- Introduction: What is Threat Intelligence?
- Types of Threat Intelligence
- Role of Threat Intelligence in Cybersecurity
- Tools and Platforms for Threat Intelligence
- Integration of Threat Intelligence into Your Security Operations
- The Future of Threat Intelligence in Cybersecurity
- Conclusion
This is in a world that continuously evolves, where cyber security threats changes, and foreseeing and mitigating threats is essential. Among the most potent tools in this arsenal is Threat Intelligence the practice of gathering, analyzing, and acting on information about potential or existing cyber threats. One valuable resource in this field is the Google Hacking Database, a collection of advanced search queries that can be used to find sensitive or vulnerable information exposed on websites. It enables organizations to avoid attackers, respond effectively to incidents, and continually improve their security posture. But what are cyber threat intelligence feeds, and how do they work in the broader cyber intelligence context? Let us delve into the intricacies of this critical discipline, its types, tools, and role within an integral cybersecurity strategy.
To Earn Your Threat Intelligence Certification, Gain Insights From Leading Cyber Security Experts And Advance Your Career With ACTE’s Cyber Security Online Training Today!
Introduction: What is Threat Intelligence?
Predicting and blocking threats is highly valued in today’s evolving cyber security trends world. In fact, Threat Intelligence can be considered one of the strongest tools in an organization’s arsenal. It helps it stand ahead of attackers, respond precisely to incidents, and continually improve its security posture by gathering, analyzing, and acting on information related to potential or actual cyber threats.
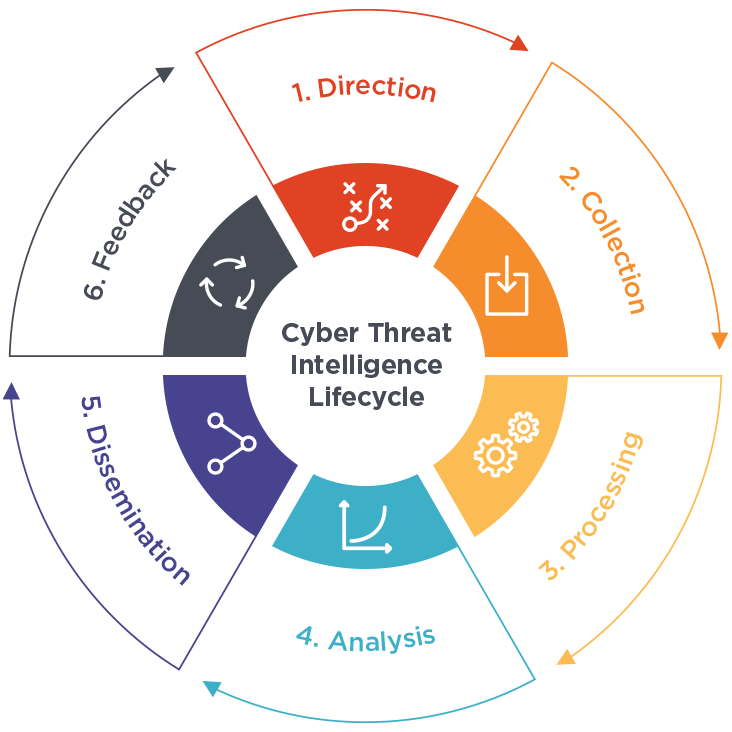
But what exactly is Threat Intelligence, and in what way does it function in the larger scheme of Cyber Security Training Courses? Let’s take it into the minutiae of this most vital discipline, its varieties, the tools used, and its role in a comprehensive cybersecurity strategy. At its core, threat intelligence helps organizations make informed decisions based on real-time data and past incidents, offering a clearer understanding of who is targeting them, why, and how. Doing so shifts security intelligence from a reactive stance to a proactive one. Organizations can anticipate cybercriminals’ next moves by analyzing emerging threat trends, understanding attacker behaviours, and strengthening their defences accordingly. This foresight improves detection and mitigation strategies and empowers businesses to allocate resources more effectively, streamline incident response, and reduce the overall impact of cyber attacks.
