
- What is OWASP
- Importance of OWASP Standards
- Injection Attacks
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting (XSS)
- Conclusion
What is OWASP
The Open Web Application Security Project (OWASP) is a globally recognized nonprofit foundation dedicated to improving the security of software. Established in 2001, Open Web Application Security Project (OWASP) provides free, vendor-neutral, and community-driven resources to help organizations identify and address security vulnerabilities. To build the skills needed to apply these principles in real-world environments, explore Cyber Security Training a hands-on program that equips learners with the tools, techniques, and frameworks essential for protecting digital assets and mitigating threats across modern IT infrastructures. One of its most widely known contributions is the OWASP, which highlights the ten most critical security risks to web applications. Updated every few years, this list serves as a standard awareness document for developers, security professionals, and organizations worldwide. It is considered a baseline for application security, guiding both technical and managerial decisions in protecting software systems.
Importance of OWASP Standards
The Open Web Application Security Project (OWASP) is not merely a list of common vulnerabilities, it is an awareness and educational framework. By following OWASP standards, organizations can drastically reduce their risk exposure and improve the resilience of their applications. To understand how these standards intersect with legal obligations and digital rights, explore Cyber Law Explained a foundational guide that covers data protection regulations, liability frameworks, and compliance strategies essential for secure and lawful web development.

These standards encourage secure development practices, vulnerability assessment, and compliance with industry regulations like GDPR, HIPAA, and PCI-DSS. For developers, the OWASP acts as a reference manual to avoid common mistakes, while for businesses, it sets a benchmark to measure their application security posture. Ultimately, adhering to Open Web Application Security Project (OWASP) standards fosters trust with users, reduces financial losses from cyberattacks, and strengthens overall cybersecurity strategy.
Interested in Obtaining Your Cyber Security Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Injection Attacks
Injection attacks occur when untrusted data is sent to an interpreter as part of a query or command. Attackers exploit flaws in input validation to execute unintended commands or access unauthorized data. The most well-known type is SQL Injection (SQLi), where malicious SQL queries are injected into an application’s database query field. Other forms include OS command injection, LDAP injection, and NoSQL injection. These attacks can lead to data theft, data loss, or complete system compromise. To understand how such threats are identified and mitigated in secure environments, explore What is Cyber Safety a practical guide that outlines safe coding practices, input validation techniques, and proactive defense strategies to protect digital assets from injection-based vulnerabilities.
For Example:
- ‘ OR ‘1’=’1
This trick bypasses authentication and grants unauthorized access.
Mitigation strategies include:
- Using prepared statements and parameterized queries.
- Employing input validation and sanitization.
- Implementing least privilege access for databases.
- Enforcing strong password policies.
- Using multi-factor authentication (MFA).
- Implementing secure session management (e.g., session timeouts, regenerating session IDs).
- Enforcing principle of least privilege.
- Implementing proper role-based access controls (RBAC).
- Conducting regular access control audits and penetration testing.
- Regular security hardening of servers, applications, and frameworks.
- Enforcing least privilege principles in configurations.
- Conducting routine security audits and penetration testing.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Broken Authentication
Broken authentication refers to flaws in the implementation of authentication and session management mechanisms. These flaws allow attackers to compromise passwords, keys, or session tokens, and potentially impersonate users. To learn how to detect, prevent, and mitigate such vulnerabilities in real-world systems, explore Cyber Security Training a hands-on course that equips learners with threat modeling, penetration testing, and incident response skills essential for safeguarding digital infrastructure. Examples include weak password policies, improper session expiration, or predictable session IDs. A real-world example is when websites allow brute-force attacks without implementing account lockout mechanisms, making it easier for attackers to guess passwords.
Mitigation strategies include:
Sensitive Data Exposure
Apps often have trouble keeping sensitive information safe, like personal info, money details, and health records. This weakness can cause data to be exposed, especially if encryption is weak, missing, or not done right. For example, hackers can grab data while it’s being sent, mainly if it’s over unsecured HTTP, or they can get to data if databases aren’t encrypted. To understand how such vulnerabilities impact interconnected environments that blend physical and digital components, explore How Cyber-Physical Systems Work a detailed guide that explains the architecture, communication protocols, and security challenges of systems where sensors, software, and networks converge to control real-world operations. Common mistakes include storing passwords without encryption, not using secure sending methods like TLS/SSL, and using old encryption methods like MD5 or SHA-1. To fix these issues, it’s key to use strong, updated encryption methods like AES-256 and TLS 1.3. Also, companies should stop using outdated hashing methods and use better options like bcrypt, scrypt, or Argon2. Making sure data is stored safely and using good key management are important for protecting sensitive info from possible breaches.
Looking to Master Cybersecurity? Discover the Cyber Security Expert Masters Program Training Course Available at ACTE Now!
