What is the Internet?
The Internet is a huge web spread all over the planet that connects firewall in computer network and allows them to converse safely. This huge web connects billions of devices worldwide, giving people access to such resources as websites, emails, and all other available services. Transferring information with specific protocols enables transmission across the globe. Whether you chat, watch videos, learn, or do business, the internet protection software is essential today in Cybersecurity Training Courses. On the other hand, such connectivity necessitates internet security, which ensures the safety of transactions as it keeps one safe from possible threats such as data breaches viruses and cyber-attacks.
History of the Internet
The Internet’s journey started in the 1970s when Bob Kahn and Vint Cerf invented the design of what we know today as the ‘Internet.’ This pioneering concept resulted from the ARPANET research project, a communication system developed for the United States Department of Defense to withstand a nuclear attack. The success of ARPANET led to the establishment of a national experimental packet network security , which laid the ground for the Internet as we experience it. However, the internet protection software did not exist until August 6, 1991, when the World Wide Web Application Security came to public light, which began the new age of global connectivity.
Become an expert in cyber security. Enroll in this Cyber Security Online Training now to acquire the knowledge you need.
Types of Internet Connections
These types of Internet connections have changed considerably to meet user demand. Here is a detailed description of different kinds of internet firewall connections:
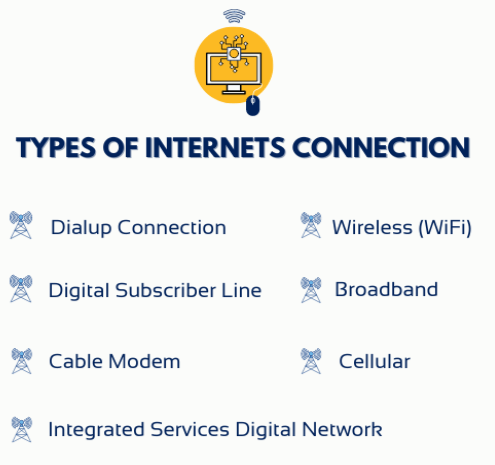
Dialup Connection: Dialup, an older mode of connecting to the internet security programs, used a regular telephone line to communicate and permitted low data transmission over slow speeds. It eventually lost its usage as this technology was not robust with bandwidth issues and could not keep pace with other present alternatives.
Digital Subscriber Line (DSL): DSL utilizes a modem, initiates an internet firewall connection, and can provide users with speeds greater than dial-up. It works over existing telephone lines and is far better suited for general surfing, streaming video, and downloading. Its connection would be much more consistent.
ISDN It allows several devices, such as firewall in computer network , faxes, or phones, to connect at once. It supports different types of data, from video and audio to voice calls. However, utilization of ISDN is still very low today because of the emergence of high-speed broadband technologies in Keylogger.
Cable Modem: These use the same cables that deliver cable TV signals. Due to their higher speed than DSL, cable modems are more common in urban and suburban regions, making them useful for any type of online activity.
Wireless (WiFi):WiFi uses radio waves to connect devices to the Internet wirelessly. It is used in houses, offices, and public spaces. It provides high convenience and flexibility because it allows several devices to be connected within a network firewall security covering them.
Broadband: This high-speed internet security programs is used to transfer enormous amounts of data and offers much faster speeds than dialup and DSL. It uses cable, either coaxial or fiber optic, and has faster and more reliable connections.
Cellular: A cellular internet of things security connects through a mobile network security. This is for smartphones and other devices that can be connected to the internet firewall protection software using mobiles. It works on 3G, 4G, and, just recently, 5G. Speeds will depend on the network firewall security and where you are.
How Does the Internet Work?
Sign up for ACTE Cyber Security Online Training and get a head start in your career cyber security.
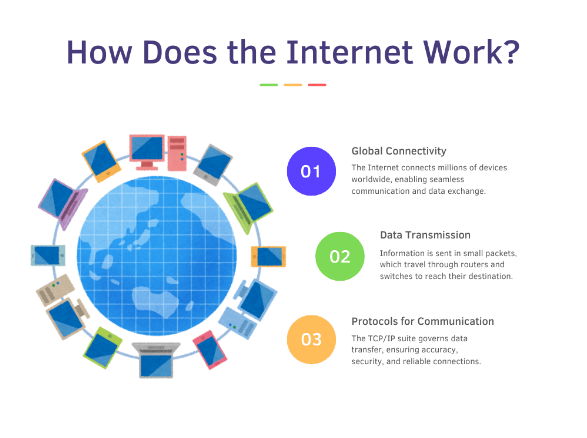
The internet security programs works by connecting firewall in computer network , devices, and servers around the globe. It happens through a widely spread system of interconnectedfirewall in computer network , standardized protocols, and hardware to form the cybernetic backbone of digital interaction, with challenges in internet network firewall security and cyber security.
