
- Introduction
- What is Maze Ransomware?
- How does Maze Ransomware work?
- Maze Ransomware Website
- The Root Cause
- Maze Ransomware Examples
- Protection Against Maze Ransomware Attacks
- Conclusion
Maze ransomware is a highly sophisticated cyber threat that first emerged in 2019, known for its dual extortion tactics. It encrypts victims’ files and demands a ransom for decryption, while also stealing sensitive data, threatening to release it publicly if the ransom is not paid. To defend against such attacks, Cyber Security Training Courses are essential in educating employees on recognizing ransomware threats and implementing proactive security measures to minimize risks. The impact of Maze ransomware is significant, as it affects organizations of all sizes, causing data breaches, financial loss, operational disruption, and reputational damage. Its use of advanced techniques, such as exploiting vulnerabilities and leveraging the “big-game hunting” approach, has made it one of the most dangerous and effective ransomware strains in recent years.
Are You Interested in Learning More About Maze Ransomware? Sign Up For Our Cyber Security Online Training Today!
Introduction
Maze ransomware operates through an affiliate model, where the core group of developers collaborates with other cybercriminals who deploy the ransomware across different networks. These affiliates are typically compensated with a percentage of the ransom paid by the victims. This decentralized approach allows Maze operators to extend their reach and maximize their impact, as the affiliates handle the distribution of the malware while the core group focuses on developing and refining the ransomware’s capabilities. To defend against such attacks, Vulnerability Scanning is essential in identifying weaknesses in systems that could be exploited by ransomware operators. This partnership-based structure has made Maze highly efficient in targeting organizations across various sectors globally. One of the most concerning aspects of Maze ransomware is its ability to move laterally within a compromised network. Once it gains access to one part of an organization’s infrastructure, it leverages the stolen credentials or vulnerabilities to propagate across other systems. This lateral movement allows the ransomware operators to maximize their ransom potential by encrypting and stealing more data, thus increasing the likelihood that the organization will pay to regain access. The added threat of data leakage, if the ransom is not paid, amplifies the pressure on organizations to comply with demands. This tactic not only disrupts operations but can also lead to long-term reputational damage, as the fear of public exposure of stolen sensitive information looms.
What is Maze Ransomware?
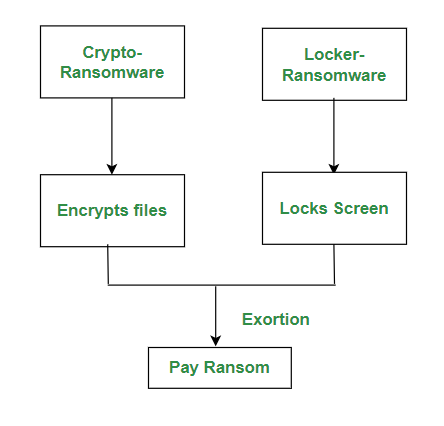
Maze Ransomware is a form of Windows ransomware that needs to be charged in cryptocurrency as an alternative for the secure recovery of encrypted data breach. It is one of many Malware Attacks that specifically target vulnerabilities in systems to extort victims for financial gain while also potentially stealing sensitive information. If the charge is refused with the aid of using any victim, the criminals leak all their private data.
Similar conduct is increasingly visible in more recent styles of ransomware. If the affected company is an IT offerings provider, it opens up an entire new container that catalyzes similarly assaults at the masses of clients that depend on those IT offerings.
Interested in Obtaining Your Maze Ransomware Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
How does Maze Ransomware work?
