
- Introduction
- What is Cyberstalking?
- Cyberstalking Examples
- Consequences of Cyberstalking
- Difference between Cyberstalking and Cyberbullying
- How to avoid Cyberstalking?
- Types of Cyberstalking
- Conclusion
In case of calls from banks or credit score card companies, confirm with the headquarters or department given in your paperwork. Securing your records will now no longer assist you in case your tool is hacked. To save you from Cyberstalking, make certain fundamental safety for your online life. Use public Wi-Fi cautiously as it may be hacked easily. Use a digital non-public community (VPN) to cover your IP cope with and different information Cybersecurity Training Courses. Do now no longer maintain your gadget’s mendacity around carelessly as a person can also additionally take the possibility to put in spyware. All gadgets need to be password-covered and up to date regularly. Use anti-spyware. Always log off of online accounts. Beware of apps that need to get the right of entry to your Facebook or contacts list.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Introduction
Cyberstalking is a kind of cybercrime that makes use of the net and era to bother or stalk an individual. It may be taken into consideration as an extension of cyberbullying and in-individual stalking. However, it takes the shape of textual content messages, e-mails, social media posts, and different mediums and is frequently persistent, deliberate, and methodical. Cyberstalking frequently begins offevolved with apparently innocent interactions that cross directly to grow to be systematic disturbingly or scarily. Some even locate the preliminary degree of Cyber Hygiene to be fun and innocent, however, it stops being a laugh anymore whilst the interactions no longer stop even after the recipient has expressed their displeasure and requested for the interplay to stop. The content material this is directed at the sufferers is frequently beside the point and disturbing.
What is Cyberstalking?
A cyberstalker may terrorize a sufferer via means of sending messages numerous instances an afternoon and from one-of-a-kind accounts. Cyberstalking always contains direct communication, and a few sufferers might not even understand that they’re the sufferers of online stalking. The sufferers may be monitored through numerous strategies and the records accrued may be later used for crimes along with identification theft. Some stalkers even cross some distance by harassing the sufferers offline nicely or even contacting their friends. Some unusual traits of Cyberstalking conduct are monitoring locations, breaching statistics privacy, tracking online and real-global activities, obsessively monitoring the sufferers` whereabouts, intimidating sufferers, etc. Social media stalking may also consist of sending threatening personal messages or faking photos. Oftentimes, cyberstalkers make fake accusations, unfold malicious rumors, create faux social media profiles or blogs, or create and post revenge porn. There is probably a misperception that as it no longer contains bodily contact, Cyberstalking isn’t as extreme because of the bodily shape of stalking. This isn’t actual in any case. The net has grown to be a vital part of the whole thing that we do, be it private or professional. This has simplest eased how communications take area alongside the elevated admission to private records.
Cyberstalking Examples
Cyberstalkers use a whole lot of processes and strategies to humiliate, harass, control, and intimidate their victims. Many cyberstalkers are technologically savvy in addition to innovative in their ways.
Here are a few examples of ways Cyberstalking may take place:- Posting offensive, suggestive, or impolite feedback on-line. Sending threatening, lewd, or offensive emails or messages to the sufferer.
- Joining identical businesses and boards because the sufferer. Releasing the sufferer`s private statistics online.
- Tracking all online actions of the sufferer via monitoring devices. Using era for blackmailing or threatening the sufferer.
- Excessively tagging the sufferer in inappropriate posts. Engaging with all online posts made via the way of means of the sufferer.
- Creating faux profiles on social media to observe the sufferer. Posting or dispensing actual or faux pics of the sufferer.
- Excessively sending express pics of themselves to the sufferer. Making faux posts supposed to disgrace the sufferer. Repeatedly messaging the sufferer. Ethical Hacking Techniques into the sufferer`s online accounts.
- Attempting to extort express pics of the sufferer. Sending undesirable items or objects to the sufferer. Using hacking equipment to get into the sufferer`s computer or telephone digital digicam and secretly report them. Continuing harassment even after being requested to stop.
- In Cyberstalking, the sufferer is stressed online via digital verbal exchange gadgets, on-the-spotaneous messaging, social networks, dialogue groups, etc., for the motive of revenge, anger, or control. A stalker can be a stranger or an acquaintance of the sufferer.
- Cyberbullying is common when a child, preteen, or youngster-ager is stressed, humiliated, tormented, threatened, embarrassed, or centered via the internet, interactive and virtual technologies, or Digital Forensics gadgets with the aid of using some other man or woman of the equal age range. If adults are involved, it’s worth taking cyber-harassment or cyberstalking into consideration.
- Cyberbullying occurs in a repeated, deliberate, and adverse manner. It may be as easy as time and again sending emails, texting, or harassing someone. Cyberbullying may also involve Repeated public threats Hate speech, pejorative labels, or defamatory fake accusations. Ganging up on a sufferer with the aid of ridiculing them in online boards and discussions. Hacking into or vandalizing websites and posting fake statements approximately a sufferer to discredit or humiliate them. Identifying sufferers of crime individually and publishing content material intended to seriously defame or humiliate them. Posting rumors approximately the sufferer online to persuade others to dislike or take part in their online denigration
- Catfishing The introduction of faux profiles or copying of current ones on Social Engineering to technique victims. Monitoring check-ins on social media. Keeping an eye fixed on the sports of a sufferer on social media to appropriately gauge their conduct pattern. Spying through Google Maps and Google Street View. Using Street View to secret agent on a sufferer and locate their vicinity from posts or pictures on social media.