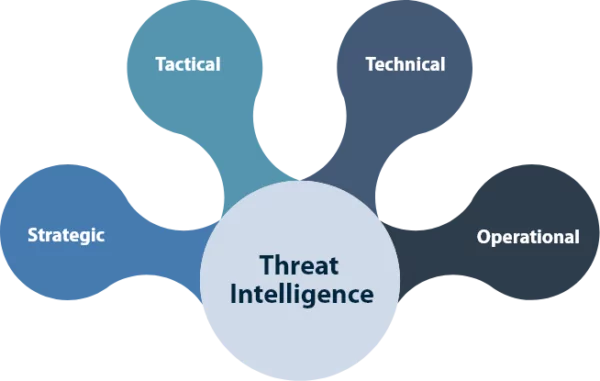
Types of Threat Intelligence
- Not all threat intelligence is the same. In fact, there are several different types, each providing a unique view of potential threats. A true grasp of the types is essential in tailoring the right threat intelligence feed strategy for an organization’s needs. Strategic intelligence focuses on a bird’ s-eye view; it is top-level information that helps senior management understand a larger part of the threat landscape. It includes insights about threat actors’ motives, capabilities, and trends, and it often involves geopolitical and economic factors that can influence an organization’s security posture.
- Strategic intelligence is less about specific threats than overall risk assessment and planning. Suppose a state-sponsored group targets organizations in your industry due to political tensions. In that case, strategic intelligence gives the context, and your organization could prepare and shift its focus on security.
- Tactical intelligence provides information about the TTPs (Tactics, Techniques, and Procedures) that attackers are using. It’s much smaller in scope than strategic intelligence and can directly inform day-to-day operations. For example, understanding the methods behind phishing attacks or malware propagation can help security teams implement specific defenses.
- Operational intelligence focuses on specific threats against an organization, such as ongoing attacks or active campaigns targeting its network. With the growing presence of the Internet of Things , operational intelligence has become even more crucial. IoT devices, often overlooked in security strategies, can become entry points for cyber attackers. By integrating operational intelligence into monitoring systems, organizations can detect threats targeting both traditional and IoT-based infrastructure, ensuring a more comprehensive defense against emerging cyber risks.
- Operational threat intelligence feeds provide immediate, real-time information about active cyber threats or campaigns that could directly influence an organization. In operational intelligence, for example, your IOCs could include malicious IP addresses, file hashes, or URL patterns used by attackers. Notifying your company’s domain that a phishing attack is targeting it falls under operational threat intelligence feeds, allowing quick response.
- This is technical information as far as the details of a threat are concerned. This type of data includes details relating to file hashes, IP addresses, URLs, malware samples, and technical indicators. Technical intelligence allows security analysts and teams handling incident response to identify, block, and analyze threats. Security tools can identify and neutralize new threats quickly because they have reported on new zero-day vulnerabilities or specific malware hash values.
- In that light, the best way to integrate effective threat intelligence feeds into operations is to have a robust framework for intelligence sharing, collaboration, and incident response.
- An independent and dedicated threat intelligence team will enable you to gather information, analyze it, and act on threat data. After that, analysts, researchers, and engineers work in teams to translate data into strategies that help curb risks at their emergence.
- Threat intelligence feeds are deeply rooted in collaboration. Intelligence sharing across teams, sectors, and even external organizations maintains collective defense against evolving cyber threats. One effective way to leverage this shared intelligence is through the use of a Sandbox Environment.
- In reality, collaboration is augmented through platforms like ISACs or threat intelligence feeds sharing groups where organizations can share invaluable insights.
- After compiling and analyzing such information, it could be used to improve defences for example, by upgrading firewalls, establishing more monitoring tools, or equipping employees with an awareness of new threats.
- The routine adoption of threat intelligence feeds ensures that an organization’s security mechanisms remain in tandem with the changing nature of the threat landscape.
To Explore Threat Intelligence in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Role of Threat Intelligence in Cybersecurity
Improving Detection and Prevention
Such threat intelligence directly feeds the intrusion detection and prevention systems (IDPS), while organizations can improve their recognition of indicators of compromise in their systems, networks, and endpoints by incorporating threat intelligence feeds into security monitoring tools.
Incident Response Improvements
Incident response teams depend on such threat intelligence feeds regarding response to active Cyber Security Training Courses. The very moment an attack breaks in, information about the nature of that threat can help guide a response process. They allow IR teams to provide the necessary context on the threat actors, their methods, and how to contain and eradicate the attack. For instance, in an incident related to some known malware, the Threat Intelligence collected beforehand could help IR teams quickly identify the operation of the malware and what defences need to be bolstered.