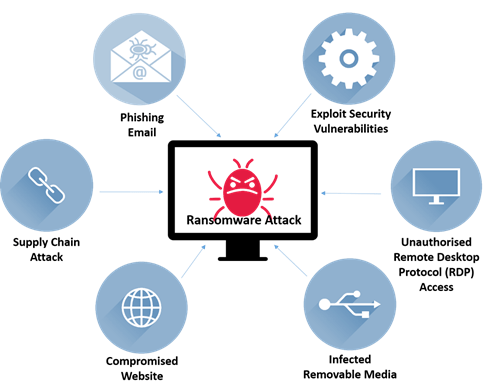
The distribution of Maze is commonly achieved through unsolicited mail emails with malicious hyperlinks or attachments, Remote Desktop Protocol (RDP) brute pressure assault, or with the aid of using the use of take advantage of kit.There are instances when the assault comes from an organization`s companions or customers who’ve fallen sufferers to hackers.Once Maze has gotten entry to a network, gaining accelerated privileges is the following goal so that document encryption may be deployed throughout all drives. Since Maze additionally steals statistics and data, leaking them to servers that are managed by hackers, it is even more risky as sufferers may be threatened primarily based on this. Threat Intelligence plays a crucial role in identifying such malicious activities and providing early warnings to organizations, helping them prevent data breaches and minimize the impact of such attacks. Although it’s far feasible to repair the statistics from a steady backup furnished the backup has now no longer been compromised, it nonetheless doesn`t do any to ensure that the attackers now have a duplicate of the statistics. Maze can essentially, be taken into consideration as a mixture of a statistics breach and a ransomware assault.Let’s review the techniques used by Maze Ransomware.
- Initial Access: In maximum cases, Maze operators use legitimate credentials to log in to the community with the assistance of internet-dealing servers (both RDP or a Citrix/VPN server). Although how the preliminary credential became compromised isn’t always known, the usual methodologies encompass guessing susceptible passwords or spear-phishing and Ransomware the use of emails containing malicious macros.
- Reconnaissance: Once a device in a community is compromised through malware, the entire community is scanned for vulnerabilities. It scans the community configuration, open SMB shares, money owed, area trusts, permissions, and different diverse Active Directory attributes. The scans are sometimes, finished with famous open-supply gear like BloodHound, Adfind, smbtools.exe, and PingCastle in addition to integrated Windows commands.
- Lateral Movement/Credential Access: Maze malware initially gathers intelligence before spreading within the network to steal credentials. It searches for plaintext passwords and uses LLMNR/NBT-NS poisoning for NTLM attacks. If unsuccessful, it attempts brute-force attacks to crack weak passwords. Once valid credentials are found, it exploits Windows services like WinRM, SMB, and RDP for lateral movement.
- Privilege Escalation: Privilege escalation includes the attacker transferring laterally to new machines and alternatively the use of identical strategies, locating new credentials to compromise and flow to different machines. Once area admin credentials are observed, this form of lateral motion stops. At this point, any device inside the community may be compromised.
- Persistence: The malware operator attempts to preserve its presence inside the community for as long as feasible. This is feasible through including diverse backdoors and passages. This allows retake manipulation of the community in case the malware is detected and removed. Maze particularly captures as many consumer credentials as feasible and creates new privileged money owed inside the community.
Maze Ransomware Website
The creators of the Maze Ransomware host an internet site in which they list their sufferers (or “customers”). This internet site regularly has posted samples of facts that is stolen. It consists of info on the date that sufferers have been hit by the assault, in addition to the hyperlinks to the stolen facts and files that can be downloadable as a “trophy.” To protect against such breaches, Cyber Security Training Courses can help individuals understand how to safeguard sensitive data and recognize signs of potential threats. Ironically, the internet site functions the slogan “Keeping the arena safe” and plenty provocatively consists of sharing alternatives on social media to percentage info of the facts breaches.
Maze Ransomware internet site warns sufferers that they will:- Make the safety breaches public and tell the media
- Sell the stolen facts that have industrial price at the darkish web
- Inform inventory exchanges approximately the breach and force down the proportion fee of the enterprise
- Target the customers and companions of the enterprise in addition to notifying them of the assault
The Root Cause
- Most of the time, those malicious activities are completed by the usage of legitimate user credentials obtained through various means.
- To prevent this, a strong understanding of Cybersecurity and Data Science is essential, as it helps in analyzing attack patterns and detecting anomalies that could indicate compromised credentials or malicious activity.
- Maze objectives passwords in neighborhood drives and sometimes, it compromises debts that have vulnerable passwords through the usage of brute pressure and credential scanning methods.
- Implementing multi-factor authentication (MFA) adds an extra layer of security, making it harder for attackers to gain access even if credentials are compromised.
