
- Introduction of Azure DevOps Pipelines
- Setting Up a CI/CD Pipeline
- YAML vs. Classic Pipelines
- Integrating with GitHub and Azure Repos
- Using Agents and Agent Pools
- Managing Secrets and Variables
- Deployment Strategies (Blue-Green, Canary)
- Monitoring and Troubleshooting Pipelines
- Pipeline Optimization and Scaling
- Security Best Practices for Pipelines
- Infrastructure as Code (IaC) with Pipelines
- Compliance and Governance in Azure DevOps Pipeline
- Cost Management and Optimization
- Conclusion
Introduction of Azure DevOps Pipelines
AWS Blockchain is a suite of managed services and tools offered by Amazon Web Services (AWS) that allows businesses to easily set up, manage, and scale blockchain networks. Blockchain is a distributed ledger technology that enables secure, transparent, and immutable transactions. AWS Blockchain services aim to simplify the deployment and management of blockchain applications while leveraging the scalability, security, and performance of AWS cloud infrastructure. AWS provides several services to enable different blockchain use cases, from public networks to private enterprise solutions and supports popular blockchain frameworks like Ethereum, Hyperledger Fabric, and Corda. Azure Devops Training services are designed to reduce the complexity of blockchain management by automating tasks like setup, maintenance, and scaling.Azure DevOps Pipelines is a cloud-based automation service that facilitates Continuous Integration (CI) and Continuous Deployment (CD). It enables development teams to automate the process of building, testing, and deploying applications efficiently. By integrating with various version control systems, such as Azure Repos, GitHub, and Bitbucket, Azure Pipelines ensures seamless software delivery with minimal manual intervention. Azure Pipelines offers two primary types: YAML and Classic. YAML pipelines use a code-based approach for better maintainability and versioning, while Classic pipelines provide a graphical interface for configuration. Additionally, Azure Pipelines support multi-stage deployments, artifact management, and gated approvals. It also integrates with Kubernetes, Terraform, Helm, and other DevOps tools for advanced deployment scenarios.
Learn how to manage and deploy Azure Devops services by joining this Azure Devops Training today.
Setting Up a CI/CD Pipeline
- To set up a CI/CD pipeline in Azure DevOps, create a new Azure DevOps project and connect it to a source code repository. Next, define a build pipeline to automate compilation, testing, and artifact creation.
- Configure build triggers to initiate pipeline execution based on events like code commits and pull requests.
- After setting up the Microsoft Azure Application Gateway, define a release pipeline to deploy artifacts to different environments, such as development, staging, and production.
- Deployment tasks may include database migrations, infrastructure provisioning, and application updates. To protect and utilize environment variables and secure secret management tools.
- Finally, monitoring and logging should be implemented to track deployments and quickly diagnose failures.
YAML vs. Classic Pipelines
Azure DevOps provides two pipeline types: YAML and Classic. YAML pipelines follow an Infrastructure-as-Code (IaC) approach, where pipeline definitions are written in YAML and stored in a version control system. This method enhances maintainability, reusability, and consistency across multiple environments. Classic pipelines use a visual editor, allowing users to configure pipelines via a drag-and-drop interface. While Classic pipelines are more manageable for beginners, they can become complex and more challenging for large-scale projects. YAML pipelines provide better automation, scalability, and integration with modern DevOps practices, making them the preferred choice for advanced workflows.
Integrating with GitHub and Azure Repos
- Azure DevOps Pipelines integrate seamlessly with GitHub and Azure Repos, enabling automated builds and deployments based on repository events.
- GitHub integration allows teams to trigger builds on Red Hat Certification Path and commits, ensuring code quality before merging.
- Azure Repos offers additional features like branch policies, gated check-ins, and work item linking to enforce coding standards.
- Service connections and webhooks facilitate real-time updates, triggering pipelines automatically upon repository changes.
- Teams can also leverage GitHub Packages and Azure Artifacts to manage dependencies and distribute software packages efficiently.
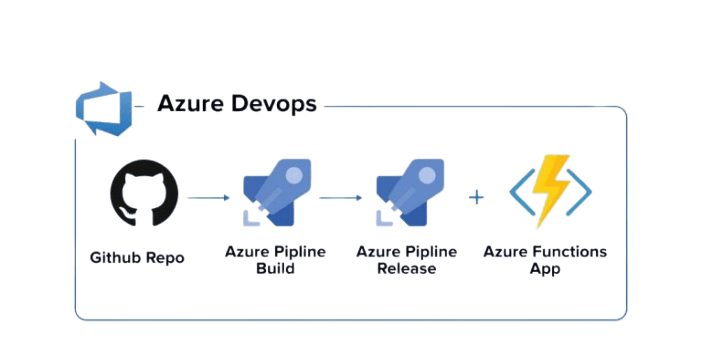
Using Agents and Agent Pools
Azure DevOps Pipelines use agents to execute CI/CD tasks. Microsoft-hosted agents come pre-configured with commonly used tools, while self-hosted agents allow customization to meet project-specific requirements. Agent pools distribute workloads across multiple agents, ensuring faster execution and reducing bottlenecks. Agents can run on Windows, Linux, or macOS, making them versatile for different technology stacks. By scaling agent pools dynamically, teams can optimize resource usage and reduce costs. Self-hosted agents also provide additional security and control over build and deployment processes.
