption techniques. If not, each letter is replaced by the one in the same row but in the column of the other letter. This method introduces a level of complexity, making it harder to break compared to simpler ciphers.
Interested in Obtaining Your Playfair Cipher Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Introduction to the Playfair Cipher
The Playfair Cipher is a manual symmetric encryption algorithm that encrypts pairs of letters in a message. It was invented in 1854 by Charles Wheatstone but popularized by Lord Playfair, hence the name “Playfair Cipher.” The cipher is notable for being one of the first to encrypt digraphs (pairs of letters) rather than individual letters, making it more secure than simple substitution ciphers like the Caesar Cipher. This technique is an early example of encryption methods that help protect sensitive data, a concept that is increasingly relevant in the context of Ransomware In Cybersecurity, where strong encryption is crucial for preventing unauthorized access to critical information. The Playfair Cipher uses a 5×5 grid of letters constructed from a keyword, with the letters of the alphabet arranged in a specific order. The basic idea is to replace pairs of letters in plaintext with other pairs of letters, ensuring that encryption is more complex than single-letter substitution. The cipher is more difficult to break than simpler ciphers, though it still has some inherent vulnerabilities.
Key Generation in Playfair Cipher
The key for the Playfair Cipher is a keyword or phrase that is used to generate the 5×5 grid. The grid is filled with the letters of the alphabet in a particular order, using the keyword to populate the grid first, followed by the remaining letters of the alphabet, excluding duplicates and the letter ‘J’ (since the grid only contains 25 spaces). This method of encryption is an important concept in Encryption in Network Security, where understanding the foundations of classical ciphers helps to build knowledge of more advanced encryption techniques used to protect data in networks.
Key Generation in Playfair Cipher
- Remove duplicates from the keyword. If the keyword is “KEYWORD,” then duplicates like the second “E” are removed.
- Combine the remaining unique letters from the keyword with the rest of the alphabet, omitting ‘J’ to ensure there are only 25 characters in total.
For example, for the keyword “KEYWORD”, the grid would look like this:
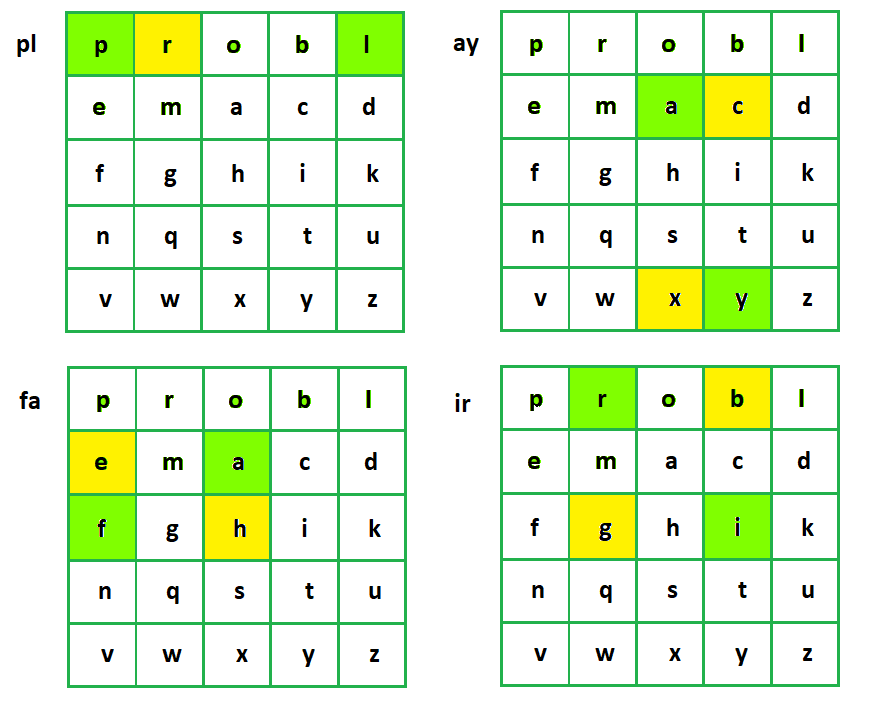
In this example, ‘J’ is omitted, and the remaining letters are placed in the grid after the keyword.
