
- Introduction: What is AWS Shield?
- Types of DDoS Attacks and How They Affect Applications
- Key Features of AWS Shield Standard
- How AWS Shield Protects Against DDoS Attacks
- Integrating AWS Shield with Other AWS Services
- AWS Shield Advanced: A Deeper Level of Protection
- Best Practices for Maximizing AWS Shield Protection
- Conclusion
Introduction: What is AWS Shield?
In today’s digital landscape, protecting applications and data from malicious threats is more critical than ever. One of the most common and damaging types of cyberattack is a Distributed Denial of Service (DDoS) attack. These attacks are designed to overwhelm a system by flooding it with enormous traffic, causing the targeted service to become slow or unavailable. Amazon Web Services (AWS) provides a robust defense against these threats through AWS Shield, a managed Distributed Denial of Service (DDoS) protection service, a critical topic covered in Amazon Web Service Training, where learners gain the skills to implement and manage security measures to protect cloud infrastructures from cyber threats. AWS Shield is built to safeguard AWS customers against various DDoS attacks without requiring additional software or configurations. It integrates with other AWS services to provide a comprehensive defense that works seamlessly to maintain uptime and availability. In this blog post, we will examine AWS Shield, its features, how it protects applications, and how you can use it to strengthen your AWS environment’s resilience against DDoS attacks.
Are You Interested in Learning More About AWS? Sign Up For Our AWS Course Today!
Types of DDoS Attacks and How They Affect Applications
Before delving into the specifics of AWS Shield, it’s essential to understand the different types of DDoS attacks that AWS Shield is designed to protect against:
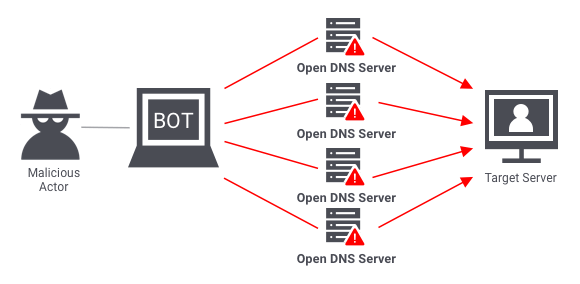
- Volumetric Attacks: These attacks aim to flood a target with massive amounts of traffic, overwhelming the bandwidth and infrastructure of the target service. Common methods include UDP (User Datagram Protocol) floods, DNS amplification, and HTTP floods. Volumetric attacks are the most common form of DDoS attack, similar to Mastering Snowflake Architecture, where understanding various methods and strategies to protect and optimize data flow is essential for building secure, scalable, and efficient systems in data warehousing environments.
- State Exhaustion Attacks: These attacks exploit a protocol’s stateful nature, such as the Transmission Control Protocol (TCP). In a state exhaustion attack, the attacker floods a target with traffic that consumes resources through open connections or sessions. This can cause the target to run out of resources, making the service unavailable.
- Application Layer Attacks: These attacks are designed to overwhelm a system’s application layer by sending requests that appear legitimate but are actually crafted to stress the server’s resources. Examples include HTTP GET or POST floods, where attackers may send many HTTP requests to a server to overwhelm it.
DDoS attacks can have severe consequences for businesses. They can lead to downtime, loss of customer trust, and significant financial losses. For organizations operating on AWS, AWS Shield provides an effective defense layer to protect against these attacks, ensuring that applications remain operational and secure.
Key Features of AWS Shield Standard
AWS Shield is a DDoS (Distributed Denial of Service) protection service offered in two tiers: AWS Shield Standard and AWS Shield Advanced. Shield Standard provides automatic and robust protection against the most common DDoS attacks. It is included by default with AWS services such as Elastic Load Balancing (ELB), Amazon CloudFront, Amazon Route 53, and AWS Global Accelerator, requiring no additional configuration. This built-in protection ensures that AWS resources remain secure without manual intervention. One of its key features is global threat detection, leveraging AWS’s extensive global network to identify and mitigate attacks in real-time across different regions, similar to how Key Artifacts in DevOps for Efficient Delivery ensure that pipelines, tools, and processes are in place to detect, prevent, and resolve issues efficiently throughout the software development and deployment lifecycle. This proactive approach helps prevent downtime and enhances overall security. Shield Standard primarily focuses on network and transport layer protection, defending against large-scale volumetric and state-exhaustion attacks that attempt to flood network resources. These attacks are absorbed and mitigated automatically, ensuring that system performance remains unaffected. Another major advantage of AWS Shield Standard is that it comes at no additional cost when used with supported AWS services, making it an efficient and cost-effective solution for basic DDoS protection. By combining automatic security, global threat intelligence, and zero additional costs, AWS Shield Standard is an essential defense mechanism for AWS users.