Managing Secrets and Variables
Azure DevOps Pipelines use variables and secrets to securely manage configuration values. Pipeline variables store dynamic values like Azure Site Recovery , database credentials, and environment-specific settings. These variables can be defined at the pipeline, stage, or job level. For enhanced security, sensitive information should be stored in Azure Key Vault, which integrates seamlessly with Azure Pipelines. Azure Key Vault ensures controlled access using Role-Based Access Control (RBAC), preventing unauthorized access to secrets. Variable groups further help centralize configurations across multiple pipelines for better maintainability.
Unlock your potential in Azure Devops with this Azure Devops Training.
Deployment Strategies (Blue-Green, Canary)
Azure DevOps facilitates deployment techniques that help minimize risks and downtime. Two commonly used strategies are Blue-Green Deployment and Canary Deployment, both designed to ensure seamless application rollouts.
- Blue-Green Deployment Blue-Green deployment maintains two identical environments: Blue (Live) and Green (Idle). The live traffic is directed to the Blue environment while the Green environment is used to deploy and test updates. Once the new version is validated in Green, traffic is switched from Blue to Green, making the updated version live. If issues arise, traffic can be rolled back to the previous version with minimal downtime. Azure DevOps supports this through Azure App Service Slots, Azure Traffic Manager, and Kubernetes for seamless transitions.
- Canary Deployment Canary deployment releases updates incrementally to a small group of users before rolling them out to the entire system. A small percentage of traffic is routed to the new version while monitoring for performance and errors. If stable, the update is gradually expanded to all users. If issues occur, the deployment is halted, and traffic is reverted to the previous version. Azure Devops Training enables canary deployments with traffic-splitting, feature flags, and Kubernetes Ingress Controllers, ensuring controlled and monitored releases. Both strategies help reduce risks, enable quick rollbacks, and ensure a smooth user experience, making deployments more reliable and efficient.
- Role-Based Access Control (RBAC) – Restrict access using least privilege principles and review permissions regularly.
- Multi-Factor Authentication (MFA) – Enable MFA and integrate with Azure AD for secure authentication.
- Secure Secrets Management – Use Azure Key Vault for storing API keys and credentials instead of hardcoding.
- Code and Dependency Scanning – Use Microsoft Defender for DevOps, SonarQube, and Snyk to detect vulnerabilities early.
- Secure Artifact Storage – Store verified packages in Azure Artifacts to prevent supply chain attacks.
- Pipeline Auditing & Logging – Monitor activities using Azure DevOps Audit Logs, Azure Monitor, and Log Analytics.
- Harden Build Agents – Keep self-hosted agents updated, isolated, and restrict network access.
- Enforce Compliance Policies – Use Azure Policy to ensure adherence to security standards like ISO 27001 & GDPR.
- SUse Terraform, ARM templates, and Bicep to define infrastructure declaratively. li> Store infrastructure configurations in version control for better tracking and collaboration.
- Implement CI/CD pipelines to automatically deploy, update, and destroy infrastructure.
- Reduce manual interventions, The Azure Network Security Group NSG an Overview and error-free deployments.
- Store IaC files in Git repositories (Azure Repos, GitHub, or Bitbucket) for version tracking.
- Enable rollback mechanisms for quick recovery in case of misconfigurations.
- Manage Terraform state using Azure Hdinsight Big Data in the Cloud , Azure Storage, or AWS S3.
- Maintain consistency across teams by centralizing infrastructure state files.
- Use Azure Policy, Sentinel, and Open Policy Agent (OPA) to enforce governance.
- Run security scans with Microsoft Defender for DevOps and Checkov to detect misconfigurations.
- Use pull requests (PRs) and branch policies to review infrastructure changes before deployment.
- Implement manual approvals and gated releases for sensitive changes.
- Integrate with Azure Monitor and Log Analytics for real-time tracking of infrastructure health.
- Set up automated scaling using Azure Autoscale and Kubernetes for optimized resource usage.
Monitoring and Troubleshooting Pipelines
Monitoring pipelines is essential for detecting and resolving issues efficiently. Azure DevOps provides built-in logging, execution history, and diagnostic tools for tracking pipeline performance. Azure Monitor and Application Insights offer real-time performance tracking, error detection, and alerting capabilities. Common pipeline failures include misconfigurations, permission errors, and failed builds. Teams can implement automated retries, notifications, and rollback mechanisms to improve pipeline stability. Distributed tracing and observability tools provide deeper insights into CI/CD processes.