Proactive Threat Hunting
While traditional security measures prefer firewalls and intrusion detection-threat hunting is proactive. Security teams are looking for potential threats that have not yet caused alarms. Therefore, this process is a threat-hunting activity that enables organizations to detect unknown dangers, such as still-undetected malware or malicious insider activity that can do significant harm. Security teams can identify many IOCs and tactics they may have yet to be aware of if they do steadfast scanning and analysis of the threat data.
Improving Risk Management
Organizations can better prioritize their defences by incorporating threat intelligence into their risk management strategies. Understanding specific threats’ likelihood and potential impact allows for a more informed approach to vulnerability management and resource allocation. Suppose this intelligence shows that. In that case, if a certain attack group specifically targets some sectors, an organization can ensure that all its assets are secured.
To Explore Threat Intelligence in Depth, Check Out Our Comprehensive Cyber Security Course To Gain Insights From Our Experts!
Tools and Platforms for Threat Intelligence
Organizations looking to use highly specific tools and platforms to aggregate, analyze, and act on threat data toto maximize its power.TIPs (Threat Intelligence Platforms) also enable organizations to manage central and consolidated intelligence information coming from many sources, offering features like data enrichment, correlation, and integration with other security tools such as SIEMs and firewalls. One of the key functionalities that TIPs support is Whitelisting the process of allowing trusted entities while blocking everything else. Some of the most popular TIPs are ThreatConnect, Anomali, and the open-source MISP platform. Security Information and Event Management (SIEM) solutions combine and analyze security event data from different sources by providing real-time log collection, threat intelligence feed integration, and incident detection. Leading SIEM solutions include Splunk, IBM QRadar, and LogRhythm. Endpoint Detection and Response solutions focus on monitoring and defending specific devices or endpoints. EDR solutions offer continuous activity monitoring, real-time threat detection, and automated responses. All of the leading EDR platforms, such as CrowdStrike Falcon and Carbon Black, bring on board threat intelligence feeds, as does SentinelOne, to supplement their capabilities to detect and respond to the threat. Together, these tools improve the threat detection powers, hasten the pace of the incident response, and enable proactive defence.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
Integration of Threat Intelligence into Your Security Operations
The Future of Threat Intelligence in Cybersecurity
Accordingly, the landscape of cyber threats has constantly changed, and so has the practice of threat intelligence feeds. In the near future, AI and ML will likely combine more noticeably into threat intelligence processes. They can automate data analysis, make predictive trends faster, and produce a higher accuracy in predictions. However, with the increasing sophistication of cyber attacks, collaboration will be much more important both inside and outside the organization. One critical area where collaboration can enhance security is Network Penetration Testing. Cybersecurity would rely on collaboration as a team effort, bringing information and expertise from different sources to outsmart adversaries. As cyber threats grow more complex, the need for real-time, adaptive cybersecurity strategies becomes even more critical. Integrating Artificial Intelligence (AI) and Machine Learning (ML) will likely play a pivotal role in the future of threat intelligence feeds. By automating the analysis of vast amounts of data, AI and ML can detect emerging threats faster, identify patterns across multiple datasets, and improve the accuracy of predictions. This will enable security teams to act swiftly and proactively, reducing incident response times. However, as cyberattacks become more sophisticated and targeted, more than relying on technology will be required.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
Now, threat intelligence feeds are no longer a luxury but a necessity in modern cybersecurity, wherein organizations may not only avoid cyber attacks but also recover better in case of a breach, all based on timely actionable insights into potential threats. In the complex scenario of today’s digital environment, proactive threat intelligence has become extremely important to stay one step ahead of cyber adversaries. With Threat Intelligence integrated into all aspects of a Cyber Security Training Courses strategy, organizations can meaningfully shore up their defences in a way they could not before. By integrating threat intelligence into daily operations, proactive threat hunting, real-time monitoring, or incident response, an organization continue learning from the constantly shifting threat landscape. Businesses will react to attacks and anticipate them, reducing risks and further damage. This will also enable them to keep up with their updates on their threat intelligence feeds, applying sophisticated solutions, including AI and machine learning, to keep their security posture robust and agile for current challenges and onslaught in the rapidly evolving cyber threats world.