To Earn Your AWS Certification, Gain Insights From Leading AWS Experts And Advance Your Career With ACTE’s AWS Course Today!
How AWS Shield Protects Against DDoS Attacks
AWS Shield is designed to automatically detect and mitigate DDoS attacks in real-time, minimizing their impact on your applications. The service uses a combination of threat intelligence, advanced machine learning algorithms, and a global network of resources to defend against various DDoS attack vectors. AWS Shield operates at different layers of the AWS network, including Global Network, Edge Locations, and Regionally Deployed Services. When an attack occurs, AWS Shield’s multi-layered protection system comes into play, ensuring that malicious traffic is identified and filtered without interrupting legitimate user activity. Here are the primary methods AWS Shield uses to protect applications from DDoS attacks:
- Traffic Engineering: AWS uses its vast global infrastructure to automatically absorb and redirect traffic that appears to be part of a DDoS attack. This is achieved through AWS’s large-scale distributed network, which can handle massive amounts of traffic while minimizing the impact on the origin servers.
- Real-time Monitoring and Detection: AWS Shield continuously monitors incoming traffic and uses sophisticated algorithms to detect abnormal patterns indicative of a DDoS attack, a key concept explored in AWS Training, where learners gain expertise in using AWS security services to protect applications and infrastructure from potential threats. When an attack is detected, it automatically triggers mitigation processes.
- Rate Limiting: AWS Shield can rate-limit requests to specific resources, ensuring that excessive traffic from malicious actors does not overwhelm an application. By applying limits to how often certain types of requests can be made, Shield helps prevent traffic overloads that result from attacks.
- Geographic Traffic Filtering: AWS Shield can filter traffic based on geographic location. If an attack originates from specific regions, traffic from those regions can be blocked or rate-limited, allowing legitimate traffic to reach the application.
- Intelligent DDoS Mitigation: The service leverages machine learning to understand an application’s standard traffic patterns and identifies and blocks attacks before they can disrupt services.
Integrating AWS Shield with Other AWS Services
AWS Shield is designed to integrate seamlessly with other AWS services to enhance security and resilience across cloud infrastructure. One key integration is with Amazon CloudFront, AWS’s content delivery network (CDN), which caches and delivers web content with low latency. By combining CloudFront with AWS Shield, organizations gain strong DDoS protection, as traffic is distributed across multiple edge locations, making it difficult for attackers to target a single resource. Another crucial integration is with Elastic Load Balancing (ELB), which automatically distributes incoming traffic across multiple targets, similar to how you Link a Raspberry Pi to the Internet, ensuring seamless communication and efficient distribution of data across multiple devices or services. Shield works with ELB to mitigate DDoS attacks effectively by scaling resources dynamically and ensuring traffic is handled efficiently. Additionally, AWS Global Accelerator plays a vital role by routing traffic through AWS’s global network to enhance application performance and availability. When paired with Shield, Global Accelerator helps absorb and redirect DDoS traffic to the nearest edge location for mitigation. Lastly, AWS Shield Advanced integrates with AWS WAF (Web Application Firewall) to provide granular control over application-layer attacks. Organizations can define security rules that block or allow traffic based on parameters like IP addresses and query patterns, strengthening protection against threats. Together, these integrations ensure robust, automated, and scalable security for AWS-hosted applications.
Considering Pursuing a AWS Master’s Degree? Enroll For AWS Masters Course Today!