Pipeline Optimization and Scaling
Pipeline optimization becomes crucial as businesses grow. Azure DevOps provides pipeline templates, caching, and parallel processes to increase efficiency. Wait times are decreased by using parallel jobs to Introduction to Azure Arc and deployments simultaneously. By reusing previously downloaded packages and generated artifacts, cached dependencies speed up build times. Pipeline templates increase consistency by standardizing configurations across several pipelines. Conditional execution and matrix builds help optimize resource usage. Scalability is improved using dedicated agent pools for particular workloads, such performance testing.
Security Best Practices for Pipelines
Looking to master Devops? Sign up for ACTE’s Devops Master Program Training Course and begin your journey today!
Infrastructure as Code (IaC) with Pipelines
Azure DevOps Pipelines support Infrastructure as Code (IaC), enabling teams to define, provision, and manage infrastructure through code. This approach ensures consistency, automation, and reduced manual errors in infrastructure deployment.
Define Infrastructure Using IaC Tools
Automate Infrastructure Provisioning
Version Control for Infrastructure Code
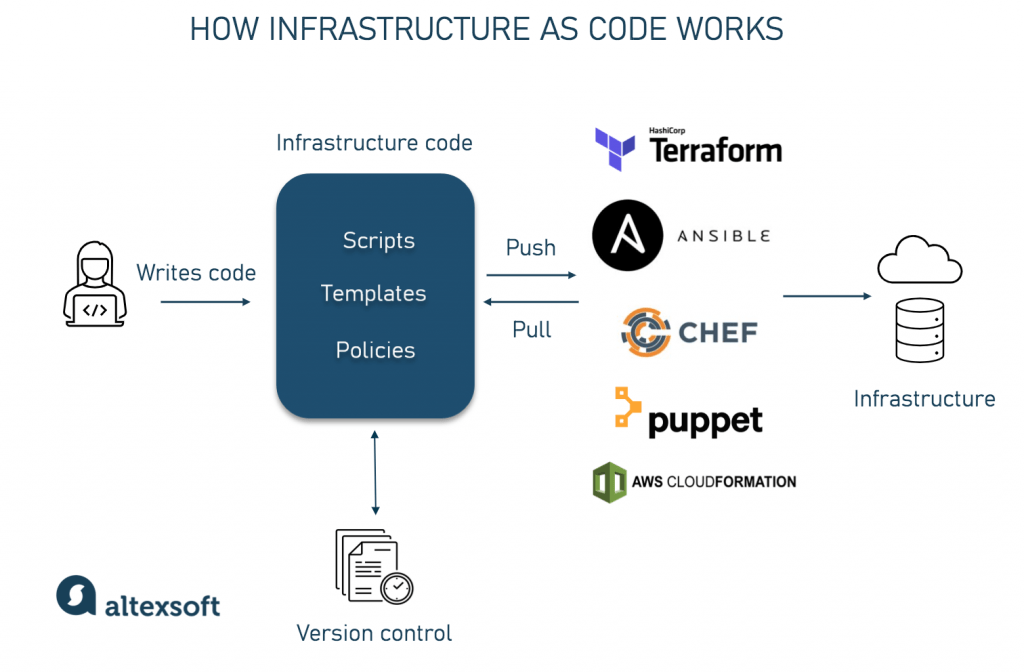
Use Remote State Management
Implement Automated Security and Compliance Checks
Enhance Collaboration and Approval Processes
Monitor and Maintain Infrastructure
Boost your chances in Azure Devops interviews by checking out our blog on Azure Devops Interview Questions and Answers!
Compliance and Governance in Azure DevOps Pipeline
Ensuring compliance with industry standards and organizational policies is critical for secure software delivery. Azure DevOps provides policy enforcement mechanisms such as branch policies, security baselines, and Azure Expressroute . Organizations can implement governance frameworks by leveraging Azure Policy, Azure Blueprints, and Compliance Manager to maintain regulatory adherence. Auditing pipeline activities using Azure DevOps Audit Logs enhances visibility into changes and security events. Automated security scans and compliance checks can be integrated into pipelines to detect vulnerabilities and enforce security best practices. Maintaining audit trails ensures accountability and simplifies regulatory reporting.
Cost Management and Optimization
Optimizing costs in Azure DevOps Pipelines is essential for efficient resource utilization. By using Microsoft-hosted agents strategically and leveraging self-hosted agents for long-running workloads, organizations can reduce operational expenses. Azure DevOps provides cost analysis tools to track build and deployment expenditures, enabling better budgeting and forecasting. Implementing caching mechanisms, parallel execution, and pipeline templates minimizes redundant processes, leading to faster build times and lower costs. Auto-scaling agent pools help balance workloads dynamically, ensuring resources are allocated efficiently while avoiding unnecessary expenses.
Conclusion
Azure DevOps Pipelines provide a comprehensive and scalable solution for implementing CI/CD workflows. By leveraging automation, security best practices, and efficient resource management, teams can enhance software quality and deployment speed. Integrating with modern Azure Devops Training , monitoring pipeline performance, and ensuring governance compliance further strengthens the software delivery process. Organizations adopting Azure Pipelines can achieve streamlined, cost-effective, and secure software releases while maintaining high availability and reliability.