XML External Entities (XXE)
XML External Entity (XXE) attacks happen when apps don’t correctly handle XML input that has bad links to outside sources. Attackers exploit XML setups that allow these outside links, which can cause serious issues like getting into private files, denial-of-service (DoS) attacks, or server-side request forgery (SSRF). For example, an attacker might create an XML file that tells the system to grab important files, like /etc/passwd on a Linux system, which puts the system at risk. To fight these weaknesses, there are several ways to lessen the damage. To understand how such technical exploits intersect with online harassment and manipulation tactics, explore What Is Cyber Trolling a focused guide that explains the psychological, legal, and technical dimensions of trolling, including how attackers exploit system vulnerabilities to provoke, disrupt, or intimidate users in digital spaces. The most important thing is to turn off external link resolution in XML setups to stop unauthorized access. Also, checking and cleaning XML inputs can help make sure only safe data is handled. If possible, using simpler data formats like JSON can also lower the chance of these attacks. By using these steps, apps can greatly improve their protection against XXE attacks.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Broken Access Control
Broken access control occurs when applications fail to enforce restrictions on authenticated users. This allows attackers to perform unauthorized actions, such as accessing restricted pages, modifying other users’ data, or escalating privileges. For instance, if an application exposes administrative functions to all users simply by changing a URL from /user/profile to /admin/dashboard, attackers can gain unauthorized access. To explore how such vulnerabilities contribute to broader digital threats, explore Understanding Cybercrime and its Implications a comprehensive resource that examines the technical, legal, and societal impact of cyberattacks, and outlines strategies for prevention, detection, and accountability.
Mitigation strategies include:
Security Misconfiguration
Security misconfiguration is one of the most common vulnerabilities, resulting from insecure default settings, incomplete configurations, or exposed error messages. Examples include leaving default admin accounts active, exposing stack traces in error messages, or misconfigured cloud storage buckets. Attackers exploit these weaknesses to gain insights into the system architecture or directly compromise applications.
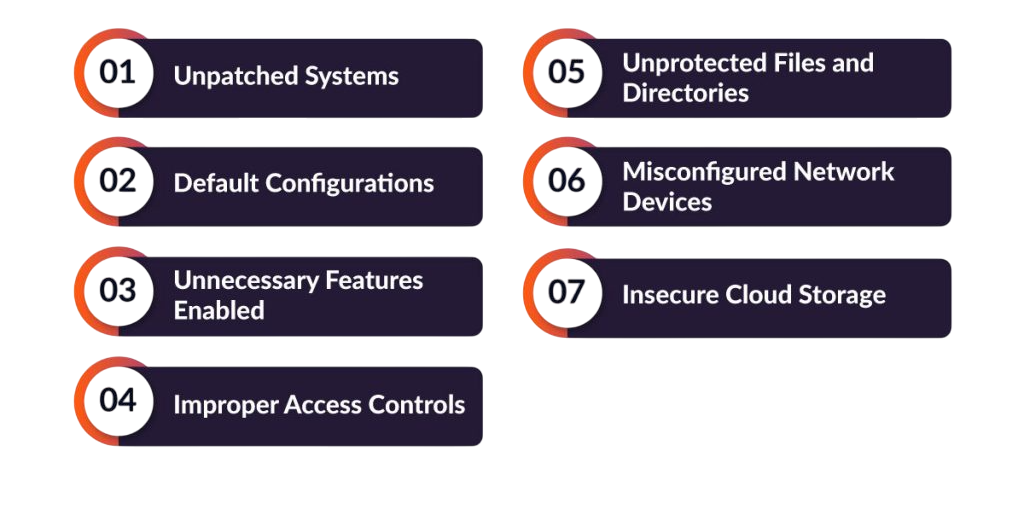
Mitigation strategies include:
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) attacks are a serious security concern. They happen when a web application puts untrusted data on a web page without checking it properly. Attackers can then inject bad JavaScript code into web pages, which runs in users’ browsers without them knowing. This can cause problems like stealing login sessions or user credentials, and sending users to harmful sites. There are three main kinds of XSS attacks. Stored XSS is when the bad script is saved on the server, so it affects anyone who visits the infected content. To proactively block such malicious scripts before they reach users, explore Intrusion Prevention System a defensive framework that monitors network traffic, detects suspicious patterns, and automatically prevents exploitation attempts like XSS, SQL injection, and buffer overflows. Reflected XSS is when the script is in a URL and runs when someone clicks the link. DOM-based XSS happens on the user’s side by changing the page structure (DOM). To defend against XSS, developers can use a few methods. They can carefully check all data that comes into the application and encode data when it leaves the application to confirm it is safe. Setting up a Content Security Policy (CSP) can also help by controlling what resources the browser can load. It’s also important not to use risky functions like eval(), which can run bad scripts by mistake. Knowing how XSS attacks work and using the right defenses can help companies keep their users safe.
Conclusion
The Open Web Application Security Project (OWASP) remains one of the most authoritative resources in the field of application security. It highlights the most critical vulnerabilities that developers, organizations, and security professionals must address to secure modern applications. To gain the skills needed to identify and remediate these threats effectively, explore Cyber Security Training a practical course that covers threat detection, secure coding practices, vulnerability assessment, and incident response strategies tailored for today’s dynamic application environments. By understanding and implementing mitigation strategies against threats like injection attacks, broken authentication, XSS, and insecure deserialization, organizations can significantly reduce their risk exposure. However, security is not a one-time effort. As technology evolves, so do attack techniques. Therefore, continuous learning, regular audits, adoption of modern frameworks, and a proactive security culture are essential. Following the OWASP not only protects applications but also builds trust with users, ensuring safe and reliable digital interactions.