AWS Shield Advanced: A Deeper Level of Protection
AWS offers AWS Shield Advanced for customers requiring comprehensive protection against more extensive and sophisticated DDoS attacks. This premium service provides additional features and benefits to protect applications further. Some key features of AWS Shield Advanced include:
- Enhanced Detection and Mitigation: Shield Advanced provides a deeper level of detection and mitigation using more granular traffic analysis. It can more accurately distinguish between benign traffic and attacks, which is especially useful for complex, low-volume application layer attacks that are harder to detect.
- 24/7 DDoS Response Team (DRT) Support: One of Shield Advanced’s most essential features is AWS’s DDoS Response Team (DRT) access. This team consists of security experts available 24/7 to provide real-time support during an attack. They can assist with identifying attack vectors, mitigating damage, and ensuring your services are restored as quickly as possible.
- Cost Protection: Large-scale DDoS attacks can spike your AWS costs, especially if they lead to increased traffic or resource consumption, similar to how Grid Computing efficiently distributes computational tasks across multiple systems to handle high workloads, ensuring optimal resource utilization and minimizing costs. Shield Advanced provides cost protection to cover extra charges incurred by the attack, ensuring that your business is not financially penalized for DDoS-related traffic spikes.
- Application Layer DDoS Protection: Shield Advanced protects against sophisticated application layer attacks, such as HTTP and DNS query floods. This allows it to guard against attacks targeting specific application vulnerabilities.
- Advanced Threat Intelligence: Shield Advanced uses global threat intelligence and advanced machine learning to detect patterns that may signal an impending attack. This enables proactive defense measures that help prevent attacks from causing significant harm to your services.
- Web Application Firewall (WAF) Integration: Shield Advanced integrates seamlessly with AWS WAF (Web Application Firewall), allowing customers to configure rules that block malicious traffic at the application layer. This enhances overall protection by defending against DDoS attacks and other web-based attacks.
- Global Response: Shield Advanced’s multi-regional mitigation can protect applications distributed across various AWS regions, ensuring protection for all parts of your infrastructure.
Best Practices for Maximizing AWS Shield Protection
While AWS Shield provides robust protection against DDoS attacks, implementing best practices can further strengthen your security posture. Businesses relying on mission-critical applications should consider AWS Shield Advanced, which offers enhanced protection, including 24/7 access to the DDoS Response Team (DRT) for real-time attack mitigation. Additionally, integrating AWS WAF (Web Application Firewall) with AWS Shield helps protect against Layer 7 attacks, allowing organizations to define custom security rules for their web applications, a practice that aligns with the Future of DaaS in Cloud Computing, where robust security measures and custom configurations play a vital role in ensuring secure, scalable, and efficient cloud-based solutions. Automating responses is another crucial aspect of DDoS protection. By leveraging AWS CloudWatch and AWS Lambda, organizations can detect unusual traffic spikes and take automated actions, such as blocking suspicious IP addresses or throttling excessive traffic.
Continuous monitoring is essential, and Amazon CloudWatch Metrics provides real-time insights into traffic patterns and blocked requests, enabling businesses to react swiftly to potential threats. Finally, proactive testing is key to ensuring a resilient defense against DDoS attacks. Regular DDoS mitigation testing using AWS Fault Injection Simulator helps identify vulnerabilities in the protection strategy before a real attack occurs. By adopting these best practices, businesses can enhance their overall security, minimize downtime, and ensure seamless service availability against evolving cyber threats.
Want to Learn About AWS? Explore Our AWS Interview Questions & Answer Featuring the Most Frequently Asked Questions in Job Interviews.
Conclusion
AWS Shield provides a comprehensive solution for protecting your AWS-based applications and infrastructure from DDoS attacks. With its two tiers of protection, Shield Standard and Shield Advanced, AWS offers a flexible and robust security model to meet the needs of different organizations. Whether you need essential protection or advanced, real-time support from the DDoS Response Team, AWS Shield offers powerful capabilities to keep your services safe from cyber threats, a critical area covered in AWS Training, where learners understand how to leverage AWS security features to safeguard cloud-based applications from DDoS and other malicious attacks. By integrating AWS Shield with other AWS services like CloudFront, ELB, and WAF, businesses can ensure that their applications are well-defended, even against sophisticated and large-scale DDoS attacks. With AWS Shield in place, you can focus on growing your business and innovating, knowing that your applications are protected from malicious traffic and downtime.





