
- Cryptography Fundamentals
- Symmetric Key Basics
- Asymmetric Key Basics
- How Symmetric Key Works
- How Asymmetric Key Works
- Key Length and Complexity
- Performance Comparison
- Security Strength
- Use Cases of Symmetric Key
- Use Cases of Asymmetric Key
- Future of Cryptography
- Conclusion
Cryptography Fundamentals
Cryptography is the science of securing information through mathematical techniques that ensure confidentiality, integrity, and authenticity of data. From ancient methods of coded messages to modern algorithms, cryptography has evolved into a cornerstone of cybersecurity. In today’s digital age, where sensitive data is exchanged across the internet every second, cryptography plays a crucial role in Cyber security training , protecting individuals, businesses, and governments from cyber threats. Modern cryptography relies on algorithms and keys to convert readable information, called plaintext, into unreadable data, known as ciphertext. Only authorized parties with the correct key can decrypt the ciphertext back into plaintext. The two main types of cryptographic techniques are symmetric key cryptography and asymmetric key cryptography. While both serve the same purpose securing data the way they use keys and their underlying operations differ significantly. Understanding the differences between these two approaches is essential for selecting the right method in a given application.
Want to learn more about Cybersecurity ? Enroll in our Complete Cyber Security Online Training Online!
Symmetric Key Basics
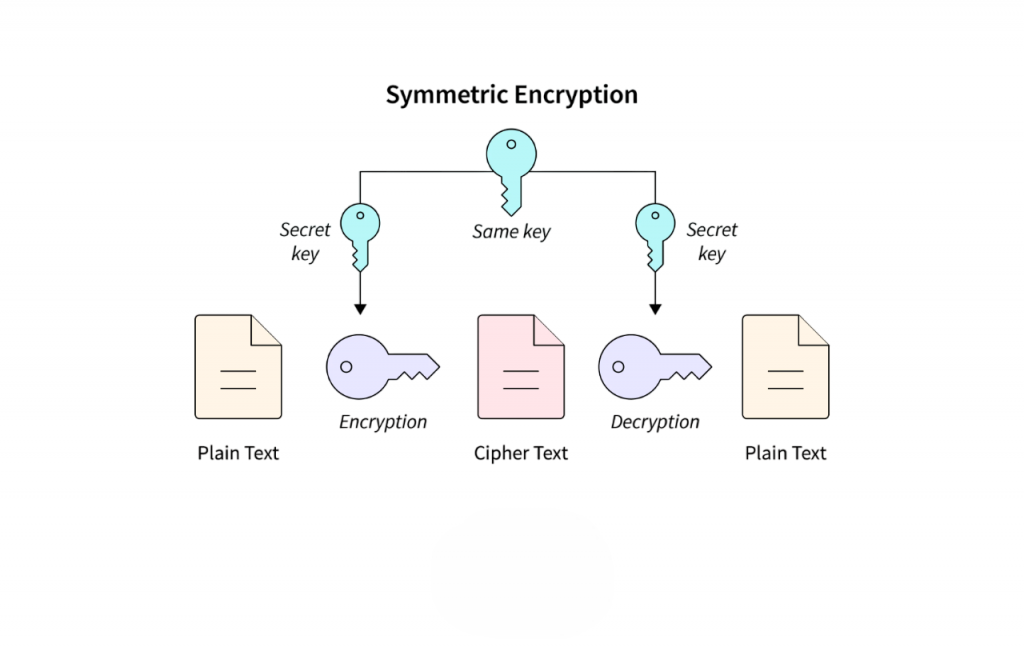
Symmetric key cryptography, also known as secret-key cryptography, uses a single key for both encryption and decryption. This means the same secret key must be shared between the sender and the receiver before secure communication can take place. For example, if Alice wants to send Bob a confidential message, she encrypts the plaintext with a key, and Bob must use the exact same key to decrypt it. The security of this system relies heavily on keeping the key secret and ensuring it is exchanged securely between both parties. Some well-known symmetric key algorithms include:
- DES (Data Encryption Standard)
- AES (Advanced Encryption Standard)
- Blowfish
- RC4 and RC5
Symmetric key cryptography is generally faster than its asymmetric counterpart, which makes it suitable for encrypting large volumes of data, such as files, databases, or entire disk drives. However, the main challenge lies in the secure distribution of keys, a problem that can be analyzed using a Tree Algorithm in ML .
Asymmetric Key Basics
Asymmetric key cryptography, also known as public-key cryptography, uses two mathematically related keys: a public key and a private key. The public key is openly shared, while the private key is kept secret by the owner.