- Conducting regular security audits helps organizations identify vulnerabilities and mitigate risks before they can be exploited.
- Educating users about phishing tactics and safe password practices significantly reduces the chances of credential theft.
- Having up-to-date software programs and running structures is vital to assist guard structures and networks from malware. Any new patches and updates for software programs, net browsers, and browser plugins must continually be carried out as soon as released. This makes it more difficult for cybercriminals to make the most vulnerable and assault the system.
- A holistic net protection answer can guard computer systems in opposition to ransomware. During downloads or streams, the safety software program will save you inflamed documents and ransomware from infecting the laptop thus, maintaining hackers at bay.
- Instead of disclosing your Remote Desktop Protocol (RDP) to the net, it is an ideal exercise to apply a VPN to get the right of entry to the network. It looks after online privateness similarly to providing get right of entry to to international content.
- Making an addiction to frequently backing up records to an offsite, stable vicinity is what could make the recuperation of stolen records convenient. In case ordinary guide backup appears unreliable, there are approaches to perform the equal through computerized backups. It doesn`t cease there. Backups must additionally be frequently examined to make sure that the records are being stored effectively and routinely.
- Organizations must continually make sure that their group of workers is knowledgeable approximately the strategies that hackers use to infiltrate organizations. All personnel must be taught and knowledgeable on the subsequent satisfactory practices of cyber attack prevention.
- Never start e-mail attachments from unknown senders and assess whether or not they appears authentic earlier than starting it. Avoiding clicking hyperlinks connected to unsolicited mail emails or unexpected websites.
- Avoiding software programs or media document downloads from unknown websites. Never receiving calls, texts, or emails from untrusted reasserts that ask for private information. Using endpoint protection collectively with conduct detection and automated document rollback.
- Only the use of stable era for faraway connections in an organization`s neighborhood network. Enabling multi-aspect authentication. Strong passwords for the safety of bills and touchy information. Encryption of all touchy records anywhere possible.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Maze Ransomware Examples
One of the maximum famous Maze ransomware assaults became the only one that centered on Cognizant. This Fortune 500 large became attacked and offerings to its clients had been disrupted as a result. The assault encrypted and disabled a number of its inner structures and pressured it to take different structures offline. The Cognizant assault came about for the duration of the Covid-19 pandemic whilst everybody became operating remotely. The malware disrupted laptop structures that supported digital computer infrastructure making it hard for the personnel to work. The assault deleted Internal directories and e-mail get admission to became misplaced as well. In the spot aftermath of the Maze Ransomware assault on Cognizant, the employer misplaced between US$50,000,000 and US$70,000,000. There had been similarly incurred prices for the complete recovery of its laptop structures. Pensacola, Florida was attacked with the aid of using Maze Ransomware on the quit of 2019. The organization held the stolen statistics in opposition to a ransom of US$1,000,000. More than 32GB of statistics were claimed to be stolen from the city`s structures. As evidence of the assault, they leaked 2GB of statistics.
Protection Against Maze Ransomware Attacks
The aspect about Maze Ransomware or any other cyber extortion threat for that matter is that it evolves. The best protection against an evolving threat is proactively taking precautions and having preventive measures in place. Utilizing resources like the Google Hacking Database can help identify potential vulnerabilities that attackers might exploit, enabling organizations to patch them before they can be used in an attack. It is frequently too past to get over encrypted statistics with the aid of using malware or hackers. Here are some guidelines for stopping ransomware assaults:
Preparing for a Cyber Security Job Interview? Check Out Our Blog on Cyber Security Interview Questions and Answers
Conclusion
At the quit of 2020, the Maze Ransomware institution asserted that they were no longer going to perform anymore and that they would no longer replace their website.All the sufferers who desired their records eliminated may want to reach out via their aid chat. However, to prevent falling victim to such attacks in the first place, Cyber Security Training Courses are crucial in teaching individuals how to recognize and avoid malicious threats like ransomware. They claimed that it became all a try and enhance the focus of cyber security. Regardless of whether or not they certainly disbanded or could cross directly to morph into every other crook institution, the ransomware hazard will usually be trouble and all measures have to be in location to save you from attacks.