History and Development of Playfair Cipher
The Playfair Cipher was developed by Charles Wheatstone in 1854, although it gained prominence after being promoted by Lord Playfair, a British statesman, during the late 19th century. Wheatstone originally designed the cipher to be used for secure communications among British officials, as a stronger alternative to simpler ciphers in use at the time. The method was not widely adopted until it became known as the Playfair Cipher, after its association with Lord Playfair, who introduced it for military use in the 20th century. Understanding such historical encryption methods can provide valuable insights into the evolution of cybersecurity, especially with the rise of AI in Cybersecurity, where modern technologies now leverage artificial intelligence to enhance encryption, detection, and threat analysis. Despite its novelty, the cipher was eventually superseded by more advanced encryption methods such as the Vigenère Cipher and, later, modern cryptographic systems. However, it remains a foundational concept in the history of encryption.
To Earn Your Playfair Cipher Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Encryption Process of Playfair Cipher
Once the 5×5 grid is constructed using the keyword, the encryption process involves converting the plaintext into digraphs (pairs of letters) and applying specific rules based on their positions in the grid. This concept is often covered in Cyber Security Training Courses, where students learn how to implement and analyze classical ciphers before moving on to more modern encryption methods.
Steps for encryption- Divide the plaintext into pairs of letters. If a pair contains identical letters (like “EE”), a filler letter (usually ‘X’) is added between them. For instance, “HELLO” becomes “HE LX LO.”
For each pair, locate the letters in the grid and apply the following rules:
- If both letters are in the same row, replace them with the letters immediately to their right (wrap around to the beginning of the row if needed).
- If both letters are in the same column, replace them with the letters immediately below (wrap around to the top of the column if needed).
- If the letters are neither in the same row nor column, form a rectangle with the two letters and replace them with the letters in the same row but at the opposite corners of the rectangle (i.e., swap the column positions).
For example, using the grid from the previous section and the plaintext “HELLO”:
- The digraphs are “HE”, “LX”, and “LO”.
- Look up “H” and “E”: They are in the same row, so replace them with “F” and “Y”.
- Look up “L” and “X”: They form a rectangle, so replace them with “C” and “S”.
- Look up “L” and “O”: They are in different rows and columns, so replace them with “B” and “W”.
Thus, “HELLO” would be encrypted as “FY CS BW”.
Decryption Process of Playfair Cipher
The decryption process of the Playfair Cipher is essentially the reverse of encryption. The same 5×5 grid generated from the keyword is used, and the ciphertext is converted back into the original plaintext by reversing the steps. This process can be applied in contexts like High-Level Data Link Control, where secure communication protocols rely on effective encryption and decryption techniques to ensure the integrity and confidentiality of data transmission.
Steps for decryption:- Break the ciphertext into pairs of letters (digraphs).
- For each digraph: If both letters are in the same row, replace them with the letters immediately to their left (wrap around to the end of the row if needed). If both letters are in the same column, replace them with the letters immediately above (wrap around to the top of the column if needed). If the letters are neither in the same row nor column, form a rectangle with the two letters and replace them with the letters in the same row but at the opposite corners of the rectangle (i.e., swap the column positions).
- If there was a filler letter (like ‘X’) added during encryption to break identical pairs, remove it during decryption to reveal the original plaintext.
For example, given the ciphertext “FY CS BW” and the same grid as before:
- Look up “F” and “Y”: They are in the same row, so replace them with “H” and “E”.
- Look up “C” and “S”: They form a rectangle, so replace them with “L” and “X”.
- Look up “B” and “W”: They are in different rows and columns, so replace them with “L” and “O”.
Thus, “FY CS BW” would be decrypted back to “HELLO”.