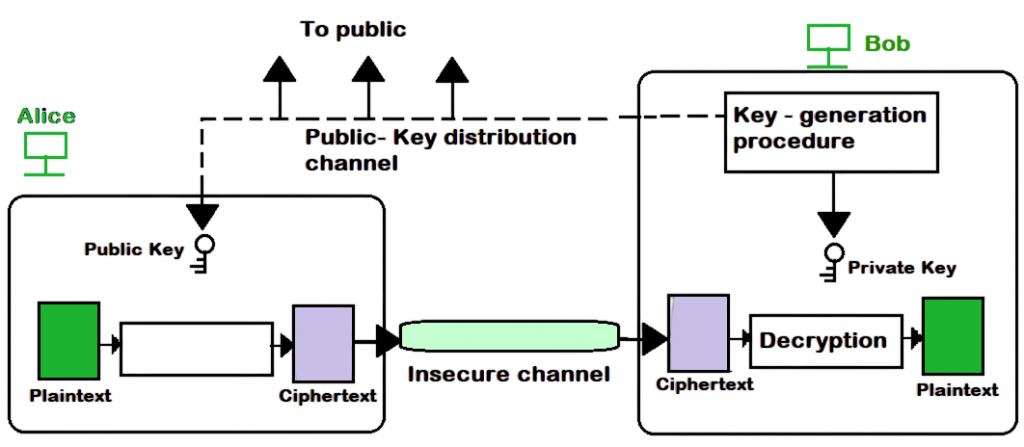
Encryption and decryption are performed with different keys:
- If a message is encrypted with the public key, it can only be decrypted with the corresponding private key.
- Conversely, if a message is signed with a private key, the authenticity can be verified with the public key.
This dual-key mechanism eliminates the need for securely sharing a single secret key, solving one of the main challenges of symmetric cryptography. Popular asymmetric algorithms include:
- RSA (Rivest–Shamir–Adleman)
- ECC (Elliptic Curve Cryptography)
- DSA (Digital Signature Algorithm)
Asymmetric cryptography is widely used in secure email, digital signatures, SSL/TLS certificates, and key exchange mechanisms.
How Symmetric Key Works
The process of symmetric encryption is relatively straightforward:
- A plaintext message is taken as input.
- A secret key and an algorithm (such as AES) are applied to scramble the plaintext into ciphertext.
- The ciphertext is transmitted over the network.
- The receiver applies the same key and algorithm to decrypt the ciphertext back into plaintext.
For instance, if Alice and Bob agree on a secret key like “12345,” they can both use that key to encrypt and decrypt their messages. However, if an attacker manages to steal that key, the entire communication is compromised. Symmetric encryption can work in different modes, such as ECB (Electronic Codebook), CBC (Cipher Block Chaining), and CTR (Counter Mode), each offering different levels of security and efficiency, which can be analyzed using a Random Forest Algorithm .
How Asymmetric Key Works
Asymmetric cryptography involves more complex mathematical operations:
- Each user generates a key pair: a public key and a private key.
- The public key is distributed widely, while the private key is kept confidential.
- If Alice wants to send Bob a secure message, she encrypts it with Bob’s public key.
- Only Bob’s private key can decrypt that message, ensuring confidentiality.
- For authentication, Bob can sign a message using his private key. Anyone with Bob’s public key can verify the signature, ensuring the message’s authenticity.
- Symmetric Keys: Require relatively shorter keys (128-bit, 192-bit, or 256-bit in AES). Despite shorter lengths, symmetric keys provide strong security because brute-force attacks would take impractically long to break them.
- Asymmetric Keys: Require much longer keys (2048-bit or even 4096-bit for RSA) to achieve the same security level. This is because the underlying mathematical problems (like factoring large primes in RSA) are computationally harder but not impossible.
- Speed: Symmetric algorithms are significantly faster, often thousands of times quicker than asymmetric methods, making them suitable for real-time applications.
- Resource Usage: Symmetric encryption requires less computational power, making it efficient for low-power devices and bulk data encryption.
- Asymmetric Performance: While asymmetric encryption is slower, it is indispensable for key exchange and secure authentication, especially over untrusted networks like the internet.