- Hijacking webcam Webcams may be hijacked via way of means of introducing malware-inflamed documents into the sufferer`s computer. Installing stalkerware Stalkerware tracks the vicinity, permits admission to texts and surfing history, makes audio recordings, etc., without the sufferer`s knowledge.
- Tracking vicinity with geotags Digital images in the main have geotagged with the time and vicinity of the image if it’s miles inside the metadata format, which makes it simpler for stalkers to get admission to those facts via way of means of the use of unique apps.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training .
Consequences of Cyberstalking
Cyberstalking isn’t any more distinct than stalking and ends in results that may be damaging to the sufferers both bodily and mentally. Victims who are stressed online enjoy fear, anger, confusion, and insomnia as a side of different fitness issues. Cyberstalking impacts the general health of sufferers. They regularly are afflicted by anxiety, distress, depression, PTSD, and suicidal ideation. If you’re experiencing Cyberstalking, it’s crucial that you seek help. You can contact a loved one, see an intellectual fitness professional, search for prison help, or maybe report a police grievance against the stalker in case you assume you are in spontaneous danger.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Difference between Cyberstalking and Cyberbullying
Here you’ll recognize what cyberbullying and Cyberstalking are and the variations among Cybersecurity Training Courses .
How to avoid Cyberstalking?
Increasing your privacy settings is the primary factor to save you from Cyberstalking. Enable sturdy privateness settings Make all posts viewable to pals most effectively so that no strangers can see them. Do now no longer permit permissions for social networks to publish your touch information publicly. Try to have a separate e-mail to cope with social media and different online activities. Share non-public facts with pals over a non-public message as opposed to a public publish. Avoid the usage of your actual call and use a gender-impartial display screen call or pseudonym as a substitute for your social media accounts. Leave elective fields in social media profiles blank. Only be given pal requests from the ones you understand in person. Set your social community settings to just accept pal requests most effectively from pals of pals. Disable geolocation settings and GPS in your tool. Remove all private records this is on the web. You can also additionally reach out to third-birthday birthday celebration Website Server to get a number of the records taken down. In case you want to have a postal cope with for commercial enterprise purposes, use a publish container cope with or workplace cope with and now no longer your private cope with. The nice safety degree isn’t giving out your complete call online, most effective on your first call. Beware of calls or emails that ask for private facts, but affordable the request can also additionally seem.
Ready to pass the interview for cybersecurity ? Learn how to answer Cybersecurity Interview Questions and Answers .
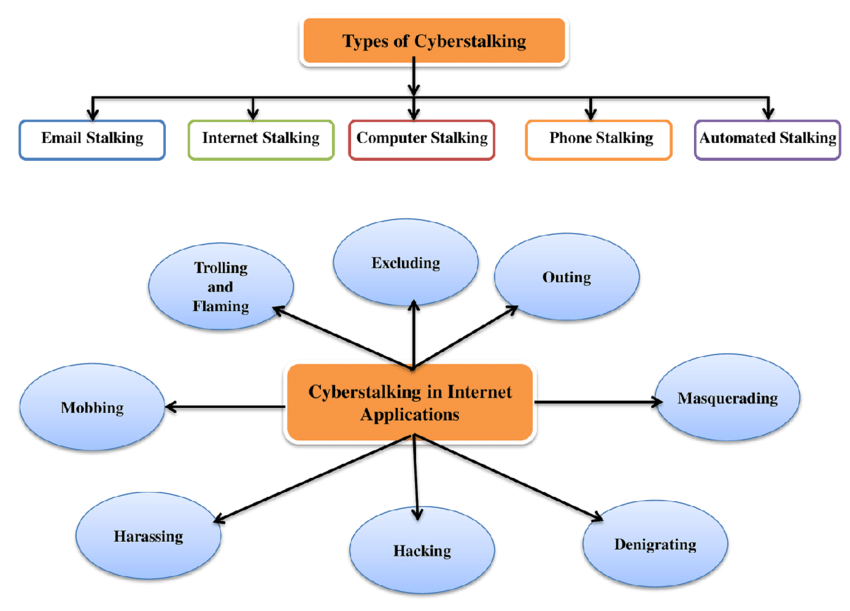
Types of Cyberstalking
Let us discover the numerous varieties of Cyberstalking which can be prevalent
Conclusion
Cyberstalking is a pervasive and dangerous crime that substantially influences individuals` mental, emotional, and bodily well-being. As the era keeps evolving, so do the techniques used via way of means of cyberstalkers, making it important for individuals, organizations, and governments to live vigilant. Educating the general public approximately on online safety, imposing sturdy cybersecurity measures, and implementing stricter felony frameworks are critical steps in mitigating this issue. Victims of Cybersecurity Training have to be recommended to are seeking for assist and file incidents without worry of stigma or reprisal. By fostering a subculture of duty and support, society can paintings toward growing more secure virtual surroundings for everyone.