Are You Considering Pursuing a Cybersecurity Master’s Degree? Enroll For Cyber Security Expert Masters Program Training Course Today!
Example of Playfair Cipher with a Keyword
Let’s work through an example with the keyword “SECRET” and the plaintext “HELLO”.
Key Grid Generation: The key “SECRET” gives the following 5×5 grid after removing duplicates and adding the remaining letters of the alphabet (omitting ‘J’)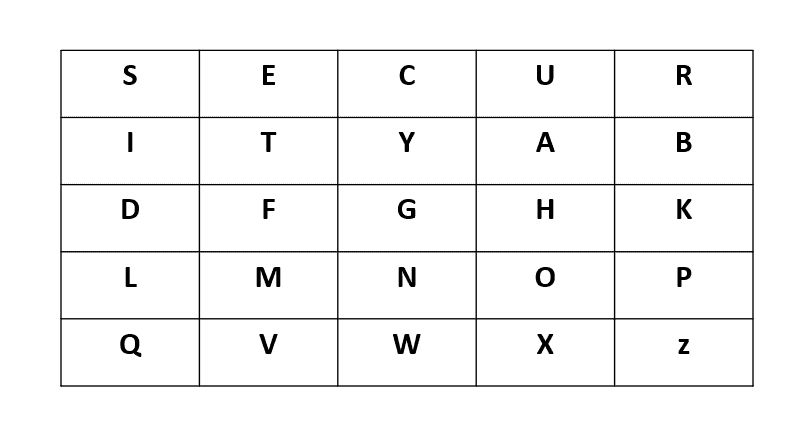
- “HELLO” becomes “HE LX LO”.
- Look up “H” and “E”: They are in the same column, so replace them with “I” and “B”.
- Look up “L” and “X”: They are in different rows and columns, so replace them with “K” and “W”.
- Look up “L” and “O”: They form a rectangle, so replace them with “I” and “P”.
Thus, the ciphertext becomes “IB KW IP”.
Want to Learn About Cyber Security? Explore Our Cyber Security Interview Questions and Answers Featuring the Most Frequently Asked Questions in Job Interviews.
Limitations and Security of Playfair Cipher
While the Playfair Cipher was a significant improvement over earlier ciphers, it has several limitations The key space is limited to 25 letters (excluding ‘J’), making it easier to guess with modern computing power. Because the Playfair Cipher operates on pairs of letters, it is still susceptible to frequency analysis, albeit to a lesser extent than single-letter ciphers. However, with the advent of Quantum Cryptography, the security of encryption systems has significantly improved, as quantum techniques offer more robust protection against such vulnerabilities by leveraging the principles of quantum mechanics. The Playfair Cipher is considered insecure for modern cryptographic applications because of its susceptibility to attacks like frequency analysis and known-plaintext attacks.
Conclusion
The Playfair Cipher, while historically important, is no longer used in modern cryptography due to its vulnerabilities. Its reliance on a 5×5 grid and the encryption of letter pairs makes it susceptible to various attacks, such as frequency analysis and known-plaintext attacks. Additionally, the cipher’s limitation of only 25 letters in the alphabet (due to the 5×5 grid) creates ambiguities, especially when dealing with letters like “J,” which are typically omitted or combined with other letters. These weaknesses render the Playfair Cipher inadequate against modern computational techniques used for cryptanalysis. It is an interesting cipher from a historical perspective, illustrating the development of encryption techniques before the advent of more secure methods like AES and RSA. Cyber Security Training Courses often explore these traditional ciphers to provide a foundational understanding of how cryptography has evolved over time. In its time, it was a significant step forward from simpler ciphers, offering a more complex encryption system that improved security. However, as cryptographic needs grew and technology advanced, the limitations of the Playfair Cipher became clear. Today, more robust encryption methods, which rely on mathematical algorithms and much stronger key systems, are used to protect sensitive data. Despite this, the Playfair Cipher remains a valuable part of cryptographic history, reflecting the early efforts to safeguard communication.





