
- How VPCs work
- Where they live
- VPC management
- Elements of a VPC
- Shared responsibility
Introduction to Amazon’s Virtual Private Cloud:
Amazon’s Virtual Private Cloud (VPC) is a foundational AWS service in both the Compute and Network AWS classes. Existing foundational means that other AWS services, such as Elastic Compute Cloud (EC2), cannot be accessed without an underlying VPC network.
Creating a VPC is critical to operating in the AWS cloud. Let’s take a look at:
- IP addresses.
- Subnets.
- Routing.
- Security.
- Networking functionality.
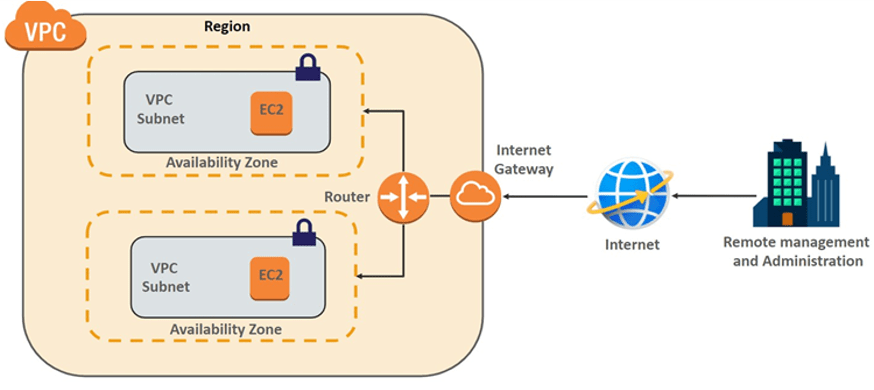
How VPCs work: virtual networking environments:
Each VPC makes a separate virtual network environment in the AWS cloud, committed to your AWS account. Other AWS help and services operate inside of VPC networks to deliver cloud services.
AWS VPC will look normal to anyone employed in running a physical Data Center (DC). A VPC acts like a standard TCP/IP network that can be developed and scaled as required. However, the DC features you are employed to trade with such as routers, switches, VLANS, etc. do not explicitly exist in a VPC. They have been outlined and re-engineered into cloud software.
Employing VPC, you can fast spin up a virtual network infrastructure that AWS models can be launched into. Each VPC represents what your AWS help market, including:
- Default subnets.
- Routing tables.
- Security groups.
- Network access control list.
Where VPCs live:
All VPCs are made and exist in one and only one AWS region. AWS regions are geographic areas around the world where Amazon clusters its cloud data centers. The benefit of regionalization is that a regional VPC delivers network services arising from that geographical area. If you require to deliver closer access for clients in another region, you can set up another VPC in that area.
Amazon makes one default VPC for each account, done with:
You can change or use that VPC for your cloud designs or you can build a new VPC and help services from scratch.
- AWS Management Console is the web interface for controlling all AWS functions (image below).
- AWS Command Line Interface (CLI) delivers Windows, Linux, and Mac commands for many AWS services. AWS frequently delivers configuration education as CLI commands.
- AWS Software Development Kit (SDK) delivers language-specific APIs for AWS services, including VPCs.
- Query APIs. Low-level API actions can be offered through HTTP or HTTPS demands. Check AWS’s EC2 API Reference for more details.
Managing your VPCs:
VPC administration is conducted through these AWS management interfaces:
- IPv4 and IPv6 address blocks.
- Subnet creation.
- Route tables.
- Internet connectivity.
- Elastic IP addresses (EIPs).
- Network/subnet security.
- Additional networking services.
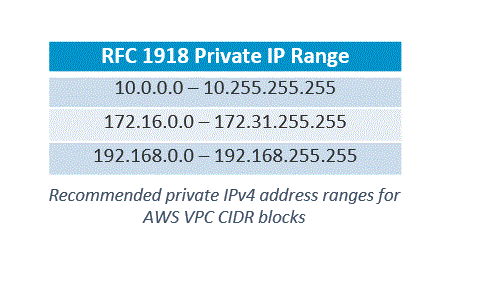
- VPC IP address fields are represented using Classless interdomain routing (CIDR) IPv4 and IPv6 blocks. You can add immediate and secondary CIDR blocks to your VPC if the secondary CIDR block arrives from the same speech range as the primary block.
- AWS suggests that you specify CIDR blocks from the private address ranges defined in RFC 1918, shown in the table below. See the AWS VPCs and Subnets page for rules on which CIDR blocks can be employed.
- Established EC2 instances run inside a specified VPC subnet (sometimes referred to as launching an instance into a subnet).
- For IP address, each subnet’s CIDR is a subset of the VPC CIDR block. Each subnet separates its traffic from all other VPC subnet traffic.
- A subnet can only have one CIDR block. You can set other subnets to handle different kinds of traffic.
- Route tables have the rules (routes) that define how network traffic is handled inside your VPC and subnets. VPC makes a default route table called the main route table. Here, you have two choices:
- Modernize and use the main route table to control network traffic.
- Complete your route table to be utilized for personal subnet traffic.
- EIPs are static public IPv4 addresses that are always given to your AWS account (EIP is not shown for IPv6). EIPs are employed for public Internet access to:
- An instance.
- An AWS elastic network interface (ENI).
- Other services require a public IP address.