- File and Disk Encryption (BitLocker, TrueCrypt, VeraCrypt)
- Database Security
- Encrypting large volumes of data in secure storage systems
- Mobile communications and IoT devices where resources are limited
- VPNs and secure tunnels for encrypting traffic quickly
- SSL/TLS Certificates for HTTPS websites
- Email encryption (PGP, S/MIME)
- Digital Signatures to verify authenticity of documents and software
- Cryptocurrencies and blockchain (Bitcoin, Ethereum use elliptic curve cryptography)
- Secure key distribution in hybrid cryptographic systems
- Authentication systems in enterprise security
- Quantum Computing Threat: Algorithms like RSA and ECC may become obsolete because quantum computers could break their underlying mathematical problems. This has led to the development of post-quantum cryptography.
- Symmetric Resilience: Symmetric algorithms like AES are believed to be more resistant to quantum attacks, although key sizes may need to increase.
- Hybrid Approaches: Continued use of both symmetric and asymmetric methods together will dominate secure communications.
- Zero-Trust Security Models: Cryptography will be central to implementing authentication and encryption across distributed systems.
This model not only secures data but also provides authentication and non-repudiation, which are difficult to achieve with symmetric cryptography alone.
Enroll in ACTE’S Cyber Security Online Training if you want to become an expert in cyber security field and have a prosperous career.
Key Length and Complexity
One of the main differences between symmetric and asymmetric cryptography lies in key length and computational complexity.
As a result, asymmetric cryptography is more resource-intensive and slower compared to symmetric encryption, a concept often emphasized in Cyber security training .
Performance Comparison
When comparing performance, symmetric cryptography clearly has the advantage:
In practice, many systems use a hybrid approach: asymmetric cryptography is used to securely exchange a symmetric key, and then symmetric encryption handles the actual data transmission. This is how protocols like SSL/TLS work in securing web communication.
Want to Take the Lead in Cyber Security ? Enroll in ACTE’s Cybersecurity Expert Masters Program Training Course Program to Begin Your Adventure Now.
Security Strength
Cryptography’s security strength is dependent on both efficient key management and algorithm complexity. Strong keys, like AES-256, make the system extremely resistant to brute-force attacks in symmetric encryption security. However, if the encryption key is misplaced, exchanged incorrectly, or revealed while being sent, it may become vulnerable.Symmetric cryptography is less appropriate for situations where identity verification is crucial, even though it offers robust confidentiality and few authentication features, especially when integrated withMachine Learning Algorithms for enhanced data processing and analysis. Asymmetric encryption security, on the other hand, provides a more complete concept of protection. It uses intricate mathematical difficulties, such factoring big prime numbers in RSA or resolving discrete logarithms in ECC, to provide confidentiality, authenticity, and non-repudiation. By using these strategies, asymmetric cryptography is more resilient to problems with key distribution than symmetric approaches. But as technology develops especially with the advent of quantum computing old asymmetric algorithms can encounter new weaknesses that need the creation of more sophisticated encryption solutions.
Use Cases of Symmetric Key
For circumstances where quick and effective data encryption is required, symmetric key cryptography is perfect. It is frequently utilised in database security, VPNs to secure high network traffic volumes, and file and disc encryption programmes like BitLocker and VeraCrypt. It is particularly well-suited for closed systems or internal communications where key sharing is controllable because it only requires one key for encryption and decryption. It is ideal for bulk data encryption, IoT applications, and mobile devices due to its rapid speed and minimal computational requirement. Symmetric key cryptography is best used when speed and efficiency are critical, concepts that can also be explored through TensorFlow AI Fundamentals to understand their application in secure and optimized data processing.
Preparing for a job interview in cybersecurity ? Examine our blog post about Cybersecurity Interview Questions and Answers to get the most of your employment experience!
Use Cases of Asymmetric Key
Asymmetric cryptography shines in environments requiring secure key exchange and authentication:
Future of Cryptography
The future of both symmetric and asymmetric cryptography is being reshaped by emerging technologies, raising important security questions such as What is Spyware and how such threats influence modern encryption methods.
Conclusion
Symmetric and asymmetric key cryptography serve the same ultimate purpose ensuring secure communication but they achieve it through very different mechanisms. Symmetric encryption excels in speed and efficiency, making it ideal for encrypting large amounts of data. However, it struggles with key distribution. Asymmetric encryption, while slower, solves the key exchange problem and adds authentication and non-repudiation, a topic often covered in Cyber security training . In practice, modern security systems use both: asymmetric cryptography to exchange keys securely and symmetric cryptography to handle data encryption. This combination balances performance with robust security. As technology evolves, especially with the rise of quantum computing, new cryptographic methods will emerge, but the fundamental principles of symmetric and asymmetric cryptography will remain foundational to securing the digital world.