When the user connects to the internet protection software, his or her device initiates communication with their Internet Service Provider, who then assigns a unique IP address to this device. The unique IP address is essentially a digital name by which the device may be identified; it’s vital to have this kind of digital name to ensure safe connections and protect user Malware Attack and information security.
The internet firewall breaks data into packets, which contain pieces of the information being sent. The packets actually cross various network security, led by routers, switches, and the rest of the hardware, along the most efficient ways to reach the destination. This mode of network and information security communication can easily be threatened by cyber attacks, hence the need for strong iot security measures on the internet of things security.
Top Uses of the Internet
Information Access: It is a vast knowledge and resource base that offers immediate access to information on any subject imaginable, assuring that users are safe from potential online threats.
Communication:The Internet offers instant communication through emails, instant messaging, video calls, and social media that link people from all over the globe. Strengthened cyber security measures protect user information in these communications
E-commerce: It allows online shopping so users can order goods and services from any vendor worldwide, with a strong internet security mechanism protecting transactions.
Education: It provides e-learning tools, online courses, and educational resources, making learning and expanding knowledge change forever while keeping online environments safe.
Entertainment:It offers streaming services related to music, movies, videos, gaming, social media, etc. This provides entertainment according to the interests of various people, keeping its users safe in consuming content due to the proper practice of Cybersecurity Training Courses.
Banking and Finance: The internet firewall offers online banking, financial transactions, investment, and digital payment systems that facilitate more convenience and access but require cyber iot security to maintain confidentiality over personal network and information security regarding one’s financial life.
Social Networking: It accommodates social network security that bring people together from around the globe and offers various communities with their common purpose or interest in a secure internet protection software environment that protects individuals’ privacy.
Want to Take the Lead in Cybersecurity? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Advantages and Disadvantages of the Internet
| Aspect | Advantages | Disadvantages |
|---|---|---|
| Global Connectivity | Enables instant communication worldwide | Increases exposure to cybercrime and security threats |
| Access to Information | Provides vast resources and knowledge | Risk of addiction and overuse |
| E-commerce and Services | Facilitates online shopping and services | Propagation of misinformation and disinformation |
| Social Networking | Enhances connections and community building | Contributes to the digital divide and inequality |
| Education and Learning | Offers online courses and resources | Raises concerns about privacy and Database Security surveillance |
What distinguishes the World Wide Web from the Internet?
The Internet is the network, while the Web Security is something that is accessed using that network. The internet security programs and the World Wide Web, or WWW, have different roles in the virtual world, although they are often confused. Because of the internet of things security, an interlinked global network firewall security of devices, transfers of files and other network and information security exchanges by email are now possible. The Internet is comprised of the World Wide Web. It includes hyperlinked web pages stored in a global network of servers and viewed through web browsers. The World Wide Web is that part of the Internet which is accessible through browsers, but the Internet itself is a network security of all connected devices.
Internet Safety Guidelines
You are likely to expose yourself to many different risks while surfing the Internet. To a large extent, Internet safety guidelines can ensure the better safety and iot security of online phenomena and protect from potential Cyber Awareness . Here are some important Internet safety guidelines:
- Use unique, strong passwords for multiple accounts,
- Avoid sharing private information over the internet of things security in general and social media in particular.
- Keep your software, operating systems, and antivirus internet security programs updated to secure against vulnerabilities.
- Never open attachments or click links from unidentified sources.
- Use two-factor authentication when it is available.
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Conclusion
The internet has become one of the pillars of our daily lives. It is an entry point for services, communications, and information. It has revolutionized global connectivity by changing how we communicate and access network and Cybersecurity Training. It has also changed the way we do business across borders. Since people and companies are now relying heavily on the internet to get their work done, it’s essential to ensure reliability and iot security. This means the internet of things security has a massive influence on how our world is constructed today.