- VPCs use security groups to deliver statefull protection (the state of the connection session is held) for instances. AWS defines security groups as virtual firewalls.
- VPCs also supply network access control lists (NACLs) to stateless VPC subnets that are, the state of the connection is not sponsored.
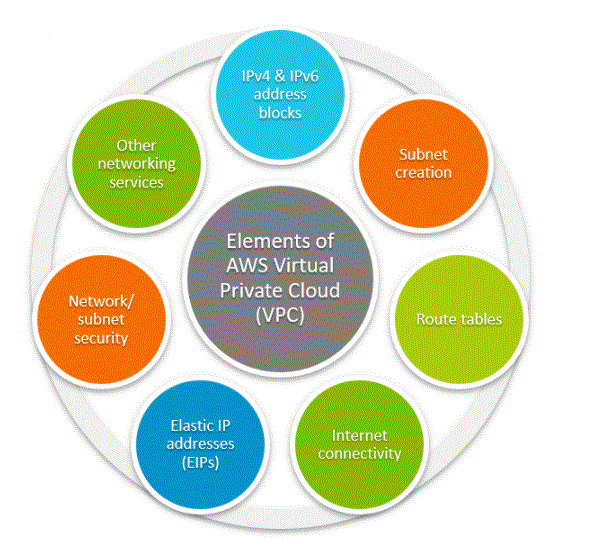
Elements of a VPC:
The web-based AWS management console, shown above, shows most of the VPC help you can make and manage. VPC network services include:
IPv4 and IPv6 address blocks:
Subnet creation:
Route tables:
Internet connectivity:
For Internet access, each VPC configuration can host one Internet Gateway and supply network address translation (NAT) services operating the Internet Gateway, NAT instances, or a NAT gateway.
Elastic IP addresses (EIPs):
Network/subnet security:
- IPV4 static addresses can be designated to the user’s models which are currently in between a start and a stop.
- An IPV6 CIDR union can be optionally associated with the user’s VPC.
- An IPV6 address can be associated with the user’s instance.
- Numerous IP addresses can be allocated to the user’s instance.
- Network interfaces can be determined, and these (single or multiple interfaces) can be connected to the user’s instance.
- Security group membership of the user’s instance can be modified when it is running.
- The outgoing traffic from the user’s model can be handled with the service of egress filtering, in addition to controlling the inbound traffic to the models (which is known as ingress filtering).
- The user’s models can be made to run on single-tenant hardware.
- An extra layer of access control can be added to the instances in the form of NACLs (network access control lists).
Features of Amazon VPC:
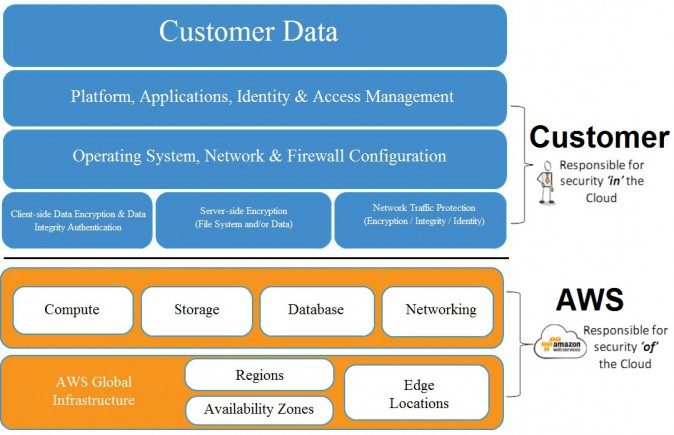
Accessing Amazon VPC:
Amazon VPC can be produced, accessed, and worked with the benefit of any of the below-mentioned interfaces:
AWS Management Console: It delivers a web interface that can be used to access the VPCs.
AWS Command Line Interface (AWS CLI): It aids in the provisioning of management for many AWS services, which contain AWS VPC. It arrives with the help of Windows, macOS, and Linux.
AWS SDK: It also delivers APIs, which are language-specific, thereby bringing care of granular connection details, which contain (but are not limited to) computing signatures, submission retries handling, and error handling.
Query API: It delivers low-level API actions, which can be called by the user with the benefit of HTTPS requests. The Query API is a direct way to access Amazon VPC, but this needs the application to have the ability to control low-level details including generation of hash which is needed to sign the request, and error handling.
VPC Pricing:
No extra charges are incurred by the usage of Amazon VPC. The expenses are incurred for the use of illustrations and Amazon EC2 features that are operated by the user. A site-on-site VPN link and a NAT gateway are responsible.
PCI DSS Compliance:
VPC requirements the processing, storage, and transmission of credit card data that belongs to a vendor or a service provider. This is validated as yielding with the Payment Card Industry (PCI) Data Security Standard (DSS).
Default VPC: If the user version supports the EC2-VPC platform, it comes with a default VPC, which arrives with a default subnet in every Availability Zone.
Nondefault VPC: Irrespective of the platform which the user account funds, the user can make their VPC and configure them according to their conditions. These are known as non-default VPCs. Subnets made by users in this non-default VPC are known as non-default subnets.
Conclusion:
In this post, we comprehended Amazon VPC, and how it can be used to establish AWS resources that are determined by the user in a private network. AWS provides a number of efficient, secure connectivity options to help you get the most out of AWS when integrating your remote networks with Amazon VPC.





